TL;DR — Google cookies that don’t expire and work even when the account’s password is changed, huge advantage for cybercriminals, nothing done by Google.
A month ago Hudson Rock reported that Lumma Infostealer group are going to implement a new feature which will allow them to revive expired Google cookies (https://www.infostealers.com/article/lumma-malware-can-allegedly-restore-expired-google-auth-cookies/)
We warned that this will cause a shift in cybercrime, and that hackers will be able to infiltrate accounts with ease.
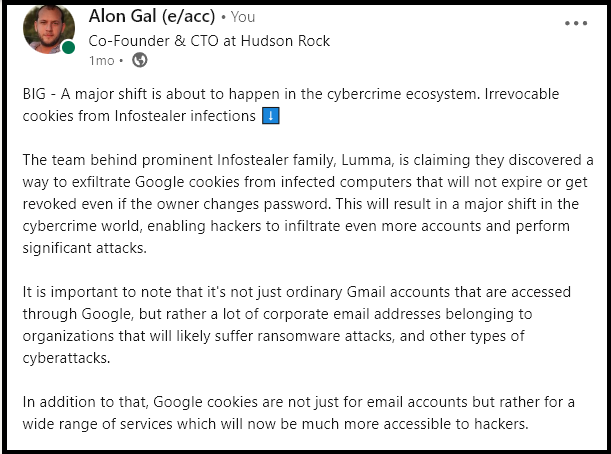
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups, the exploit is only becoming more widely used, with over 5 Infostealer groups taking advantage of the exploit.
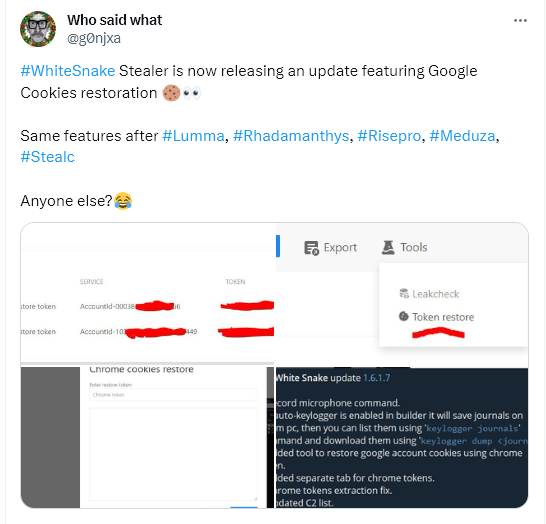
In addition, Hudson Rock spoke to a developer who claims they came up with this 0-day back in October and was selling it independently. They sent us a video of the exploit which you can watch here — https://www.youtube.com/watch?v=NzAtZzzFoOs
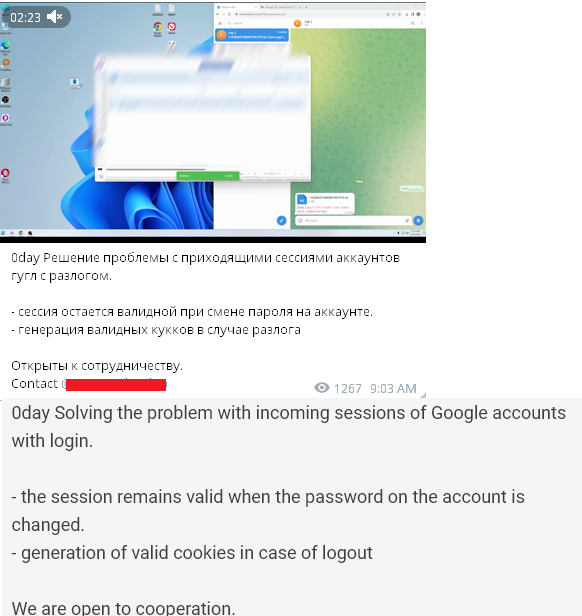
We expect to see this feature implemented by all Infostealer groups until some action is taken by Google.
Why aren’t Google doing anything about it? We speculate that the reason is that the trade off with blocking the cookie reviving mechanism is not worth it because it serves some kind of user ease of use.
We’ll follow up on developments, don’t forget to sign up with your email to receive our updates!