In yet another reminder of the dangers posed by infostealer malware, the emerging Arkana ransomware group has claimed responsibility for a massive breach of WideOpenWest (WOW!), one of the largest Internet Service Providers (ISPs) in the United States.
The attack, which Hudson Rock researchers trace its origins to an infostealer infection back in September 2024, has allegedly compromised over 403,000 customer accounts and given the attackers control over critical backend systems. This incident underscores the growing threat of infostealers as a precursor to ransomware attacks—and the urgent need for organizations to prioritize infostealer monitoring to prevent such breaches.
A Breach Showcased with a Music Video
The cybersecurity community first learned of the breach through a post by vx-underground on X, where the Arkana ransomware group proudly showcased their intrusion. In a bizarre twist, the group even created a music video montage to illustrate the extent of their access.
The video, shared in the tweet, reveals three distinct URLs that Arkana accessed during the attack:
- wowinc.symphonica.com
- wowway.com (at the 0:12 mark)
- appiancloud.com (at the 0:15 mark)
Arkana ransomware group claims to have compromised an Internet Service Provider in California.
— vx-underground (@vxunderground) March 25, 2025
They were even nice enough to put together a music video montage illustrating the level of access they possess. pic.twitter.com/3DYHFLaq5H
These URLs point to critical systems used by WideOpenWest, including the Symphonica admin panel and AppianCloud infrastructure, both of which are now under the control of the ransomware group.
Arkana has not only stolen sensitive data but is also attempting to blackmail WOW! with the threat of leaking or selling the information. They even claimed they have the ability to push malware to the company’s customers.
The Infostealer Connection: A Preventable Disaster
What makes this breach particularly frustrating is its origin: an infostealer infection on an employee’s computer in September 2024.
Our investigation reveals that the credentials for all three URLs—wowinc.symphonica.com, wowway.com, and appiancloud.com—were harvested from this infected device. Infostealers, as we’ve covered extensively on Infostealers.com, are a type of malware designed to steal credentials, authentication cookies, and other sensitive data. Once stolen, these credentials are often sold on the dark web or used directly by threat actors to gain unauthorized access to systems.
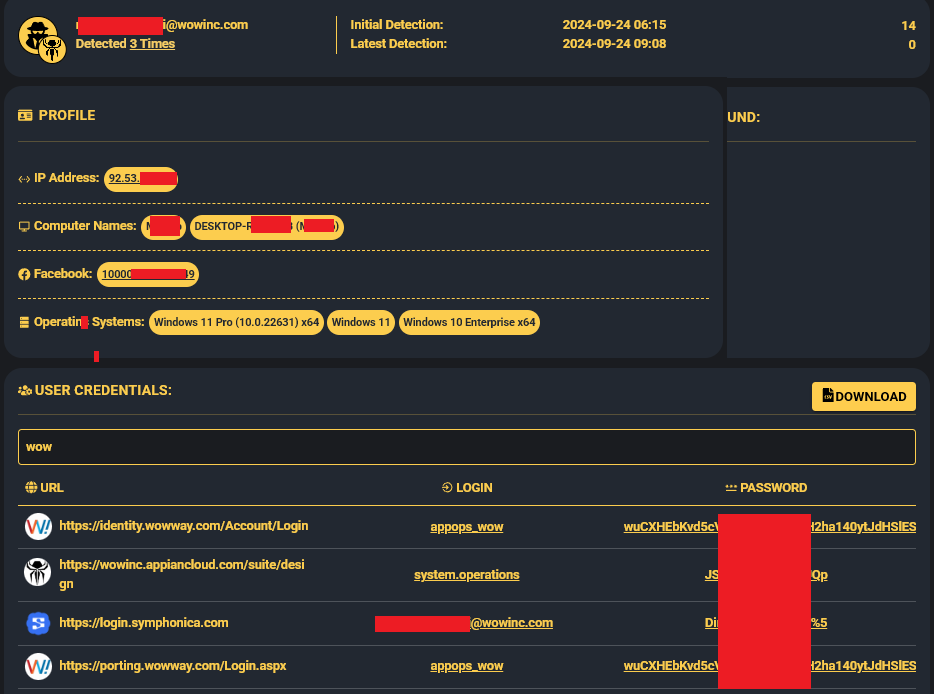
In this case, the stolen credentials gave Arkana a foothold into WideOpenWest’s infrastructure. From there, they were able to move laterally, exfiltrating data and seizing control of critical systems like the Symphonica admin panel (used for managing customer accounts) and AppianCloud (a platform for business process management). The result? A ransomware attack that has put the personal information of over 403,000 customers at risk, not to mention the operational disruption to one of the largest ISPs in the U.S.
Why This Was Preventable—and What WOW! Should Have Done
The Arkana ransomware attack on WideOpenWest could have been stopped in its tracks with proper infostealer monitoring and rapid response protocols. Here’s why:
Early Detection of Infostealer Activity: Infostealers often leave traces of their activity, such as unusual outbound connections or the presence of known infostealer malware on a device. If WideOpenWest had deployed robust endpoint detection and response (EDR) tools, they might have caught the infection on the employee’s device back in September 2024.
Credential Reset and Monitoring: As soon as an infostealer infection is detected, organizations must immediately reset all potentially compromised credentials and monitor for unauthorized access attempts. In this case, the stolen credentials for wowinc.symphonica.com, wowway.com, and appiancloud.com sat unused for months, giving Arkana plenty of time to plan their attack.
Multi-Layered Security for Critical Systems: The fact that Arkana was able to access and control systems like Symphonica and AppianCloud suggests a lack of multi-factor authentication (MFA) or network segmentation. These basic security measures can significantly slow down attackers, even if they have valid credentials.
The reality is that infostealers are a gateway to far more damaging attacks, as we’ve seen time and again. WideOpenWest’s breach is just the latest in a long line of incidents that could have been prevented with proactive monitoring and a strong cybersecurity posture.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by infostealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





