Lumma infostealer malware operation disrupted, 2,300 domains seized

Earlier this month, a coordinated disruption action targeting the Lumma malware-as-a-service (MaaS) information stealer operation seized thousands of domains and part of its infrastructure backbone worldwide. This effort involved multiple tech companies and law enforcement authorities, resulting in Microsoft’s seizure of approximately 2,300 domains after legal action against the malware on May 13, 2025. At the […]
Stealing the Future: Infostealers Power Cybercrime in 2025

By [Alon Gal] | April 2025 Infostealers have become a cornerstone of cybercrime in 2025, infiltrating systems to steal credentials and sensitive data, enabling devastating follow-on attacks. This article for Infostealers.com synthesizes insights from Verizon’s 2025 Data Breach Investigations Report (DBIR), IBM’s X-Force Threat Intelligence Index 2025, and perspectives from cybersecurity leaders like Check Point, Hudson Rock, Huntress, Recorded Future, CrowdStrike, SpyCloud, Sophos, and Mandiant. It […]
HELLCAT Ransomware Group Strikes Again: Four New Victims Breached via Jira Credentials from Infostealer Logs

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting four new organizations: HighWire Press, Asseco, Racami, and LeoVegas Group. Hudson Rock has been tracking HellCat’s activities since their emergence. Research conducted by Hudson Rock confirms that all four breaches […]
Royal Mail Group Loses 144GB to Infostealers: Same Samsung Hacker, Same 2021 Infostealer Log
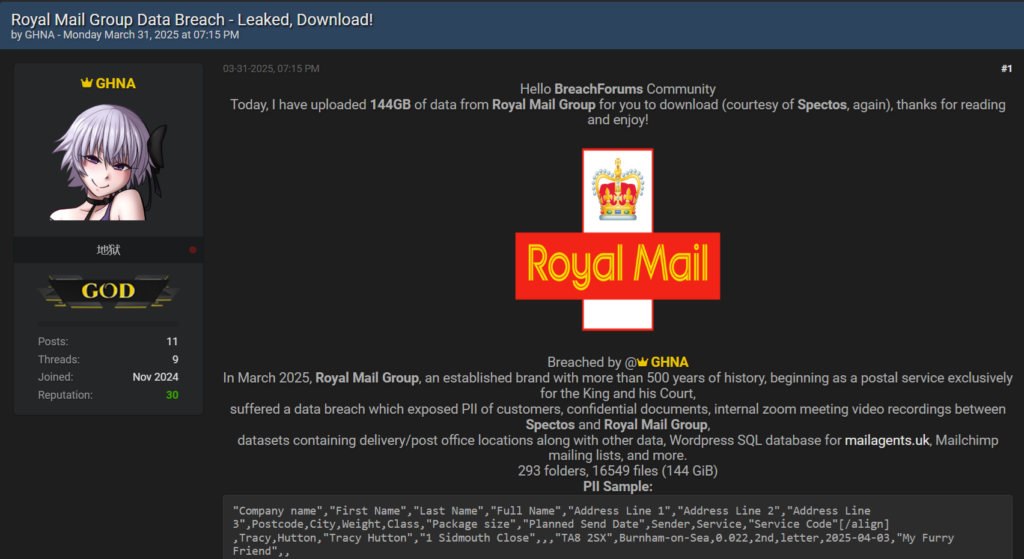
By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail Group, a British institution with over 500 years of history. On April 2, 2025, a threat actor known as “GHNA” posted on BreachForums, announcing the release of 144GB of data […]
Samsung Tickets Data Leak: Infostealers Strike Again in Massive Free Dump
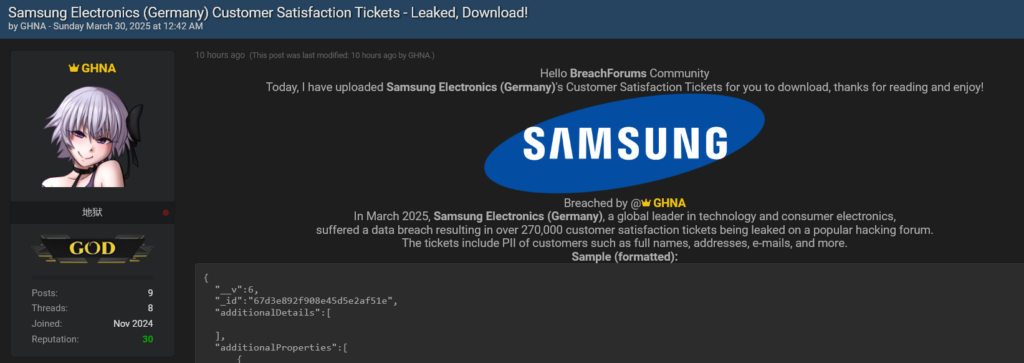
By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the alias “GHNA” has dumped a staggering 270,000 customer tickets from Samsung Germany online, completely free of charge. The data, which appears to be sourced from samsung-shop.spectos.com, didn’t come from some […]
StreamElements Confirms Third-Party Data Breach from an Infostealer Infection

