Infostealer Infections Lead to Hacking of Google, TikTok, and Meta Law Enforcement Systems

Edit 03/02/24 – ‘Tamagami’ reveals they also possess access to Kodex which enables EDR / Subpoena requests for services such as LinkedIn, Discord, Tinder, Binance, Coinbase, Chainlink, SendGrid, and others A worrying trend emerges as threat actors hack into the law enforcement systems of major organizations, gaining the ability to legally request personal details of […]
CrackedCantil: A Malware Symphony Breakdown

Malware is constantly evolving to become more evasive, destructive, efficient, and infectious. There are numerous families of malware, each with its own unique characteristics. These different families of malware can work together in a symphonious manner to deliver a powerful infection. For instance, the stealer malware can exfiltrate data before the ransomware encrypts the files. […]
Hundreds Of Network Operators’ Credentials Found Circulating In Dark Web

Following a recent and highly disruptive cyberattack on telecom carrier Orange España the cybersecurity community needs to rethink its approach to safeguarding the digital identity of staff involved in network engineering and IT infrastructure management. Orange España is the second-largest mobile operator in Spain. In early January, an attacker going by the alias ‘Snow’ hijacked […]
Prioritizing cybercrime intelligence for effective decision-making in cybersecurity (Hudson Rock)

In this Help Net Security interview, Alon Gal, CTO at Hudson Rock, discusses integrating cybercrime intelligence into existing security infrastructures. Our discussion will cover a range of essential aspects, from the importance of continuous adaptation in cybersecurity strategies to practical advice for CISOs on enhancing threat detection and response capabilities. We’ll also explore the challenges of […]
Info Stealing Packages Hidden in PyPI

Affected platforms: All platforms where PyPI packages can be installedImpacted parties: Any individuals or institutions that have these malicious packages installedImpact: Leak of credentials, sensitive information, etc.Severity level: High The Python Package Index (PyPI) is an open repository of software packages developed by the Python community to help people quickly develop or update applications. While most of the packages […]
Top 5 Breaches Caused by Infostealer Infections

The rise of infostealer malware has become a serious challenge for organizations worldwide. These sophisticated malware types are designed to stealthily infiltrate systems, extract sensitive information, and pave the way for more destructive cyberattacks. The following cases, involving high-profile companies, underscore the critical importance of robust cybersecurity measures. These incidents not only highlight the vulnerabilities […]
Chae$ Chronicles: Version 4.1 Dedicated to Morphisec Researchers

In ongoing efforts to monitor and analyze emerging cyber threats, Morphisec Threat Labs has recently turned its focus to Chae$ 4.1, an update to the Chaes malware Infostealer series. This version introduces key updates, including an improved Chronod module, and features a unique aspect: a direct message to the Morphisec team within the source code. […]
MailerLite Hack Leads to Massive Cryptocurrency Theft — An Exploit or an Infostealer Infection?
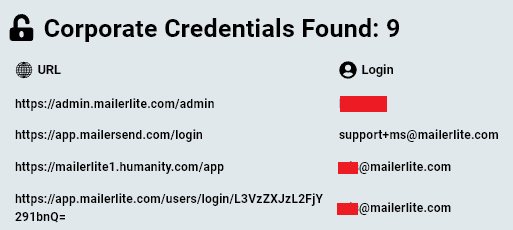
Cryptocurrency on-chain sleuth, ZachXBT, alerted the cryptocurrency community today that several notable organizations such as CoinTelegraph and WalletConnect are being used to send phishing messages through their mailing lists. It appears that the emails sent to victims are an attempt to convey them into signing a transaction that will drain their crypto wallets So far […]
Cracked software beats gold: new macOS backdoor stealing cryptowallets

A month ago, we discovered some cracked apps circulating on pirating websites and infected with a Trojan proxy. The malicious actors repackaged pre-cracked applications as PKG files with an embedded Trojan proxy and a post-install script initiating the infection. We recently caught sight of a new, hitherto unknown, macOS malware family that was piggybacking on cracked software. […]
JAVA-Based Sophisticated Stealer Using Discord Bot as EventListener
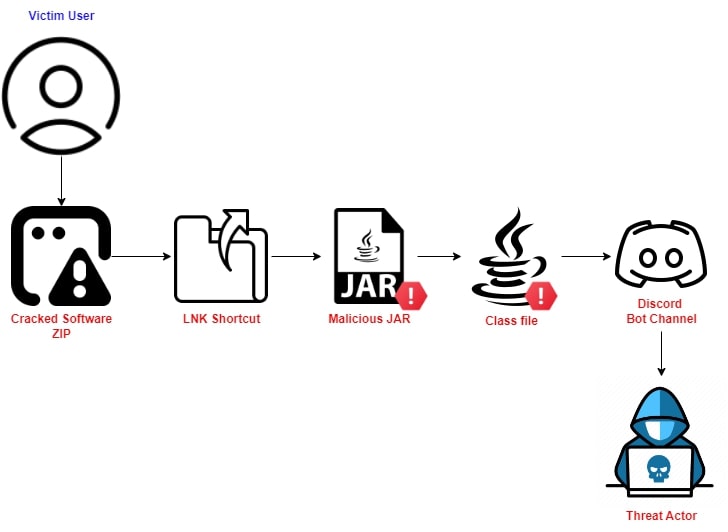
Executive Summary: In mid-November 2023, Trellix Advanced Research Center team members observed a Java-based stealer being spread through cracked software zip files using JDABuilder Classes to create an instance of the EventListener to easily register. The Stealer uses Discord bot channel as an EventListener. Delivery Mechanism: Figure 1: Infection Mechanism Threat Analysis: The Malicious ZIP […]
The Many Faces of Undetected macOS InfoStealers | KeySteal, Atomic & CherryPie Continue to Adapt

We have been reporting on the rise of infostealers targeting macOS since early last year, but threat actors show no signs of slowing down. Throughout last year, we saw variants of Atomic Stealer, macOS MetaStealer, RealStealer and others. Recent updates to macOS’s XProtect signature database indicate that Apple are aware of the problem, but early 2024 has already seen […]
Exploring FBot | Python-Based Malware Targeting Cloud and Payment Services
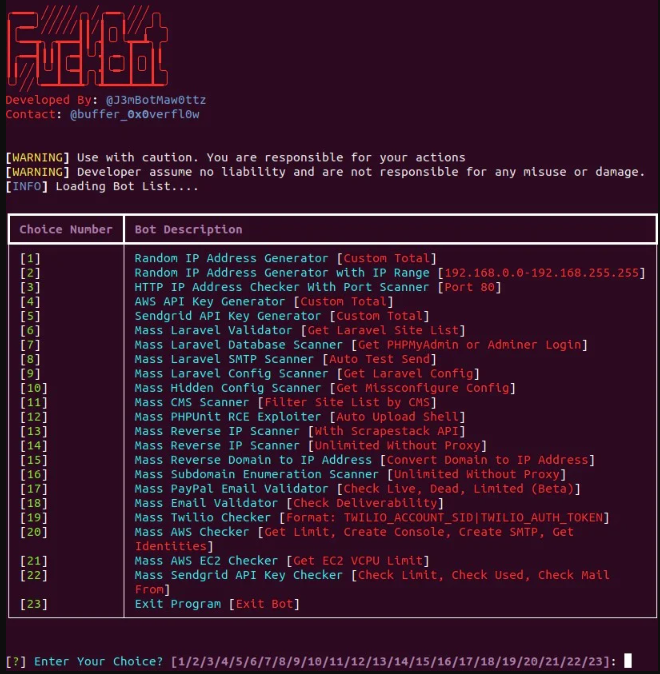
Executive Summary Overview The cloud hacktool scene is highly intertwined, with many tools relying on one another’s code. This is particularly true for malware families like AlienFox, Greenbot, Legion, and Predator, which share code from a credential scraping module called Androxgh0st. We identified a tool that is related but distinct from these families. FBot is a Python-based […]


