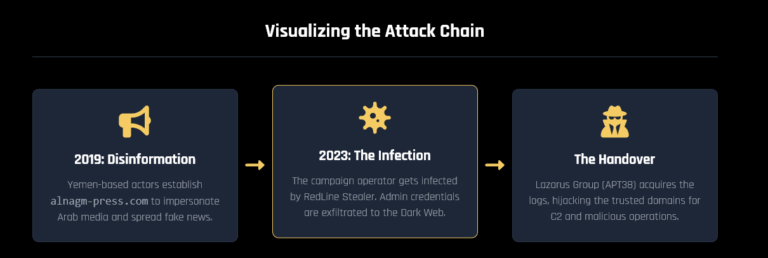
Disclaimer: Hudson Rock does not insinuate or imply responsibility or liability on behalf of any parties mentioned herein. The content is intended solely for informational purposes and reflects our findings at the time of publication. Hudson Rock disclaims any responsibility for how this information regarding Infostealer Infection may be interpreted or used by others.
Update 07/11/24 – Atlas Privacy obtained a copy of the Hot Topic database and allows users to search whether their email or phone were involved in the breach for free – https://databreach.com/breach/hot-topic
It is not every day that we see such a massive database being compromised. That’s why it’s important to analyze the stolen data, understand how it was stolen to prevent future incidents, and also understand the implications.
Let’s Begin.
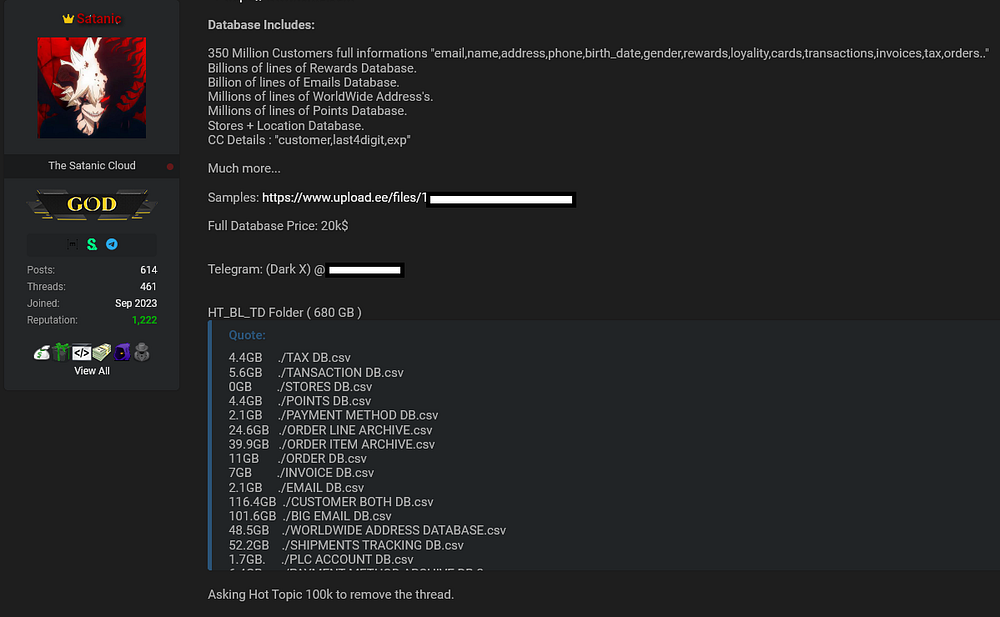
On October 21st, a prominent threat actor using the username “Satanic” posts a thread in which they seek to sell various databases relating to three major retail companies : Hot Topic, Torrid, and Box Lunch (all of which are founded by Hot Topic).
