What do Andrew Tate, a Pro-Palestine hacking group, and AnyDesk all have in common?
For a while now, Infostealer credentials data has been used as a means for disinformation, propaganda, or to facilitate fraud. Here are some recent examples Hudson Rock was able to discover:
1. Haghjoyan Hacking Group Cyberwar Disinformation.
Their Claim:
On october 13th 2023 amidst the breakout of the Israel-Hamas war, a Pro-Palestine hacking group,“Haghjoyan”, claimed to have infected more than 5,000 Israeli computers:
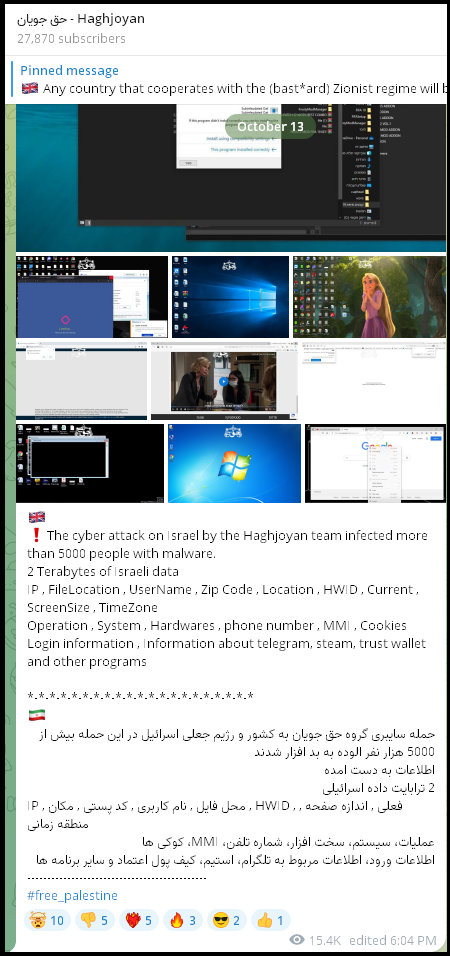
Their “Proof”:
In order to add to the credibility of their claim, the group provided a sample of the data which helped us identify the victims.

Debunking their “Proof”:
At first glance, it was suspicious that the group specifically infected Israeli computers, and the number of computers seemed relatively high in comparison to numbers that Hudson Rock is familiar with in terms of Infostealer infections in Israel.
Through cross-examination of the victim data from the group’s sample alongside Hudson Rock’s cybercrime intelligence database, which contains records of over 25,000,000 computers infected by Infostealers, we’ve determined that the depicted victims are, in fact, older Israeli computers infected through unrelated malware spreading campaigns, distinct from the activities of the ‘Haghjoyan’ group.”
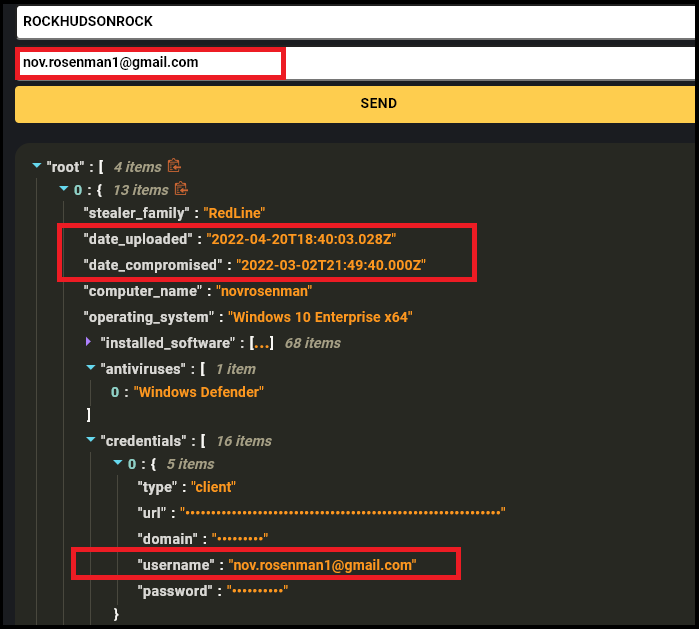
It is evident that the group was trying to use disinformation as a mean for war propaganda and to skew public opinon.
2. Hacker claiming to sell AnyDesk’s database on the darknet, on the day they suffered a breach.
On February 5th, AnyDesk published a public statement in which they revealed that the company suffered a cyber incident in which threat actors were able compromise the company’s production systems:

