One in Four Cyberattacks in 2024 Traced to Infostealers, Huntress Reports
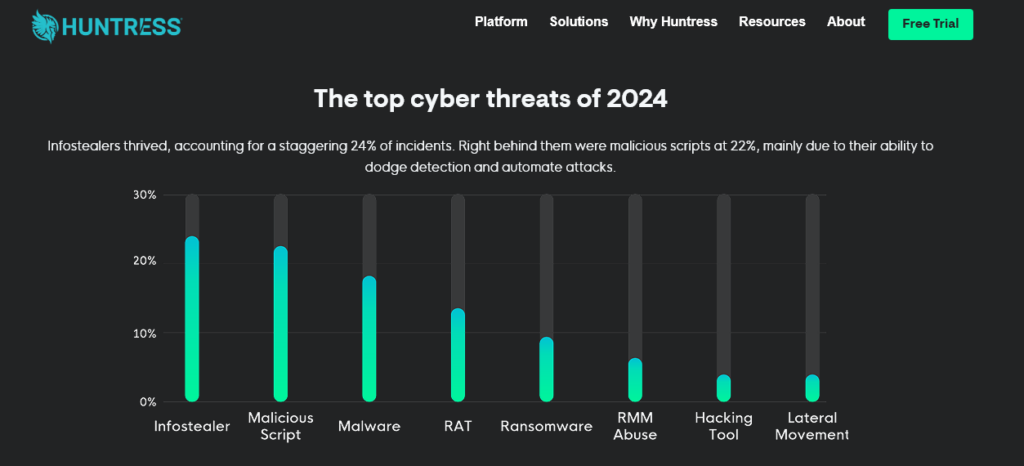
By [Alon Gal] | March 2025 At Infostealers.com, we’ve been sounding the alarm on the infostealer epidemic for years, uncovering how these malware families—like Vidar, Lumma, RedLine, and Raccoon—silently harvest credentials and pave the way for devastating breaches. Backed by Hudson Rock’s threat intelligence, we’ve tracked countless corporate compromises stemming from infected devices. Now, the “2025 […]
ALIEN TXTBASE Data Leak: A Deep Analysis of the 284M Accounts Breach Added by HaveIbeenPwned
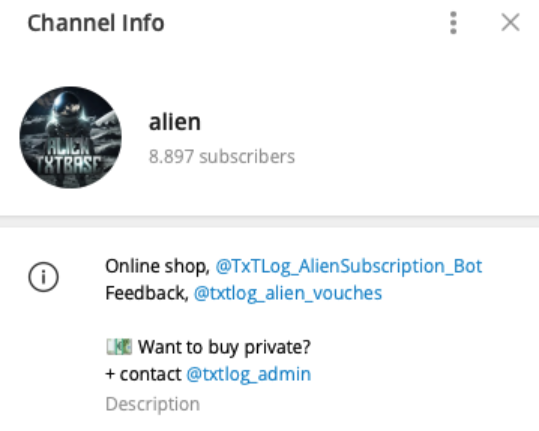
In recent days, the cybersecurity community has been alarmed by the emergence of a massive data leak known as ALIEN TXTBASE, which was recently indexed on Have I Been Pwned (HIBP). This breach, reportedly containing over 23 billion records, was published on a Telegram channel and claimed to be a collection of Stealer Logs—credentials stolen from malware-infected devices. Our […]
Hudson Rock Drops BlackBastaGPT: Built from 1M Internal Messages Leaked from Black Basta Ransomware Group
We scrambled to launch BlackBastaGPT super fast after the latest Black Basta leak hit to get you immediate value. Find it here – www.hudsonrock.com/blackbastagpt This AI chatbot is for threat intelligence researchers, letting you dive into Black Basta’s internal chats to unpack their ops, tactics, cash flow, and humor. It’s raw, real, and pulls straight […]
