Hudson Rock Announces First Comprehensive Infostealers AI Bot: CavalierGPT

Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data associated with Infostealer infections. CavalierGPT retrieves and curates information from various Hudson Rock endpoints, enabling investigators to delve deeper into cybersecurity threats with unprecedented ease and efficiency. We are excited […]
Massive MOVEit Vulnerability Breach: Hacker Leaks Employee Data from Amazon, McDonald’s, HSBC, HP, and Potentially 1000+ Other Companies
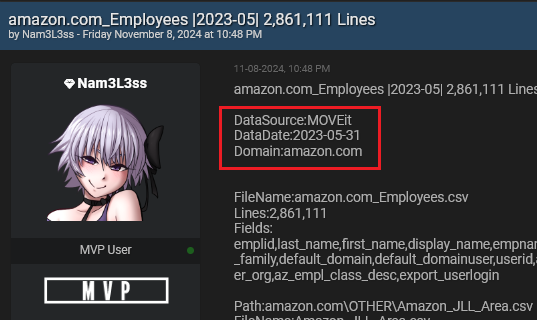
Written by Alon Gal A person operating under the username Nam3L3ss has exploited a critical vulnerability in MOVEit, a file transfer software, exposing extensive employee data from prominent companies worldwide. The vulnerability, known as CVE-2023–34362, has led to one of the most substantial leaks of corporate information this year, affecting various sectors, including finance, healthcare, […]
Threat actors use copyright infringement phishing lure to deploy infostealers

Phishing email campaign targets Taiwan Talos observed an unknown threat actor conducting a malicious phishing campaign targeting victims in Taiwan since at least July 2024. The campaign specifically targets victims whose Facebook accounts are used for business or advertising purposes. The initial vector of the campaign is a phishing email containing a malware download link. […]
Mnemonic Security Podcast – Infostealers

In this new episode of the mnemonic security podcast, Robby Peralta is joined by Leonid Rozenberg, a cybersecurity expert and dark web researcher at Hudson Rock, to discuss infostealers. Rozenberg provides a brief history of infostealers, which began with Zeus in 2007, a malware initially designed to steal only banking information. Today, infostealers have evolved […]
Schneider Electric Hacked and Blackmailed Following Lumma Infostealer Infection

Free Infostealer Intelligence Tools by Hudson Rock – www.hudsonrock.com/free-tools On November 4th, Schneider Electric acknowledged a data breach in which hackers stole 40GB of data from the company’s Jira server. “Schneider Electric is investigating a cybersecurity incident involving unauthorized access to one of our internal project execution tracking platforms which is hosted within an isolated […]
Law Enforcement Hacked Infrastructure of Redline and Meta Infostealers (Operation Magnus)

*Not fully confirmed yet According to the website which was discovered through Redline related Telegram channels, law enforcement was able to hack the infrastructure of Redline and Meta Infostealers and obtain critical data With the message being that more information is to come In addition, law enforcement attached the following video: Update: Security researcher g0njxa […]
Threat Actors Push ClickFix Fake Browser Updates Using Stolen Credentials
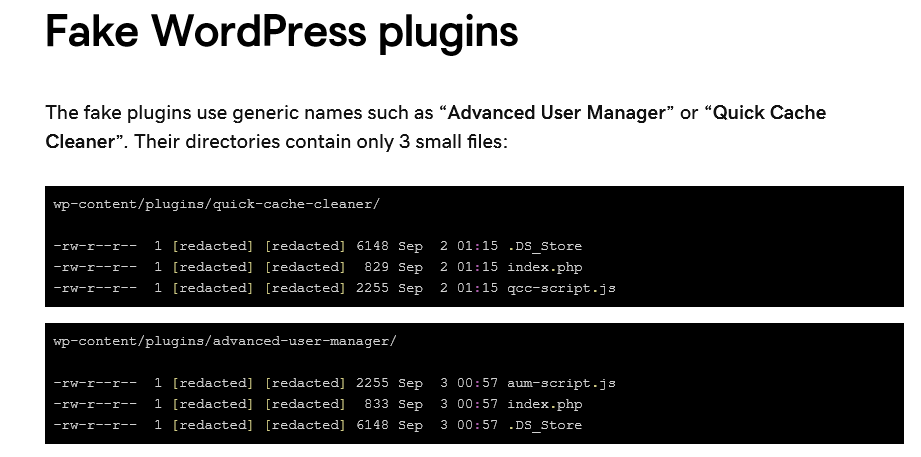
Key findings Overview The GoDaddy Security team is tracking a new variant of ClickFix (also known as ClearFake) fake browser update malware that is distributed via bogus WordPress plugins. These seemingly legitimate plugins are designed to appear harmless to website administrators but contain embedded malicious scripts that deliver fake browser update prompts to end-users. This technique leverages social […]
Largest Retail Breach in History: 350 Million “Hot Topic” Customers’ Personal & Payment Data Exposed — As a Result of Infostealer Infection
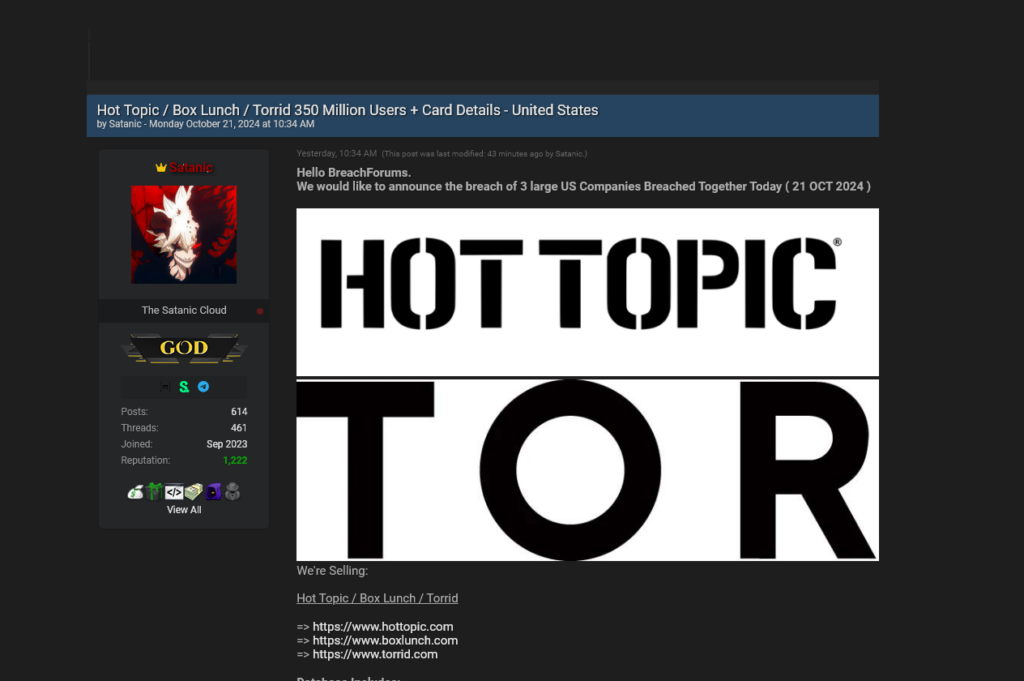
Disclaimer: Hudson Rock does not insinuate or imply responsibility or liability on behalf of any parties mentioned herein. The content is intended solely for informational purposes and reflects our findings at the time of publication. Hudson Rock disclaims any responsibility for how this information regarding Infostealer Infection may be interpreted or used by others. Update […]
ClickFix tactic: The Phantom Meet (Infostealers)

This blog post provides a chronological overview of the observed ClickFix campaigns. We further share technical details about a ClickFix cluster that uses fake Google Meet video conference pages to distribute infostealers. Context In May 2024, a new social engineering tactic called ClickFix emerged, featuring a ClearFake cluster that the Sekoia Threat Detection & Research […]
How Hackers Really Used Infostealers for the Biggest Recent Cyber Breaches
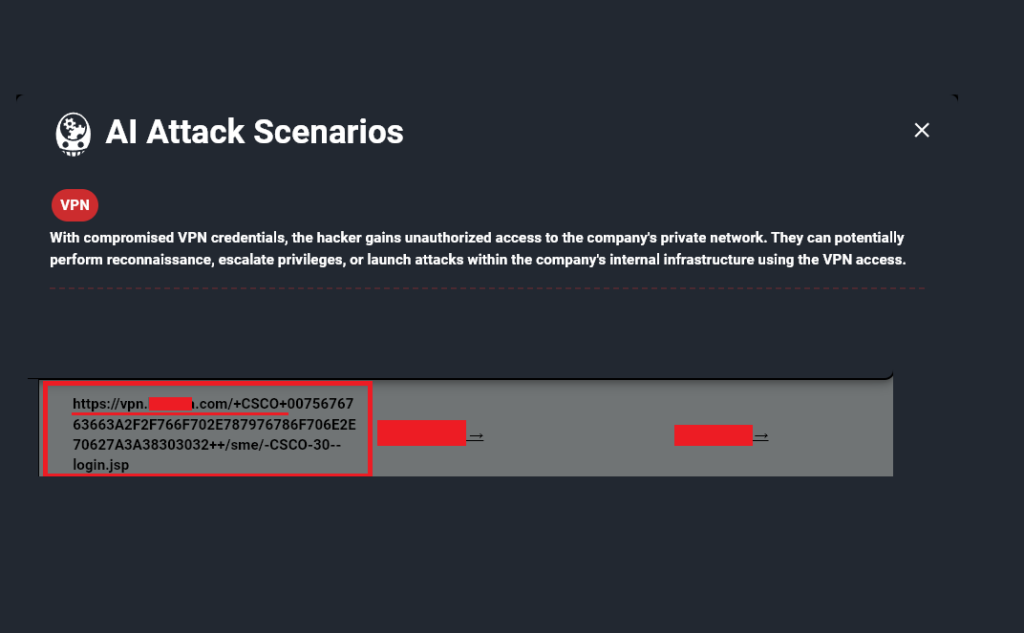
We are now at a point where numerous cyberattacks have been carried out using compromised Infostealer data. Major companies such as AT&T, Ticketmaster, Orange, Airbus, Uber, and EA Sports have all suffered similar fates. But how does a breach really unfold once an employee is infected by Infostealers? Threat actors often target low-hanging fruit; like […]
Exposing Information Stealers | Protecting Identities Online

Interview with Malware Protection expert Leonid Rozenberg with Hudson Rock (www.hudsonrock.com) on exposing information stealers, protecting identities online, hackers who sell vulnerabilities, and how to know if your identity is stolen. Check out Hudson Rock’s free tools available here – https://www.hudsonrock.com/threat-intelligence-cybercrime-tools
FIN7 Hosting Honeypot Domains with Malicious AI DeepNude Generators – New Silent Push Research

Key findings Executive summary Silent Push Threat Analysts have observed the FIN7 group (aka Sangria Tempest) using new tactics in their malware and phishing attacks. We found that FIN7 has created at least seven websites serving malware to visitors looking to use an “AI Deepnude generator.” The threat group is also continuing to use browser […]


