Free Infostealer Intelligence Tools by Hudson Rock – www.hudsonrock.com/free-tools
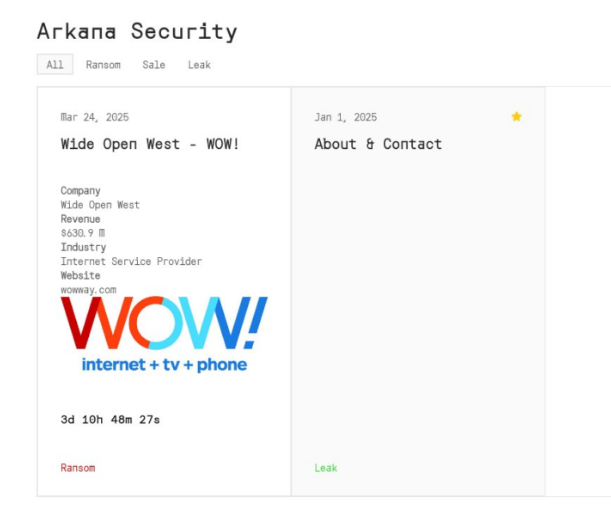
On November 4th, Schneider Electric acknowledged a data breach in which hackers stole 40GB of data from the company’s Jira server.
“Schneider Electric is investigating a cybersecurity incident involving unauthorized access to one of our internal project execution tracking platforms which is hosted within an isolated environment,” Schneider Electric told BleepingComputer.
The company was apparently targeted by a new ransomware group named “HellCat,” which consists of several prominent hackers, including “grep,” who previously hacked Dell and Capgemini.
The group demands $125,000 to delete the data and prevent its public release.

The Infostealer Connection
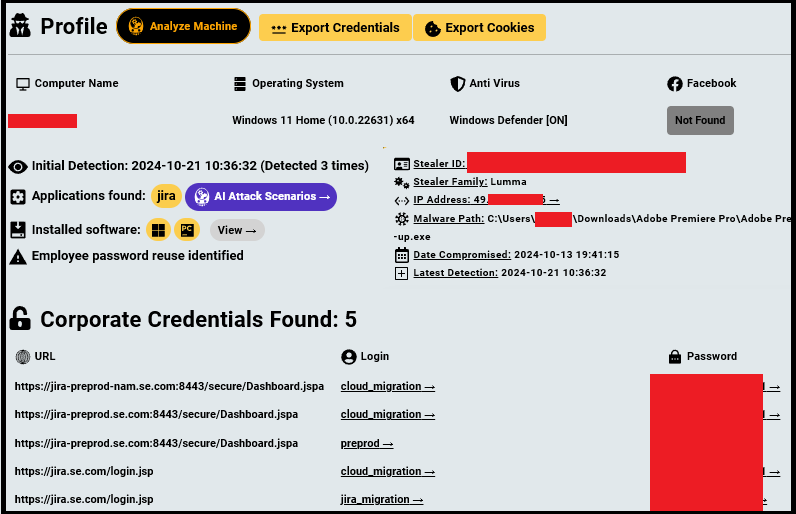
Hudson Rock researchers identified a Schneider Electric employee infected by Lumma Infostealer on October 13, 2024. The employee, who appears to be based in India, was likely infected while attempting to download a cracked version of Adobe Premiere from a YouTube video.
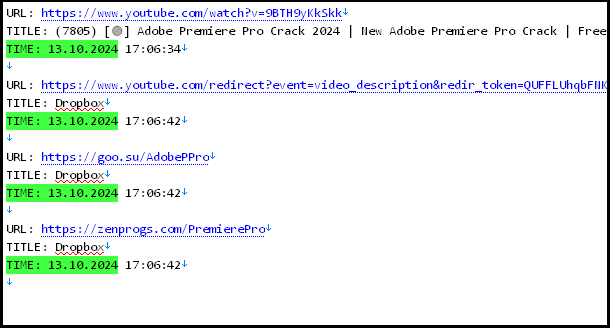
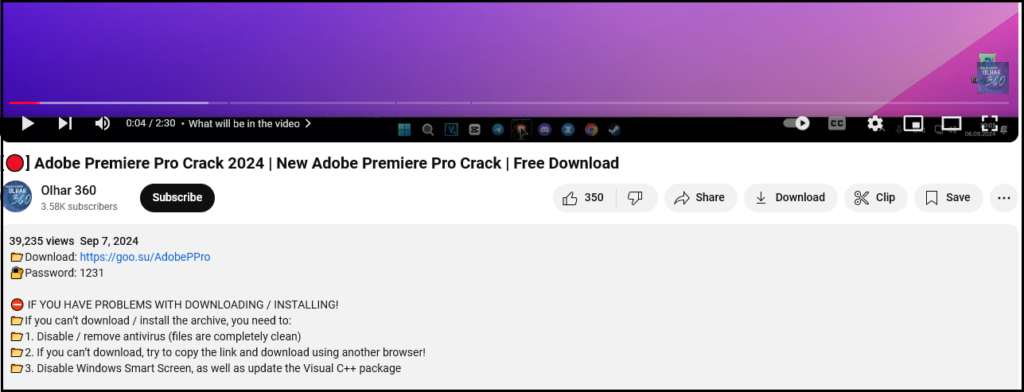
In a conversation with BleepingComputer, Grep said they breached Schneider Electric’s Jira server using exposed credentials. Once they gained access, they claimed to use a MiniOrange REST API to scrape 400k rows of user data, which Grep says includes 75,000 unique email addresses and full names for Schneider Electric employees and customers.
When investigating these claims, researchers found a direct match between Grep’s assertions and credentials on the compromised computer, Hudson Rock had these credentials ahead of the breach and it was highly preventable –
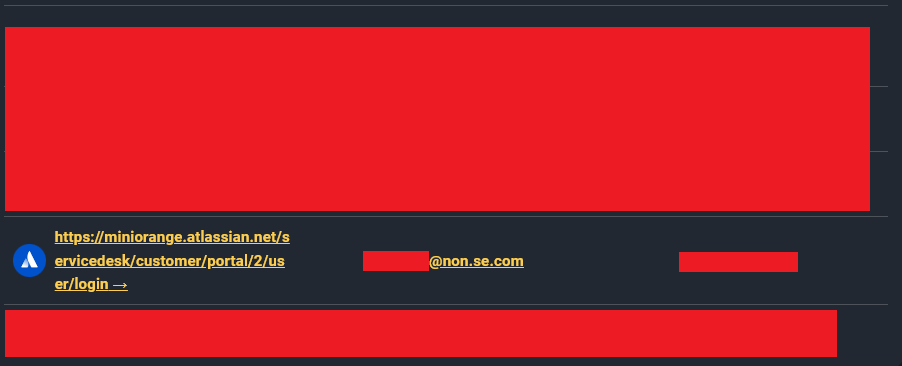
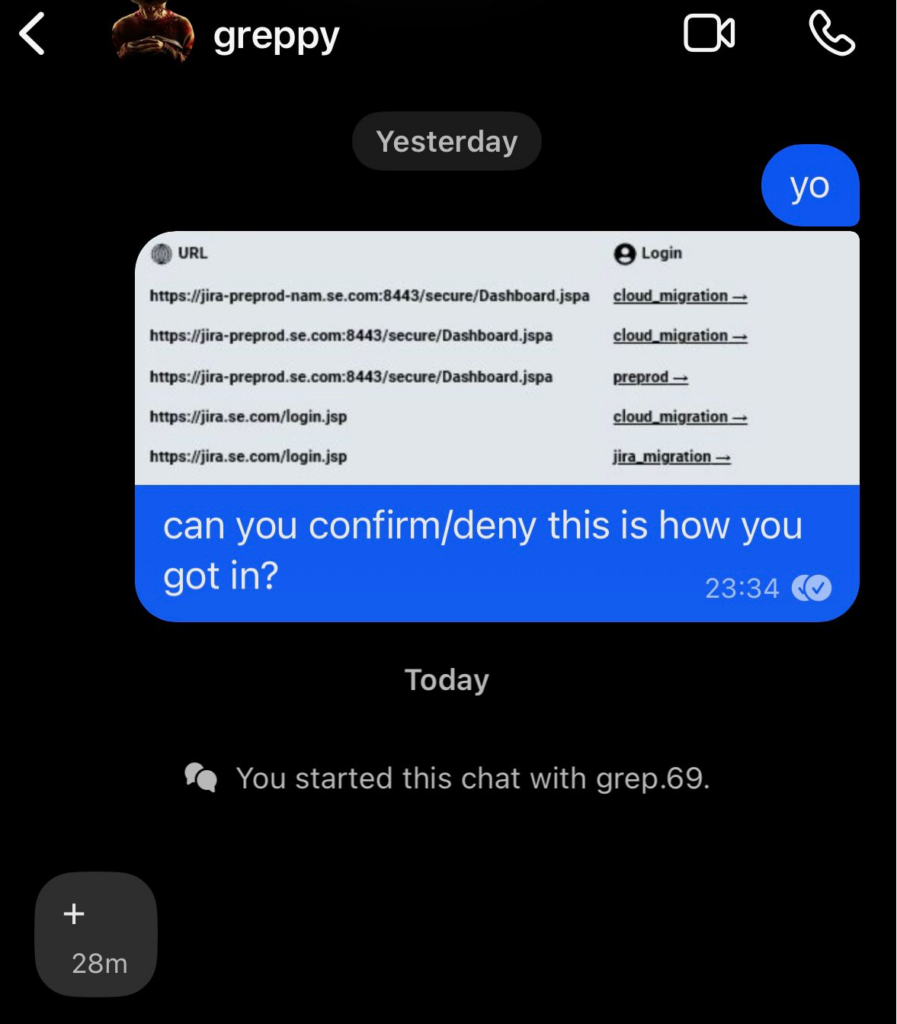
Additionally, the employee’s computer held other sensitive Jira-related credentials belonging to the organization, with usernames like “cloud_migration” and “jira_migration” and an associated password which is too embarrassing to share (believe us).
Speaking to the threat actor they provided researchers with confirmation

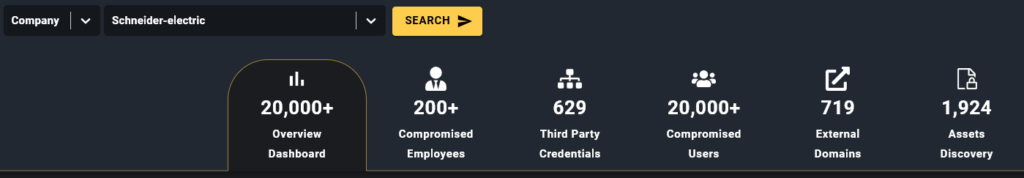
Schneider Electric has hundreds of employees who were infected by Infostealers over the years, many of them with sensitive credentials and accesses, along with bad passwords, and lack of anti-viruses installed, demonstrating a poor cyber hygiene at the company.
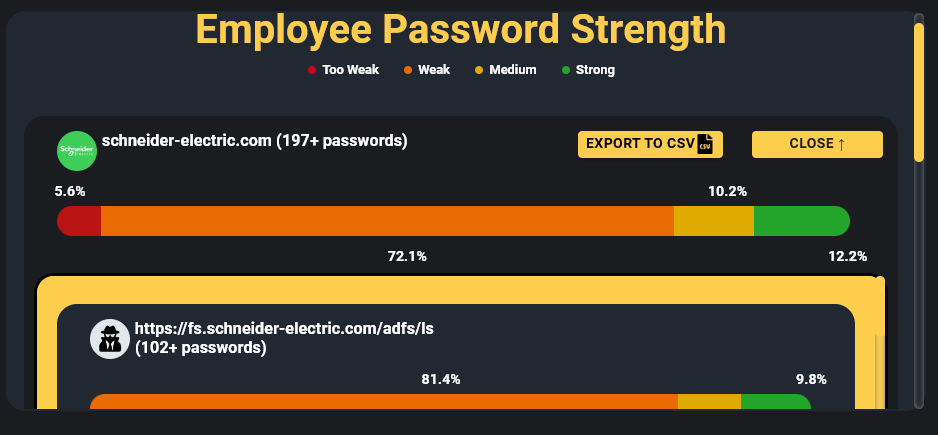
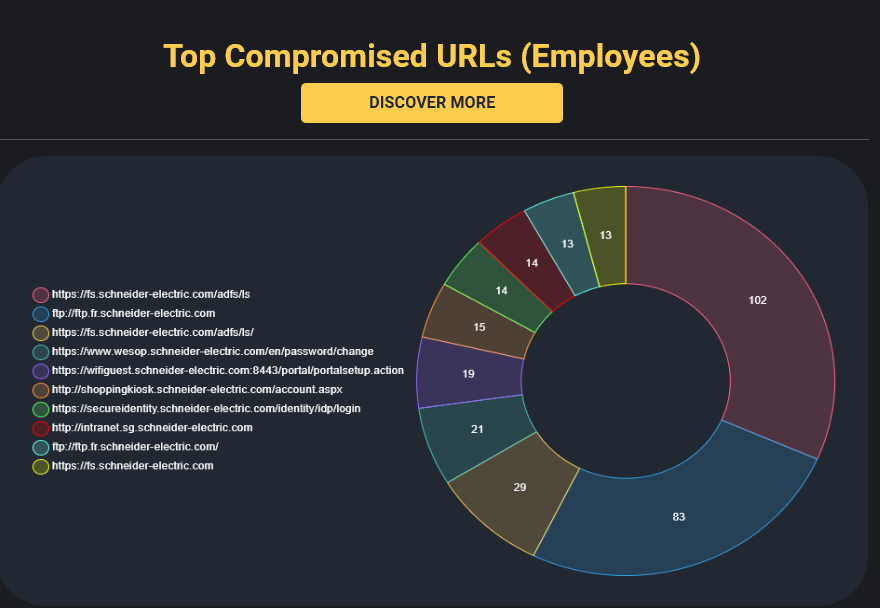
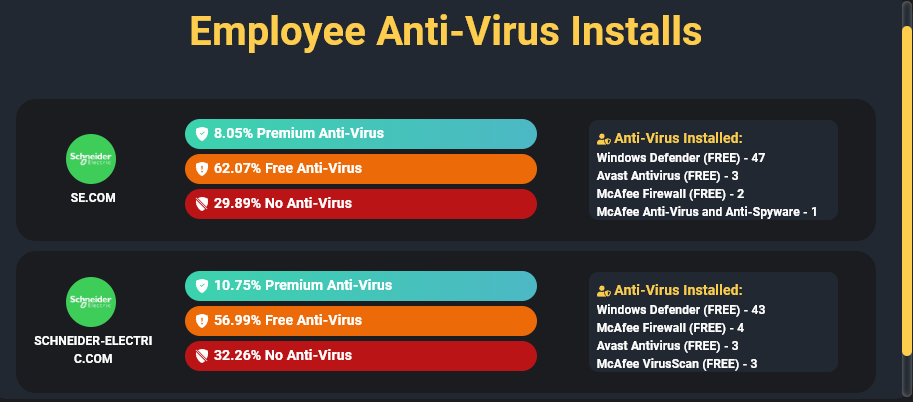
Collaborative tools such as JIRA, Confluence, and others pose significant risks for organizations today, as they are heavily targeted by hackers due to the wealth of information stored within them. We highlighted this in a previous research report titled ‘How Hackers Really Used Infostealers for the Biggest Recent Cyber Breaches.’
Conclusion
Infostealers are a real and growing threat, enabling hackers to execute significant breaches across major organizations. By exploiting weak points like webmail and VPNs, they gain access to sensitive data and systems, as seen in recent attacks on companies like Snowflake and EA Sports.
To combat this, organizations must strengthen their cybersecurity measures, such as implementing multi-factor authentication and educating employees about safe practices. Utilizing Hudson Rock’s threat intelligence can provide invaluable insights into compromised credentials and real-time notifications, helping companies proactively address vulnerabilities before they lead to breaches.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock