Hamster Kombat Players Threatened by Spyware & Infostealers

In the past few months, the Telegram clicker game Hamster Kombat has taken the world of cryptocurrency game enthusiasts by storm. Even though the gameplay, which mostly entails repeatedly tapping the screen of one’s mobile device, might be rather simple, players are after something more: the possibility of earning big once Hamster Kombat’s creators unveil […]
STARGAZERS GHOST NETWORK

Key Points Introduction Threat actors continually evolve their tactics to stay ahead of detection. Traditional methods of malware distribution via emails containing malicious attachments are heavily monitored, and the general public has become more aware of these tactics. Recently, Check Point Research observed threat actors using GitHub to achieve initial infections by utilizing new methods. Previously, GitHub […]
KnowBe4 mistakenly hires North Korean hacker, faces infostealer attack

American cybersecurity company KnowBe4 says a person it recently hired as a Principal Software Engineer turned out to be a North Korean state actor who attempted to install information-stealing on its devices. The firm detected and stopped the malicious actions in time, so no data breach occurred. However, the case highlights the continued threat posed […]
Threat Actor Uses Fake CrowdStrike Recovery Manual to Deliver Unidentified Stealer
On July 22, 2024, CrowdStrike Intelligence identified a Word document containing macros that download an unidentified stealer now tracked as Daolpu. The document impersonates a Microsoft recovery manual.1 Initial analysis suggests the activity is likely criminal. Technical Analysis Lure Document The analyzed file, (SHA256 hash: ), is a Word document containing malicious macros. Upon execution, the macro […]
Infostealers AI Module – Online Behaviour Analysis (Hudson Rock)

Hudson Rock’s database, with tens of millions of computers infected worldwide, enables cybersecurity and law enforcement customers to investigate suspicious infected computers that are using login credentials to darknet websites. Our AI module adds an additional layer of research, which helps profile the behavior of suspicious users and aids in investigations. To learn more, visit […]
Info Stealers Exposed: The Silent Threat Stealing Your Data
In the ever-evolving world of cybersecurity, staying ahead of emerging threats is crucial. One such threat that has been gaining traction is info stealers. These malicious programs are designed to harvest sensitive information from unsuspecting victims, posing significant risks to individuals and organizations. This article aims to shed light on the growing trend of info […]
Infostealer Infection Results in Data Breach of Blockchain Identity Platform, Fractal ID
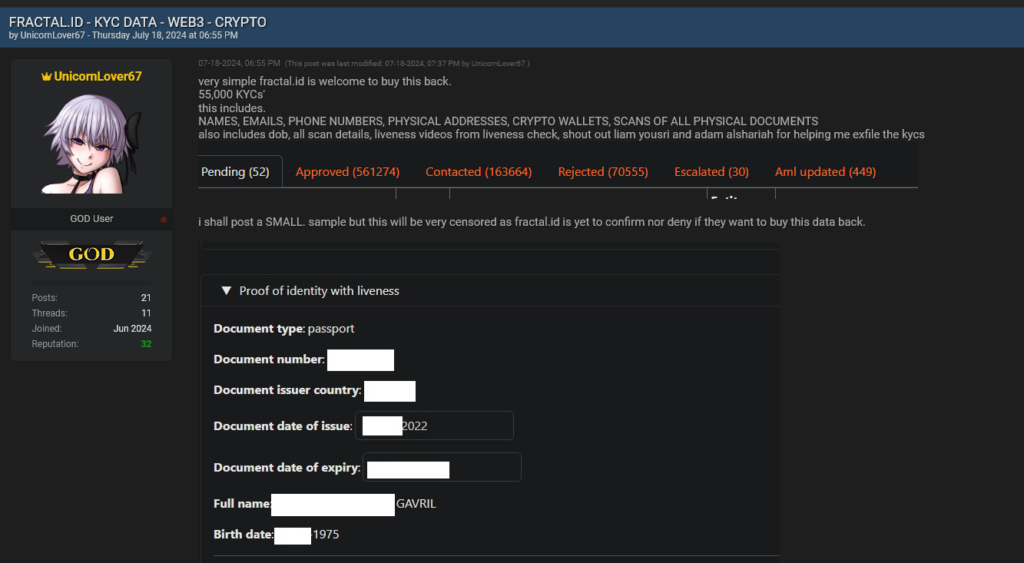
On July 14th, 2024 Blockchain identity platform Fractal ID suffered a data breach resulting in sensitive KYC data of over 55,000 individuals being exposed online. Fractal ID acknowledged the breach on July 17th: The severity of this data leak should not be underestimated, as it includes the following set of sensitive details on the impacted […]
Hackers Steal Text and Call Records of ‘Nearly All’ AT&T Customers

In one of the most significant data breaches in recent history, hackers stole AT&T customers’ call and text metadata spanning several months. Hackers broke into a cloud platform used by AT&T and downloaded call and text records of “nearly all” of AT&T’s cellular customers across a several month period, AT&T announced early on Friday. The […]
Re-Infected: The Persistent Threat of Infostealers
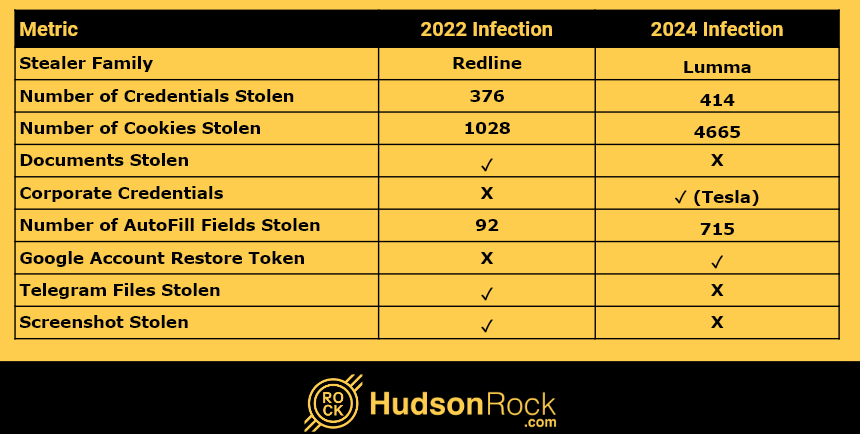
Having your data stolen once is bad enough, but for some people, it happens repeatedly. Infostealer infections are not a new phenomenon in the cybersecurity world, in fact, Hudson Rock has been collecting threat intelligence data from computers infected by Infostealers going back to 2018. With almost 30,000,000 computers infected in total by July 2024, it comes […]
Supply Chain Compromise Leads to Trojanized Installers for Notezilla, RecentX, Copywhiz

Executive Summary On Tuesday, June 18th, 2024, Rapid7 initiated an investigation into suspicious activity in a customer environment. Our investigation identified that the suspicious behavior was emanating from the installation of Notezilla, a program that allows for the creation of sticky notes on a Windows desktop. Installers for Notezilla, along with tools called RecentX and […]
Open-Sourced Infostealers About to Fuel New Wave of Computer Infections

A potential shift in Infostealers might be happening again. Traditionally, teams of cybercriminals develop an Infostealer family (variant) such as Redline, Lumma, Raccoon, etc., and rent the capabilities of that variant to other cybercriminals, typically costing a few hundred dollars per month. However, a new trend is emerging that could significantly alter the landscape of […]
ID Verification Service for X & TikTok Breached due to an Infostealer Infection
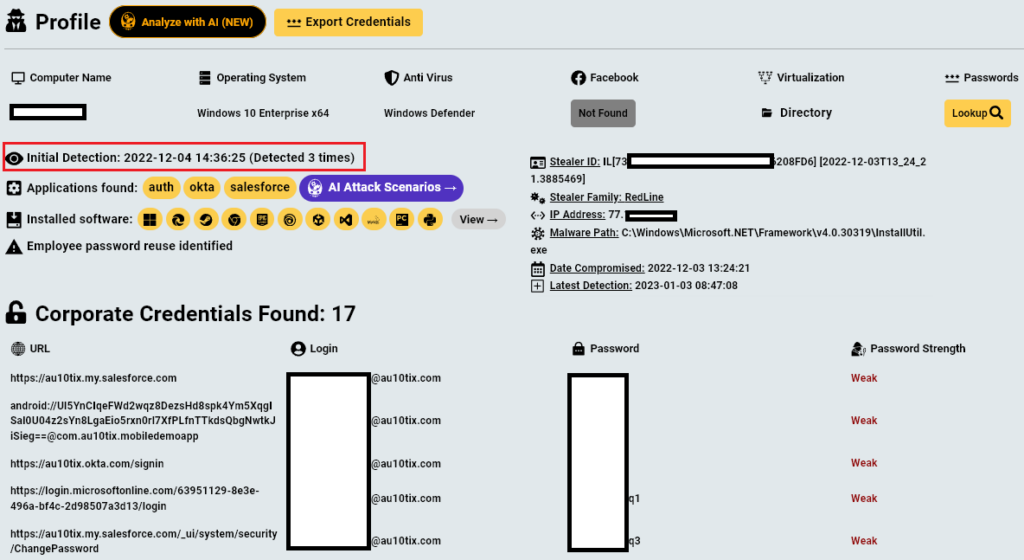
AU10TIX, a company that verifies the identities of TikTok, Uber, and X users, sometimes by processing photographs of their faces and pictures of their drivers’ licenses, exposed a set of administrative credentials online for more than a year, potentially allowing hackers to access sensitive data. This information comes from screenshots and data obtained by 404 […]


