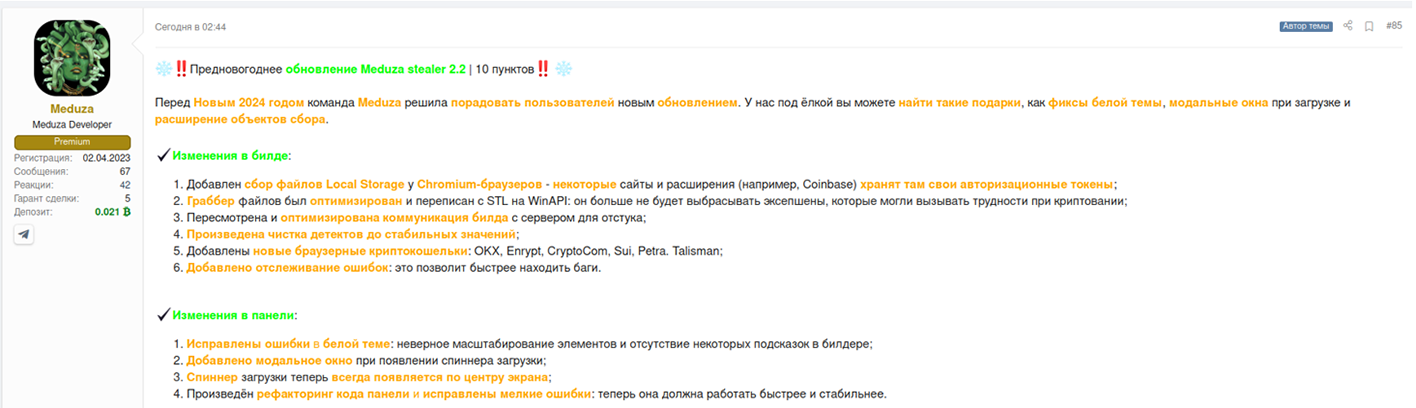
On Christmas Eve, Resecurity’s HUNTER (HUMINT) spotted the author of perspective password stealer Meduza has released a new version (2.2). This product has already generated significant interest in Dark Web after the initial release in June this year. One of the key significant improvements are support of more software clients (including browser-based cryptocurrency wallets), upgraded credit card (CC) grabber, and additional advanced mechanisms for password storage dump on various platforms to extract credentials and tokens. Altogether, Meduza makes a great competitor to Azorult, Redline, Racoon, and Vidar Stealer used by cybercriminals for account takeover (ATO), online-banking theft, and financial fraud.
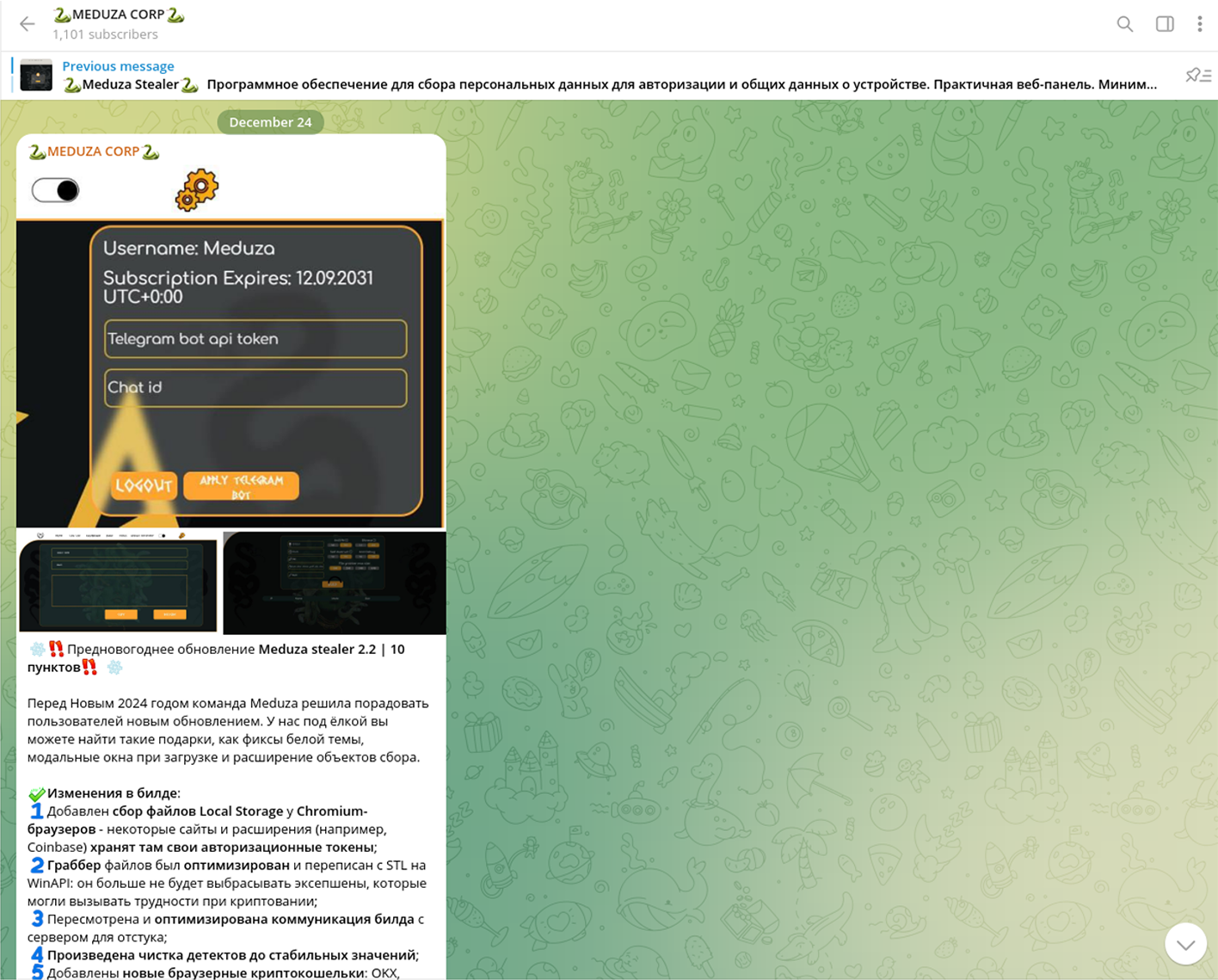
Translation:
Attention! The New Year’s Update
Before the New Year 2024, the Meduza team decided to please customers with an update. Under Christmas tree you can find great gifts such as significant improvements of user interface (panel), modal windows on loading and expansion of data collection objects.
