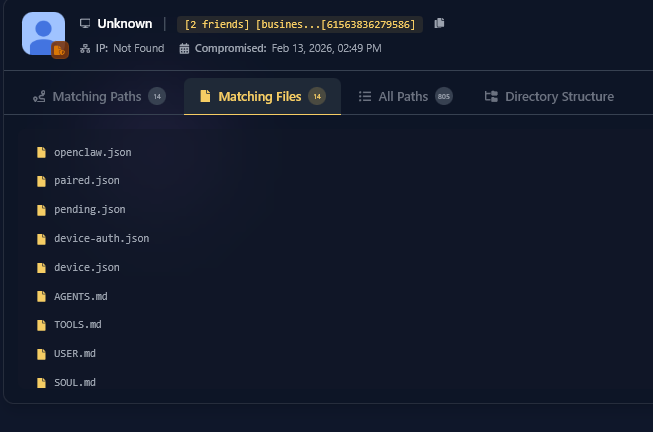
In case you missed it, hackers have been utilizing a new technique to infect victims with Infostealers, it is done by setting a fake Captcha page that prompts the victim to paste a powershell command into their Windows Run which causes a Lumma Infostealer infection.
But does it actually work?
In reality, the Infostealer infection method works too well actually.
Hudson Rock has spotted thousands of computers that were infected using this method just this month, here is a real scenario from a victim’s computer showing how it went down:
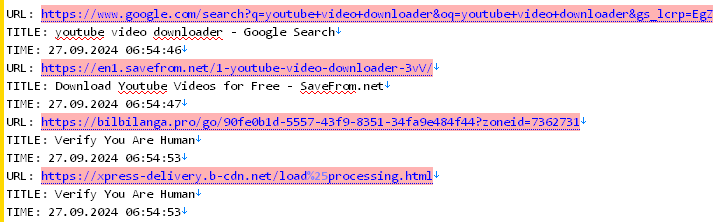
Infection Timeline:
1. Search for a YouTube video downloader:
The user searched for “youtube video downloader” at 06:54:46 and clicked on a link from the search results.
2. Visit to a suspicious site:
They landed on SaveFrom.net, a well-known video downloading website, but were quickly redirected to suspicious sites with “Verify You Are Human” prompts at 06:54:53.

3. Fake CAPTCHA scam:
The “Verify You Are Human” page showed a fake CAPTCHA, asking the user to copy and paste a PowerShell command into their computer. This technique eventually leads to an Infostealer infection.
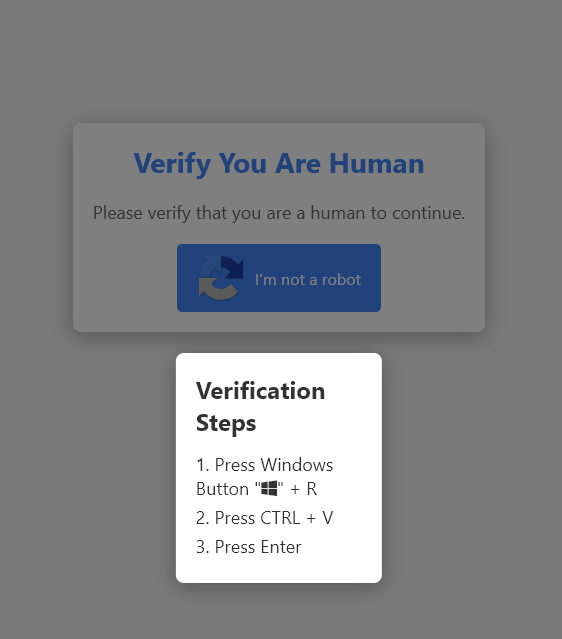
4. Infection by Lumma:
When the user followed the instructions and ran the PowerShell command, they unknowingly installed Lumma malware on their system.
5. You’re F***ed, but at least Hudson Rock has your back:
Hackers have stolen all of your data, including credentials, cookies, browsing history, documents, etc. You will become the target of many kinds of account takeover attempts, fraud, and if you have corporate credentials they will be used to carry out cyberattacks against your employer.
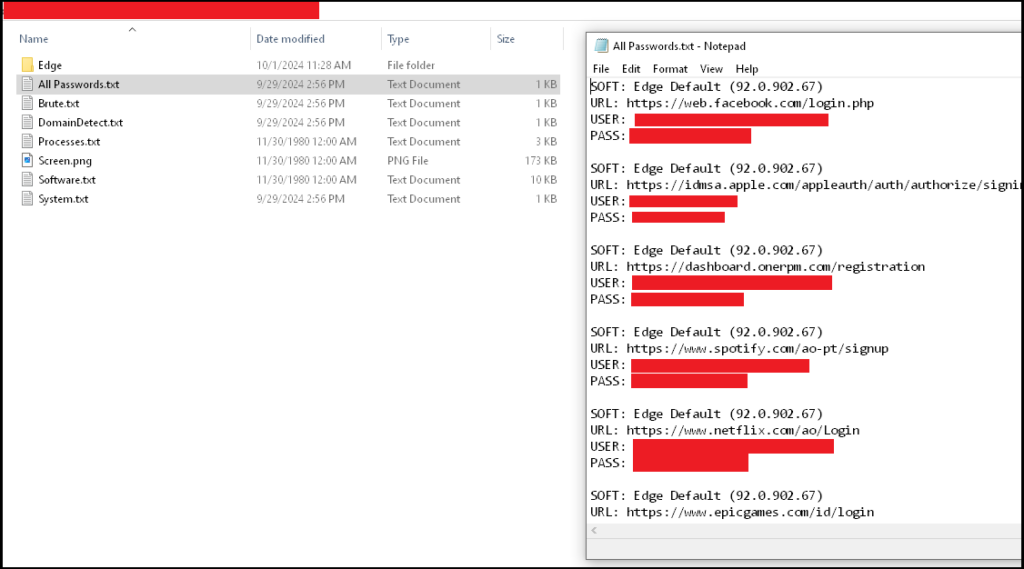
Luckily, Hudson Rock is collecting this data too and every day we alert thousands of companies about stolen credentials belonging to their employees & users.
6. Next steps for you reading this:
Even if you personally weren’t infected and you wouldn’t paste a powershell command because a captcha told you to, you can probably think of someone who works with you who you’re thinking “oh wow they’ll fall for it for sure”.
If that’s the case you can feel free to ask us for an ethical disclosure about Infostealer infections in your organization after searching your domain using our Infostealer intelligence tools – www.hudsonrock.com/are-you-compromised
Thanks for reading, share this to raise awareness about this ongoing campaign.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock