Recently, Rasta Mouse, a well-known cybersecurity researcher and founder of Zero-Point Security Ltd, became the target of an alarming attack that resulted in a staggering loss of £10,000. This incident, which took place while he was selling cybersecurity courses through his company’s website, highlights a new dimension of financial DDoS attacks that combine elements of Infostealer malware and payment fraud.
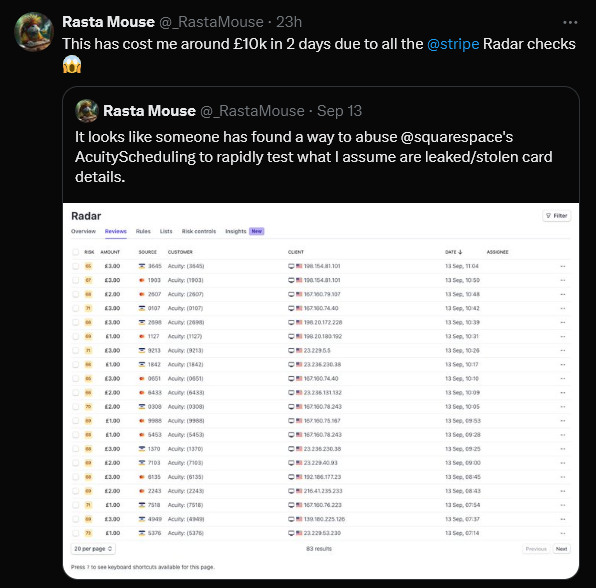
Although the exact details of the attack remain unclear, it seems likely that this breach involved a dangerous combination of Infostealer malware and the way Stripe Radar handles fraud detection. Here’s a closer look at how the attack may have unfolded:
How the Attack Worked
1. Infostealer Credentials Compromised
The first step in the attack was the theft of credentials. Infostealer malware was used to capture login details for Squarespace’s Acuity Scheduling platform, which is commonly used for scheduling payments. Thousands of login credentials to this platform have been seen in Infostealer logs through Hudson Rock‘s platform , suggesting that a threat actor was aggregating stolen data on a large scale.
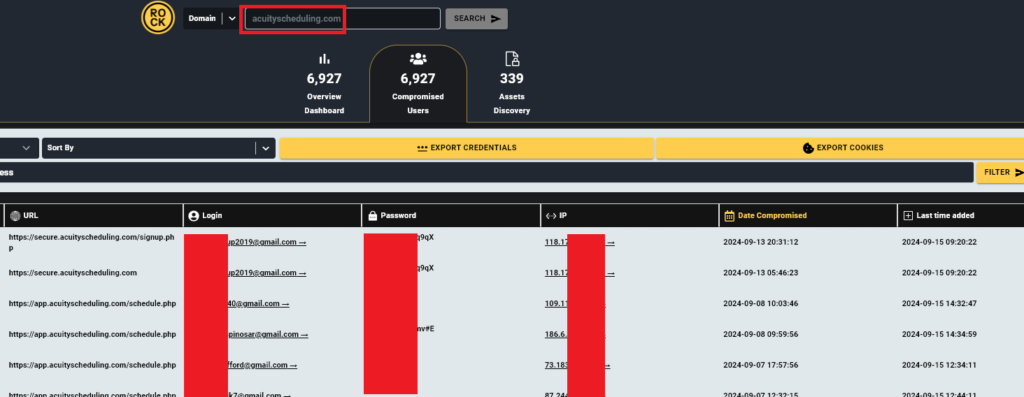
2. Credential Stuffing Attack
Once they had access to these stolen credentials, the attackers began a brute-force entry operation. Using credential stuffing, they attempted to break into as many accounts as possible. Acuity Scheduling, with its payment integrations, proved a prime target.
3. Exploiting Linked Payment Methods
Upon successfully accessing accounts, the attackers discovered linked payment methods, particularly credit card details. They then used these stolen cards to conduct automated transactions, essentially testing the validity of the stolen card data.
4. Financial Impact
As these fraudulent transactions piled up, Stripe Radar, a system designed to detect and prevent fraud, was triggered. However, instead of protecting the researcher, Stripe Radar’s checks led to high fees and chargebacks, inflicting severe financial damage. Within just two days, this relentless series of fraudulent transactions resulted in a loss of £10,000.
Financial DDoS: A Devastating Tactic
This attack demonstrates how cybercriminals can effectively launch a form of financial DDoS (Distributed Denial of Service) through stolen credit card abuse. By overwhelming the payment system with fraudulent transactions, they not only test the stolen card data but also cause significant financial losses to their victims. This type of attack has the potential to wreak havoc on businesses, particularly those that rely on automated payment platforms.
Preventative Measures
What makes this incident particularly concerning is that with proper Infostealer credentials monitoring, this entire breach might have been avoided. Proactive monitoring of credentials, especially for platforms like Acuity Scheduling, can help detect unauthorized access before it escalates into a full-blown financial attack. For businesses and individuals alike, it’s a critical reminder to regularly check for exposed credentials on their domains.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