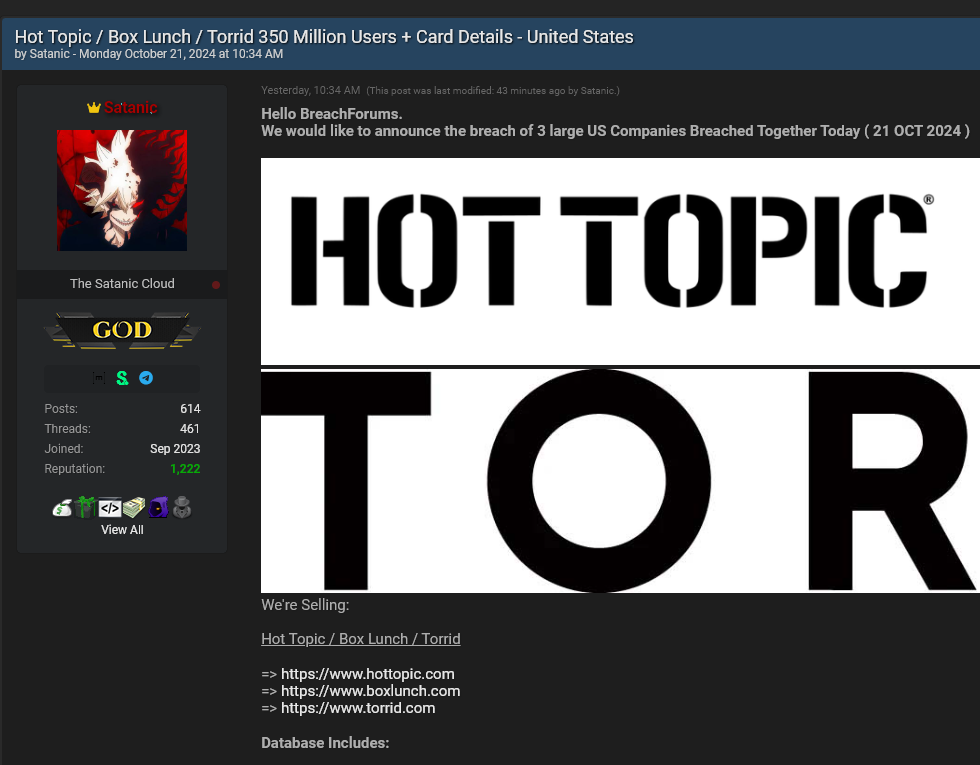
The threat actor goes into length explaining exactly what they say was stolen from these companies — we’re talking about A LOT of data:
- 350,000,000 customers’ PII, including names, emails, addresses, phone numbers, and birthdates.
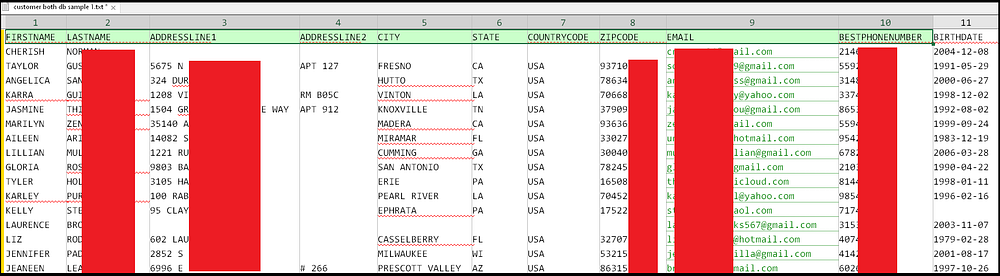
- Billions of payment details, including the last 4 digits of customers’ credit cards, card types, hashed expiration dates, and account holder names.
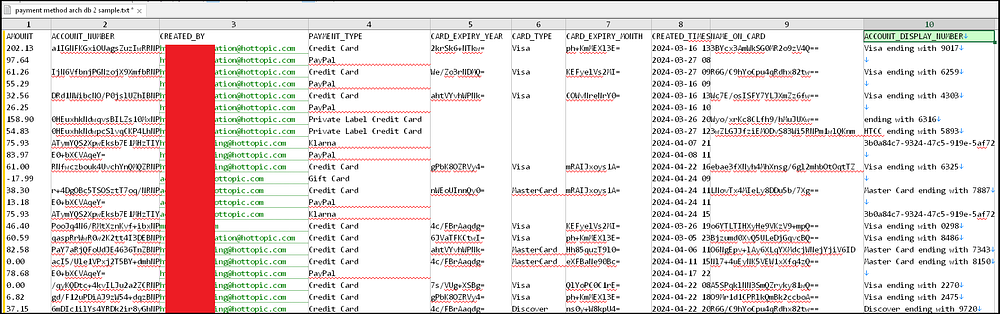
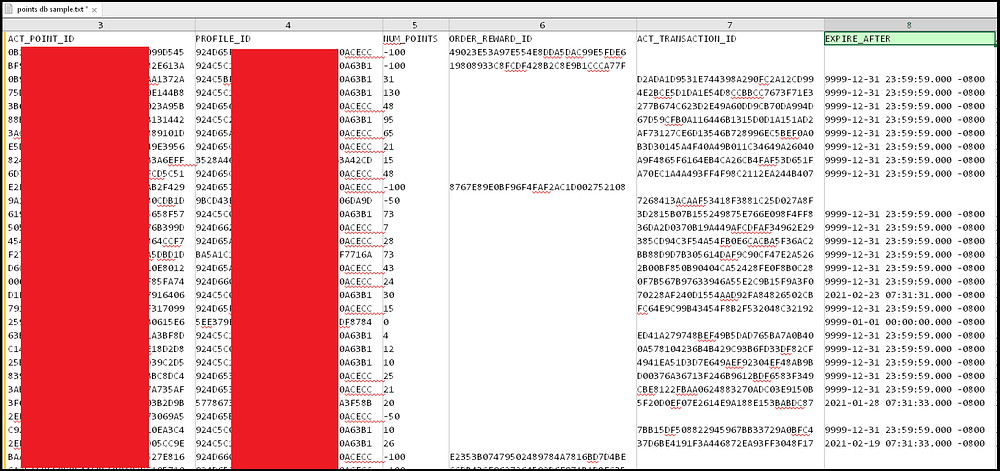
- Billions of loyalty points tied to Hot Topic & Box Lunch, linked to profile identifiers (PROFILE_ID). These points could be used by threat actors for account takeovers, especially since many of the points do not expire, as seen in the database.
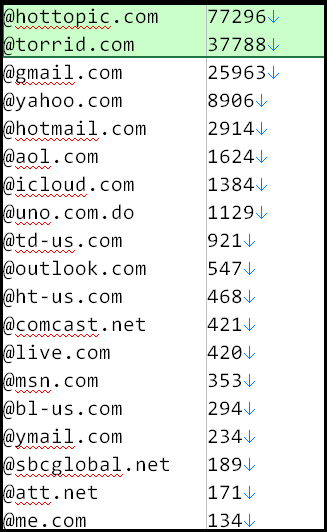
By aggregating all the emails from these leaks and examining the most common mail providers, Hudson Rock researchers found a significant number of Hot Topic and Torrid email addresses, indicating that the breach is likely indeed connected to these companies.
The threat actor is asking for $20,000 for the data, or alternatively $100,000 from Hot Topic to remove the thread.
So How Did this Huge Breach Even Happen..?
Infostealers
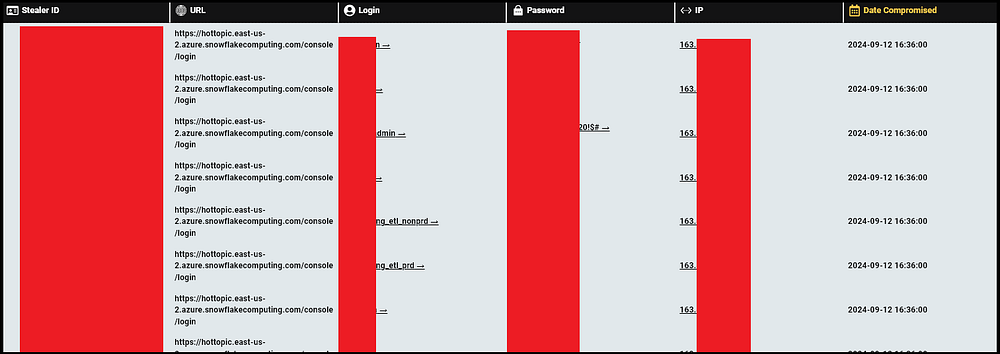
Hudson Rock’s researchers’ first clue was the possibility that Infostealers were involved in the breach. By searching the keyword “hottopic” in Hudson Rock’s Cavalier platform, researchers discovered an employee who was recently infected by an Infostealer on September 12th, 2024:
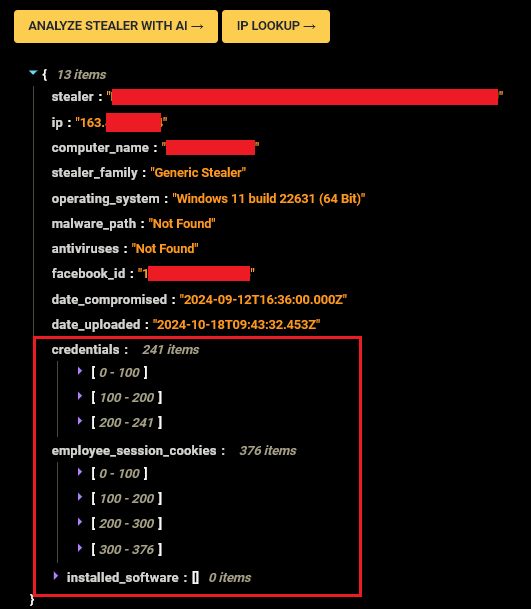
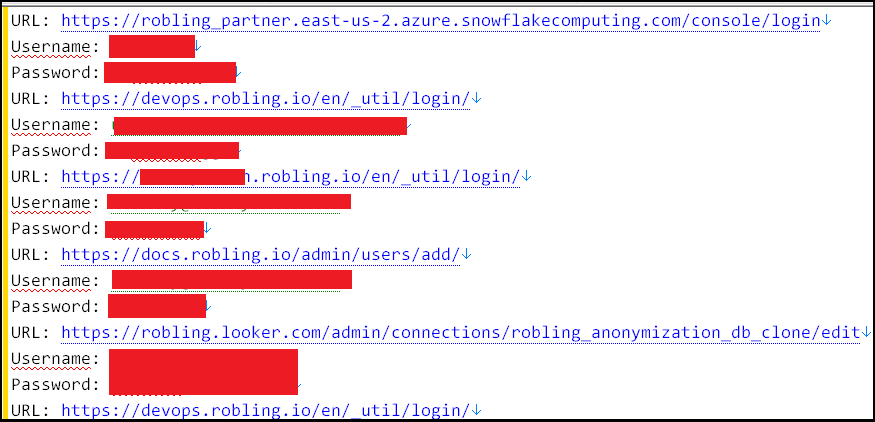
With over 240 credentials found on the machine, many of which are corporate, researchers determined that this person is employed at a company called “Robling”, whose description is “Helping retailers unite data across silos”.

This is aligned with the various accesses they had for this company:
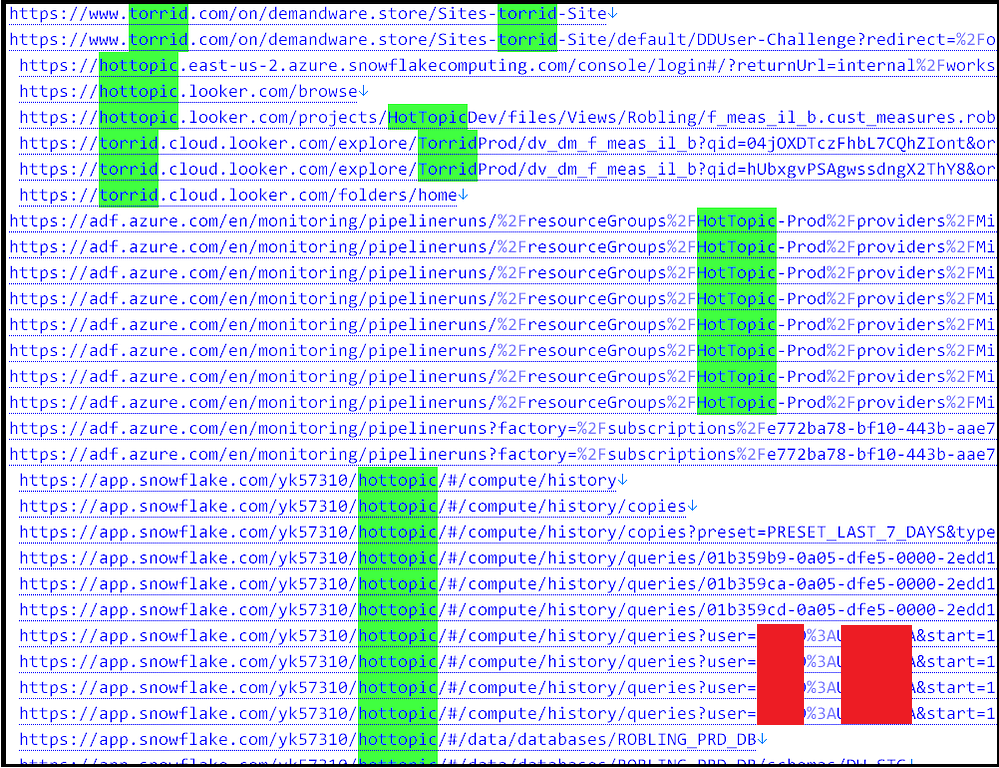
When looking for “Hottopic” and “Torrid” within the infected computer, researchers identified dozens of credentials associated with corporate URLs related to Hot Topic and Torrid’s environment on Snowflake and Looker (Google Cloud):
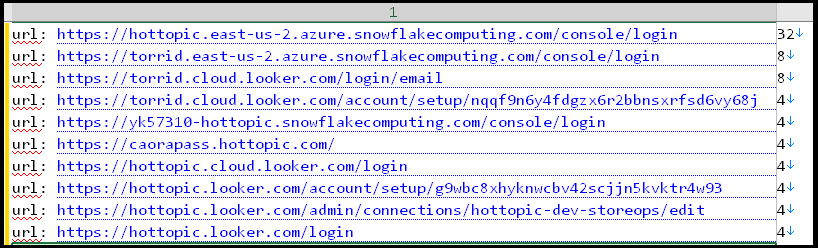
In addition to this, the browsing history of the employee was full of similar references, indicating sensitive accesses within services related to Hot Topic and Torrid in Snowflakecomputing(.)com, Azure(.)com, and Looker(.)com, cloud services are known to have been involved in prior infostealer related breaches.
Conversation With Satanic
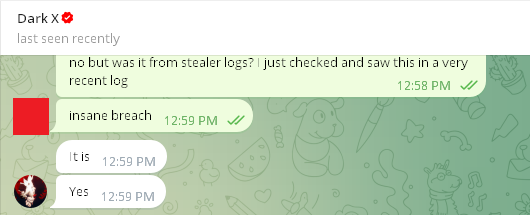
While this evidence alone doesn’t conclusively prove how these companies were hacked, Hudson Rock’s researchers reached out to “Satanic” for more details.
“Satanic” first claimed that the breach originated from an Infostealer log:
They provided a username matching the one found on the computer our researchers were investigating:
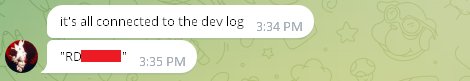
By searching this specific username across the infected computer, researchers identified it was primarily associated with Snowflake-related URLs for Hot Topic and Torrid, along with corresponding credentials.
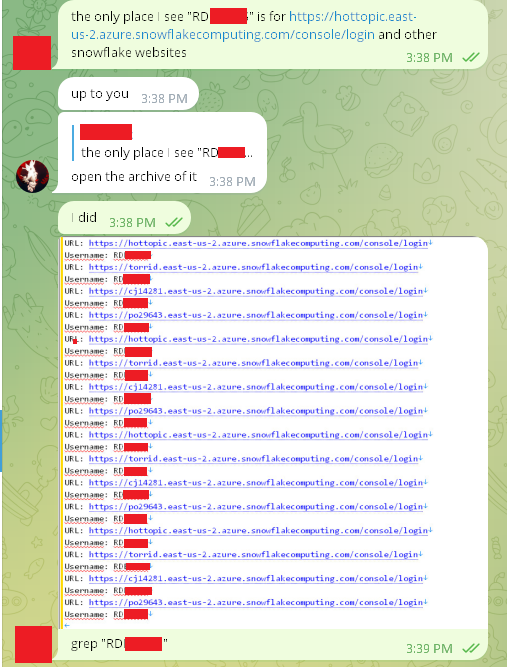
Lastly, Satanic claimed, we emphasize, the hacker CLAIMED, that the breach originated from a lack of MFA on a Snowflake account along with “other links”:
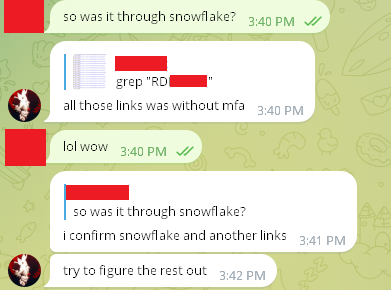
While we can’t determine conclusively whether the hacker is speaking the truth, our evidence is supported by the following:
- The sample evidence shared from the impacted companies appears to be aligned with the claims.
