This article aims to shed light on the identity behind a massive Discord spying tool and raise concerns about the possibility of private Discord data being accessed by hackers.
Intro
A controversy surrounding the anonymously-run website spy.pet has recently made headlines, raising serious privacy concerns.
The website is designed to enable anyone to access messages from over 300,000,000 Discord users across 8,000 Discord servers.
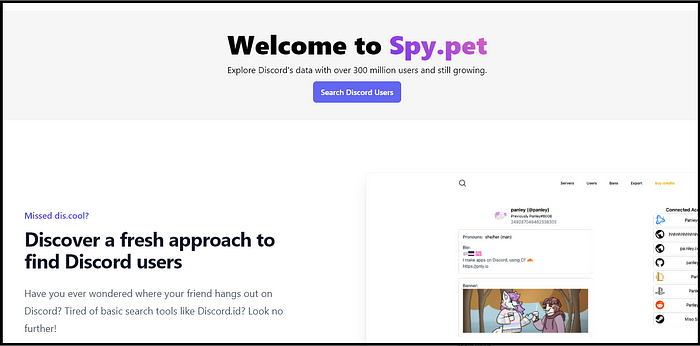
Following privacy-related allegations against spy.pet, the website was shut down by its hosting provider. Although Discord threatened the anonymous founder with ‘appropriate legal actions,’ it appears that the website has been relaunched and is currently operating under a new domain — spy(.)pm.”
Infostealing malware infection of spy.pet’s owner
In recent years, infostealing malware infections have been on the rise. With over 500,000 computers infected every month due to downloading fake software, it is not uncommon for even the most tech-savvy individuals to fall victim. One such victim happened to be the owner of spy.pet.
On April 11, 2023, a computer with a Japanese IP was infected by a Raccoon type Infostealer, resulting in over 4420 (!) credentials being stolen from the computer.
Hudson Rock’s automated sorting which categorizes credentials into employees and users based on their sensitivity, identified over 37 sensitive credentials used for the infrastructure of spy.pet:
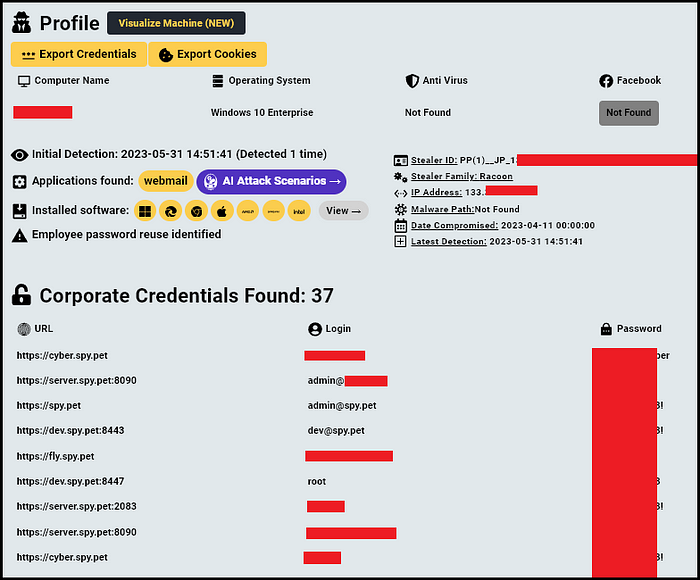
Credentials which are stored on browsers are almost guaranteed to work and due to the sensitivity of the credentials that were exfiltrated from the computer (webmail.spy.pet, server.spy.pet, dev.spy.pet) it is likely that hackers who obtained the same data were able to hack into spy.pet and possibly steal the massive 300,000,000 Discord users database.
If true, this could indicate that the massive database of spy.pet is circulating among hackers, or potentially even being sold.
This is especially critical because Infostealers data is actively bought by hackers with the specific intention of breaching into organizations, accounts, and services-

Owner’s Identity
From the moment spy.pet was launched, it is likely that the owner knew that the website would be considered illegal and made attempts to conceal their identity. This is evident in the absence of any information relating to the owner or team behind the project on the website.
Following the controversy surrounding spy.pet and Discord’s active attempts to take appropriate legal action, it was safe to assume that unless the culprit’s identity could be found using traditional methods, Discord would likely come up empty-handed.
This is when the Infostealer infection comes to play — once a computer is infected by an Infostealer, typically any hopes for the privacy of the victim is lost due to the massive amounts of data that is being captured —
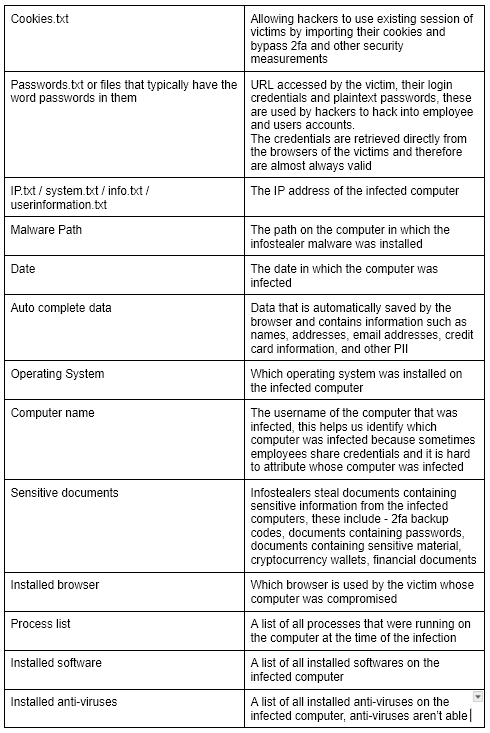
And while the specific Infostealer infection of spy.pet’s owner did not result in the retrieval of much of the aforementioned data, Hudson Rock’s researchers were still able to analyze the data and identify the owner’s identity.
For example, grouping the email addresses found on the computer by their occurrences results in several email surfacing as the most commonly used by the owner:

A simple investigation around these email addresses reveal the owner’s real identity on a Github account:

In another example, the full name of the owner appears simply as the username to one of the services.
In addition, spy.pet’s owner is registered to a significant amount of cybercrime forums, indicating their interest in cybercrime:

Hudson Rock will share this information with Discord, hopefully aiding in shutting down any future attempts to launch spy.pet.
Infostealer infections as a cybercrime trend surged by an incredible 6000% since 2018, positioning them as the primary initial attack vector used by threat actors to infiltrate organizations and execute cyberattacks, including ransomware, data breaches, account overtakes, and corporate espionage.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
Hudson Rock provides access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools