The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of malware: Infostealers.
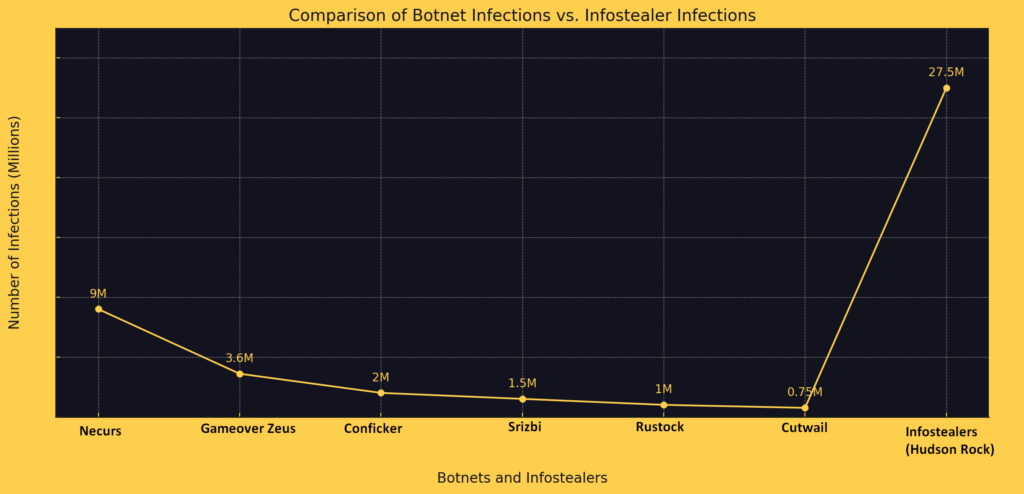
According to Hudson Rock’s cybercrime intelligence database, which tracks historical data on Infostealer infections, there have been 27,500,000 recorded instances of these attacks.
This staggering number highlights the growing prevalence and danger of infostealers in the world of cybercrime.
The Decline of Botnets
Botnets, once the dominant force in cybercrime, have seen a decline in prominence. These networks of compromised computers, controlled by cybercriminals, were notorious for their use in distributed denial-of-service (DDoS) attacks, spam email distribution, and large-scale data theft. High-profile botnets such as Necurs, Gameover Zeus, and Conficker wreaked havoc across the globe, infecting millions of machines and causing billions in damages.
However, several factors have contributed to the decline of traditional botnets:
- Enhanced Cybersecurity Measures: Improved detection and prevention technologies, along with coordinated efforts by law enforcement agencies and cybersecurity firms, have led to the takedown of many major botnets.
- Legal and Technical Actions: Coordinated international actions, such as the dismantling of the Necurs botnet by Microsoft and its partners, have significantly disrupted botnet operations.
- Shift in Cybercriminal Strategies: Cybercriminals have increasingly turned to more covert and financially lucrative methods, such as ransomware and infostealers.
The Rise of Infostealers
Infostealers have emerged as the preferred tool for cybercriminals due to their efficiency and profitability. These malware variants are designed to stealthily infiltrate systems and exfiltrate sensitive information, such as login credentials, financial data, and personal information. The stolen data is then sold on the dark web or used for further cyber attacks.
Key Factors Driving the Popularity of Infostealers:
- Low Detection Rates: Infostealers often operate quietly in the background, making them difficult to detect. They can evade traditional antivirus software and remain undetected for long periods.
- High Return on Investment: The data harvested by infostealers is highly valuable. Login credentials, for example, can be sold to multiple buyers, providing a high return on investment for cybercriminals.
- Ease of Distribution: Infostealers can be distributed through various vectors, including phishing emails, malicious websites, and software exploits. This versatility makes them easy to deploy on a large scale.

Infostealers vs. Botnets: A Comparison
When comparing the historical impact of Windows botnets to the recent surge in Infostealer infections, the numbers speak for themselves. Botnets such as Necurs, Gameover Zeus, and Conficker had infection numbers in the millions, with Necurs being one of the largest at 9 million infections. In contrast, Infostealer infections have reached an unprecedented 27,500,000 cases according to Hudson Rock’s database. This threefold increase highlights the shift in cybercriminal tactics and the growing prominence of Infostealers in the cyber threat landscape.
Case Studies Highlighting the Impact of Infostealers
Recent incidents underscore the severe consequences of infostealer infections:
- Healthcare Sector Breach: A single compromised Citrix credential resulted in a $22,000,000 ransom demand, demonstrating the high stakes of Infostealer-related breaches.
- Airbus Incident: Cybercriminal “USDoD” leaked sensitive data from Airbus, exposing personal information of 3,200 vendors. The breach was traced back to an employee at Turkish Airlines whose computer was infected with RedLine Infostealing malware.
- Orange Employee Incident: An infostealer infection of an Orange employee led to disruptions in Border Gateway Protocol (BGP) routing, highlighting the far-reaching implications of these attacks.
As Infostealers continue to evolve and become more sophisticated, organizations must remain vigilant and adopt robust cybersecurity measures. The shift from botnets to infostealers represents a new era in cyber threats, one that requires adaptive strategies and proactive defense mechanisms to protect sensitive information and maintain cybersecurity.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock