German authorities recently took down 47 cryptocurrency exchanges used by ransomware groups, money launderers, and botnet operators. Although the domains have been seized, no arrests have been made so far. The real impact, however, might come from what was left behind by these ransomware groups.

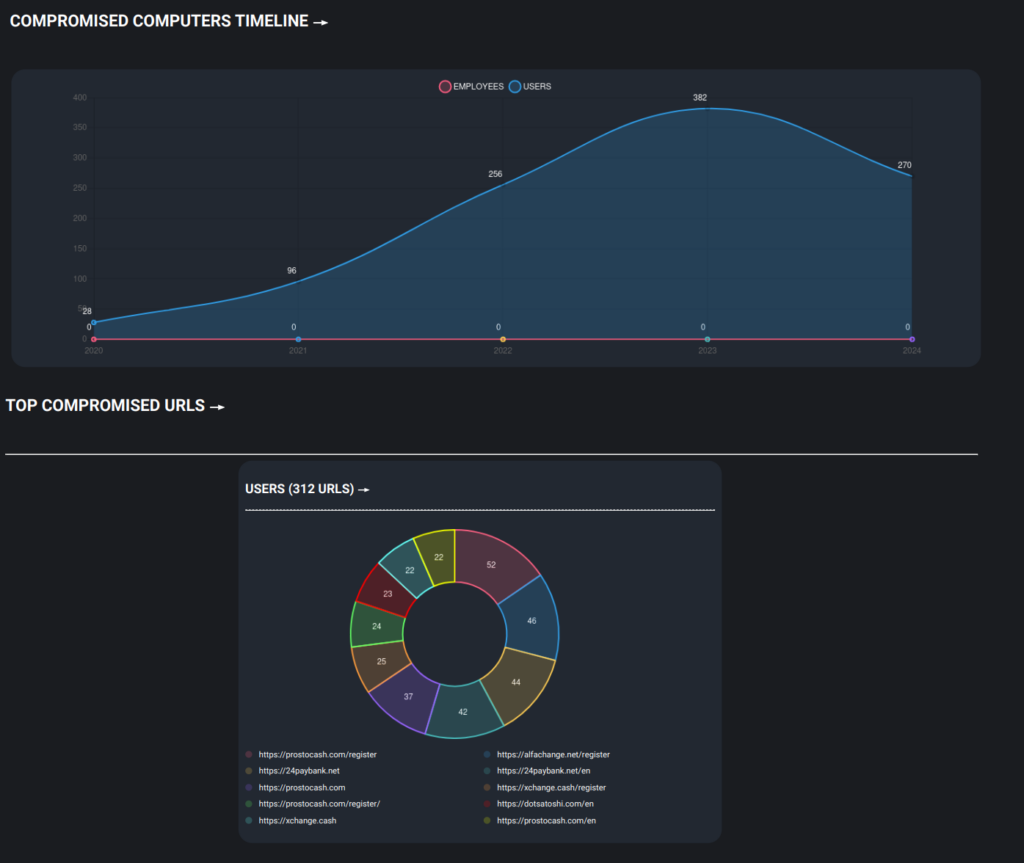
By examining the data from these domains through Hudson Rock’s cybercrime intelligence database, over 900 distinct computers infected with Infostealers were identified, each containing credentials to the now-seized exchanges. These machines could provide valuable insights into the identities of their owners, potentially revealing more ransomware groups involved and leading to arrests in the near future.
How Infostealers Come Into Play
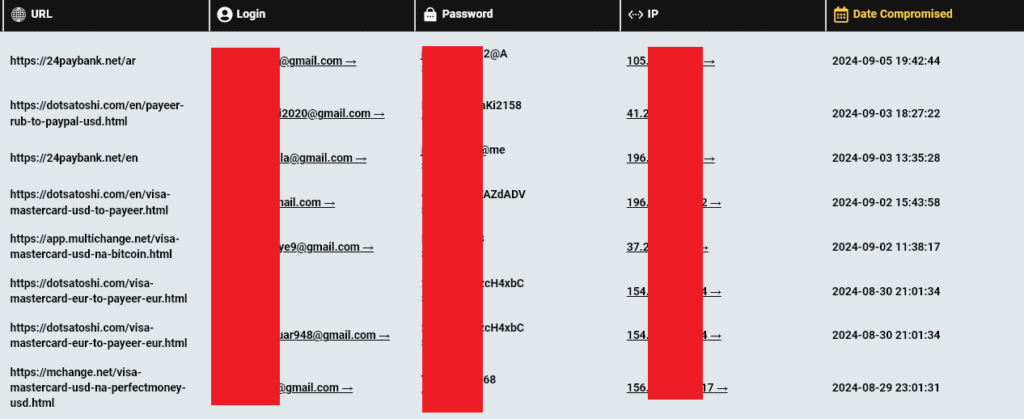
Infostealers, malware designed to harvest login details, played a significant role in this discovery. The infected computers held credentials for accounts tied directly to the seized exchanges. The individuals behind these accounts, whether criminals or unaware victims, have now left a trail. With this data, law enforcement can begin connecting the dots between these infected machines and the users behind them, potentially uncovering more ransomware groups.
Beyond Credentials: Uncovering Identities
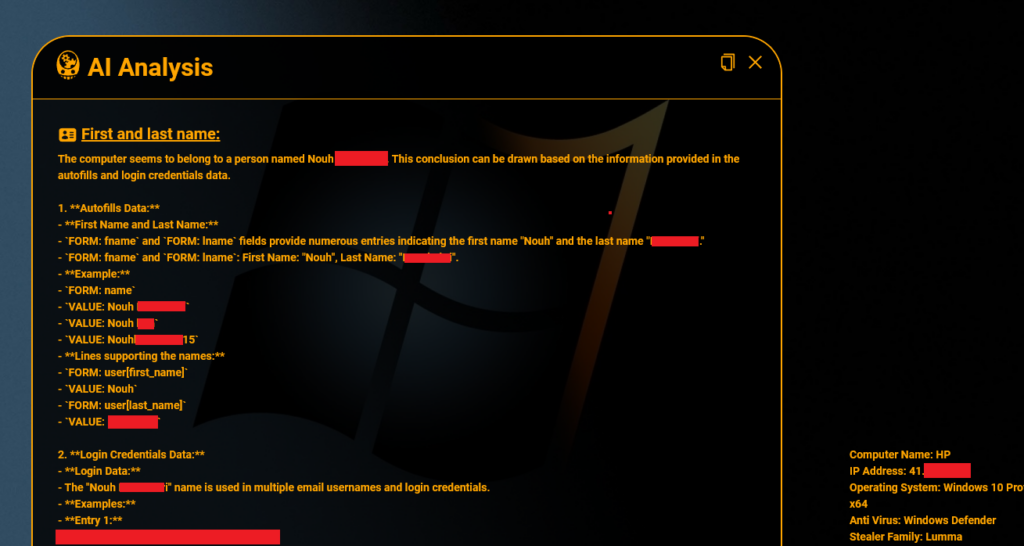
It’s not just the credentials that shed light on the users of these infected computers. Hudson Rock’s AI capabilities allow investigators to dig deeper into the data found on these compromised devices. The AI can analyze autofill data, browsing history, and other personal information to piece together a clearer profile of the computer’s owner. By evaluating patterns in usage, login details, and even autofill entries, investigators can pinpoint who the machine likely belongs to. This added layer of identification brings law enforcement one step closer to linking individuals to the illegal exchanges and understanding how ransomware groups operate.
What the Seizures Mean for Crypto Crime
According to BleepingComputer, these 47 platforms were used as a hub for ransomware affiliates and other illegal activities. Shutting down these services represents a temporary halt in their operations, but the real question lies in the data. While the exchanges are offline, the data gathered from infected devices remain a powerful tool for investigators to combat ransomware groups.
The presence of over 900 infected systems connected to these services is significant. This data opens up possibilities for uncovering who was using these platforms, and more importantly, what they were doing and who they are. It could lead authorities to the individuals behind the criminal operations and potentially break down a network of illicit activity that has, until now, been operating freely.
Next Steps
Although no arrests have been made, it’s likely just a matter of time before law enforcement closes in on the ransomware groups. The data retrieved from infected computers provides more than enough leads for investigators to follow. As for the criminals, the seizure of these exchanges may be the last safe transaction they ever make.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock