Compromising Google Accounts: Malwares Exploiting Undocumented OAuth2 Functionality for session hijacking.

A detailed blog on Analysis of the Global Malware Trend: Exploiting Undocumented OAuth2 Functionality to Regenerate Google Service Cookies Regardless of IP or Password Reset…
Epsilon infostealer spread via fan-made indie game expansion.

Installation of Epsilon infostealer enabled exfiltration of browser-stored data, including passwords, credit cards, and cookies and more…
Novice Rugmi Loader Delivers Various Spyware.

The threat landscape meets a new player – Rugmi Loader. This threat specializes in spreading spyware, and is in fact capable of delivering any malware type…
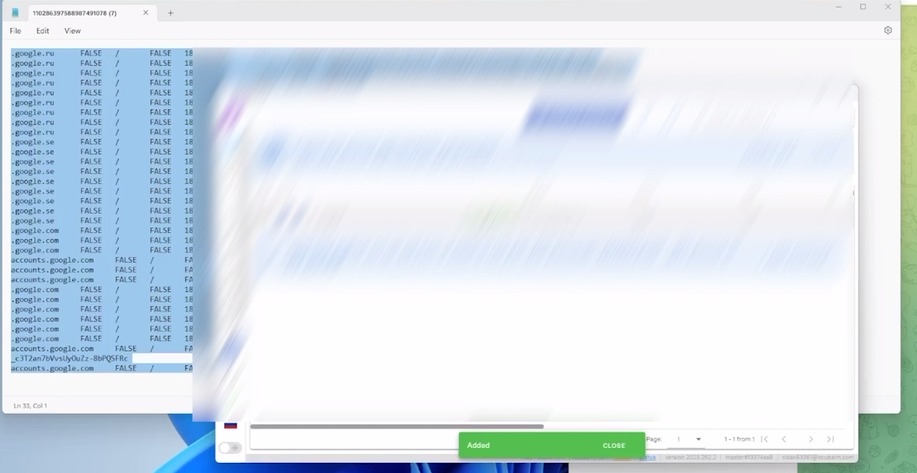
Breaking through the Infostealer Exploit and the Enigma of Cookie Restoration.
The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Pure Logs Stealer Fails to Impress.

Pure Logs Stealer first appeared on hacking forums at the end of October 2022. The stealer is developed by a malware developer…
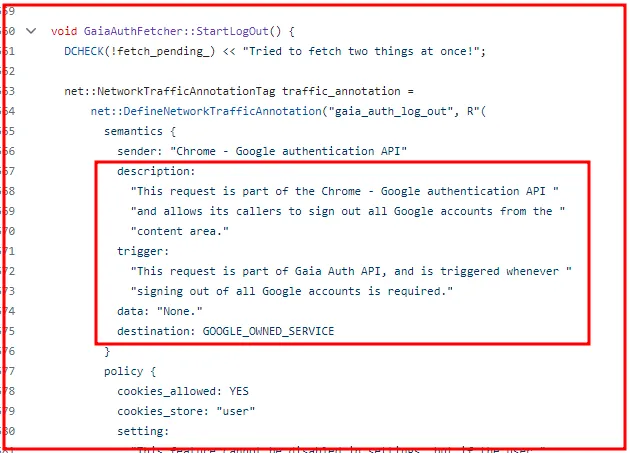
The Google 0-day all Infostealer groups are exploiting.
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…
Healthcare and Finance Suffer Most Cyberattacks.

During the summer of 2023, cyberattacks rose significantly, according to data from the new quarterly BlackBerry Global Threat Intelligence Report, November 2023 edition…
Windows, macOS targeted by novel JaskaGO infostealer.

Windows and macOS systems have been subjected to attacks leveraging the novel Go-based information-stealing malware JaskaGO, reports The Hacker News…
8220 gang exploits old Oracle WebLogic vulnerability to deliver infostealers, cryptominers.
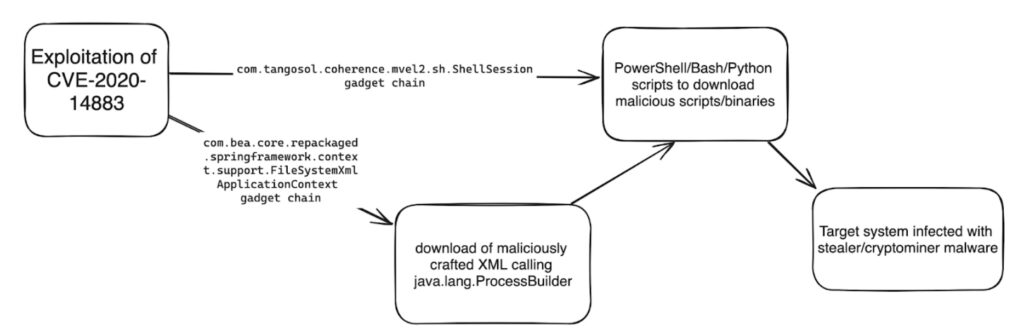
The 8220 gang has been leveraging an old Oracle WebLogic Server vulnerability (CVE-2020-14883) to distribute malware, the Imperva Threat Research team has found…
Hacker Sells Access to Binance’s Law Enforcement Portal.
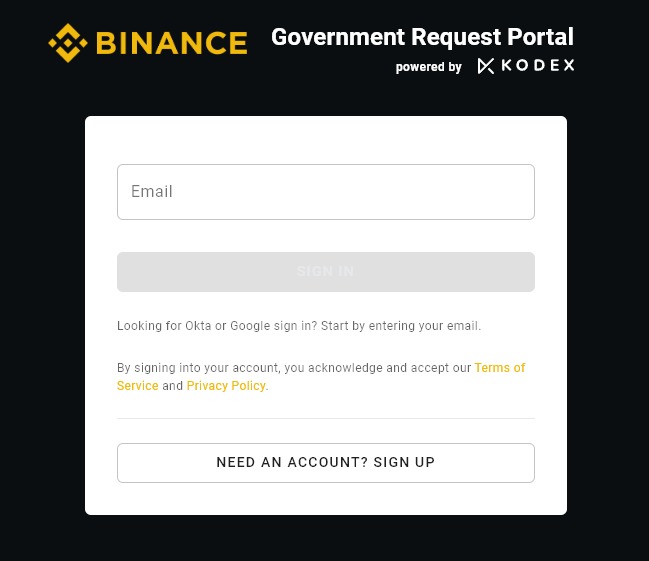
A threat actor attempts to sell access to a sensitive area of Binance — the major cryptocurrency exchange’s…
Hacker Uses Infostealer Data to Gain Access to Brazil’s Police Portal.
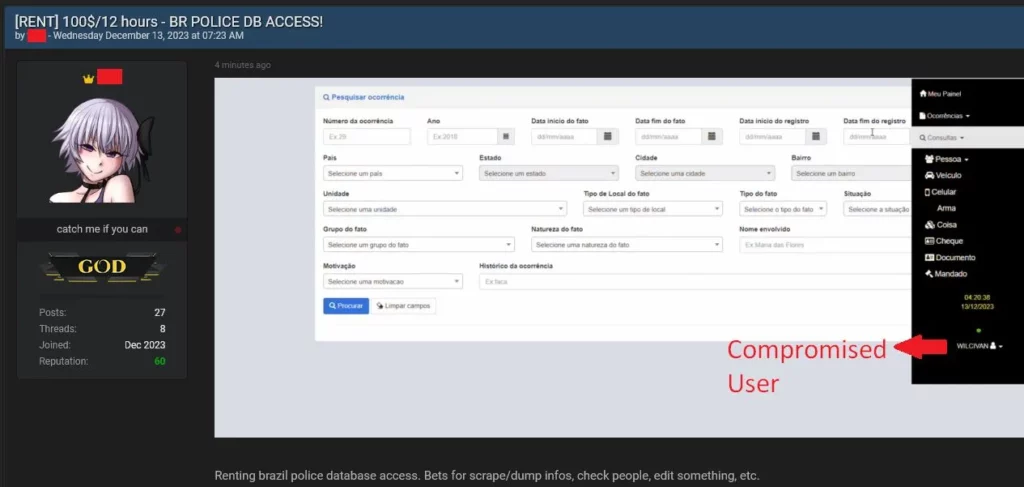
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…
Infostealer Credentials Compromise Password Managers, Posing Identity and Financial Theft Risks.
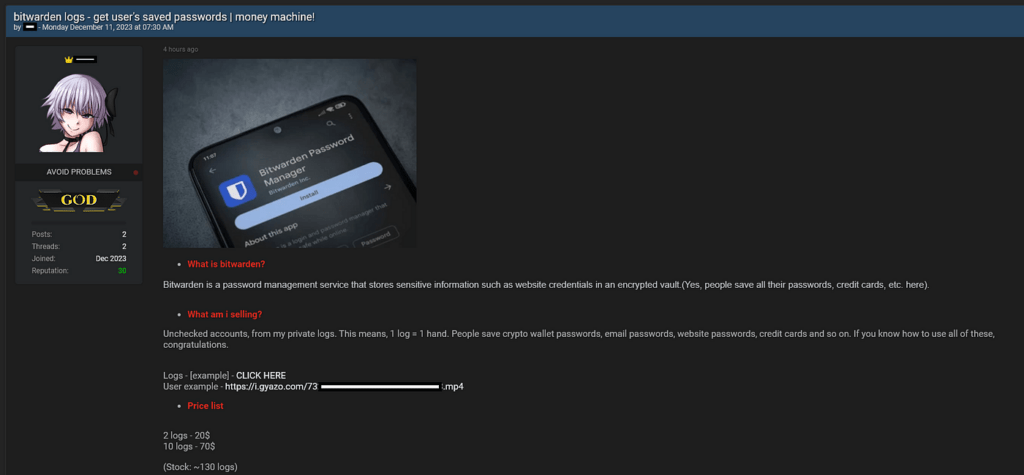
In today’s digital landscape, the reliance on password managers has become commonplace, providing users with a sense of security…