By [Alon Gal] | March 2025 StreamElements, a popular cloud-based streaming platform, has confirmed a significant data breach involving a third-party service provider, following reports of stolen data being offered for sale on a hacking forum. The breach, which potentially impacts over 100,000 individuals, exposed sensitive information including names, addresses, phone numbers, and emails. New details […]
Arkana Ransomware Group Hacks WideOpenWest Using Data from an Infostealer Infection
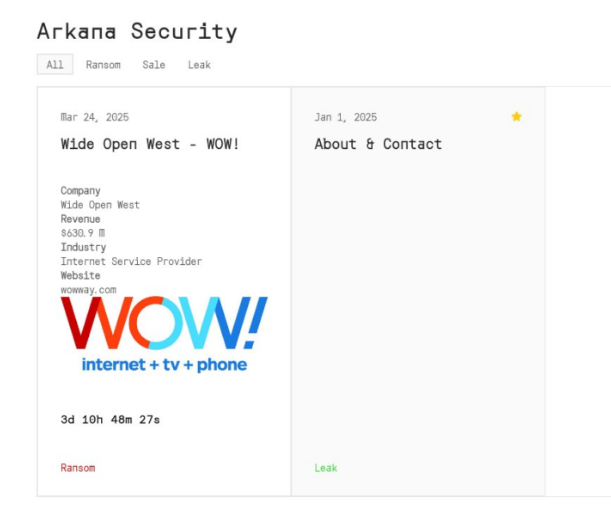
In yet another reminder of the dangers posed by infostealer malware, the emerging Arkana ransomware group has claimed responsibility for a massive breach of WideOpenWest (WOW!), one of the largest Internet Service Providers (ISPs) in the United States. The attack, which Hudson Rock researchers trace its origins to an infostealer infection back in September 2024, […]
The Information Heist: Cracking the Code on Infostealers (New Hudson Rock Interview)
🔊 *Hudson Rock* is back with a new podcast episode! In this episode, Leonid Rozenberg, cybercrime and threat intelligence researcher, speaks with Kevin Poireault from Infosecurity Magazine Magazine about the Infostealer landscape in 2025. While Infostealers are still harvesting passwords and cookies, Leonid dives into additional malware features such as: 🔹 File-grabbing module🔹 Credit card […]
Jaguar Land Rover Breached by HELLCAT Ransomware Group Using Its Infostealer Playbook—Then a Second Hacker Strikes
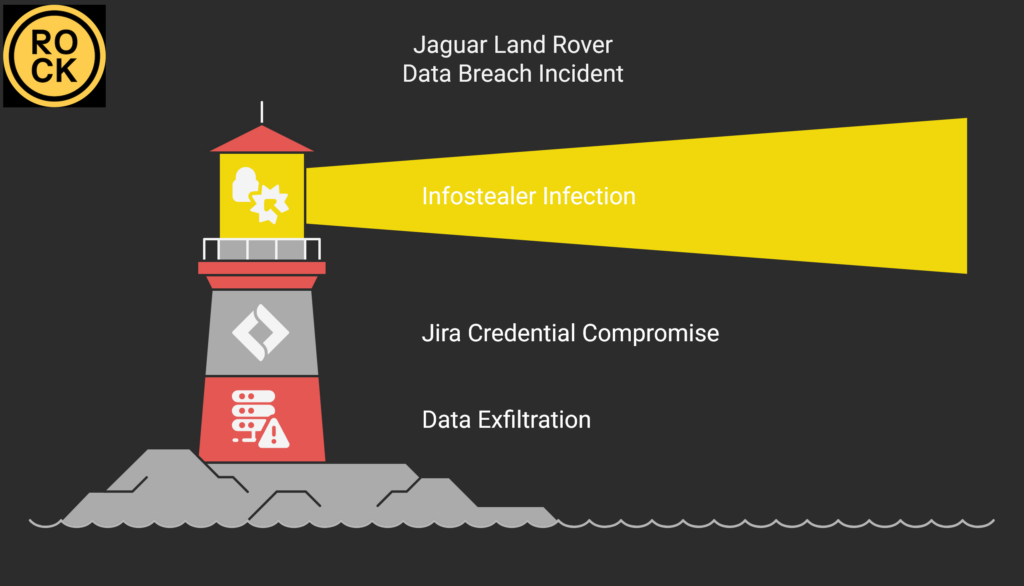
By [Alon Gal] | March 2025 In a repeat of a now-familiar playbook, the HELLCAT ransomware group has claimed responsibility for a massive data breach targeting Jaguar Land Rover (JLR), leaking gigabytes of sensitive information including proprietary documents, source codes, and employee and partner data. The breach, executed by a threat actor known as “Rey,” mirrors […]
One Million Devices Infected: Hackers Use Malvertising and GitHub to Spread Infostealers
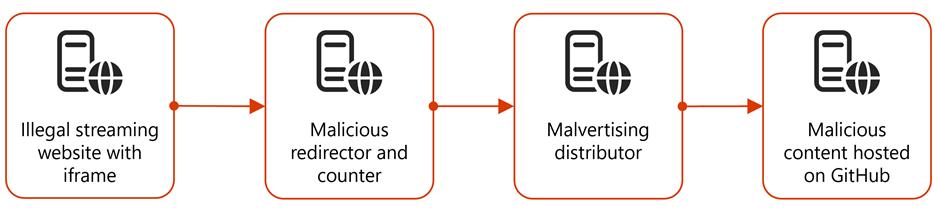
In early December 2024, Microsoft Threat Intelligence detected a large-scale malvertising campaign that impacted nearly one million devices globally in an opportunistic attack to steal information. The attack originated from illegal streaming websites embedded with malvertising redirectors, leading to an intermediary website where the user was then redirected to GitHub and two other platforms. The […]
Microsoft Research Reveals – Phishing Campaign Impersonates Booking(.)com, Delivers a Suite of Credential-Stealing Malware

Starting in December 2024, leading up to some of the busiest travel days, Microsoft Threat Intelligence identified a phishing campaign that impersonates online travel agency Booking.com and targets organizations in the hospitality industry. The campaign uses a social engineering technique called ClickFix to deliver multiple credential-stealing malware in order to conduct financial fraud and theft. […]
AI’s Role in Turning Massive Data Leaks into Hacker Paydays: A Look at the Orange Breach
By [Alon Gal] | March 2025 Breaches like Orange, Schneider Electric, and Telefonica often start with a simple infostealer stealing JIRA or Confluence credentials (signature HELLCAT group initial attack vector). From there, it’s a straight shot to pulling heaps of data from internal servers. Companies tend to downplay these leaks—“no big deal, just some files”—while the […]