Taking advantage of the timing, a threat actor published a thread on a Russian cybercrime forum in which they claim to sell AnyDesk’s database.
Their Claim:
The threat actor claims they have access to a database of a large RMS vendor which can be used by a potential buyer to facilitate scams.
The asking price for the database is $15,000 using Bitcoins or Monero.
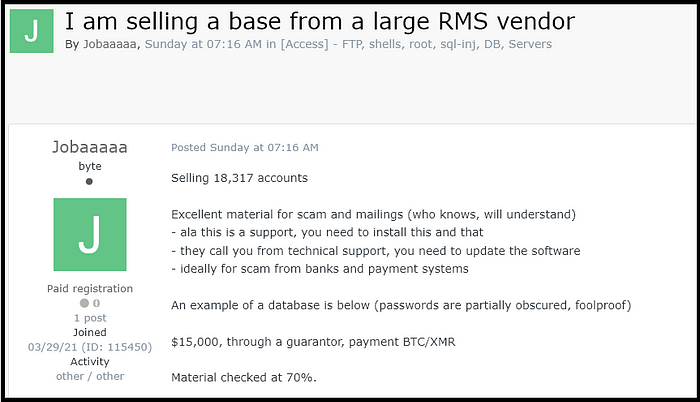
Their “Proof”:
In order to add to the legitimacy of their claims, the threat actor provided a sample from the database, albeit with censored passwords.
The sample made it obvious to potential buyers that the targeted company is AnyDesk (my.anydesk.com):
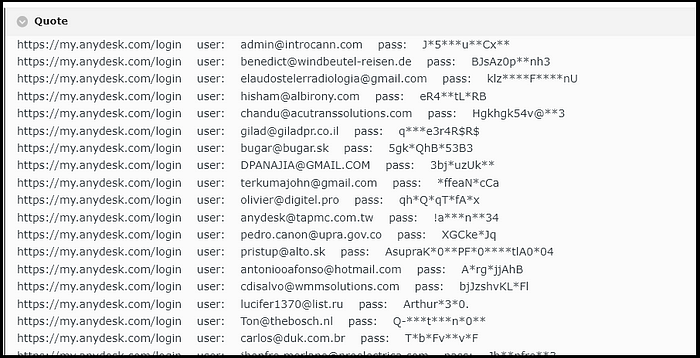
Due to the timing of the threat actor, many cybersecurity publications and Twitter users reported that a threat actor is selling AnyDesk’s database on the darknet, causing a lot of confusion.
Debunking their “Proof”:
By cross checking the hacker’s email sample (admin@introcann.com) with Hudson Rock’s cybercrime intelligence database, researchers were able to determine that the data is in fact from previous Infostealer infections and is not related to the recent AnyDesk breach:

This is not the first time we’ve seen threat actors attempting to sell what they claim are databases of companies when, in actuality, they are just aggregated lists of credentials from previous Infostealer infections.
The idea behind this is of course for the threat actor to attempt scamming users for monetary gains.
3. Disinformation campaign against Andrew Tate.
Their claim:
On February 6th, a paste was published by an anonymous user who claimed they have leaked data from Andrew Tate’s course selling website— therealworld.net:

Their “Proof”:
The anonymous user provided a sample of the “leak”, making it seem as though they hacked the database of Andrew Tate’s website and are now leaking it, the leak allegedly contains email addresses and plaintext passwords of the users:

Debunking their “proof”:
By searching the email address found in the sample (s.adhikari18@wlc.ac.uk), Hudson Rock was able to determine that the data shown is actually from historical Infostealer infections that are unrelated to any targeted breach related to Andrew Tate’s domain:

It is hard to tell the intentions of the user, it is apparent they were trying to contact Andrew Tate at some point and were ghosted. It is possible they were trying to blackmail Tate or simply trying to gain some recognition from him. However it is certain that by leaking the data there was an attempt to cause harm facilitated by disinformation.
Conclusion:
The misuse of infostealer credentials data stands out as a significant challenge.
As illustrated by recent events involving the Haghjoyan Hacking Group, the fraudulent sale of AnyDesk’s database, and the disinformation campaign against Andrew Tate, cybercriminals are increasingly leveraging stolen data to propagate misinformation, conduct scams, and manipulate public opinion.
These incidents underscore the complexity of the cybersecurity threats we face. The Haghjoyan group’s attempt to increase tensions during the Israel-Hamas conflict, the opportunistic claims around AnyDesk’s security breach, and the misleading allegations against Andrew Tate’s website reveal how threat actors are able to exploit the digital ecosystem for various nefarious purposes.
The key takeaway from these examples is the critical importance of data verification. Cybersecurity experts, companies, and the general public must be proactive in identifying and debunking false claims.
The reliance on comprehensive cybercrime intelligence databases, like the one maintained by Hudson Rock, is invaluable for verifying the authenticity of purported data breaches and infostealer campaigns.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock