Introduction
Recent research from Halcyon has uncovered a novel approach by a threat actor — referred to as Codefinger — who is actively abusing Amazon Web Services (AWS) by leveraging its native features to facilitate ransomware attacks in the wild. This technique underlines a powerful shift in the cyber threat landscape: instead of exploiting infrastructure outside the victim’s cloud environments, attackers are now using legitimate AWS tools to execute ransomware campaigns directly on victims’ own S3 buckets.

Furthermore, a series of recent high-profile breaches — including Telefonica’s and Schneider Electric’s — illustrate how infostealer malware can open the door to devastating social engineering and extortion, underscoring the urgent need for robust credential security.
This blog post will explore how infostealer logs containing AWS credentials could fuel these novel attacks, and highlight how the infostealer ecosystem may be laying the groundwork for this next generation of ransomware campaigns.
Key Takeaways
- New Ransomware Tactics in AWS: Threat actors are now encrypting S3 buckets directly using AWS-native capabilities, showcasing a novel approach to ransomware in the cloud.

2. Infostealers as the “Initial Access” Vector: Infostealer data commonly includes AWS credentials, access tokens, and cookies, providing malicious actors with direct access to cloud infrastructure.
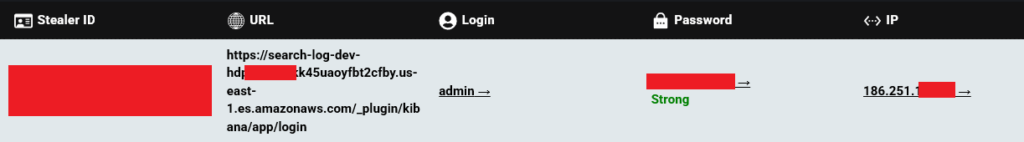
Hudson Rock researchers have identified tens of thousands of corporate credentials to AWS servers of various companies due to Infostealer infections.

3. Recent Breaches as Warning Signs: The breaches of Telefonica and Schneider Electric demonstrate the real-world impact of stolen credentials, with attackers using the foothold to escalate attacks and demand ransoms.

4. Credential Harvesting: A Growing Threat: Rising infostealer infections mean that more AWS credentials are flooding underground markets, setting the stage for large-scale ransomware attempts on cloud environments, similar to the widespread attack seen on Snowflake customers via Infostealer credentials in mid 2024.

