In a recent interview given to Osint10x , “Pryx”, the admin of the Hellcat Ransomware Group, shared insights into their methods, their vision for the future of infostealers, and how server-side innovations are reshaping the game.
Breaking Down the Traditional Infostealer Model
Traditionally, infostealers rely on client-side operations, with malicious payloads deployed directly on victim machines. These stealers scrape sensitive data — such as credentials, cookies, and session tokens — and exfiltrate it back to the threat actor. However, this approach comes with limitations:
- Detection Risks: Malware execution on endpoints increases the likelihood of detection by antivirus or EDR (Endpoint Detection and Response) solutions.
- Operational Bottlenecks: The need to distribute payloads at scale often results in inconsistencies in infection rates and quality of stolen data.
- Short Lifespan: Stealers typically lose effectiveness quickly as indicators of compromise (IOCs) are shared within threat intelligence communities.
Pryx’s Server-Side Revolution
Pryx’s approach flips this model on its head. Instead of relying solely on client-side stealers, Pryx emphasizes the power of server-side stealers. Unlike traditional methods that operate fully on the victim’s device, Pryx’s innovation introduces a stealthier, more efficient alternative:
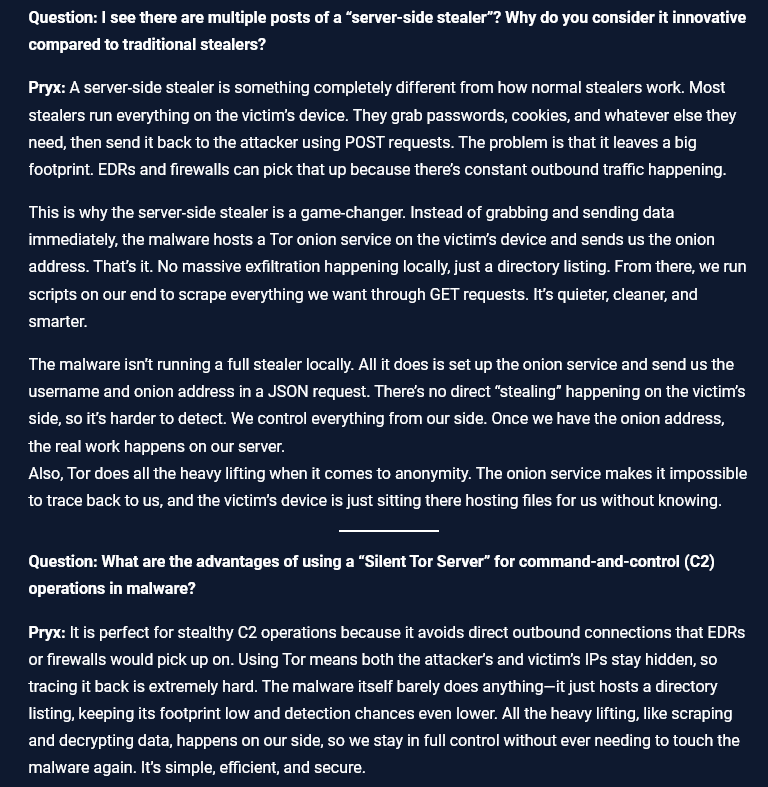
- Silent Persistence: The malware doesn’t immediately exfiltrate data. Instead, it sets up a Tor onion service on the victim’s device and sends only the onion address and username back to the attacker via a small JSON request. This drastically reduces detectable outbound traffic.
- Remote Control: Once the onion service is established, the real data harvesting occurs on the attacker’s server. Scripts on their end use GET requests to quietly scrape files, credentials, and sensitive data hosted on the victim’s device. The victim remains unaware as their device acts like a passive file host.
- Anonymity and Stealth: By leveraging Tor’s onion routing, both the victim and attacker remain effectively untraceable. The attacker’s operations leave minimal footprints, and traditional detection systems struggle to flag such low-activity malware.