- The recent infection of an employee carrying the relevant privileges to enable such a breach at Hot Topic.
- “Satanic” is operating an Infostealer logs selling service, showing they are using Infostealers on a daily basis.
- The reputation of “Satanic” in the hacking community indicates they are able to carry out such breaches.
According to all of these, we strongly believe that this information is likely true.
Note that Hudson Rock attempted to reach out to Hot Topic and Robling, but has received no answer yet.
Conclusion
The stolen data from this breach — including personal information, payment details, and loyalty points — can be exploited by hackers for identity theft, financial fraud, and account takeovers.
The scale of this breach not only threatens individuals but also undermines trust in the affected companies, making it a significant reminder of the risks posed by Infostealer infections.
This year Infostealers served as the most powerful initial attack vector used by cybercriminals. They aided in the hacks of some of the world’s biggest companies including AT&T, Orange, Ticketmaster, Airbus.
In fact, 3 out of the top 5 most devastating breaches in 2024 were as a result of Infostealers according to a Kiteworks report:
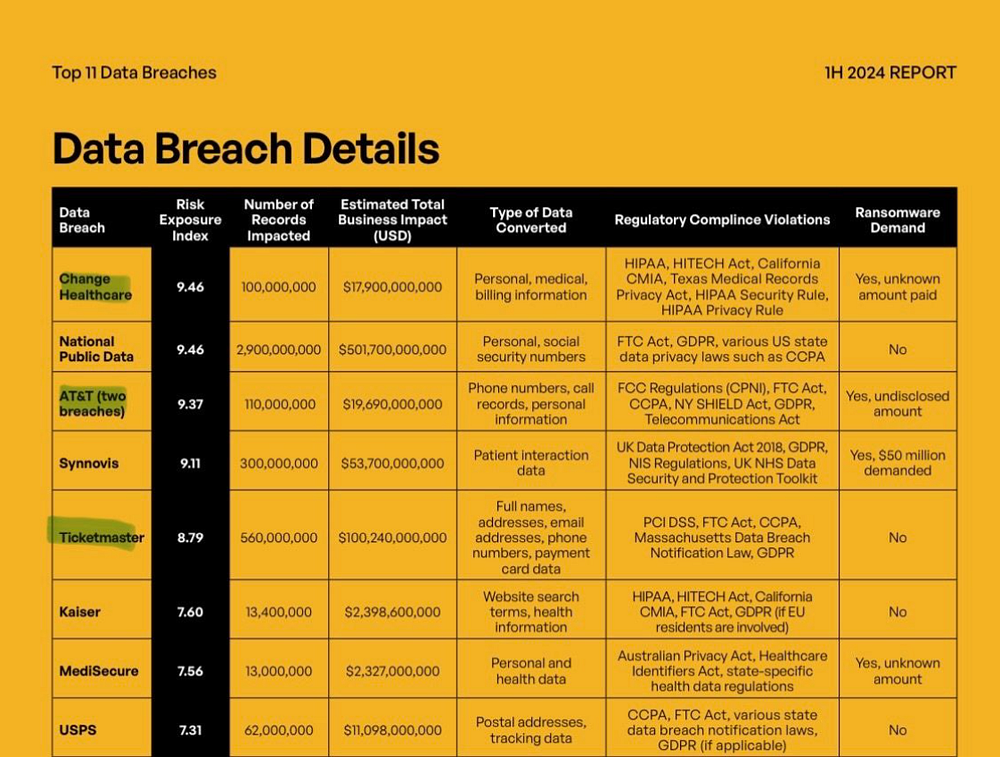
To learn more about how Hudson Rock protects companies from imminent intrusions caused by Infostealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading — Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock