Another finding by Fox, related to LummaC2 infostealer sparked an infra hunt that led to many findings.
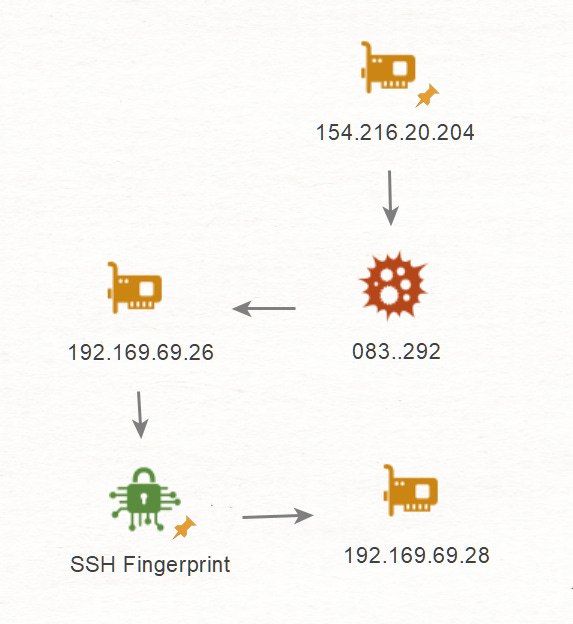
C2 Host Pivot & Windows Server Pattern
Following the finding of X user Fox_threatintel, we can see that there are 17 hosts matching the query for specific nginx versions running on port 19000. What stands out immediately are the findings regarding Windows server 2012, this was something that helped me identify infrastructure related to Rhadamanthys infostealer on a recent post. This finding helps me hypothesize that this infrastructure is used by multiple threat actors and is mainly serving infostealers and RATs.
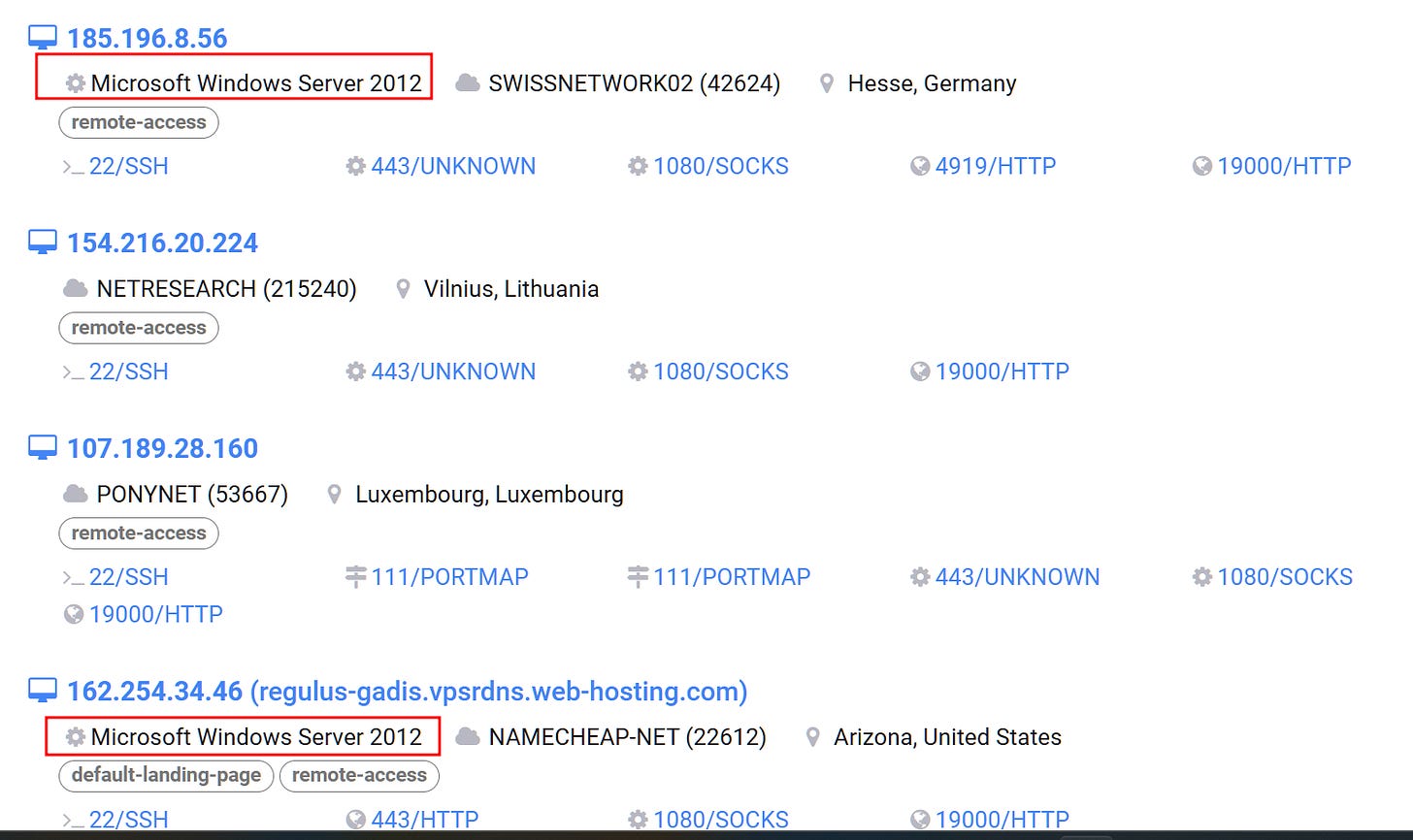
Having this additional piece of information I formulated a more accurate search. This search returned 29 results, removing 7 IPs that were also reported by Fox and we are left with 22 unique IPs, from the 22 IPs, 6 have been previously reported giving us some validation of our hypothesis so we can associate these IPs with malicious infrastructure with moderate to high confidence.
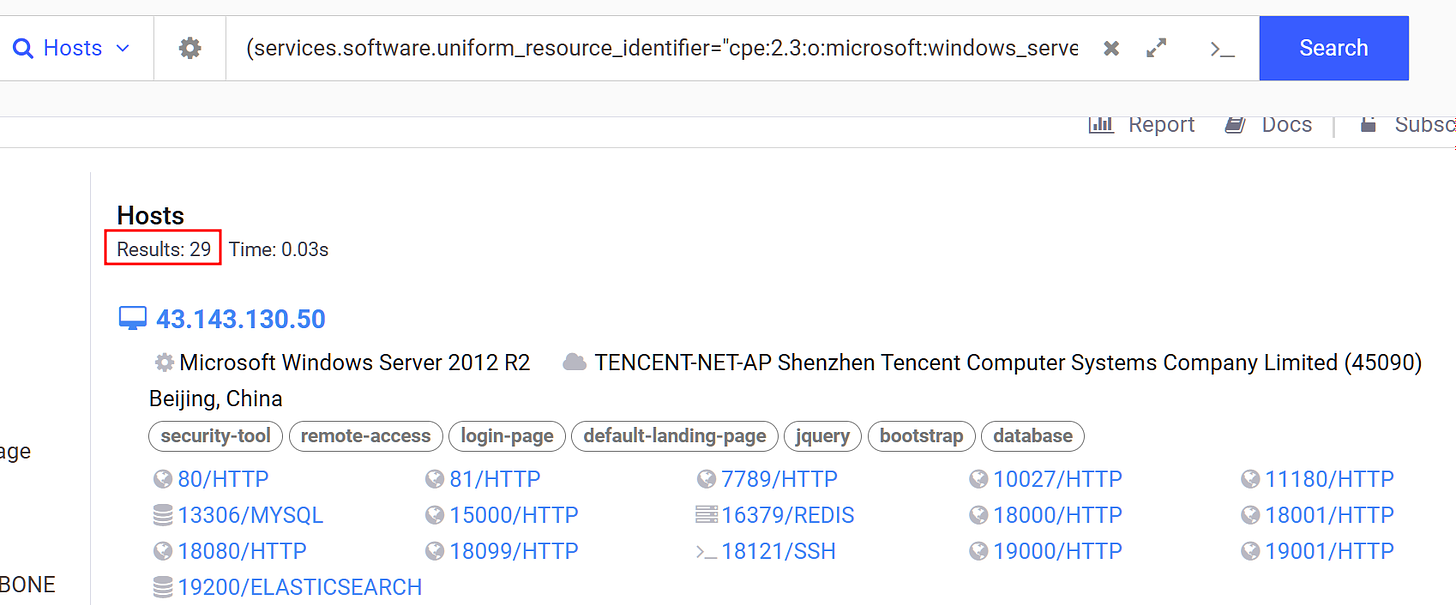
Unfortunately, the hosts didn’t share any SSH fingerprints so no further associations can be made.
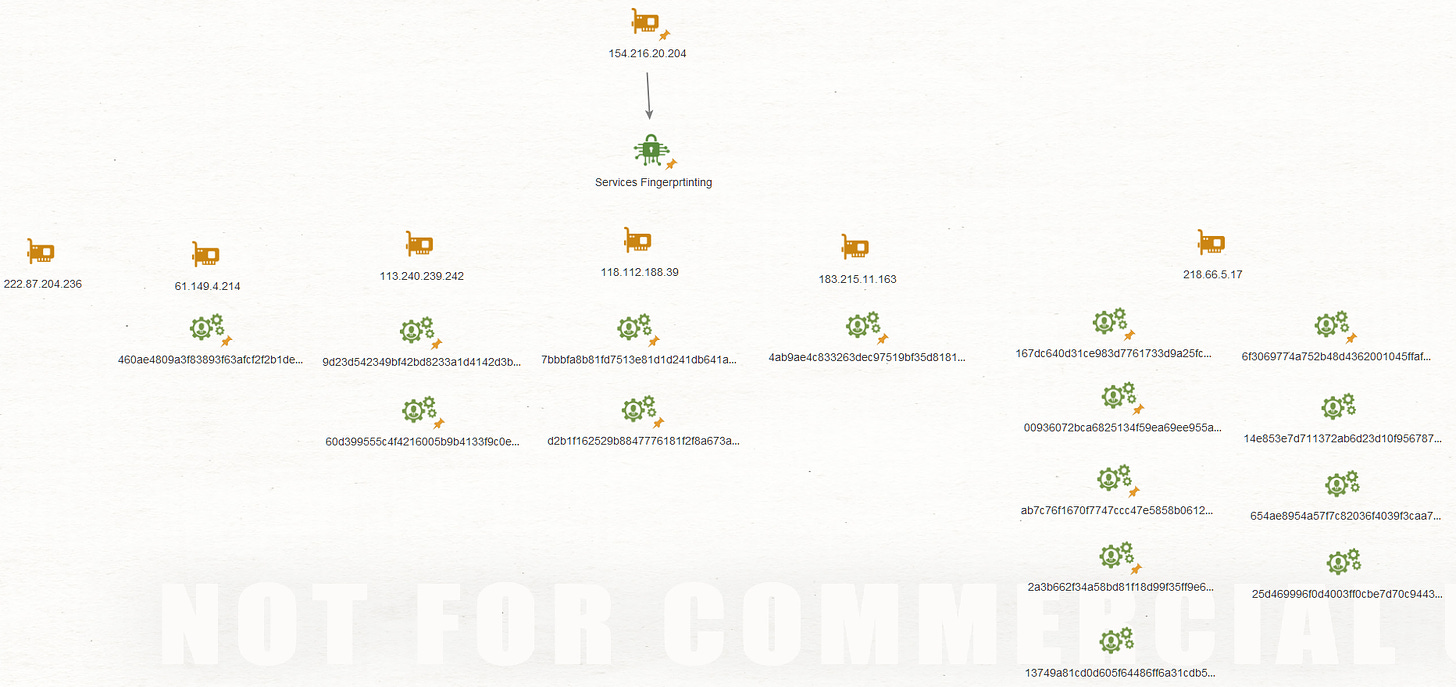
Communicating Files Pivot
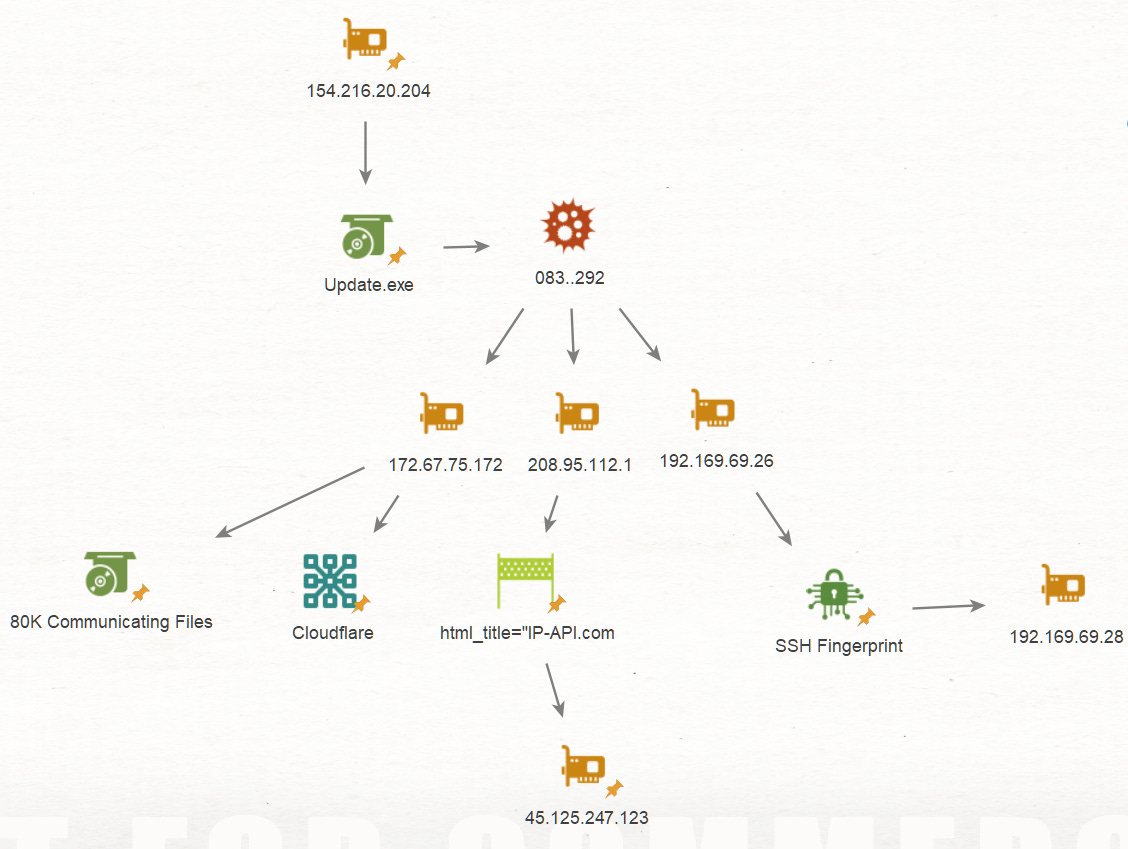
Furthermore the C2 IP 154.216.20[.]204 – AS 215240 is communicating with 15 files which have all been previously reported as malicious, so I reviewed them to map additional infrastructure
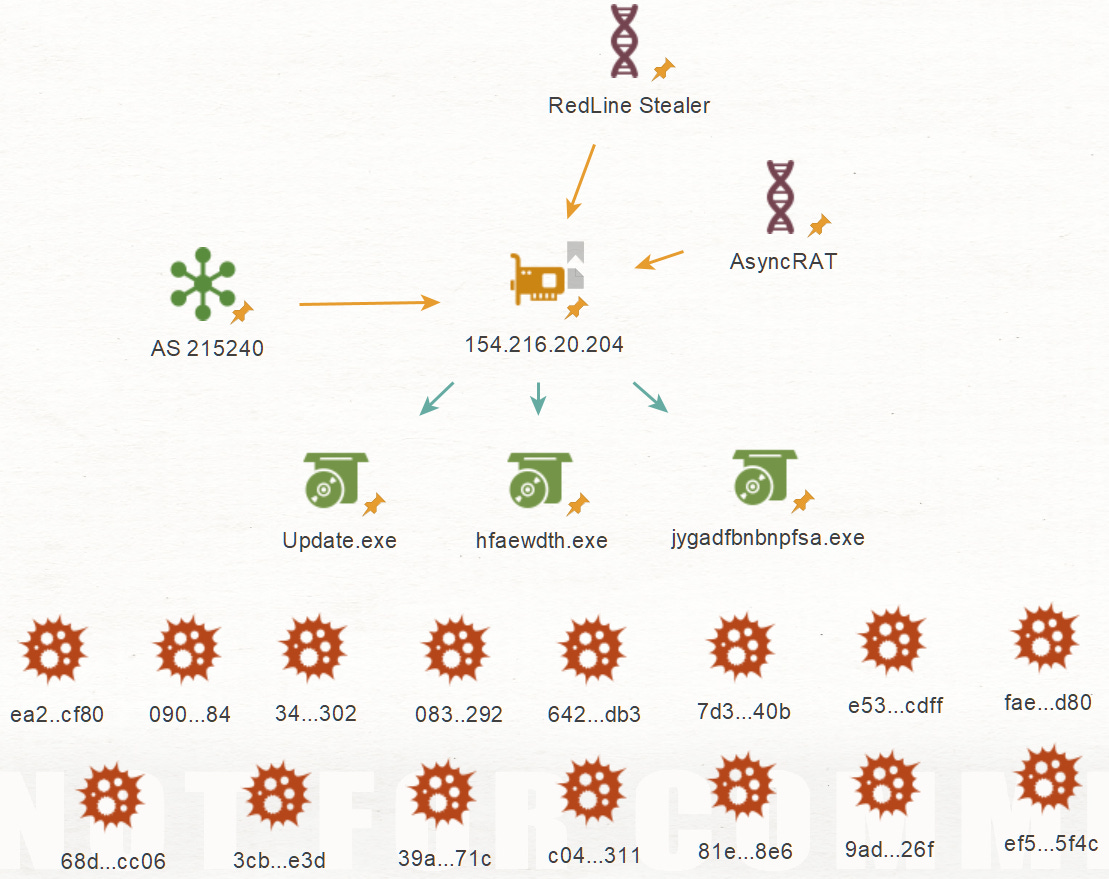
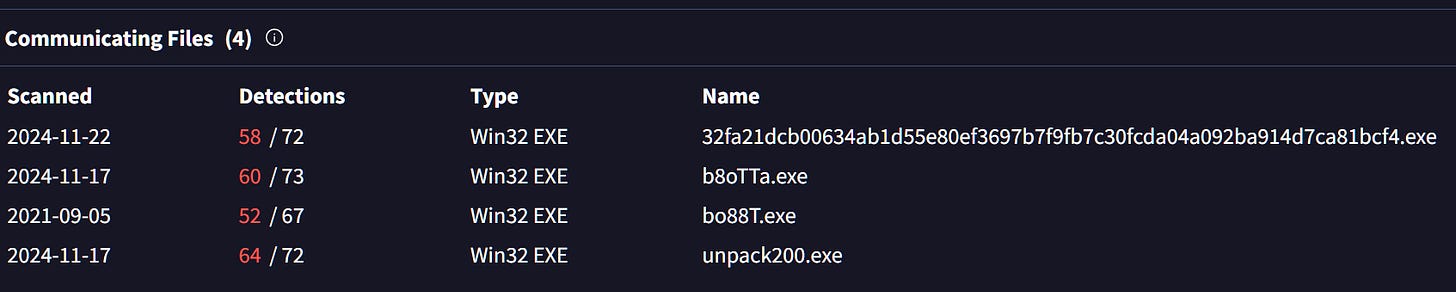
The file hash 083f0f217bff41523e9faa49bb13e9e5d691a3c51341b12d0c4829d8cfc33292 has 3 communicating IPs, let’s review them.
083f0f217bff41523e9faa49bb13e9e5d691a3c51341b12d0c4829d8cfc33292
172.67.75[.]172
192.169.69[.]26
208.95.112[.]1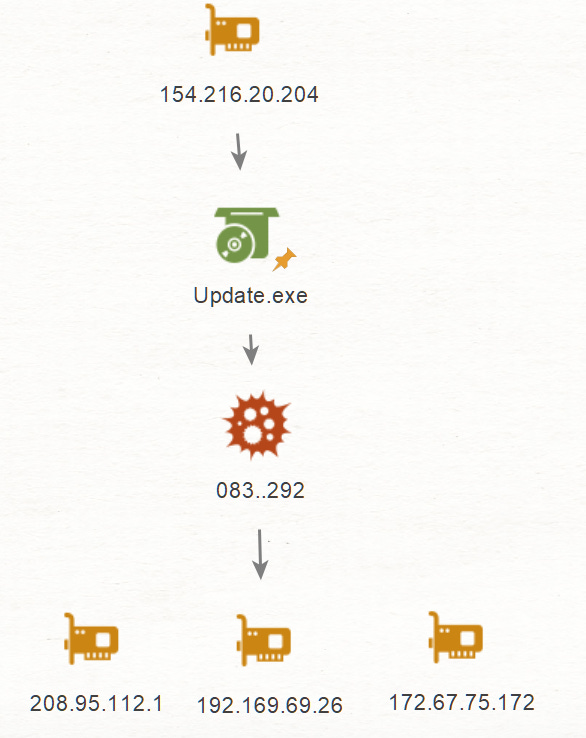
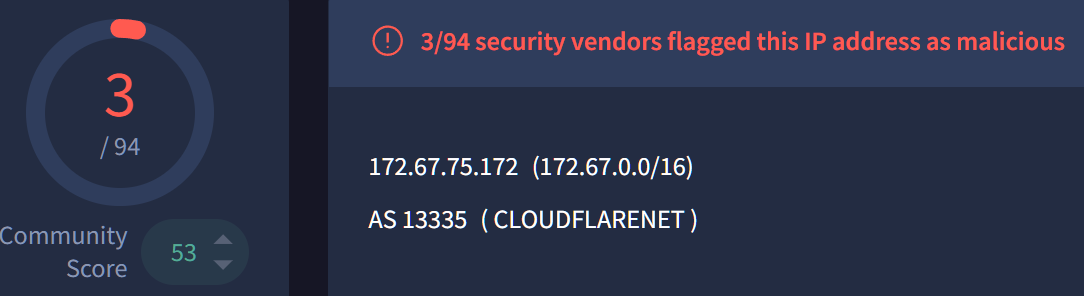
172.67[.]75.172
Reviewing the IP which is part of the Cloudflare CDN, we can see that it’s communicating with 78.6K files, most of them reported as malicious leading us to the conclusion that the threat actors behind the malware are using Cloudflare.
Cloudflare can be used as a reverse proxy, masking the IP while providing SSL encryption and provide a legitimate appearance making it harder to detect.
192.169.69[.]26
Next IP is 192.169.69[.]26 AS27323 Wowrack.com, communicating with 14K files so I can’t really go through all of them. Instead I looked at the host using Censys.
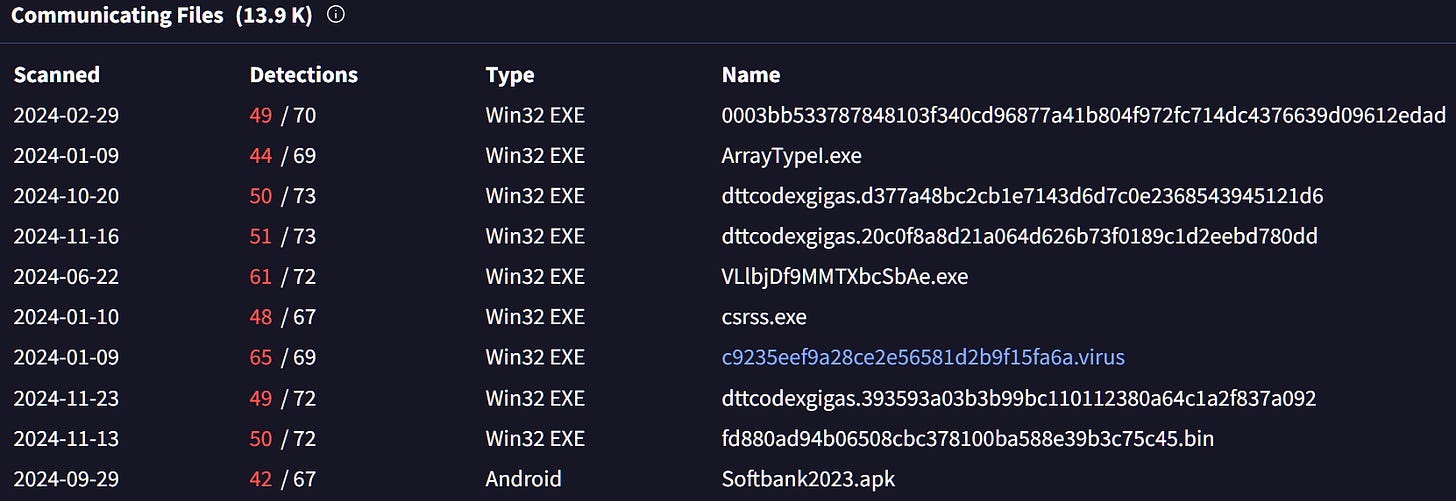
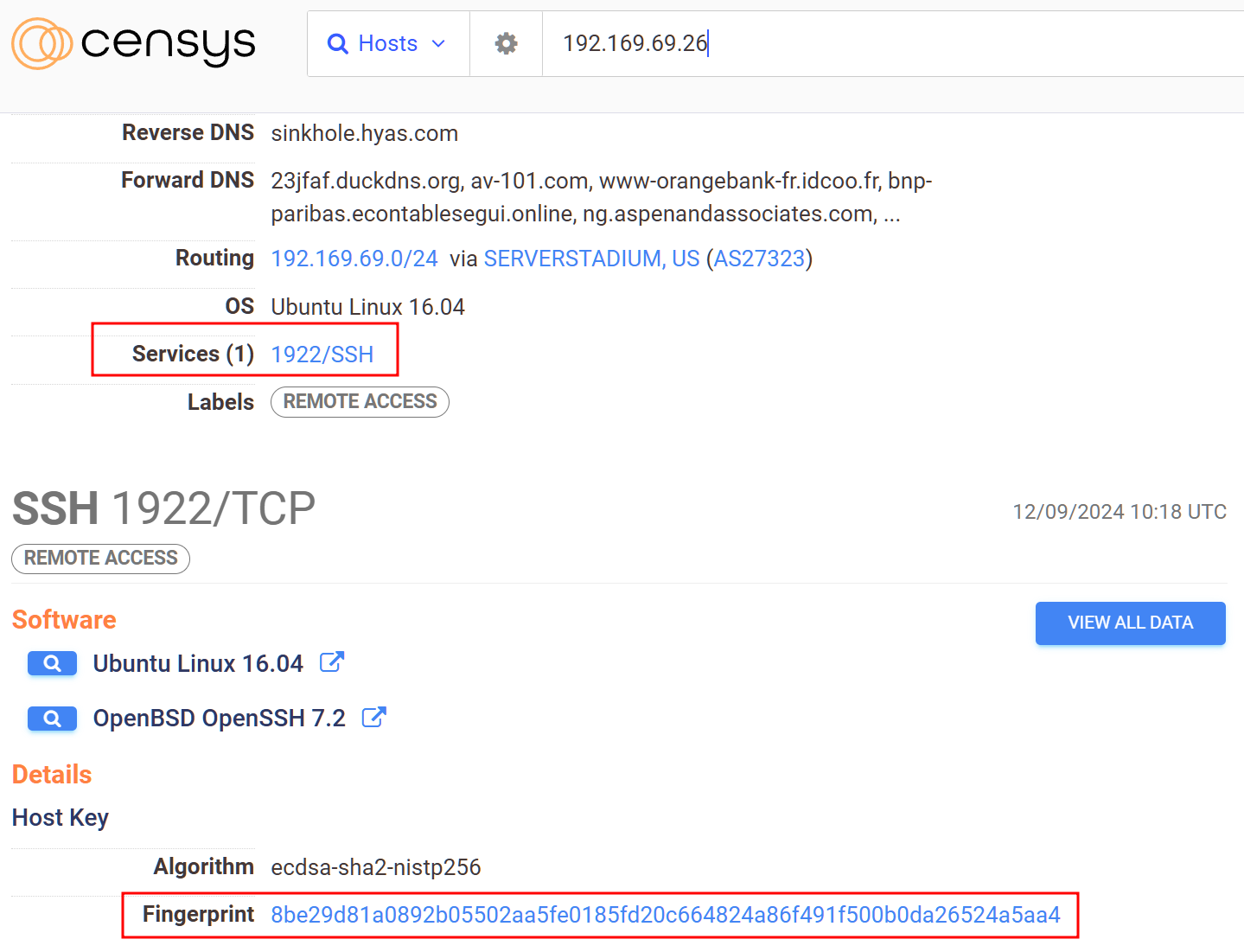
It seems to be running SSH on an unusual port, using the SSH fingerprint results in one more host matching the Fingerprint.
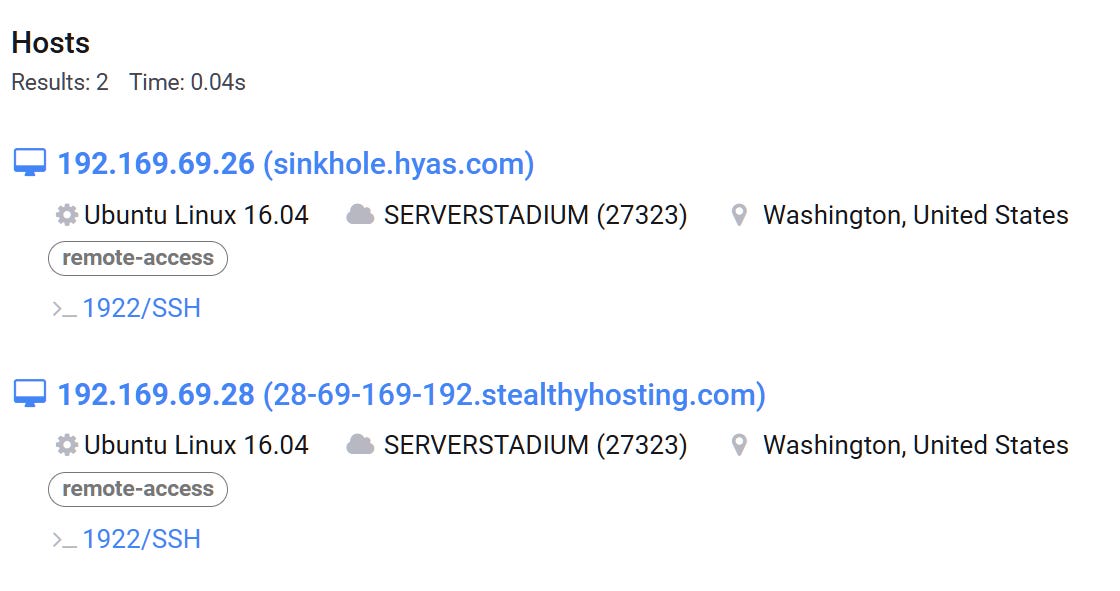
The host doesn’t have any detections yet but the fingerprint indicates that it was provisioned by the same actor on the same hosting service, additionally this IP communicates with malicious files that have been previously reported so we can associate the IP with this specific threat actor with high confidence.
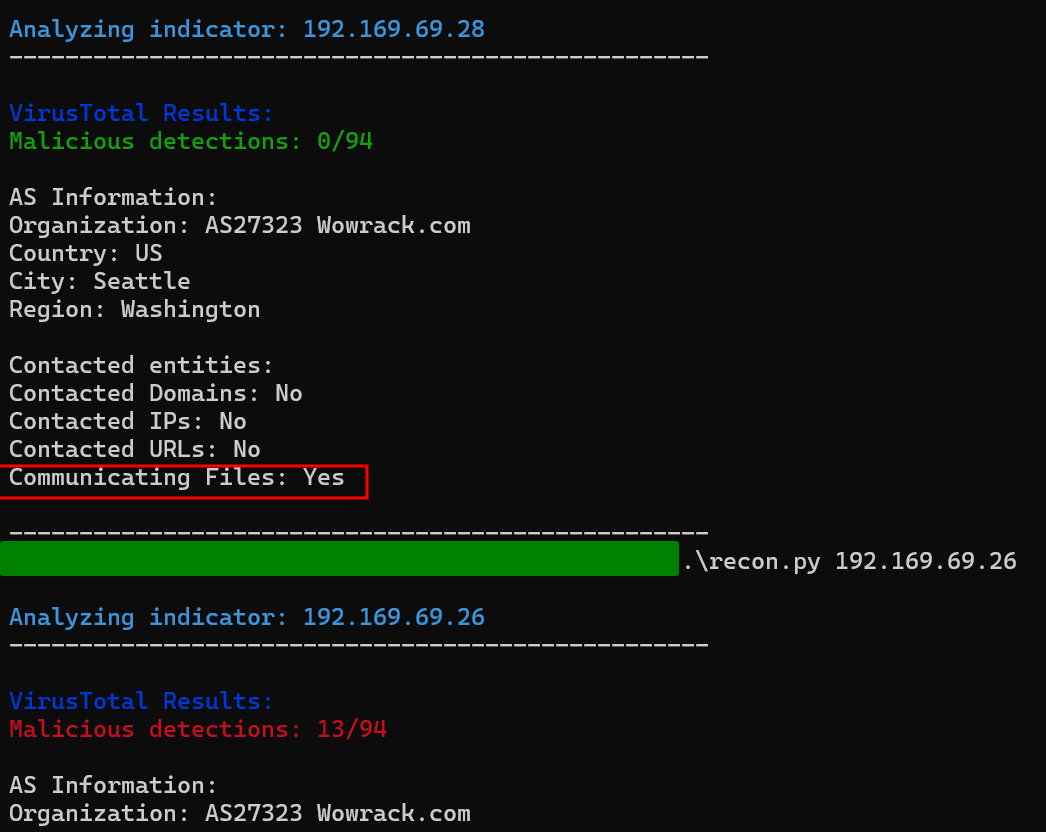
208.95.112[.]1
The last of the communicating IPs is part of AS 53334( TUT-AS ) and is associated with AsyncRAT, communicating with more than 488K files so I used the html body which was pointing to geolocation service API to pivot and discovered another server communicating with known malicious files.
services.http.response.html_title="IP-API.com - Geolocation API"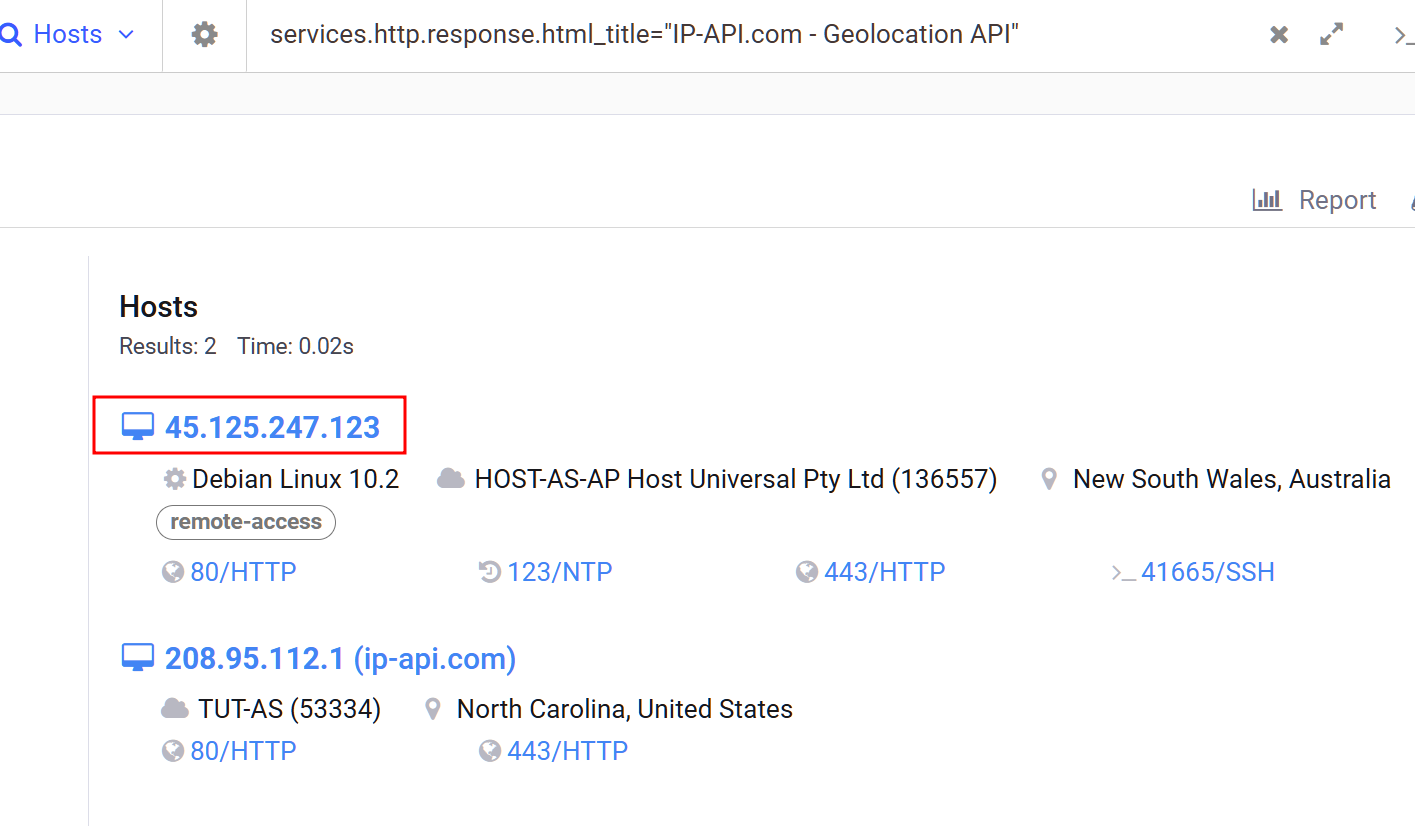
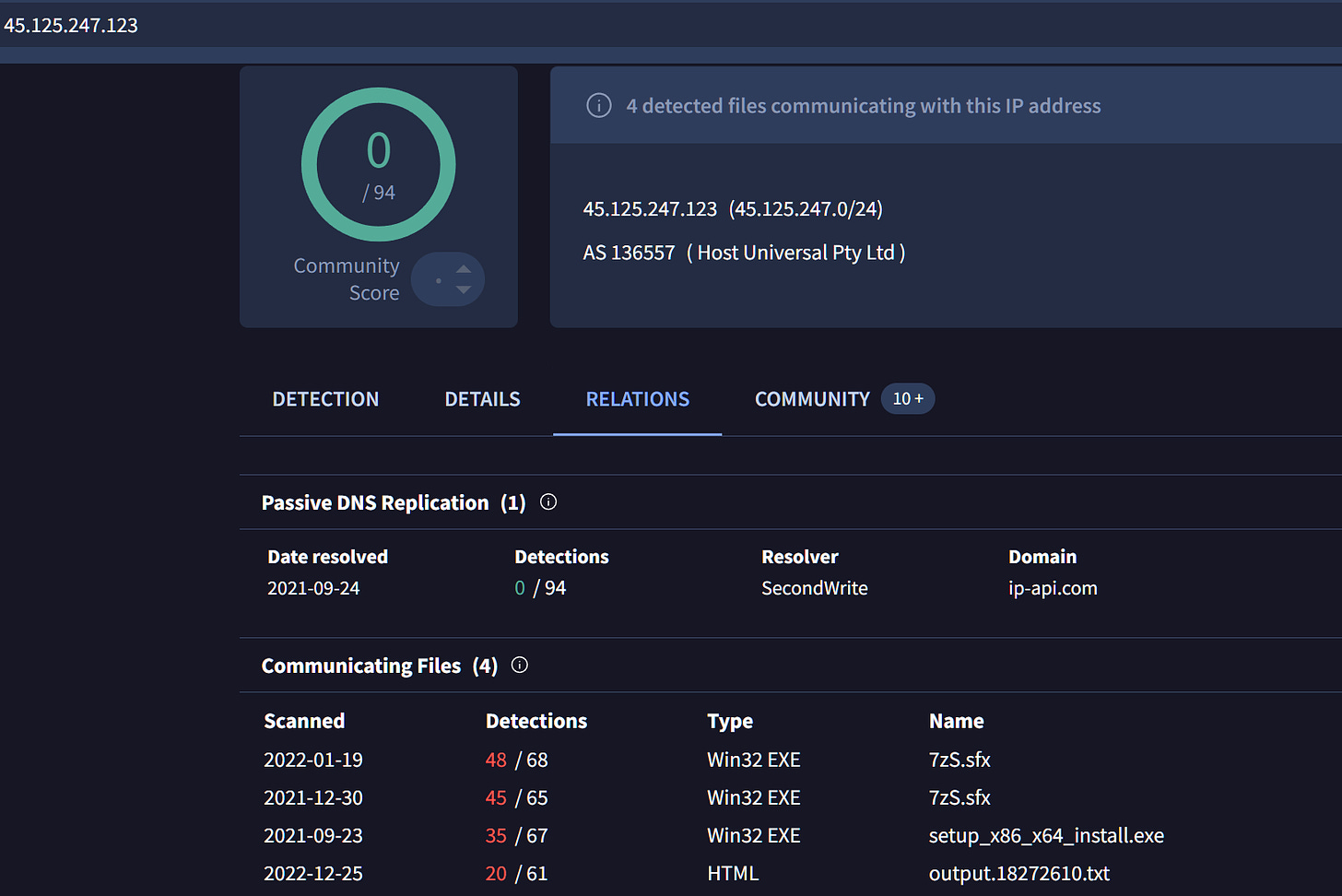
It’s clear now that this is a massive infrastructure mainly associated with infostealers and RATs, varying naming conventions and diverse provisioning methods suggest that the infrastructure is used by multiple threat actors.
As always, feel free to add on or roast my findings and reach out if you are interested.
Thanks!
IOC
# C2 IP
154.216.20[.]204
# Communicating Files & Associated IPs
a9f22319f417a9c78eb4c96257c847f1c08e9381ad05ebc05889d8b140ebf5d2
61.149.4[.]214
083f0f217bff41523e9faa49bb13e9e5d691a3c51341b12d0c4829d8cfc33292
172.67.75[.]172
192.169.69[.]26
192.169.69[.]28
208.95.112[.]1
45.125.247[.]123
0909cf95903c9f07651f4361b8e929c53a62162f6eaaeb11b0dd70eaef2c2784
129.6.15[.]28
239.255.255[.]250
34a265197110995c087e43edde1d1425b1c4c809443491b480cdef4d89a1d302
39a2a0e55cd35c5f61c80e3de3335e529778f9602a3aa281d08e38df8df4071c
3cb18e4d9f70b897cf1bba44ceb965522b31da34ace530d8a1fb9f481a9cae3d
642a7f341146d4b2a5381186ec636a8e0ce7ccc16bb730be331e51d6e65f4db3
68d54b631ec36072fe2a833a0a4aa6c131b7f464383cab338a83aff7827ccc06
7d3ff6ad74c57a4df53ada02881d2da8243ba098c6b65bddefd405829729b40b
81e362d1aae7ca2398219edc502323062fbd06845a42a044668ac808362d58e6
9adfca702feeb585a9bb2e370cb27746a9f7bcecce8c4f182cffc411b829226f
c041e7547fc7f9dbbcde766a199fb6226309c60f76795ddfe46da698664f9311
e53e552a44c7746c9b2916b83d5d9c7d5f0f19305b313bde698841509efccdff
ea2db0b533eacf73d3b23f4da806e87be41925251a69108d9eb699b895f4cf80
ef54db47ae752d795e0734e3ea73c4607490cec58e2570818b65681d94a35f4c
fae4297f765a1c93fef48d7bddd8c88e6361dcb7eb9efc7cb10ff050e2157d80
12ca4ad8cd613c8d086cd39a5c6e787c12209f2271ba850817b72eae3cd559da
81.19.131[.]103
83.217.208[.]134
107.189.28[.]160
154.216.17[.]46
154.216.17[.]167
154.216.20[.]89
154.216.20[.]133
154.216.20[.]204
154.216.20[.]224
162.254.34[.]46
185.196.8[.]56
185.196.8[.]68
185.196.8[.]76
185.196.10[.]135
185.196.11[.]18
193.124.205[.]63
198.251.84[.]107
43.143.130[.]50
58.56.172[.]234
60.222.237[.]158
61.157.153[.]24
101.207.142[.]35
112.216.232[.]82
113.240.239[.]242
115.239.173[.]226
117.141.0[.]134
118.112.188[.]39
123.52.136[.]150
123.135.104[.]58
183.215.11[.]163
183.230.82[.]22
183.237.57[.]250
191.97.7[.]106
218.59.172[.]213
218.66.5[.]17
222.87.204[.]236
222.249.226[.]134
223.95.119[.]193




