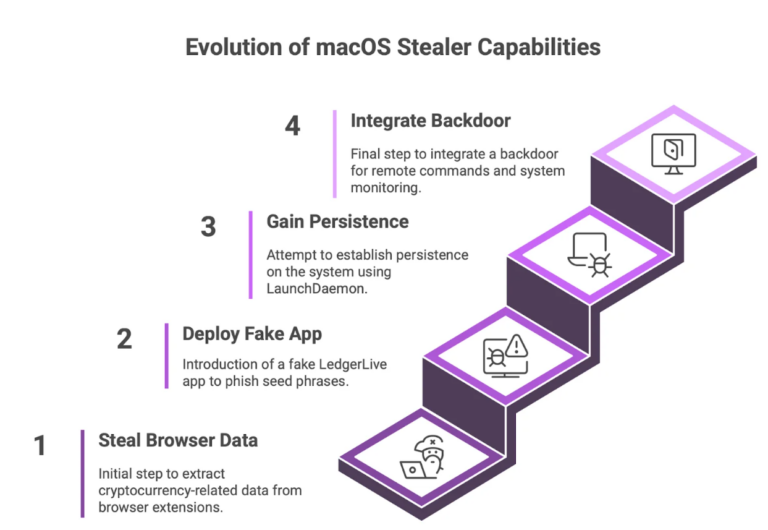
In the ever-evolving world of cybersecurity, staying ahead of emerging threats is crucial. One such threat that has been gaining traction is info stealers. These malicious programs are designed to harvest sensitive information from unsuspecting victims, posing significant risks to individuals and organizations. This article aims to shed light on the growing trend of info stealers, explore the types of information they target, and provide actionable insights to help security professionals mitigate these risks.
The Rise of Info Stealers
Info stealers have become a prominent tool in cybercriminals’ arsenal. Over the past few years, deploying these malware programs has seen a noticeable increase. According to recent statistics, the number of reported cases involving info stealers has surged by over 50% in the last year alone. This alarming trend underscores the need for heightened vigilance and proactive measures in cybersecurity.
For the past two years, we have been closely monitoring this trend. Over the last seven months, our research team has been actively collecting data from available sources. Our efforts have yielded a staggering collection of 315 million different types of credentials, including domain credentials, personal Gmail accounts, and more. Notably, we observed not only employee domain credentials but also credentials for Active Directory (AD) service accounts. Furthermore, following the approach detailed in this article, we identified credentials exposed to various third-party services such as CRMs, HRM systems, EDRs, and vulnerability management solutions. This substantial dataset highlights the scale at which info stealers operate and the diverse nature of the stolen information.
Example of info stealer’s log structure


How Info Stealers Work
At their core, info stealers are designed to infiltrate systems, extract valuable information, and transmit it back to the attackers. These programs often gain access through phishing emails, malicious downloads, or exploit kits. Once inside a system, they can capture a wide range of data, including:
· Login Credentials: Usernames and passwords for various online services.
· Personal Information: Names, addresses, phone numbers, and other identifying details.
· Financial Data: Credit card numbers, banking details, and transaction records.
· Service Credentials: AD service account credentials and credentials for third-party services like CRMs, HRM systems, EDRs, and vulnerability management solutions.


Impact Analysis
The impact of info stealers is far-reaching and global, affecting numerous countries and industries. Based on the statistics we’ve collected, the most affected countries include the following:
- Germany: More than 20 million credentials
- Brazil: 18 million credentials
- US: 12 million credentials
- India: More than 10 million credentials
- Turkey: Almost 10 million credentials
- Pakistan: Almost 9 million credentials
- Puerto Rico: 8.5 million credentials
- Egypt: 8 million credentials
and many others…
These figures illustrate the scale of the problem and highlight that info stealers are a worldwide threat, impacting diverse regions and populations. For instance, a notable case involved a significant healthcare provider in the US, where an info stealer managed to exfiltrate sensitive patient records, leading to significant financial and reputational damage. Such incidents underscore the urgent need for robust security measures and constant vigilance.
For Whom It Can Be Useful
Understanding the mechanics and impact of info stealers is essential for several key roles within the cybersecurity field:
- Security Engineers: Can use this knowledge to develop and implement more effective security protocols.
- Security Managers: Can better allocate resources and prioritize threats based on the latest trends.
- CISOs: Can make informed decisions about their organization’s cybersecurity strategy.
- Red Teamers: Can use the credentials from info stealer logs to simulate real-world attacks and demonstrate how easily initial access can be gained with compromised credentials.
By staying informed and applying the insights shared in this article, these professionals can enhance their defensive measures and contribute to a safer digital environment.
Conclusion
Info stealers represent a growing threat in the cyber realm, targeting a wide array of sensitive information and affecting numerous countries and industries. Our research has tracked this trend over the past 7 months and collected 315 million credentials — including those for AD service accounts and various third-party services — underscores this threat’s scale and global nature. Security professionals can better protect their systems and data by understanding how these malware programs operate and staying informed about the latest trends. Remember, the key to effective cybersecurity is responding to threats and anticipating and mitigating them before they can cause harm.
P.S
Some might think that having two-factor authentication (2FA) will protect them from these threats. While 2FA is a valuable security layer, it’s not foolproof.