Infostealing Malware Infections in the U.S. Military & Defense Sector: A Cybersecurity Disaster in the Making
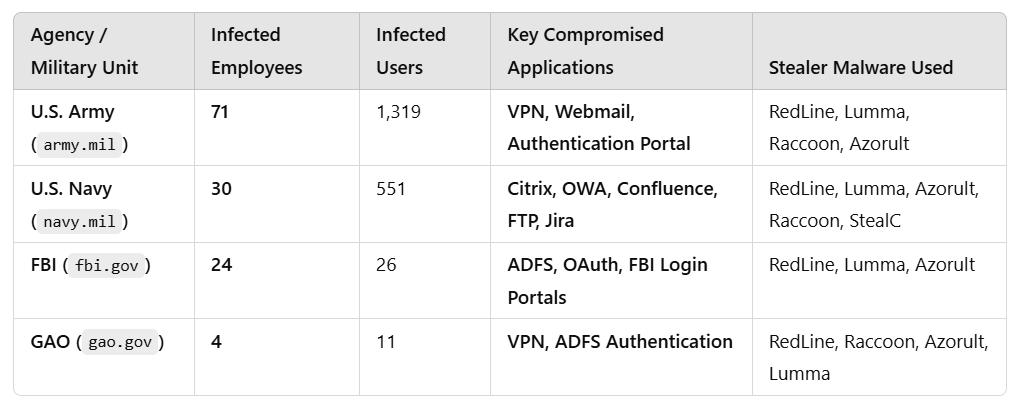
By [Alon Gal] | February 2025 Introduction: When National Security Gets Compromised for $10 For years, the U.S. military and its defense contractors have been considered the gold standard of security — equipped with multi-billion-dollar budgets, classified intelligence networks, and the world’s most advanced cybersecurity measures. Yet, Global Infostealing Malware Data from Hudson Rock reveals an unsettling reality: […]
Hudson Rock’s Cybercrime and Threat Intelligence Researcher, Leonid Rozenberg, Shares Insights About Infostealers and Security

Hudson Rock has been the go-to source for all things cybersecurity and infosec updates. Be it offering dark web intelligence or finding one’s own data on breach forums, Hudson Rock has been a torch bearer, bringing the latest updates to people. TechNadu reached out to the company to know how they work, what powers them, […]
CAPTCHA Chaos: From X Threads to Telegram
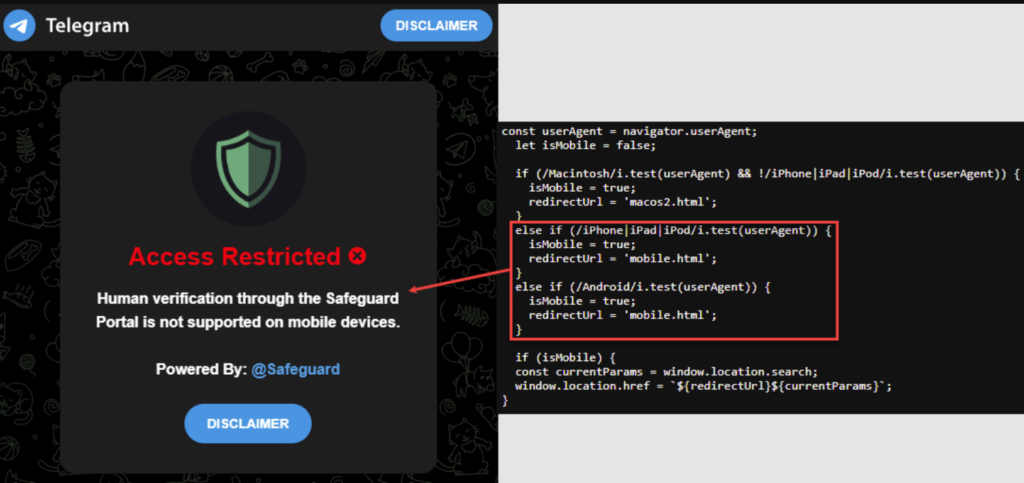
Cybercriminals are continuously evolving their tactics to exploit human behavior and trust. In one of the latest campaigns, attackers have weaponized fake CAPTCHA verification systems—tools typically used to verify a user’s legitimacy—to deliver malicious payloads. Introduction This campaign demonstrates an evolution from basic fake URL-based CAPTCHAs, seen in previous attacks, to a more sophisticated Telegram-based […]
Information Stealer Masquerades as LDAPNightmare (CVE-2024-49113) PoC Exploit
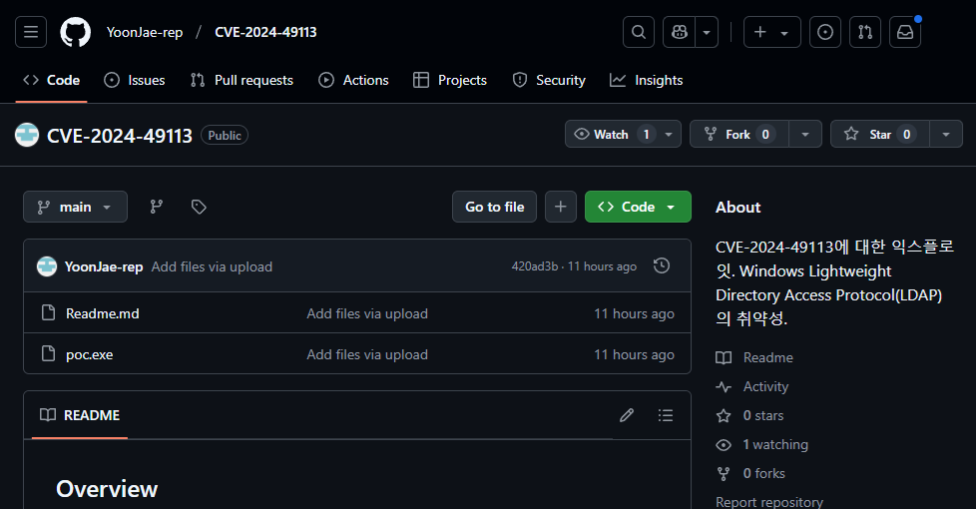
In December 2024, two critical vulnerabilities in Microsoft’s Windows Lightweight Directory Access Protocol (LDAP) were addressed via Microsoft’s monthly Patch Tuesday release. Both vulnerabilities were deemed as highly significant due to the widespread use of LDAP in Windows environments: In this blog entry, we discuss a fake proof-of-concept (PoC) exploit for CVE-2024-49113 (aka LDAPNightmare) designed to lure security researchers […]
How Cracks and Installers Bring Malware to Your Device
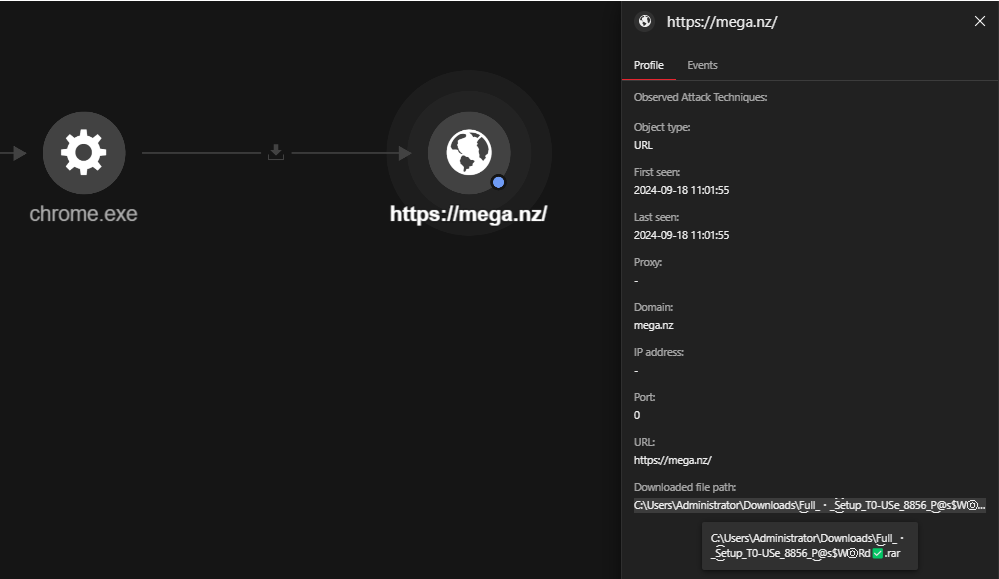
Key Takeaways Introduction The increase of fake installers bundled with info stealers is a growing threat for users looking for pirated software. These malicious programs disguise themselves as legitimate applications, often appearing in search results or comments on platforms like GitHub. Unfortunately, many users fall prey to these tricks. The Trend Micro™ Managed XDR service frequently sees the […]
Infostealer Logs to Fuel a New Wave of AWS Ransomware Attacks
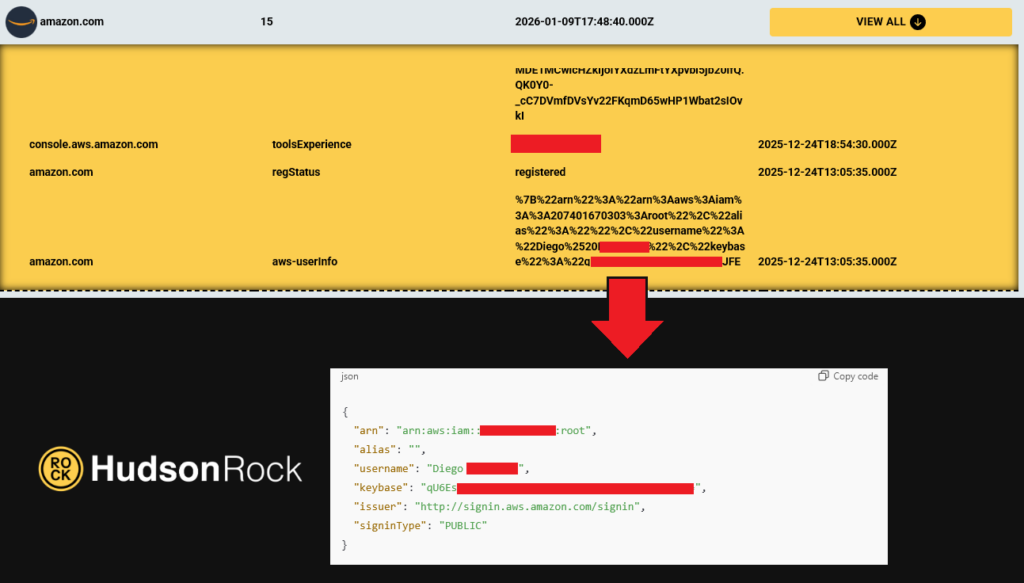
Introduction Recent research from Halcyon has uncovered a novel approach by a threat actor — referred to as Codefinger — who is actively abusing Amazon Web Services (AWS) by leveraging its native features to facilitate ransomware attacks in the wild. This technique underlines a powerful shift in the cyber threat landscape: instead of exploiting infrastructure outside the victim’s cloud […]
Information Stealer Masquerades as LDAPNightmare (CVE-2024-49113) PoC Exploit
In December 2024, two critical vulnerabilities in Microsoft’s Windows Lightweight Directory Access Protocol (LDAP) were addressed via Microsoft’s monthly Patch Tuesday release. Both vulnerabilities were deemed as highly significant due to the widespread use of LDAP in Windows environments: In this blog entry, we discuss a fake proof-of-concept (PoC) exploit for CVE-2024-49113 (aka LDAPNightmare) designed to lure security researchers […]
Telefonica Breach: Infostealer Malware Opens Door for Social Engineering Tactics

Telefonica, a major telecommunications company, recently confirmed a breach in their internal ticketing system, which led to a significant data leak. The breach involved unauthorized access and extraction of sensitive information, including a vast amount of employee and operational data. Infostealer Malware and Social Engineering Tactics New information has emerged indicating that the breach was […]
“Can you try a game I made?” Fake Game Sites Lead to Information Stealers

The background and the IOCs for this blog were gathered by an Expert helper on our forums and Malwarebytes researchers. Our thanks go out to them. A new, malicious campaign is making the rounds online and it starts simple: Unwitting targets receive a direct message (DM) on a Discord server asking about their interest in […]


