
EXECUTIVE SUMMARY
At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors who target organizations and individuals. The ‘Iluria Stealer’ is a new malware variant created by the same developer behind the Nikki Stealer, who uses the alias ‘Ykg”. Both share similar code with SonicGlyde; a discord stealer, which is a variant of the Epsilon Stealer, which captures browser cookies, credentials, and credit card information saved in Discord. This time, four individuals are managing the Iluria Stealer: Ykg, Noxty, Outlier, and Ness.
INTRODUCTION
In addition to the above, the ‘Iluria Stealer’ is also an NSIS installer that includes an obfuscated Electron app. This app decrypts malicious code during runtime to steal Discord tokens and browser credentials, and in the second stage, downloads a malicious JavaScript file that replaces Discord’s index.js file. This injected file intercepts any account changes, like password and email updates or 2FA activation, and sends this information back to the attacker’s command and control (C2) server.
Once a victim’s account is compromised, the hacker uses their account and browser information to either ransom the user or target new victims. They can also search through browser data for other accounts that can be exploited, such as crypto exchanges, and bank accounts.
ASSESSMENT
File Namedskadksa-1d7Izx3B5.exeFile Size71.27 MbSignedNot SignedMD5 Hashf13115afbc6c7440771aa8b26daa1494SHA-256 Hashb66ce85c6942855970fe939a31459e5b7489e6d2c4bbe0d9d89cb8a863082e1cFirst Seen in the WildMay 2024
At the time of writing this report, VirusTotal shows zero detections for this stealer.

The primary executable file i.e. ‘dskadksa-1d7Izx3B5.exe’ is built using the Electron framework, storing its source code and essential files within a resource file which typically contains an “app.asar” file (that serves as the main source of code and important resources).
The file i.e. app.js is highly obfuscated, but we managed to identify most of the functions used by this malware by debugging the code in Visual Studio Code:

The stealer initially fetches IP address information by using the ipinfo[.]io domain. This step allows the attacker to gather geolocation data and other details about the victim’s network environment.

The malware is also targeting Discord by manipulating its desktop application. It specifically focuses on the index.js file located within the Discord desktop core module and modifies it by injecting malicious code. This modification includes making GET requests to the Command and Control (C2) server api[.]nikkistealer[.]shop. The responses from these requests are appended to the index.js file, ensuring that the malicious code runs whenever Discord is started.

This function steals saved browser passwords by extracting and decrypting them from the browser’s local data files. It reads the encryption key from the ‘Local State’ file and decrypts passwords stored in the ‘Login Data’ file, compiling the credentials into a list categorized by browser type.

The browser Autofill function steals data by copying and reading the ‘Web Data’ file from the browser’s local storage, extracting names and values from the autofill database to formulate a list categorized by browser type.

The browser Cookies function works by copying and reading the ‘Cookies’ database from the browser’s local storage and decrypting them using extracted encryption keys. This data is also compiled into a list categorized by browser type.

This function terminates specified processes on a Windows system by obtaining a list of running tasks potentially used for analysis, and then filtering the specified processes to those currently running. ‘taskkill` is used to terminate each one.

Discord tokens are unique identifiers that grant access to a user’s account, similar to a username and password combination. Once an attacker steals the token, they can use the Discord API to perform actions on behalf of the victim, including retrieving information about the user’s profile and any Discord servers they are a member of.
Additionally, the attacker could use the Discord API to check the permissions and roles assigned to the user within Discord servers, which could reveal the level of access the user has within those servers, such as administrative privileges or moderator roles.

The malware appears to be capable of accessing and retrieving payment sources stored within a user’s Discord account in the billing section. This includes sensitive financial information such as credit card details or other payment methods linked to the user’s profile.

During dynamic analysis, we executed the stealer in a sandbox environment and found that it attempts to communicate with the domain api[.]nikkistealer[.]shop.

The stealer uses this configuration to interact with the specified API, indicating its control server and possibly the unique identifier for the infected user.

A WHOIS lookup for the domain `nikkistealer[.]shop` reveals that it is hosted by Hostinger.

During further analysis of the code, we also examined another stealer, ‘SonicGlyde’, which is a variant of the Epsilon Stealer, indicating that the Iluria Stealer is also an indirect variant of the Epsilon Stealer/SonicGlyde.

Recent Development
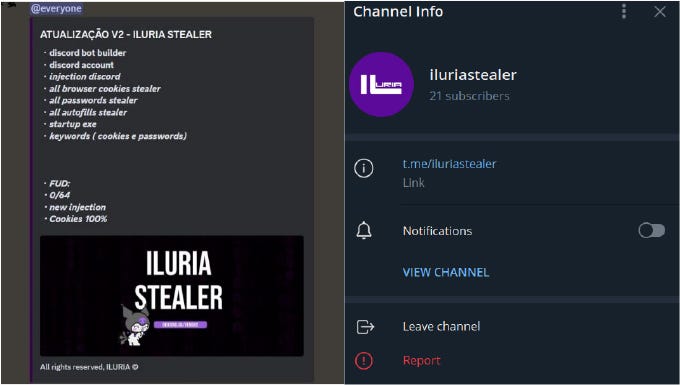
On May 11, 2024, “Ykg,” who claimed to be the developer of Iluria Stealer, announced version 2 of the Iluria Stealer with various subscription plans available.

EXTERNAL THREAT LANDSCAPE MANAGEMENT
The Nikki Stealer channel has transitioned to Iluria Stealer. Their Discord channel has a strong user base of Portuguese speakers. The owner of Iluria Stealer, ‘Ykg’, is the former CEO of Nikki Stealer, as claimed in his Discord bio.

While investigating his YouTube channel, we discovered another website registered with Hostinger, which is similar to the nikkistealer[.]shop.

The developer transformed the Nikki Stealer discord channel into the Iluria Stealer channel and began promoting it. He also created a new Telegram channel for this purpose, which currently has 21 users (albeit no activity).

List of IOCs

MITRE ATT&CK TTPs

CONCLUSION
In summary, the Nikki Stealer group has now become the Iluria Stealer, and while their Discord channel is full of Portuguese speakers, both of their websites are hosted by Hostinger. The owner claims to be the former CEO of Nikki Stealer in their Discord bio, and when we looked at their code, we found out that Iluria Stealer can steal browser passwords, and autofill data and cookies. This group keeps changing and growing, which makes them a serious threat to online security, underlining the importance of staying alert and having strong security measures in place to protect against Iluria Stealer and similar threats.
RECOMMENDATIONS
Strategic Recommendations:
- Implement Defense-in-Depth Strategy: Develop a comprehensive defense strategy that combines network segmentation, robust perimeter defenses, and endpoint security to create multiple layers of protection against such threats.
- Invest in Threat Intelligence: Engage with threat intelligence services to stay informed about the evolving tactics, techniques, and procedures employed by malware operators. Regularly update defenses based on the latest threat intelligence to enhance proactive detection capabilities.
- Enhance Employee Training: Conduct regular cybersecurity training programs to educate employees about phishing threats, social engineering, and safe browsing practices. Building a security-aware culture can significantly reduce the likelihood of successful infostealer infections.
Management Recommendations:
- Develop an Incident Response Plan: Establish a robust incident response plan that outlines clear procedures for identifying, containing, eradicating, and recovering from an Iluria Stealer infection. Regularly test and update the plan to ensure effectiveness.
- Conduct Regular Security Audits: Perform periodic security audits to assess the effectiveness of existing security controls, identify potential weaknesses, and validate the organization’s overall security posture. Use the findings to make informed adjustments and improvements.
- Collaborate with Industry Peers: Engage in information sharing and collaboration with industry peers, cybersecurity communities, and relevant authorities. Sharing threat intelligence and best practices can enhance collective resilience against emerging threats like the Iluria Stealer.
Tactical Recommendations:
- Update and Patch Systems: Regularly update and patch operating systems, software, and applications to address vulnerabilities that malware like Iluria stealer exploits. Automated patch management tools can streamline this process and minimize the attack surface.
- Utilize Advanced Endpoint Protection: Deploy advanced endpoint protection solutions that incorporate behavioural analysis, heuristic detection, and threat intelligence to identify and mitigate the specific techniques employed by Iluria Stealer. Ensure these solutions are regularly updated with the latest detection rules such as the one given in the report.
- Implement Application Whitelisting: Restrict the execution of unauthorized applications by implementing application whitelisting. This helps prevent the execution of unknown or malicious binaries, hindering Iluria Stealer’s ability to run on endpoints.
Iluria Stealer; a Variant of Another Discord Stealer was originally published on CYFIRMA