The product has been originally emerged at XSS underground forum, and later received positive feedback on other well-established communities including Exploit.
Presently, Meduza password stealer supports Windows Server 2012/2016/2019/2022 and Windows 10/11. The author demonstrated successful work on all editions and what other Dark Web actors called “stable and ideal”.
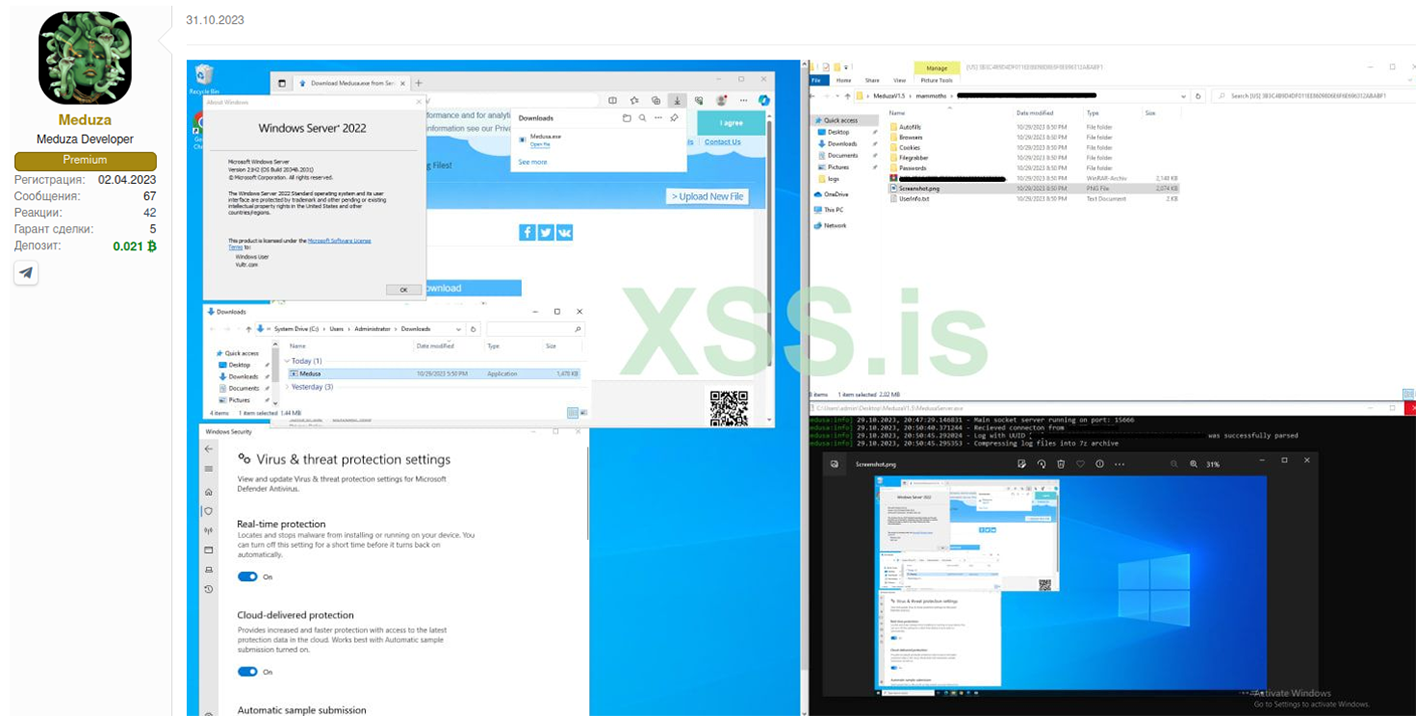
The stealer allows to grab data from popular software applications, including but not limited to support of:
- 106 browsers
- 107 cryptocurrency wallets
- any file extension via FileGrabber (module)
- Telegram IM
- Steam
- Discord
- 27 password managers
- OpenVPN
- Outlook (e-mail client)
- Google Tokens
The full updated list of supported software is provided below:
Chromium-based:
Google Chrome, Google Chrome Beta, Google Chrome (x86), Google Chrome SxS, 360ChromeX, Chromium, Microsoft Edge, Brave Browser, Epic Privacy Browser, Amigo, Vivaldi, Kometa, Orbitum, Mail.Ru Atom, Comodo Dragon, Torch, Comodo, Slimjet, 360Browser, 360 Secure Browser, Maxthon3, Maxthon5, Maxthon, QQBrowser, K-Meleon, Xpom, Lenovo Browser, Xvast, Go!, Safer Secure Browser, Sputnik, Nichrome, CocCoc Browser, Uran, Chromodo, Yandex Browser, 7Star, Chedot, CentBrowser, Iridium, Opera Stable, Opera Neon, Opera Crypto Developer, Opera GX, Elements Browser, Citrio, Sleipnir5 ChromiumViewer, QIP Surf, Liebao, Coowon, ChromePlus, Rafotech Mustang, Suhba, TorBro, RockMelt, Bromium, Twinkstar, CCleaner Browser, AcWebBrowser, CoolNovo, Baidu Spark, SRWare Iron, Titan Browser, AVAST Browser, AVG Browser, UCBrowser, URBrowser, Blisk, Flock, CryptoTab Browser, SwingBrowser, Sidekick, Superbird, SalamWeb, GhostBrowser, NetboxBrowser, GarenaPlus, Kinza, InsomniacBrowser, ViaSat Browser, Naver Whale, Falkon
Gecko-based:
Firefox, SeaMonkey, Waterfox, K-Meleon, Thunderbird, CLIQZ, IceDragon, Cyberfox, BlackHawk, Pale Moon, IceCat, Basilisk, BitTube, SlimBrowser
Supported Crypto-extensions:
Metamask, Metamask (Edge), Metamask (Opera), BinanceChain, Bitapp, Coin98, Safe Pal, Safe Pal (Edge), DAppPlay, Guarda, Equal, Guild, Casper, Casper (Edge), ICONex, Math, Math (Edge), Mobox, Phantom, TronLink, XinPay, Ton, Sollet, Slope, DuinoCoin, Starcoin, Hiro Wallet, MetaWallet, Swash, Finnie, Keplr, Crocobit, Oxygen, Nifty, Liquality, Ronin, Ronin (Edge), Oasis, Temple, Pontem, Solflare, Yoroi, iWallet, Wombat, Coinbase, MewCx, Jaxx Liberty (Web), OneKey, Hycon Lite Client, SubWallet (Polkadot), Goby, TezBox, ONTO Wallet, Hashpack, Cyano, Martian Wallet, Sender Wallet, Zecrey, Auro, Terra Station, KardiaChain, Rabby, NeoLine, Nabox, XDeFi, KHC, CLW, Polymesh, ZilPay, Byone, Eternl, Guarda (Web), Nami, Maiar DeFi Wallet, Leaf Wallet, Brave Wallet, Opera Wallet, CardWallet, Flint, Exodus (Web), TrustWallet, CryptoAirdrop
Desktop cryptocurrency wallets:
Coinomi, Dash, Litecoin, Bitcoin, Dogecoin, Qtum, Armory, Bytecoin, MultiBit, Jaxx Liberty, Exodus, Ethereum, Electrum, Electrum-LTC, Atomic Wallet, Guarda, WalletWasabi, ElectronCash, Sparrow, IOCoin, PPCoin, BBQCoin, Mincoin, DevCoin, YACoin, Franko, FreiCoin, InfiniteCoin, GoldCoinGLD, Binance, Terracoin, Daedalus Mainnet, MyMonero, MyCrypto, AtomicDEX, Bisq, Defichain-Electrum, TokenPocket (Browser), Zap
Password managers:
Authenticator, Authenticator (Edge), Trezor Password Manager, GAuth Authenticator, EOS Authenticator, 1Password, 1Password (Edge), KeePassXC (Web), KeePassXC (Web Edge), Dashlane, Dashlane (Edge), Bitwarden, Bitwarden (Edge), NordPass, Keeper, RoboForm (Web), RoboForm (Web Edge), LastPass, LastPass (Edge), BrowserPass, MYKI, MYKI (Edge), Splikity, CommonKey, SAASPASS, Zoho Vault, Authy (Web)
Discord clients:
Discord, DiscordCanary, DiscordPTB, Lightcord, DiscordDevelopment
Telegram clients:
Kotatogram, Telegram desktop
The report of Meduza Stealer contains specific signature with its brand. Similar to Azorult and Redline the structure of the report (log) is very detailed providing insights about the victim’s infected machine.
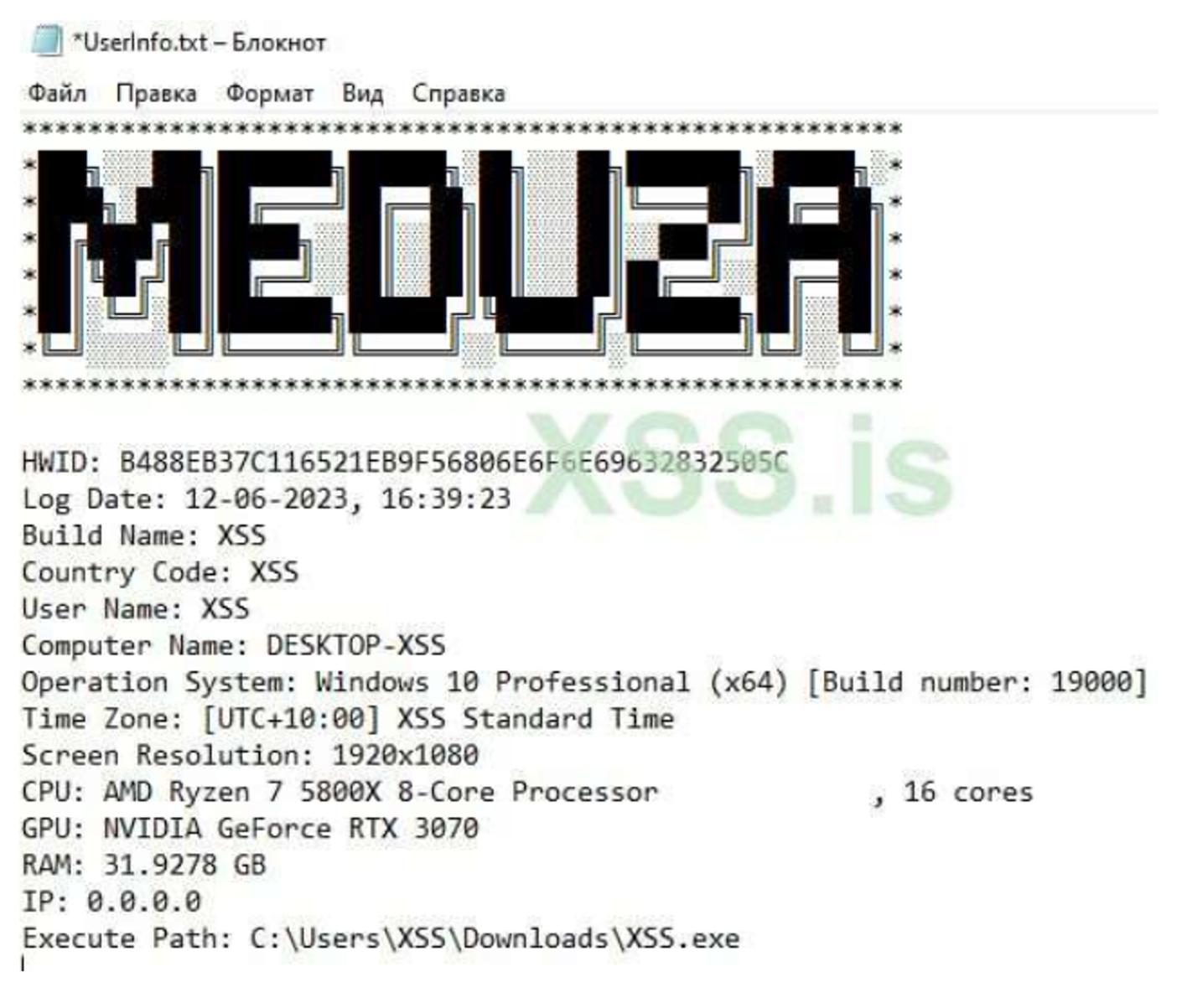
GUI:
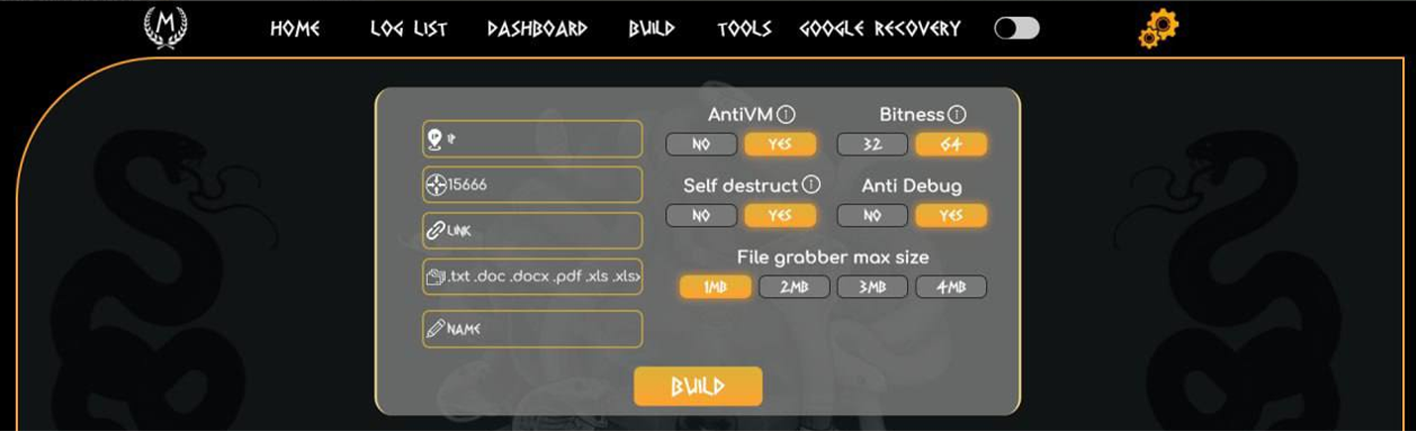
Configuration Panel:
Coming in 2024, the author behind Meduza is implmenting the following upgrades:
- Chromium-based Browsers Support (Local Storage Dump), as some of the WEB-sites and extensions (for e.g. Coinbase) store their authorization tokens. Notably, the week before current release, the author implemented Windows Credential Manager and Windows Vault dump.
- Password grabber has been optimized and re-written from STL to WinAPI, multiple improvements have been implemented into C2C communications;
- Support of new browser-based cryptocurrency wallets including but not limited to OKX, Enrypt, CryptoCom, Sui, Petra, Talisman. Besides crypto-related tokens, Meduza also supports Google Account tokens, which may be used for cookie manipulation to access compromised accounts. There was added support of Google Chrome Canary, Google Chrome Dev, Google Chrome Beta. In the C2C panel there is a new dection called “Google Token Recovery” allowing to process such tokens.
- Improved crypting stub and AV evasion. For additional fee ($119) the author may deliver enhanced obfuscation of the stealer with better AV anti-detection coverage.
Interface of “Google Token Recovery” feature:
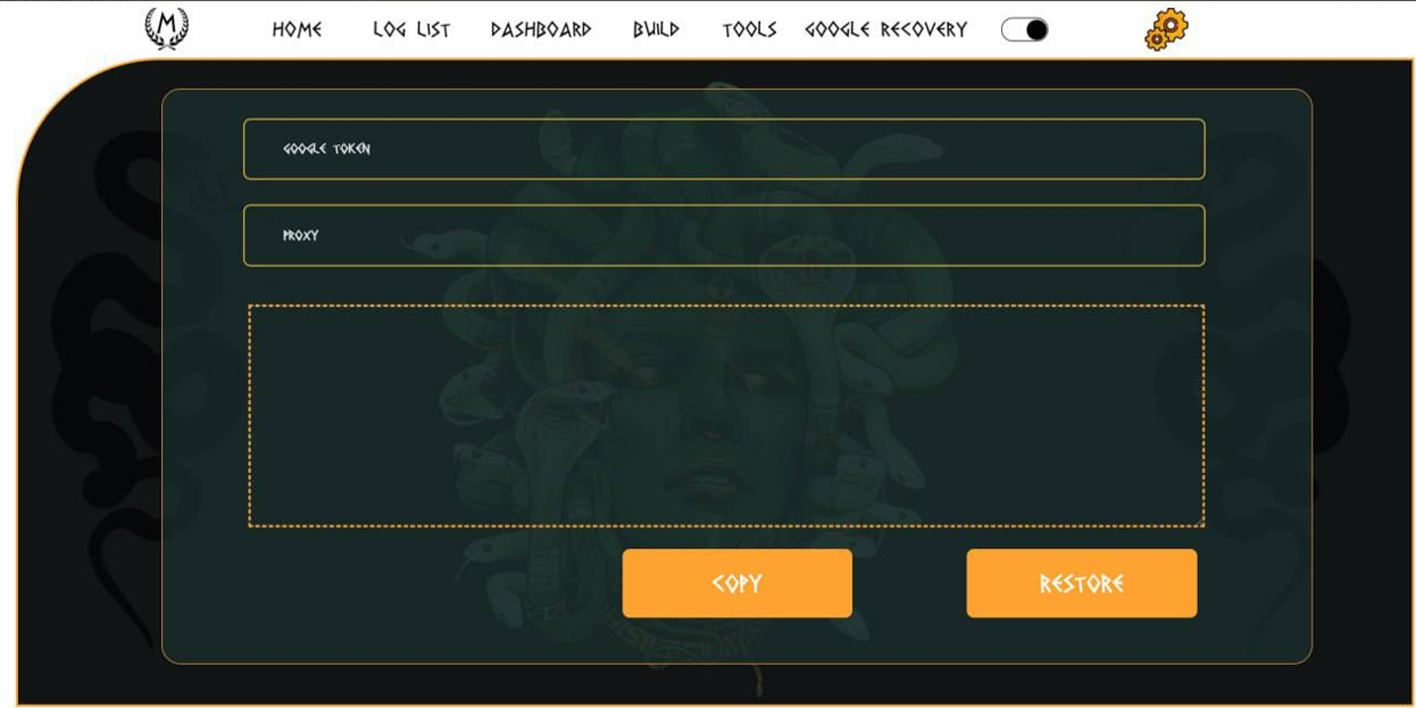
Notably, Meduza has partnered with one of the reputable underground crypting services called TrueCrypt Service. This service is widely used by malware and ransomware operators to obfuscate malicious payloads and evade AVs.
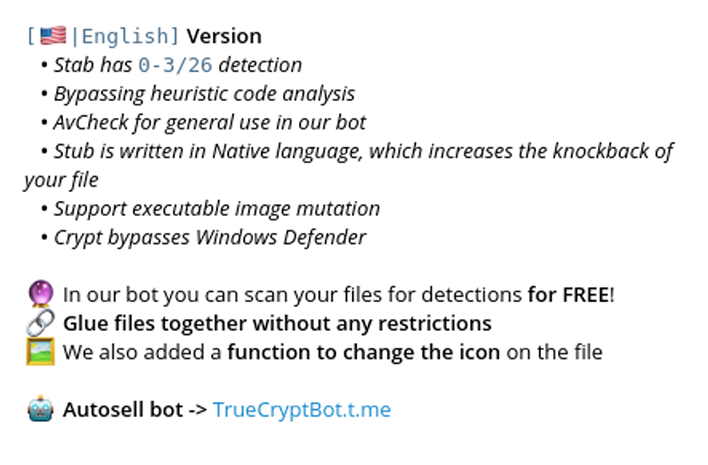
Crypting is available via interactive Telegram bot:
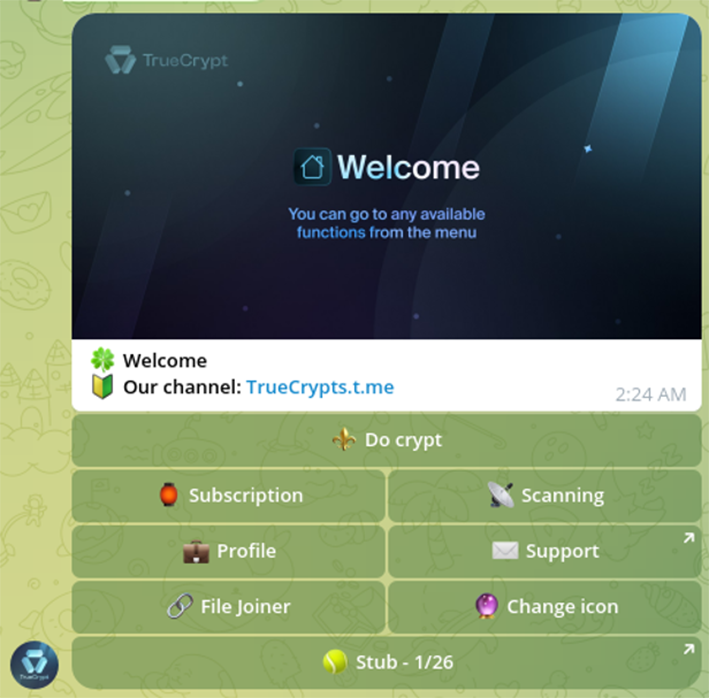
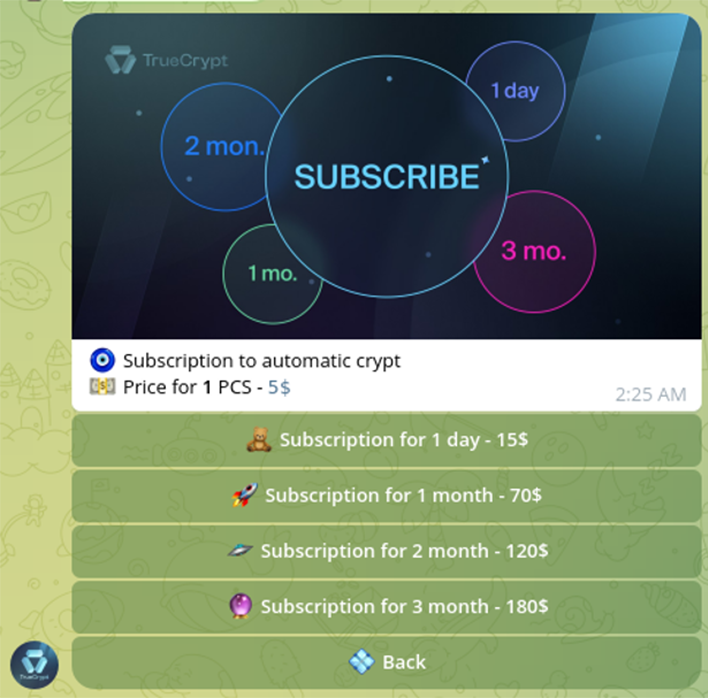
Notably, the latest result of crypting showed great results and detection just by 1 AV from 27 (1/27):
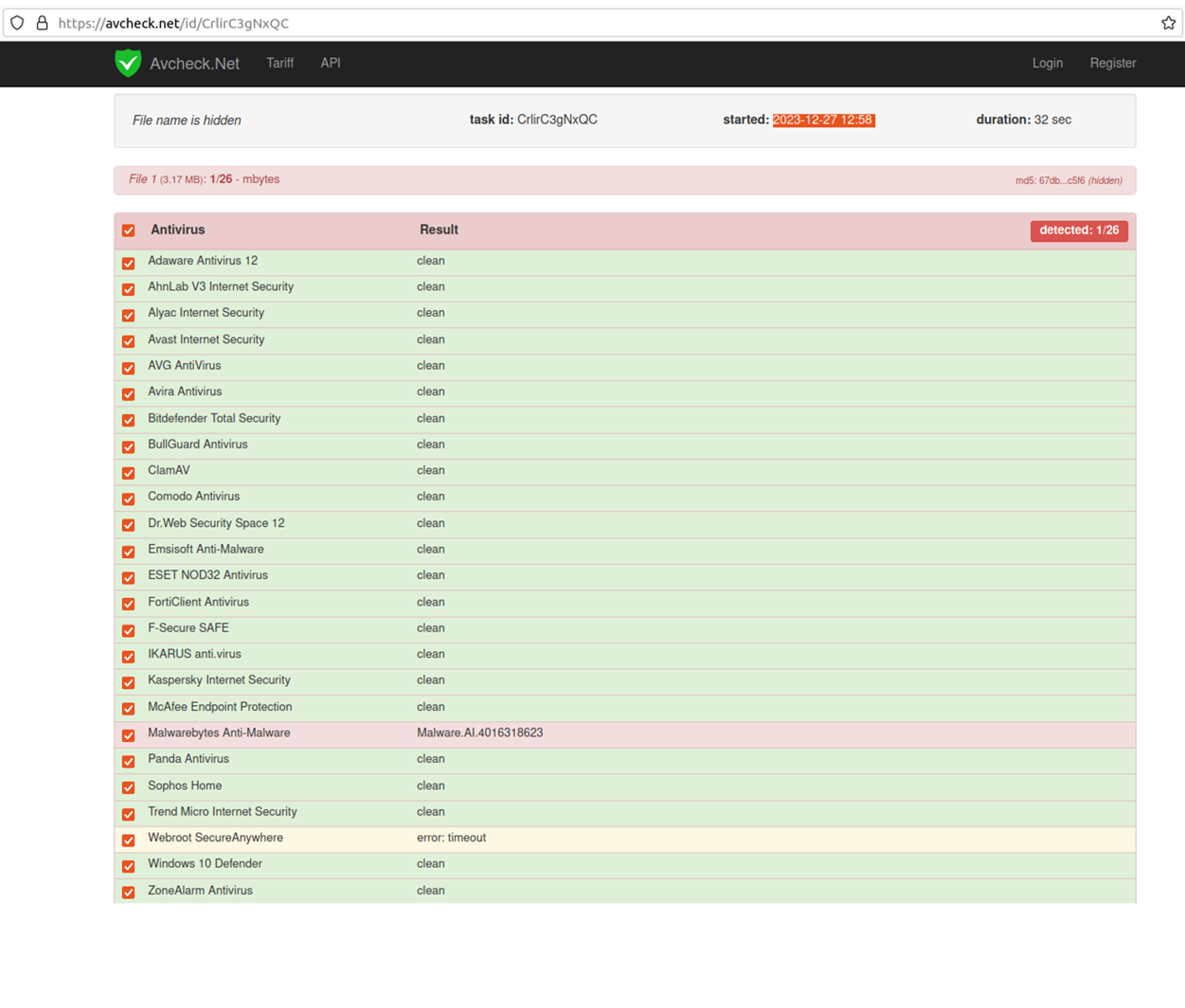
Meduza Stealer 2.2 is available for rent starting at $199 per month. The team behind the stealer is also offering crypting services with public (shared across all customers) and private stub (prepared individually), as well as servers for rent to host C2C panel.
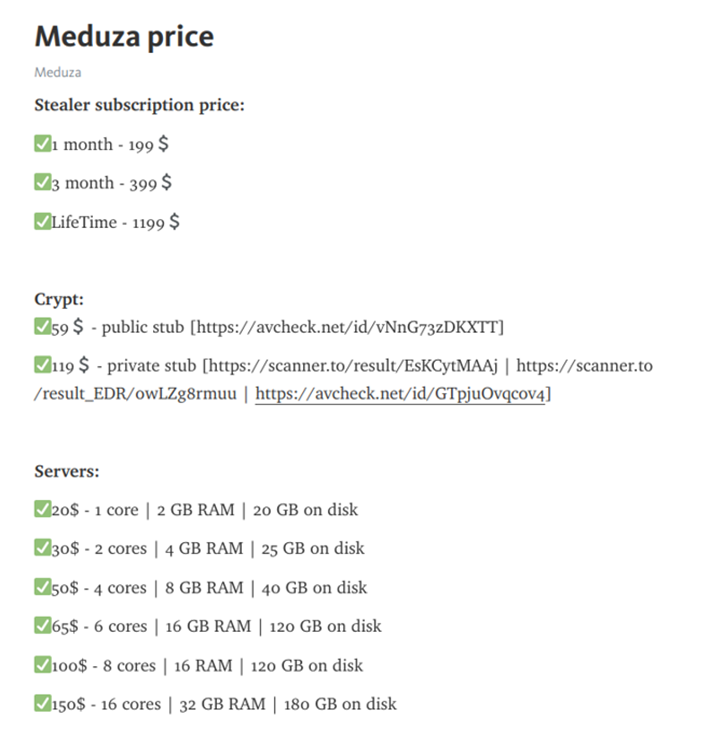
After the payment has been made, the author will invite the new client into private (invite-only) channel on Telegram where he will share the newly released tooling.
In fact, the most newest version released for today and available on private Telegram channel after subscription activation is Meduza 2.2.7.
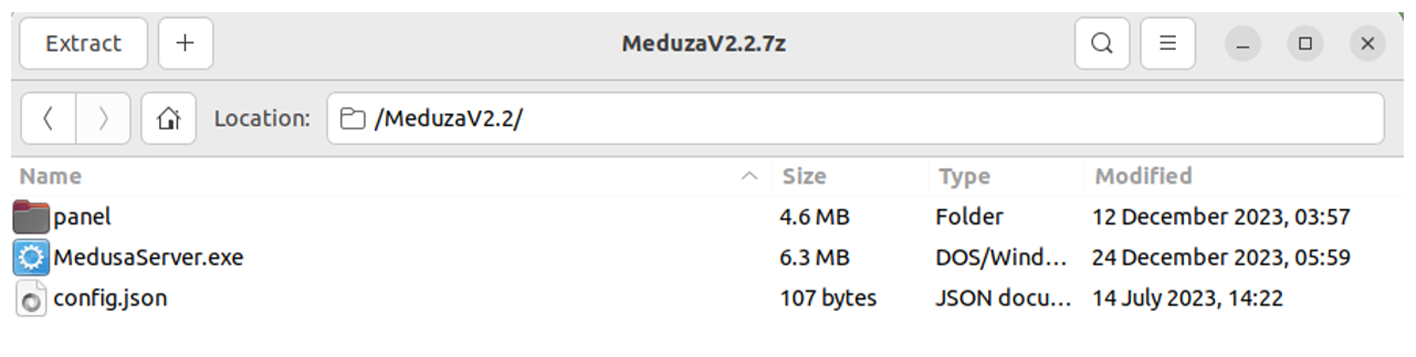
The C2C panel has been also upgraded and remained written in Python:
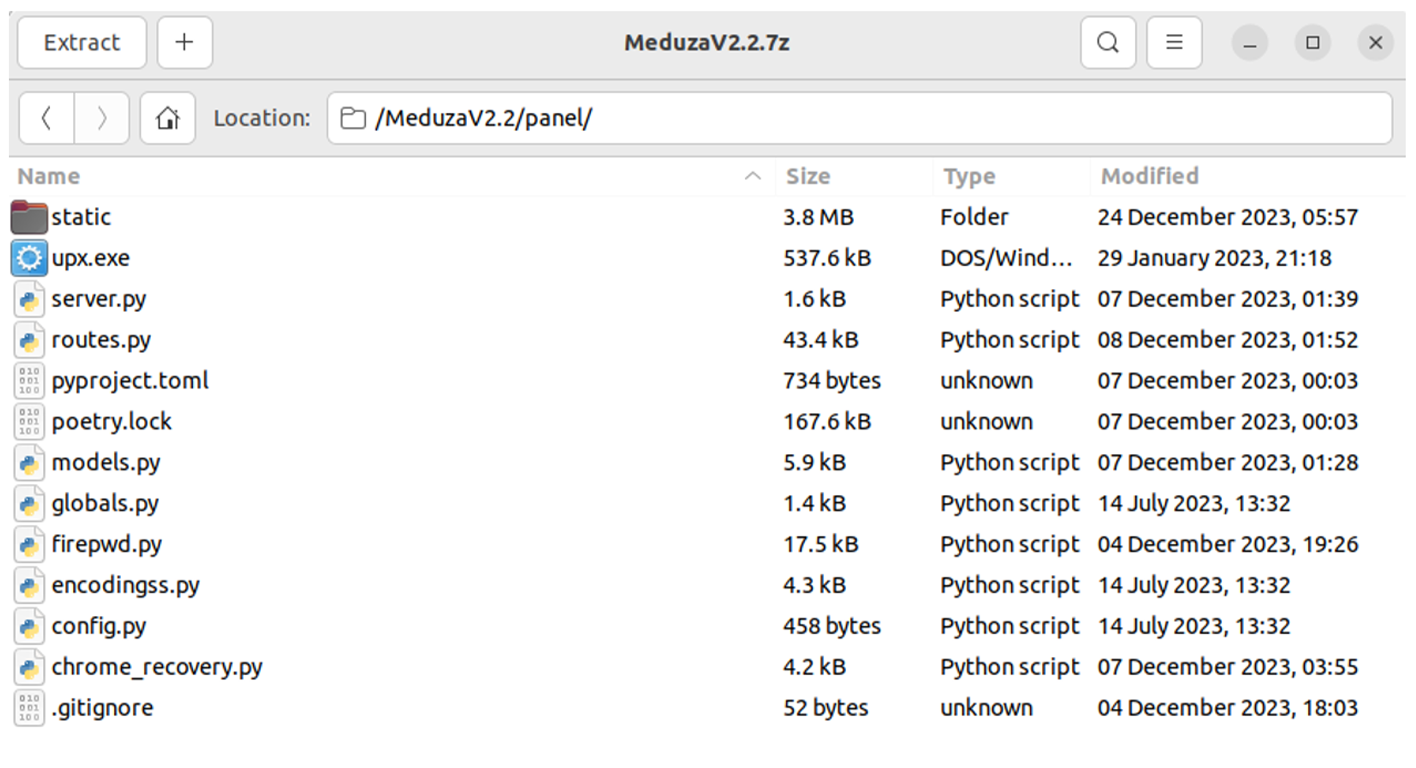
In order to install Meduza, the operator needs to follow the following instructions:
- Launch MedusaServer.exe
- Install Python 3.10.2
- Install Microsoft Visual Studio Redistributable
- Execute in console the following commands:
pip install poetry
poetry config virtualenvs.in-project true
cd panel
poetry install
.venv\Scripts\activate
playwright install
python server.py
Meduza 2.2 supports communications via Telegram IM to deliver logs from the infected victim. The operator may define API key and ID of the channel to set it up.
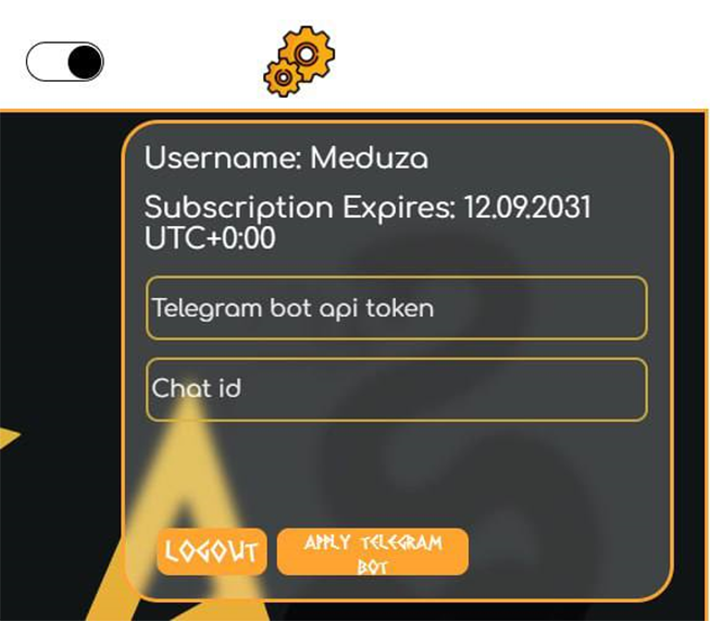
Meduza Stealer remains one of the best in class. The product has operative support and constant updates with significant feature set improvements. Meduza has already started to compete with Azorult and Redline Stealer due to flexible configuration system and wide application coverage.
