- The FBI indicated that there were no law enforcement concerns with the public disclosure of this information.
According to the FBI’s most wanted list — Mujtaba Raza and Mohsin Raza are wanted for allegedly operating a fraudulent online business based in Karachi, Pakistan.
Since at least 2011, the business known as SecondEye Solution (SecondEye), aka Forwarderz, allegedly sold digital images in false identity documents including passports, driver’s licenses, bank statements, and national identity cards associated with more than 200 countries and territories.
SecondEye marketed these fake documents as a mean of verifying online accounts, which allowed SecondEye customers to defraud payment processing companies, e-commerce businesses, social media websites, and social networking platforms.
Due to this, the operators of these companies were put on the FBI’s most wanted list:


Using its cybercrime intelligence database of 29,500,000 infected computers, Hudson Rock researchers identified two separate machines infected by Infostealing malware, associated with Mujtaba Raza, Mohsin Raza, and other key figures not yet identified by authorities.
Computer A — On April 15, 2021, a computer with a Pakistani IP address (103.xxx.xxx.xx) was infected by an Infostealer, it contains various corporate credentials associated with “SecondEye Solution” and “Forwarderz.”
Computer B — On October 9, 2020, a computer with a Pakistani IP address (203.xxx.xx.xx) was infected by an Infostealer, it too contains various corporate credentials associated with “SecondEye Solution” and “Forwarderz.”
These Infostealer infections led to the exfiltration of the following sensitive information from the computers, which formed the basis of our research:
- All login credentials from browsers (URLs, logins, passwords).
- Technical information from the computers such as IP, malware path, infection date, and computer names.
- Entire browsing history from one of the computers.
- Auto-Fill data, which includes sensitive details such as addresses, account numbers, and passport numbers.
Below is the information we believe can help establish a better understanding of SecondEye Solution, Forwarderz, and additional key figures, potentially leading to their arrest.
Key details relating to SecondEye Solution and Forwarderz found on the computers:
By going over the login credentials found on the computers, Hudson Rock researchers were able to locate various infrastructure credentials relating to SecondEye Solution and Forwarderz:
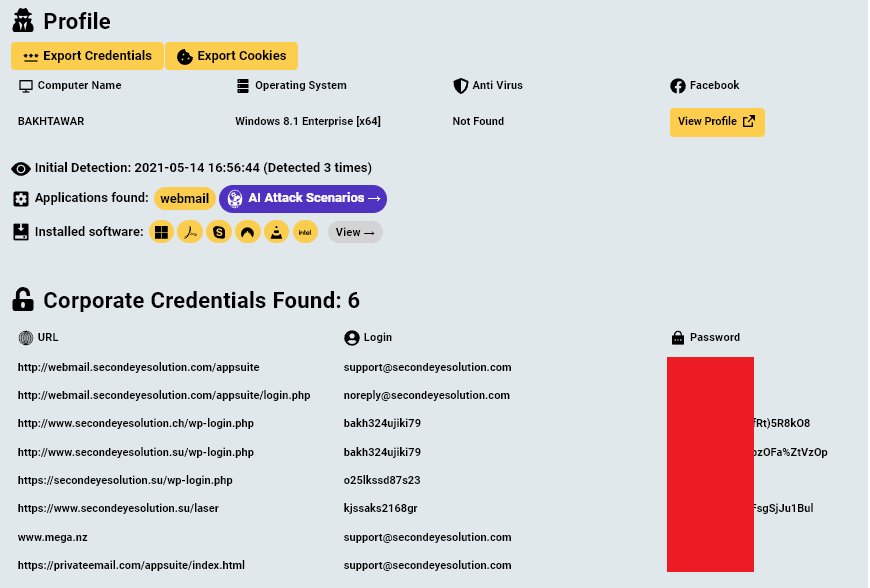
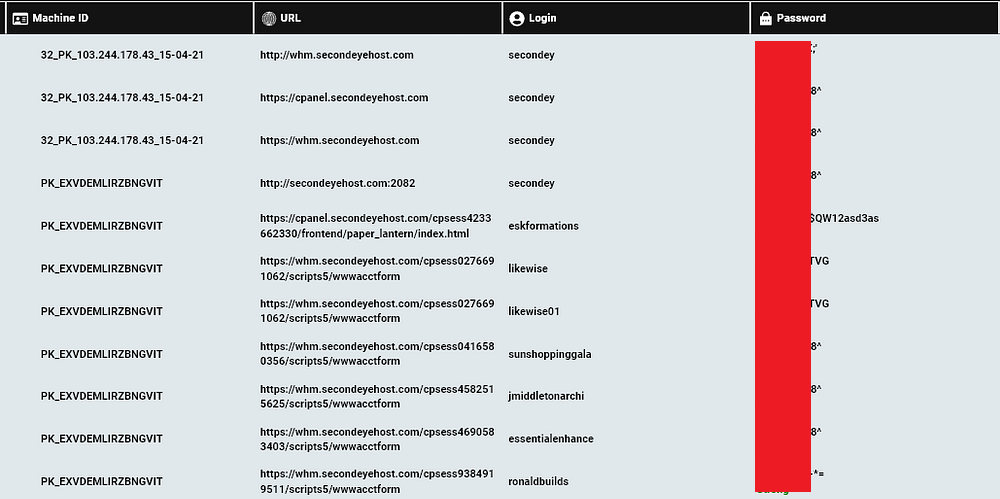
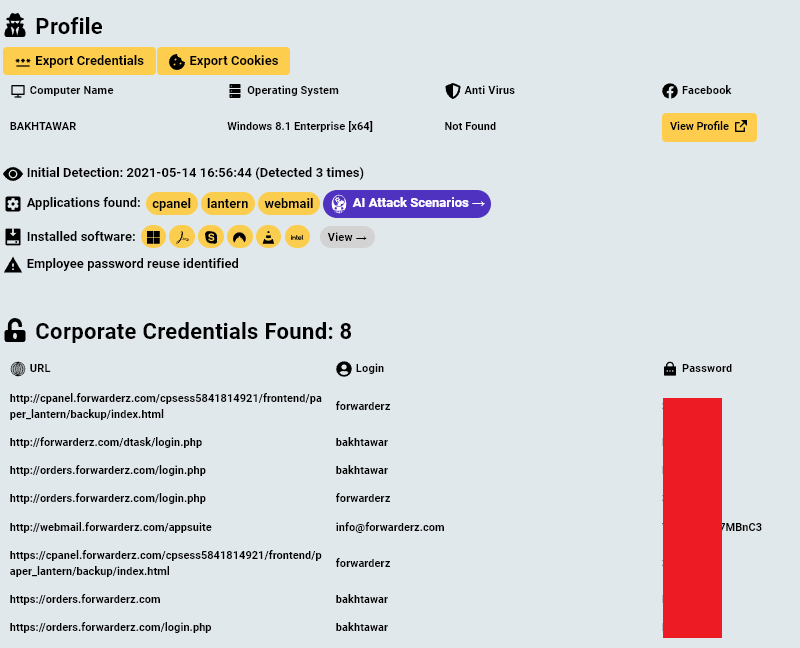
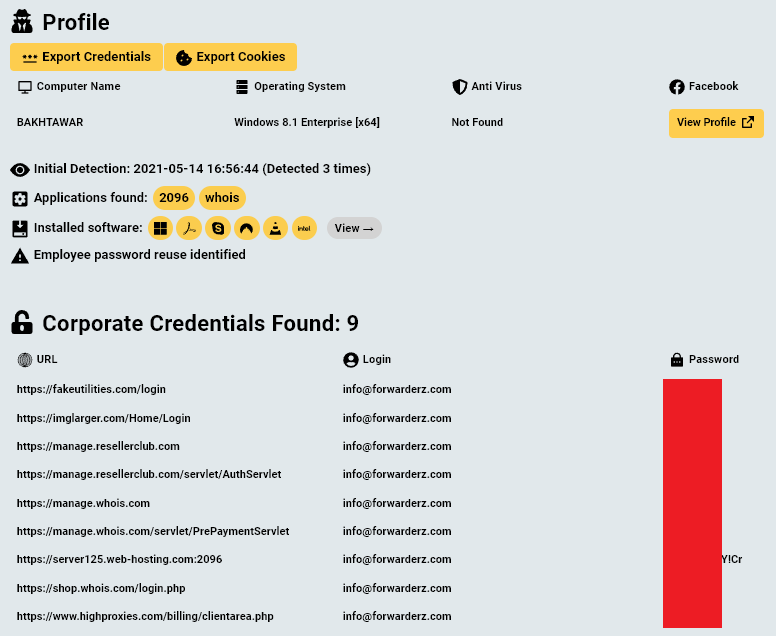
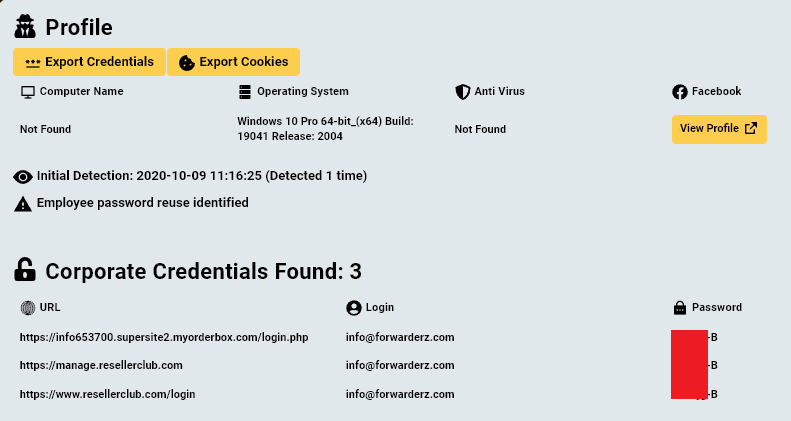
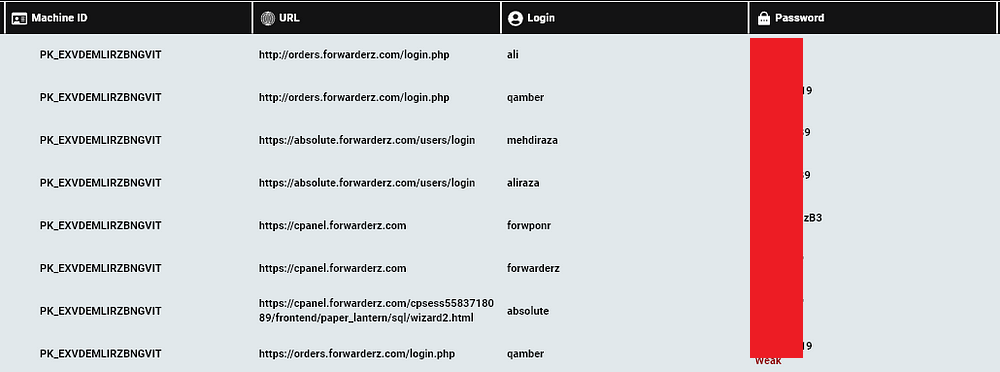
- Additional credentials that are not shown here were also located on the infected computers.
These credentials could aid law enforcement officials to gain additional insight about SecondEye Solution’s operations.
In addition, at the time of the Infostealer infection, a screenshot of computer A. was taken, showing an official Forwarderz skype account and various chats.
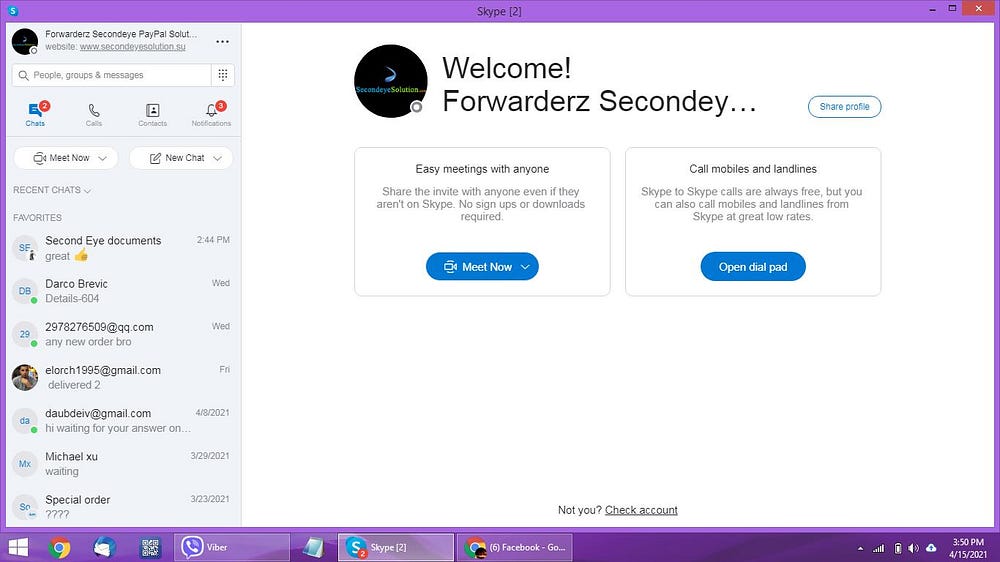
Who do the infected computers belong to?
While the computers do not belong to Mohsin and Mujtaba, it is evident that they belong to highly privileged employees at SecondEye Solution and Forwarderz.
Computer A. —
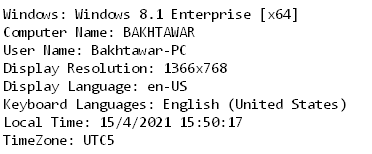
By examining the top logins identified on the computer, we conclude that it belongs to a person named “Bakhtawar Abbas”
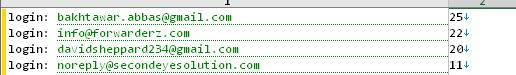
This is supported by the computer’s name — “BAKHTAWAR-PC”
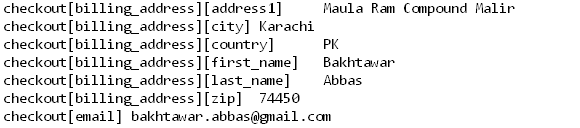
A potential physical address used by Bakhtawar is found in the auto-fill data grabbed by the Infostealing malware —
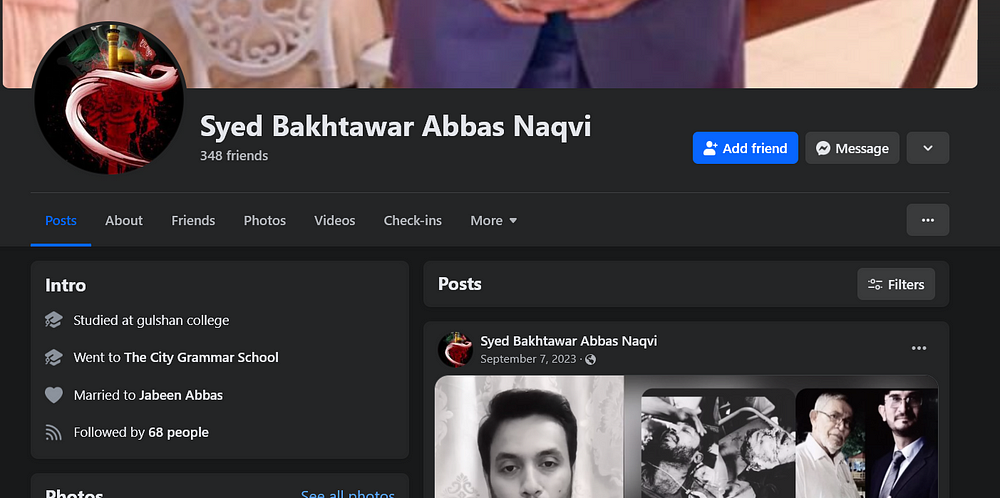
In addition, by examining the cookies found on the computer, Hudson Rock researchers were able to determine that the following Facebook account was actively by Bakhtawar —
The computer holds a total of 238 credentials to various websites, which can help law enforcement gain a better understanding of the group.
Computer B. –
By examining the top logins identified on the computer, Hudson Rock researchers concluded it belongs to a person named “Qamber Jamani” or “Muhammad Qamber”.
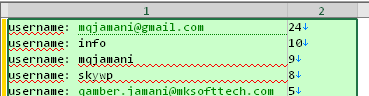
This is supported by the computer’s name — “Jamani”
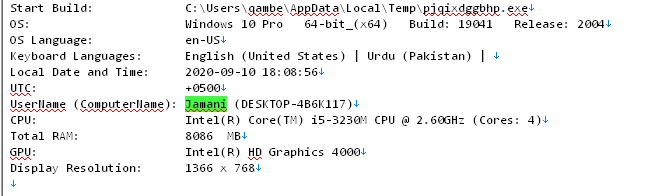
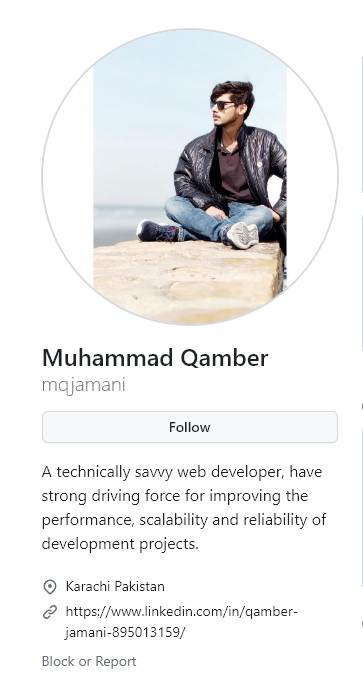
By establishing Qamber is predominantly using the username “mqjamani”, Hudson Rock researchers were able to identify a Github account belonging to a web developer using the same username —
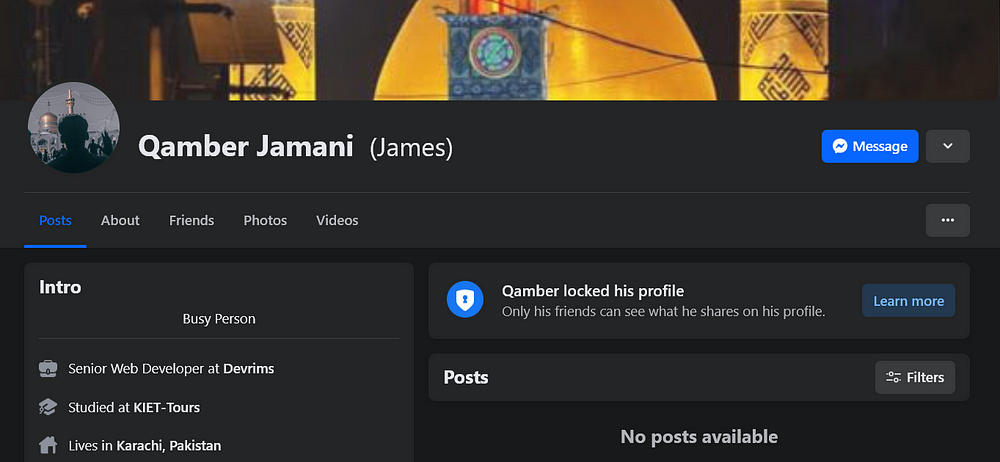
In addition, by examining the cookies found on the infected computer, researchers were able to determine that the following Facebook account was signed into by Qamber —
The computer has a total of 426 credentials to various websites, they can be used by law enforcement to get a better operation about the group.
Key details relating to Mohsin Raza found on the computers:
While the computer doesn’t belong to Mohsin Raza, by going over login credentials, Hudson Rock researchers were able to locate various credentials used by Mohsin to log into different services.
Emails used by Mohsin, provided by OFAC –
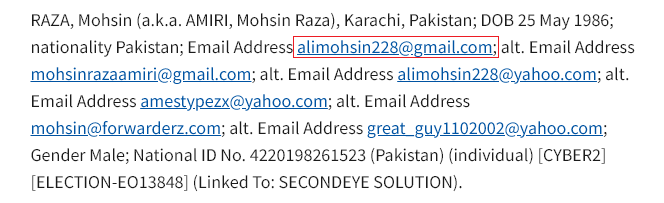
By searching the keyword “alimohsin” on Computer A. we identified the following credentials:
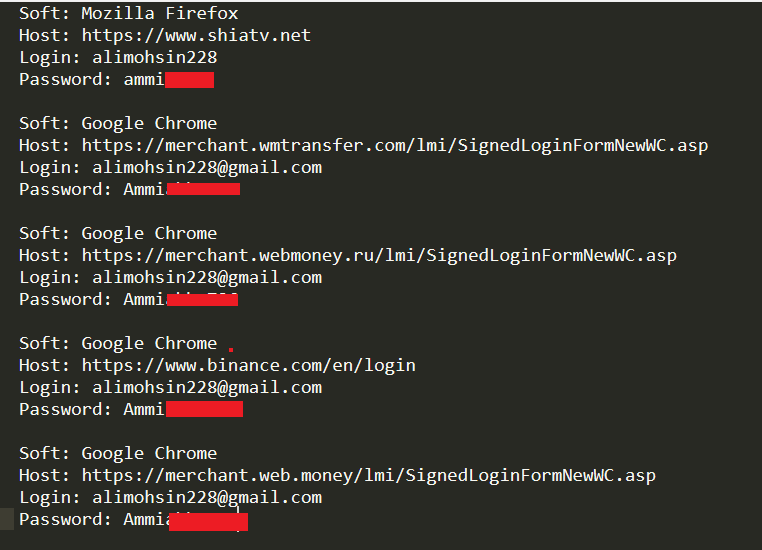
By identifying the password “ammi****” being used by Mohsin Raza, we were able to determine that the username “Likewise” & email “likewise466@gmail.com are likewise associated with Mohsin on Computer A.
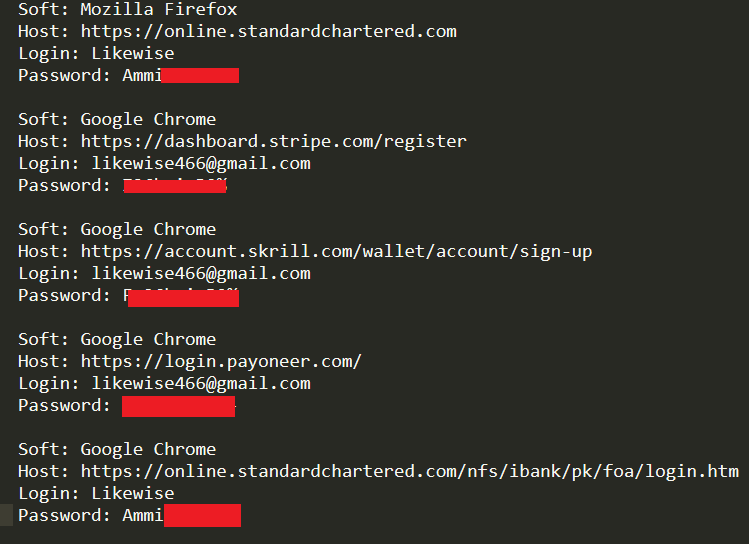
This enabled Hudson Rock researchers to find additional credentials associated with Mohsin Raza on computer B.
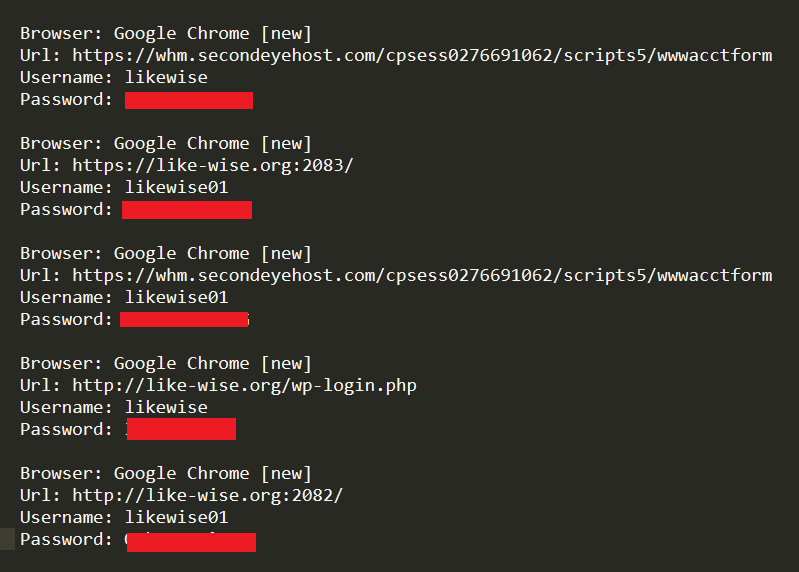
Key details relating to Mujtaba Raza found on the computers:
The following are email addresses belonging to Mujtaba, provided by OFAC:
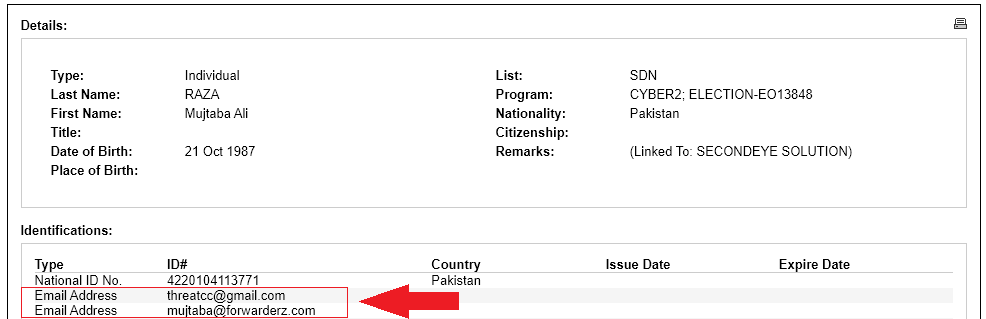
Hudson Rock researchers were able to find several login credentials associated with the email address “threatcc@gmail.com” found on computer A.
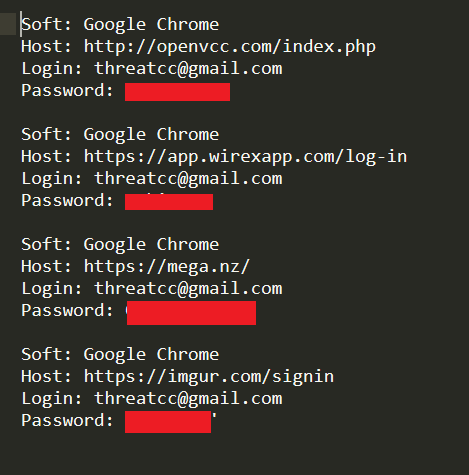
In addition to that, text files with browsing history relating to computer A. shed multiple evidences relating to the sale of illicit goods, such as Bitcoin transactions, screenshots, and more incriminating evidence.
Conclusion
Hudson Rock’s access to Infostealer data from infected computers offers law enforcement a unique advantage in investigations. By analyzing credentials, browsing history, and sensitive information exfiltrated by malware, law enforcement can uncover key operational details of criminal entities.
This data enables authorities to map out networks, identify previously unknown associates, and track illicit activities like fraud and identity theft. By providing actionable intelligence from real-time malware infections, Hudson Rock helps authorities gather concrete evidence to support arrests and prosecutions.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





