Botnets Are Dead, Long Live Infostealers (A Comparison)
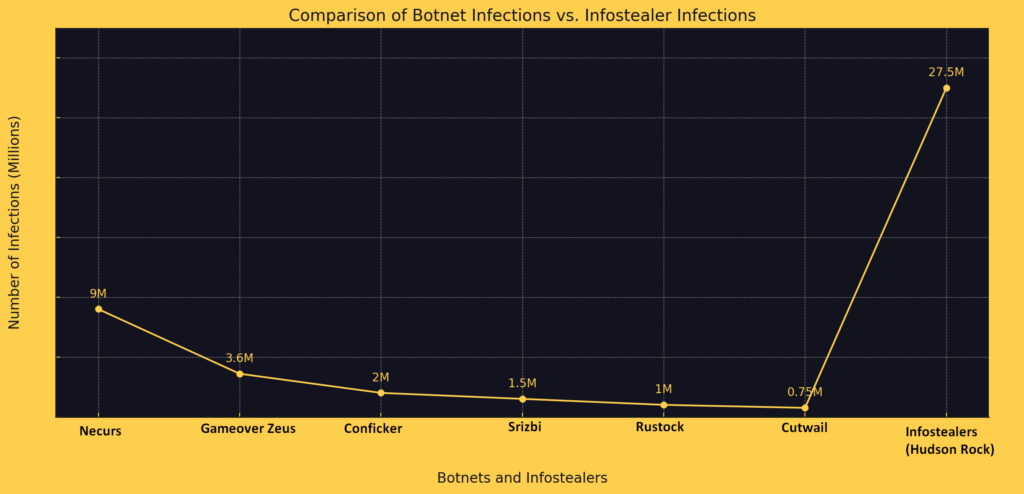
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of malware: Infostealers. According to Hudson Rock’s cybercrime intelligence database, which tracks historical data on Infostealer infections, there have been 27,500,000 recorded instances of these attacks. This staggering number highlights the growing […]
Analysis of APT attack cases targeting domestic companies using Dora RAT (Andariel Group)
AhnLab SEcurity intelligence Center (ASEC) recently confirmed cases of APT attacks by the Andariel group targeting domestic companies and institutions. The organizations identified as targets of the attack were domestic manufacturing companies, construction companies, and educational institutions, and backdoors as well as keyloggers, infostealers, and proxy tools were used in the attacks. It is believed […]
An Infostealer’s Brewin’: Cuckoo & AtomicStealer Get Creative

Summary So far, 2024 really has been the year of the infostealer when it comes to macOS malware. Families like AtomicStealer, Cuckoo, and CloudJump are getting dumped like crazy from search engine ads and crack sites. This post examines a particularly sneaky typosquatting campaign that’s being used to deliver both AtomicStealer and Cuckoo. It makes […]
Initial Access Brokers, Infostealers, and Everything Between Them

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This attack not only led to business disruption but also resulted in a ransom payment of $22 million. The likely cause was an employee being infected with Infostealing malware. To demonstrate […]
Identity Behind Massive Discord Spying Tool Revealed due to Infostealer Infection
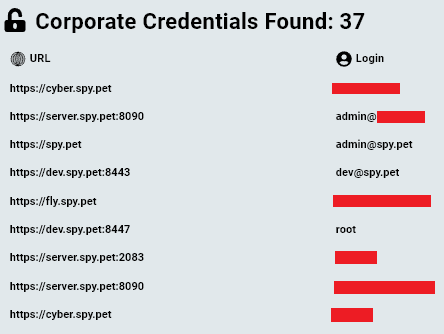
This article aims to shed light on the identity behind a massive Discord spying tool and raise concerns about the possibility of private Discord data being accessed by hackers. Intro A controversy surrounding the anonymously-run website spy.pet has recently made headlines, raising serious privacy concerns. The website is designed to enable anyone to access messages […]
Single Citrix Compromised Credential Results in $22,000,000 Ransom to Change Healthcare
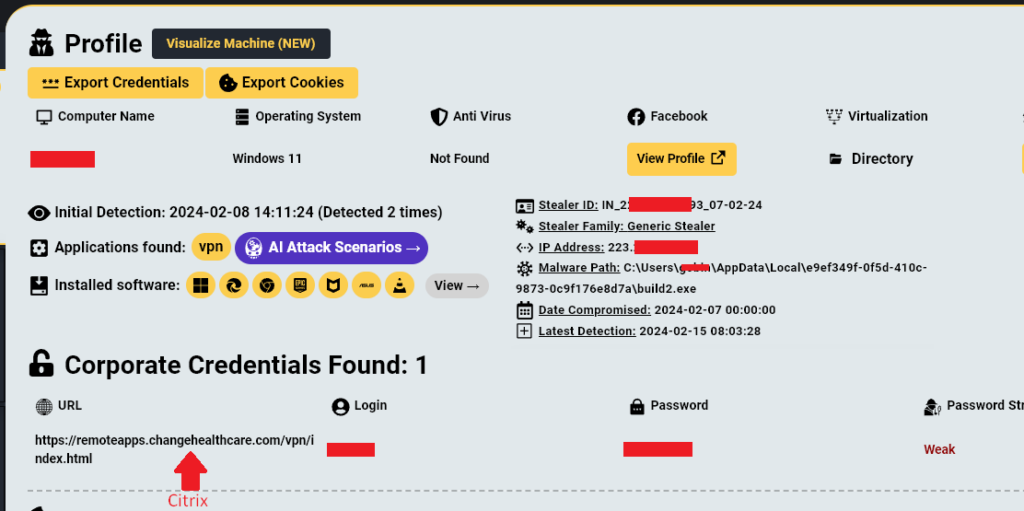
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000 The attack which was carried out by BlackCat ransomware group also resulted in a $22,000,000 ransom payment. But how did this happen? In a testimony by Andrew Witty, Change Healthcare’s […]
Distribution of Infostealer Made With Electron
AhnLab SEcurity intelligence Center (ASEC) has discovered an Infostealer strain made with Electron. Electron is a framework that allows one to develop apps using JavaScript, HTML, and CSS. Discord and Microsoft VSCode are major examples of applications made with Electron. Apps made with Electron are packaged and usually distributed in Nullsoft Scriptable Install System (NSIS) […]
Redline Stealer: A Novel Approach
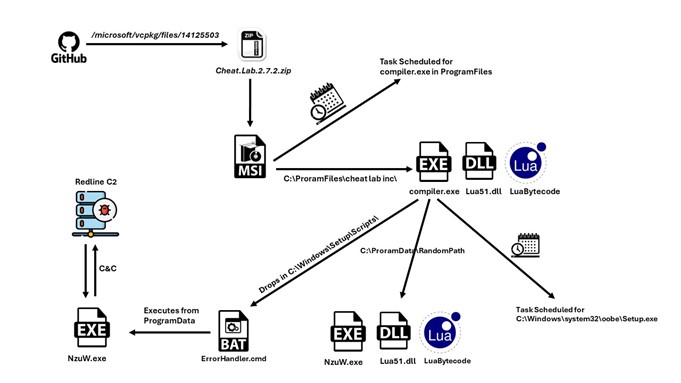
A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this malware strain is very prevalent, covering North America, South America, Europe, and Asia and reaching Australia. Infection Chain Source: Add a Custom Script to Windows Setup | Microsoft Learn We can […]
CoralRaider targets victims’ data and social media accounts

CoralRaider operators likely based in Vietnam Talos assesses with high confidence that the CoralRaider operators are based in Vietnam, based on the actor messages in their Telegram C2 bot channels and language preference in naming their bots, PDB strings, and other Vietnamese words hardcoded in their payload binaries. The actor’s IP address is located in […]
Activision: Enable 2FA to secure accounts recently stolen by malware

An infostealer malware campaign has collected millions of logins from users of various gaming websites, including players that use cheats, pay-to-cheat services. The details emerged after Zebleer, the developer of Phantom Overlay cheats for Call of Duty and Counter-Strike, apparently found an infostealer database. “The DB for the stealer represents gaming related accounts much more than […]
PyPI halts new projects, users for 10 hours due to infostealer influx

A few hours ago, The Python Package Index (PyPi) suspended new project creation and new user registration to mitigate an ongoing malware upload campaign. The research team of Checkmarx simultaneously investigated a campaign of multiple malicious packages appear to be related to the same threat actors. The threat actors target victims with Typosquatting attack technique […]
Extra credit: VietCredCare information stealer takes aim at Vietnamese businesses

Group-IB discovers new information stealer targeting Vietnam with rare functionality to filter out Facebook accounts with advertising credits…