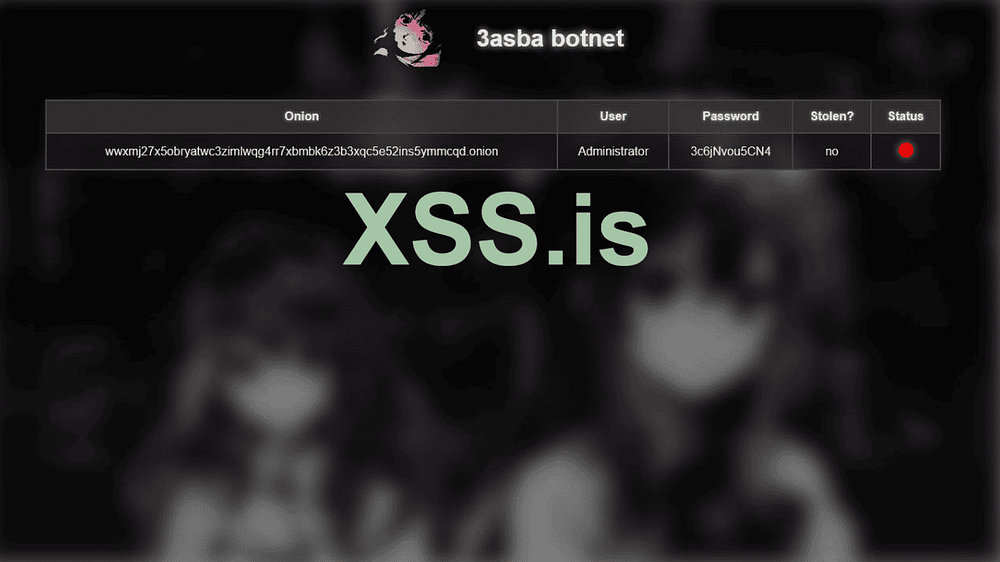
Pryx elaborates: “Most stealers grab passwords, cookies, and whatever else they need directly from the victim’s device, sending it back via POST requests. That’s noisy and easy to spot. The server-side stealer is different. It’s quieter, cleaner, and smarter. The malware does almost nothing locally, just sets up the onion service. All the heavy lifting happens on our side.”
The Vision for Infostealers 2.0
According to Pryx, the future of infostealers lies in modular, hybrid approaches that combine client-side precision with server-side stealth. For example, a lightweight client-side payload could initiate access, while server-side modules execute advanced data exfiltration. This two-pronged strategy minimizes risk while maximizing impact.
In the interview, Pryx detailed several techniques that are shaping this new era:
- Browser-Less Credential Harvesting: Instead of relying on browser-specific stealers, these new tools directly interact with backend systems to extract credentials stored in encrypted databases or cloud environments.
- Token Hijacking on Steroids: By targeting server configurations, attackers can hijack OAuth or API tokens directly from cloud dashboards, enabling them to bypass multi-factor authentication (MFA).
- Adversary-in-the-Middle (AiTM) Enhancements: Server-side AiTM techniques allow for real-time interception and manipulation of user sessions, further reducing reliance on endpoint compromise.
Monetizing Innovation
As an Initial Access Broker (IAB), Pryx’s innovations not only enhance the effectiveness of infostealers but also create lucrative opportunities within the cybercriminal ecosystem. By selling access to compromised servers pre-loaded with server-side stealers, Pryx has positioned themselves as a critical enabler for ransomware groups, financial fraud rings, and APTs (Advanced Persistent Threats).
This model also underscores the symbiotic relationship between infostealers and ransomware groups. By delivering high-quality credentials and privileged access, Pryx’s operations significantly reduce the reconnaissance phase for ransomware operators, accelerating their attacks and improving profitability.
The Ethical Hacker’s Nightmare
Pryx’s methods are a stark reminder of the challenges faced by ethical hackers and security researchers. Traditional mitigation strategies like endpoint protection and user education are insufficient against server-side stealers. Organizations must now adopt a more proactive stance, including:
- Infostealer Logs Monitoring: Actively analyzing logs from known infostealer campaigns to identify patterns or evidence of compromise.
- Continuous Monitoring of Server Logs: Detecting anomalous behavior within server environments.
- Zero-Trust Architecture: Limiting lateral movement and access within networks.
- Cloud-Specific Security Solutions: Implementing tools designed to monitor and protect cloud workloads.
What’s Next for Pryx and the Hellcat Group?
When asked about their long-term goals, Pryx was unapologetically candid: “The goal isn’t just to innovate but to dominate. We’re not interested in small wins. This is about reshaping how cybercrime operates.”
The Hellcat Group’s focus on modularity, automation, and server-side tactics is setting the stage for a new generation of infostealers that are harder to detect, harder to mitigate, and far more effective. For defenders, the stakes have never been higher.
Conclusion
Pryx’s approach represents a paradigm shift in the infostealer ecosystem. By leveraging server-side techniques and modular strategies, they’re not just keeping up with the evolution of cybersecurity defenses — they’re actively staying ahead.
Researchers: watch this space. The next wave of infostealers is here, and it’s changing everything.
To learn about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock