This one tries to highlight how I got access to the log files present over a C2 server of an infamous information stealer malware. This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations within the maliciously hosted C2 servers. Without wasting any time, let’s get started.

I found an IP that hosted multiple login panels and mentioned ‘Mana Tools’. I have not added the image, but OSINT researchers very well know where to look for the same!
About Mana Tools
The context of Mana Tools is not very new for the people who have spent some years in threat intelligence and security research. Based on a blog by Malware News, it is a malware distribution and command and control (C2) panel associated with several big names in the malware world.
Mana Tools was discovered in 2019 by Yoroi researchers.
After a significant pause, in 2023, a similar C2 panel was reused by a big name in the malware world, as mentioned above.
Back to the blog
The given URL was mentioned like https://x.x.x.x/[name]/login.php
My immediate next step was to check for VirusTotal results that yielded me some file names that the IP was referring to, some files were named as ‘[name]_payload.vbs’. Here the same name was present as a VBS filename as it appeared in the URL. That being said, I happened to brute search for other names that were as recent as 1 June 2023.
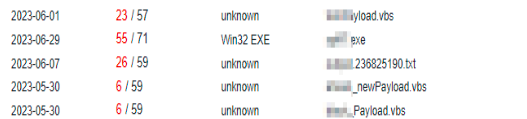
And it worked! I was able to identify at least 3 different logins hosted on the same IP.
It was then the time to bruteforce for the directories that can give us further insights, if any. After setting the IP for Gobuster, I identified multiple endpoints with status code 301. Sharing the image below for reference.
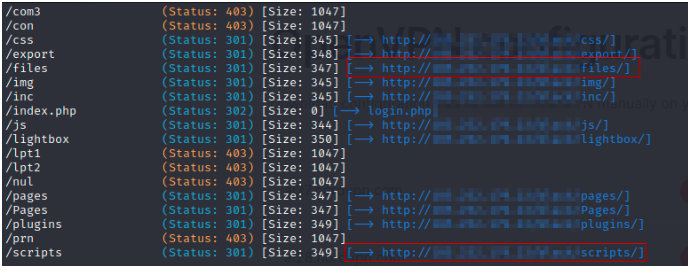
Out of which, the interesting finds were inc, js, lightbox, pages, plugins, scripts, and files. Had there been any other interesting keys present, then the Trufflehog extension would have definitely triggered it, but unfortunately, there wasn’t any. I moved forward by manually searching for anything interesting.
And voila, the ‘file’ endpoint had all the logs collected as recently as May 2023.
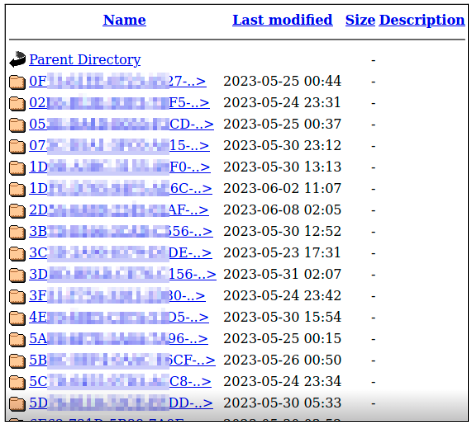
I tried viewing the files or extracting its metadata but it didn’t open citing an unsuitable viewing format. After multiple attempts, I tried viewing it and found the data as follows:
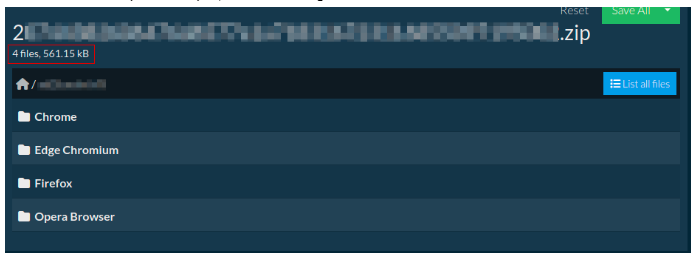
We had access to all the logs collected by the information stealer malware, they were mostly logins and cookies stolen through browsers, in yet to be processed format.
Further, when I tried to obtain the data and convert, it was obtained in sqlite format. I wasn’t able to provide time to this incident further and eventually left it here.
Key takeaways
Scope for automation
It is good to have an automation tool in place that can brute force for common endpoints on a given C2 site to see if there’s a chance to exploit.
Understanding of sophistication
As much as it’s interesting to get a sample of new variants of malware, sometimes, a slightest misconfiguration can reveal the sophistication of the threat actors operating at the backend.
Revealing sensitive information
Considering a scenario where we might have got access to the log files, or credentials, or keys of any sort, there was a slight chance to maintaining persistence in the system further.
To summarize
Unfortunately, the research was halted here, but sometimes you might get lucky enough to maintain persistence and perform stealthy operations. A similar case was observed in the initial C2 instances for Titan information stealer malware. However, that was patched later. This being the second instance, there’s quite some possibility to identify the right loophole when the malware is new or the brand is reused by adversaries with less sophistication.
This might not be the only approach, also, this might not be the perfect approach. There can be many ways to hunt for threats and I presented my case here. Looking forward to knowing your views on the same!
Hope you liked this article. Stay tuned for more such content on threat intelligence.