Malware Hashes (MD5)
\Meduza V2.2\Builder
5D9E2C18B4A261519E121754CD682B25 MedusaServer.exe
EA6562FF5BCCA7182EEBC6F4E83DECAA config.json
\MeduzaV2.2\Panel
—————————————————
EBA71E82CB96780B4711BF898067BA81 server.py
5C1E871A99108B68C90F6ADBAC5B190F routes.py
3894A29E43D8847778F0FBB81BB479B9 pyproject.toml
73070434952F46D1F37F9AB4BB99754F poetry.lock
EB52C4A4BEF2367E721BBE13E89AACF5 models.py
ADC35BB330618A365685B5864E403007 globals.py
02FA600EB8A92D7CE676F87269365CA0 firepwd.py
021B649CE9D11E2CA9C67761953B1408 encodingss.py
C1824076854ACAC6858177062C1F5493 config.py
80136B6C96F8B23F8E938E38E01C58E6 chrome_recovery.py
C712A1B8A70FB7D0C7A714E12EFF0E38 .gitignore
\MeduzaV2.2\Panel\Static Folder
—————————————————
FA1DED1ED7C11438A9B0385B1E112850 robots.txt
74EE6AC5ACEABA962B45D8295DB06823 manifest.json
6FEF55E48E2392DBE72DF975EEAA5030 index.html
\MeduzaV2.2\Panel\Static\Assets Folder
—————————————————
D35ECA43E27128431B427578D7EC4404 TotalLogs-B-E2YwnZ.png
005A687909B2CD3B0DC757E696AEDFD3 snake-lPgznXqp.png
BD1F946D08F9E4747E7DFDEC6823E4F0 settings-I0_wb9DP.png
A77B3786F7A53152D9AE31930D4C7FE4 proxy-djqteFjQ.png
54BBEBBFEB771DD609FF329099704A6A profile-bXjbzb05.png
14DC11E9386E2AEB9005DC2906F27DD1 port-rmPefoZT.png
557BDA3A9CD30126257AE2733DC51738 pencil-_4BhWMe4.png
7264FD364F9DFF44E65DACF23348A29E Meduza-Xf1ectds.png
2AAA6F1BE965EB98DE80E55286525FF6 loupe-_mfn3Vyn.png
E7A2BB050F7EC5EC2BA405400170A27D logo-ovWOqCdT.svg
E7C085CD99652B734D208888C91BD249 link-9UZGtMhQ.png
244F76846B82C315F96A6A70BBD4C7DC ip-BeCA78j8.png
EB17C2089CE02C6C9A711DB92751D9E1 information-MI6lnrKe.png
05FC2D25B0B1AF9EA058F9B8DB3D5156 index-meiT9fTn.css
DBC8C6622A2E9BE15ADEA1C936340D9E index-cm7TvlL3.js
D8625B338B13C0A1703AE2CD0059540F GoogleToken-JnjNeTRs.png
39A083EB4D82950E58CEF105A3C6A9D4 fileSize-jXgEEV2i.png
D3A9C85A9155C22F5719D7953BA8F8D6 file-7daGp-7D.png
0BB345C489B1D09A276D8AE1409FE28F ds-greece-eWgboWnd.ttf
6174A343DD4C9A7D4AE7802B3EEA3134 delete-O6fZYS2-.png
FBE3D766BC659B28244F5B401D497A1B delete_after-CPfbcLvs.png
B14DA82FD326FB23ADA0B4DF443CDA25 Comfortaa-VariableFont_wght-R_5AX4pn.ttf
E22F9B945371079B09E4E1E562DFC071 calendarWeek-ZP6zLNm9.png
96F38055CAF432E112077AD70663ABD2 calendarMounth-vgkHK7KK.png
7B9A86691DAE4B913BA8B08F3F2ADFF8 calendarAfter-PPQE7FN7.png
C012CF6D414F3DFFFCE577623D91FD50 calendar-5_8NiYB7.png
FA1DED1ED7C11438A9B0385B1E112850 robots.txt
74EE6AC5ACEABA962B45D8295DB06823 manifest.json
6FEF55E48E2392DBE72DF975EEAA5030 index.html
\MeduzaV2.2\Panel Folder
—————————————————
EBA71E82CB96780B4711BF898067BA81 server.py
5C1E871A99108B68C90F6ADBAC5B190F routes.py
3894A29E43D8847778F0FBB81BB479B9 pyproject.toml
73070434952F46D1F37F9AB4BB99754F poetry.lock
EB52C4A4BEF2367E721BBE13E89AACF5 models.py
ADC35BB330618A365685B5864E403007 globals.py
02FA600EB8A92D7CE676F87269365CA0 firepwd.py
021B649CE9D11E2CA9C67761953B1408 encodingss.py
C1824076854ACAC6858177062C1F5493 config.py
80136B6C96F8B23F8E938E38E01C58E6 chrome_recovery.py
C712A1B8A70FB7D0C7A714E12EFF0E38 .gitignore
\MeduzaV2.2\Panel\Static Folder
—————————————————
FA1DED1ED7C11438A9B0385B1E112850 robots.txt
74EE6AC5ACEABA962B45D8295DB06823 manifest.json
6FEF55E48E2392DBE72DF975EEAA5030 index.html
\MeduzaV2.2\Panel\Static\Assets Folder
—————————————————
D35ECA43E27128431B427578D7EC4404 TotalLogs-B-E2YwnZ.png
005A687909B2CD3B0DC757E696AEDFD3 snake-lPgznXqp.png
BD1F946D08F9E4747E7DFDEC6823E4F0 settings-I0_wb9DP.png
A77B3786F7A53152D9AE31930D4C7FE4 proxy-djqteFjQ.png
54BBEBBFEB771DD609FF329099704A6A profile-bXjbzb05.png
14DC11E9386E2AEB9005DC2906F27DD1 port-rmPefoZT.png
557BDA3A9CD30126257AE2733DC51738 pencil-_4BhWMe4.png
7264FD364F9DFF44E65DACF23348A29E Meduza-Xf1ectds.png
2AAA6F1BE965EB98DE80E55286525FF6 loupe-_mfn3Vyn.png
E7A2BB050F7EC5EC2BA405400170A27D logo-ovWOqCdT.svg
E7C085CD99652B734D208888C91BD249 link-9UZGtMhQ.png
244F76846B82C315F96A6A70BBD4C7DC ip-BeCA78j8.png
EB17C2089CE02C6C9A711DB92751D9E1 information-MI6lnrKe.png
05FC2D25B0B1AF9EA058F9B8DB3D5156 index-meiT9fTn.css
DBC8C6622A2E9BE15ADEA1C936340D9E index-cm7TvlL3.js
D8625B338B13C0A1703AE2CD0059540F GoogleToken-JnjNeTRs.png
39A083EB4D82950E58CEF105A3C6A9D4 fileSize-jXgEEV2i.png
D3A9C85A9155C22F5719D7953BA8F8D6 file-7daGp-7D.png
0BB345C489B1D09A276D8AE1409FE28F ds-greece-eWgboWnd.ttf
6174A343DD4C9A7D4AE7802B3EEA3134 delete-O6fZYS2-.png
FBE3D766BC659B28244F5B401D497A1B delete_after-CPfbcLvs.png
B14DA82FD326FB23ADA0B4DF443CDA25 Comfortaa-VariableFont_wght-R_5AX4pn.ttf
E22F9B945371079B09E4E1E562DFC071 calendarWeek-ZP6zLNm9.png
96F38055CAF432E112077AD70663ABD2 calendarMounth-vgkHK7KK.png
7B9A86691DAE4B913BA8B08F3F2ADFF8 calendarAfter-PPQE7FN7.png
C012CF6D414F3DFFFCE577623D91FD50 calendar-5_8NiYB7.png
FA1DED1ED7C11438A9B0385B1E112850 robots.txt
74EE6AC5ACEABA962B45D8295DB06823 manifest.json
6FEF55E48E2392DBE72DF975EEAA5030 index.html