Executive Summary
- FBot is a Python-based hacking tool distinct from other cloud malware families, targeting web servers, cloud services, and SaaS platforms like AWS, Office365, PayPal, Sendgrid, and Twilio.
- FBot does not utilize the widely-used Androxgh0st code but shares similarities with the Legion cloud infostealer in functionality and design.
- Key features include credential harvesting for spamming attacks, AWS account hijacking tools, and functions to enable attacks against PayPal and various SaaS accounts.
- FBot is characterized by a smaller footprint compared to similar tools, indicating possible private development and a more targeted distribution approach.
Overview
The cloud hacktool scene is highly intertwined, with many tools relying on one another’s code. This is particularly true for malware families like AlienFox, Greenbot, Legion, and Predator, which share code from a credential scraping module called Androxgh0st.
We identified a tool that is related but distinct from these families. FBot is a Python-based attack tool with features to target web servers and cloud services as well as Software-as-a-Service (SaaS) technologies, including:
- Amazon Web Services (AWS)
- Office365
- PayPal
- Sendgrid
- Twilio
FBot is unique in that it does not apparently adapt the Androxgh0st code so common among similar hacktools, though the earliest reference to FBot is one year more recent than the first sighting of Androxgh0st. However, there are several connections to the Legion cloud infostealer, making it likely the Legion maintainer adapted code from FBot into their tool.
FBot is primarily designed for actors to hijack cloud, SaaS, and web services. There is a secondary focus on obtaining accounts to conduct spamming attacks. Actors can use the credential harvesting features to obtain initial access, which they can sell to other parties.
The tool contains assorted utilities, including an IP address generator and port scanner. There is also an email validator function, which uses an Indonesian technology service provider to validate email addresses.
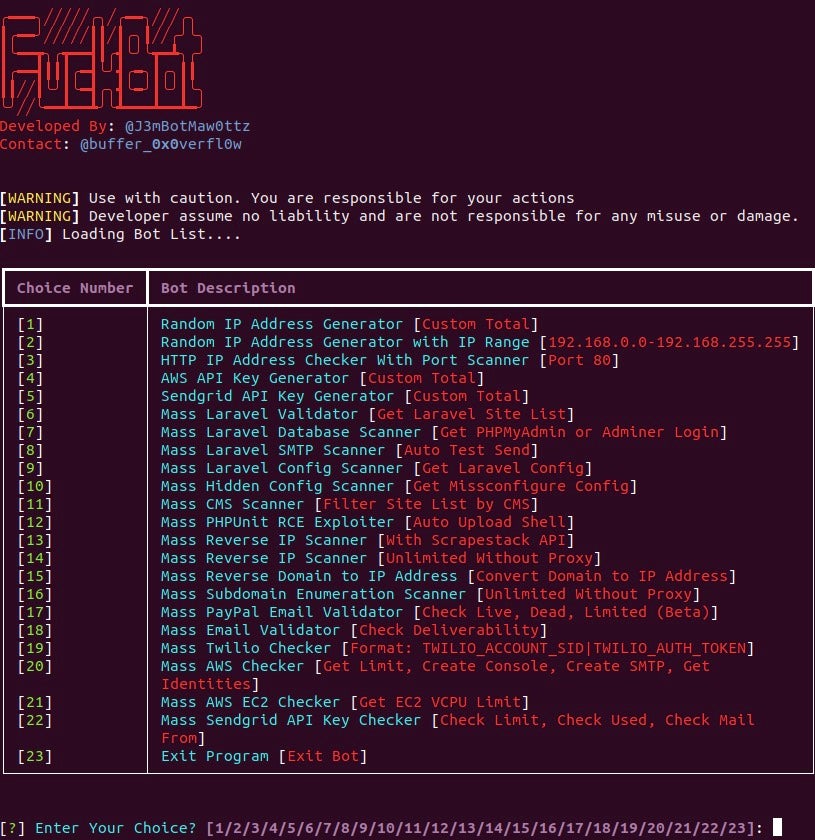
AWS Targeting
FBot has three functions dedicated to AWS account attacks. The first is an AWS API Key Generator, handled by function aws_generator, which generates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the standard AKIA prefix. Then, it generates a secret key from 40 randomly selected alphabetic characters.
Despite FBot’s apparent lack of adopting the Androxgh0st modules, the same feature was highlighted in research on the Legion stealer as well as an older Androxgh0st variant, and it has not changed significantly. We agree with the aforementioned researchers’ conclusion that this feature is unlikely to succeed at brute forcing account credentials due to the possible number of access key and password combinations.
The second AWS feature is a Mass AWS Checker, handled by function aws_checker. This function checks for AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as how many messages have been sent in the past 24 hours, likely to maximize spamming efforts against the targeted account. It also creates a new user account with the username iDevXploit and the password MCDonald2021D#1337 and attaches the AdminsitratorAccess policy to elevate privileges for the new account. Unlike other cloud attack tools such as AlienFox, FBot does not delete the compromised account that the attacker used to gain access.
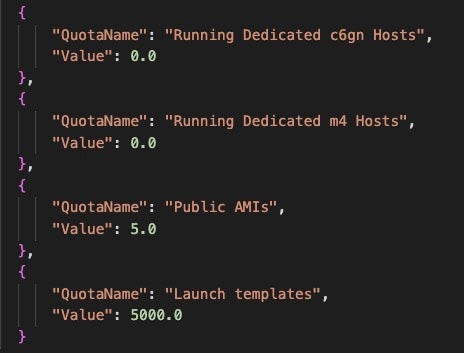
The third and final AWS feature is an AWS EC2 Checker, with the description Get EC2 VCPU Limit, which is handled by function ec_checker. This function reads a list of AWS identities from a text file in the format of AccessKey|SecretKey|Region. The script uses these values to check the targeted account’s EC2 service quotas. The FBot menu highlights that this can be used to check vCPU details, although the output is less straightforward. The query results describe the account’s EC2 configurations and capabilities, such as what types of EC2 instances can run. The script iterates through a list of specified AWS regions, runs the query again for each region, and logs the result to a text file.
SaaS & Payment Services Targeting
FBot has several features that target payment services as well as SaaS configurations.
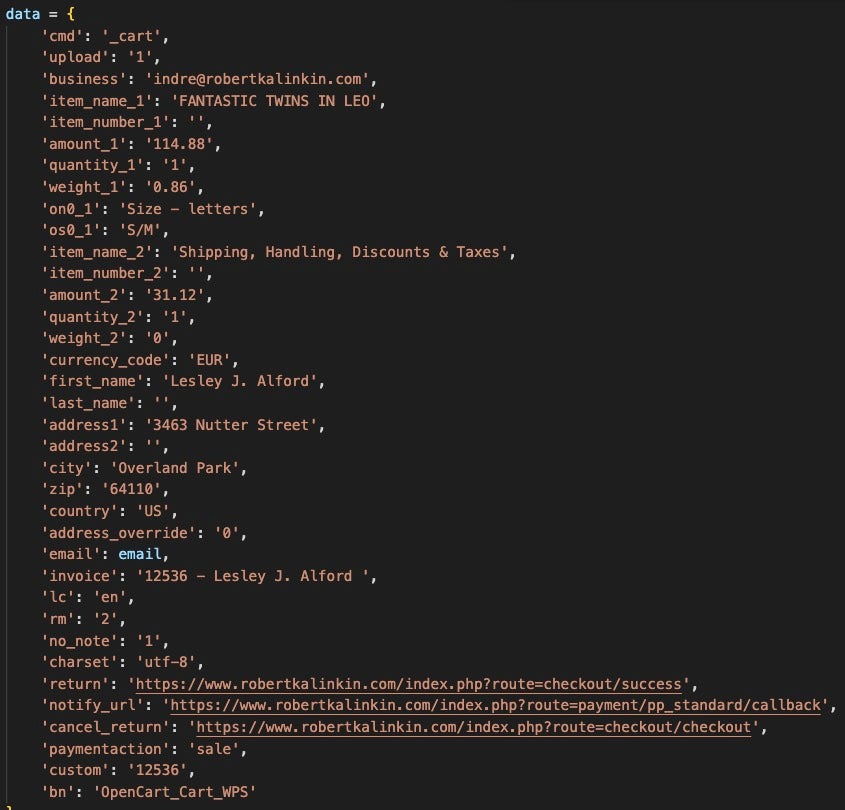
The PayPal Validator feature is handled by paypal_validator. This function validates PayPal account status by contacting a hardcoded URL with an email address read from an input list. The email is added to the request in the customer details section to validate whether an email address is associated with a PayPal account.
The script initiates the Paypal API request via the website hxxps://www.robertkalinkin.com/index.php, which is a Lithuanian fashion designer’s retail sales website. Interestingly, all identified FBot samples use this website to authenticate the PayPal API requests, and several Legion Stealer samples do as well.
PayPal Validator crafts the request to this site with a fake item ID as well as phony customer details, then parses the response for a status message indicating success.
FBot also targets several SaaS platforms, including Sendgrid and Twilio. The Sendgrid feature is a Sendgrid API Key Generator, which generates a Sendgrid key formatted like:SG.{22 characters from [A-Z0-9-_]}.{1 more character from previous range}
The Twilio feature takes the Twilio SID and Twilio Auth Token as input, separated by a pipe. The function then checks the SID & auth token combination for details about the account, including the balance and which currency, a list of phone numbers connected to the account.
Web Framework Features
FBot has features for validating if URLs host a Laravel environment file and for extracting credentials from those files. The Hidden Config Scanner feature takes a URL as input and crafts an HTTP GET request to several PHP, Laravel, and AWS-related URIs where configuration values may be stored, including:
| _profiler/phpinfo | config.js |
| .env | config/aws.yml |
| .env.bak | info.php |
| aws.yml | phpinfo |
| aws/credentials | phpinfo.php |
The response is parsed for keys and secrets related to the following services and the result is written to a text file:
| AWS | MandrillApp |
| Coinpayments | Office365 |
| DB_USERNAME (generic database) | Plivo |
| Ionos | Sendgrid |
| MAIL_PASSWORD (generic SMTP) | Twilio |
| Mailgun |
FBot also targets several popular Content Management Systems (CMS). The function cms_scanner contains a map of CMS and web frameworks to regular expressions (regex) associated with the service. The program creates a request to the targeted URL and parses the response for the following technologies:
| Codeigniter | Laravel | phpBB |
| Discuz | Lithium | PrestaShop |
| Drupal | Magento | vBulletin |
| Esportsify | MediaWiki | Whmcs |
| FluxBB | Moodle | WordPress |
| Invision | Ning | YetAnotherForum |
| Jive | OpenCart | ZenCart |
| Joomla | osCommerce | Zimbra |
Taxonomy
FBot relies on configuration values to be fed to it through a configuration file (.ini), or through headers that initiate the main class. We identified one version that is compiled as a Windows executable.
The string iDevXploit is present across all samples: this handle is credited as the author in the main class. Additionally, the aws_checker function leaves artifacts in targeted AWS consoles: when FBot creates a new user in the AWS account, the username iDevXploit is consistent across samples, along with the password MCDonald2021D#1337.
Unlike many similar cloud hacktools, FBot does not contain references to the open-source Androxgh0st code found in tools like AlienFox, GreenBot, and Predator. The logic implemented is very similar in that both Androxgh0st and FBot parse environment configuration files for credentials related to similar mail & cloud services, but the implementation is different and no code seems to be directly borrowed.
There is considerable overlap with the Legion cloud infostealer in how the tools scrape URLs for PHP configuration. However, FBot is much smaller and less fully featured than Legion, with FBot samples weighing in at approximately 200 KB and Legion ranging from 800-1200 KB in size.
Conclusion
FBot demonstrates another tool family that continues the trend of adopting cloud attack tool code from one tool into another, while maintaining its own distinct flavor. We have seen samples spanning July 2022 to January 2024, showing there is continued proliferation of this tool. However, there are relatively few changes across versions and it is unclear whether this is actively maintained.
As of this writing, we are unable to identify a distribution channel dedicated to FBot, which differentiates the tool from other cloud infostealers often sold on Telegram. The bot has references to buffer_0x0verfl0w, a Telegram channel associated with various crimeware that has since been retired. However, we found indications that FBot is the product of private development work, so contemporary builds may be distributed through a smaller scale operation. This aligns with the theme of cloud attack tools being bespoke ‘private bots’ tailored for the individual buyer, which is a theme prevalent among AlienFox builds.
Organizations should enable multi-factor authentication (MFA) for AWS services with programmatic access. Create alerts that notify security operations teams when a new AWS user account is added to the organization, as well as alerts for new identities added or major configuration changes to SaaS bulk mailing applications where possible.
Indicators of Compromise
| SHA1 | Notes |
| 1ad78e99918fd66ed43d42a93d2f910a2173b3c5 | Bot.py, January 2024 version of FBot |
| 2becd32162b2b0cb1afc541e33ace3a29dad96f1 | April 2023 version of FBot |
| 8ba3fca4deada6dbdc94b17a0c3c55a0b785331e | Bot.py, July 2022 version of FBot |
| iDevXploit | Hardcoded AWS IAM Username |
| MCDonald2021D#1337 | Hardcoded AWS IAM User password |