The Infostealer Ecosystem: Fueling Ransomware in the Cloud
Infostealers have become a key cog in the cybercrime underworld: once they infect a machine, they collect credential data — including usernames, passwords, session cookies, and sometimes even MFA tokens — and send it back to command-and-control servers or incorporate it into illicit logs sold on dark web marketplaces.
Telefonica and Schneider Electric Breaches
- Telefonica: As reported recently, attackers leveraged stolen credentials from an infostealer infection, enabling them to perform sophisticated social engineering and infiltration.
- Schneider Electric: Similarly, our coverage of Schneider Electric’s breach revealed that Lumma infostealer malware led to unauthorized internal access. Threat actors proceeded to extort the company using stolen data and privileges.
Both incidents highlight how the initial gateway of an infostealer can eventually escalate into full-blown network compromise, brand damage, and extortion schemes — including ransomware. With AWS credentials increasingly appearing in infostealer logs, these same tactics may soon pivot to cloud-based infrastructure.
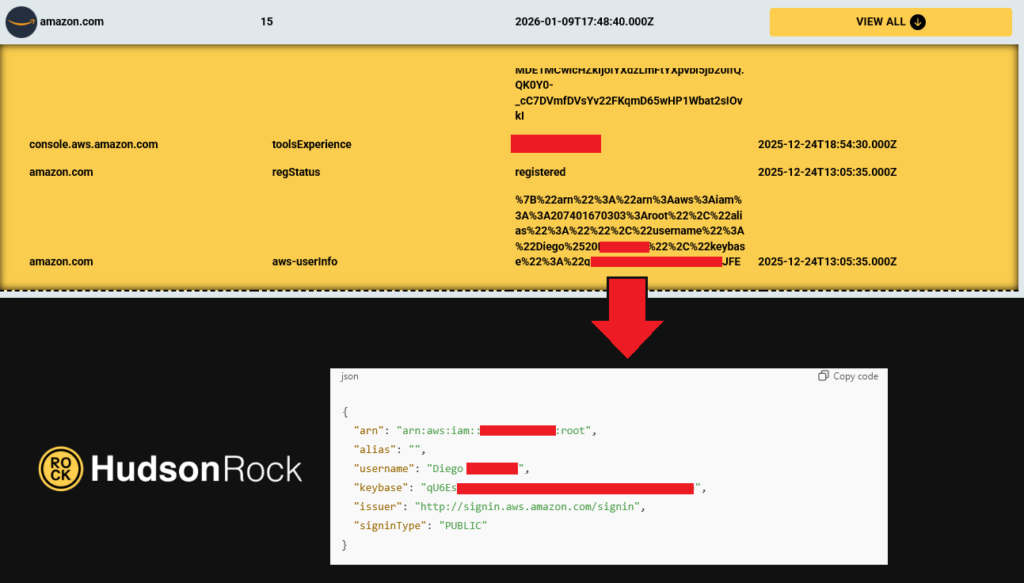
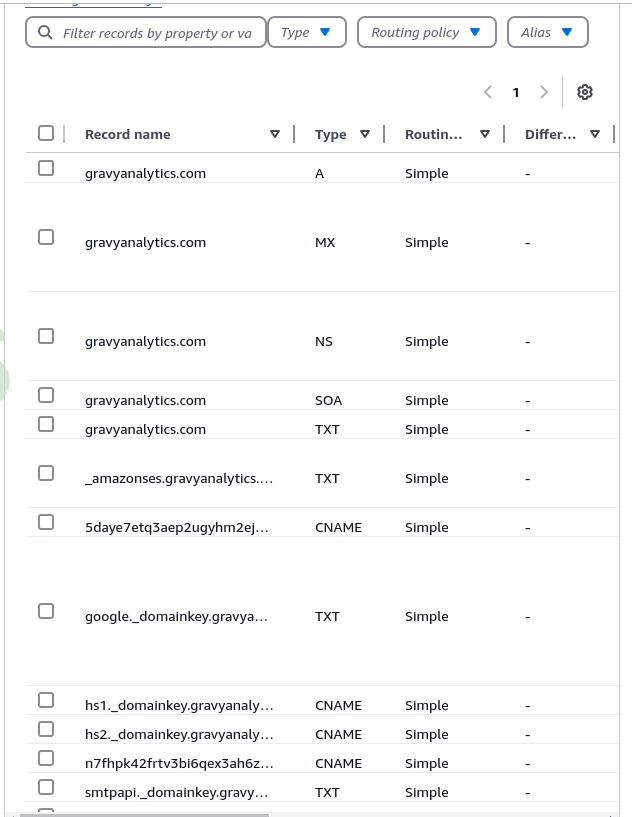
“Fun” Fact- in the recent Gravy Analytics hack, the hacker was able to exfiltrate 10TB of location data through access he was able to obtain to the company’s S3 server
How Infostealer-Derived AWS Credentials Enable Ransomware
A stolen set of AWS credentials can be a goldmine for cybercriminals. Here’s how attackers might leverage them:
- Access & Enumeration
Attackers log in to the compromised AWS account and enumerate existing services. This includes identifying S3 buckets containing critical data. - Exploiting Native AWS Services
Building on Halcyon’s findings, the threat actor can use legitimate features (such as server-side encryption or custom encryption keys) against the victim to encrypt data within S3. This approach can effectively lock the rightful owner out of their own data unless a ransom is paid. - Threat Actor Persistence
The attacker might create new IAM users, roles, or access keys, ensuring persistent re-entry points even if one set of credentials is revoked. - Extortion & Ransom
Once the data is inaccessible to the victim, ransom notes may appear — or the threat actor could exfiltrate data for added leverage, demanding additional payments to prevent further disclosure.
The critical factor here is the initial access to AWS, which will likely often start with infostealer logs. As more infostealer infections occur, attackers have a larger pool of potential cloud environments to target.
Potential Impact on Organizations
- Operational Disruptions: Ransomware attacks on cloud environments can paralyze business operations, potentially leading to multi-day or multi-week outages.
- Financial Costs: Beyond ransom payments, businesses face substantial costs from incident response, legal fees, and regulatory penalties.
- Reputational Damage: Clients, partners, and stakeholders could lose trust in an organization’s ability to protect data, impacting future business opportunities.
Defensive Measures & Best Practices
- Monitor Infostealer Infections
Regularly scan corporate systems for infostealer infections. A small foothold on an employee device can expose a treasure trove of passwords and tokens. - Implement Robust Access Controls
- Use MFA for AWS logins, ideally with hardware-based security keys where possible.
- Follow the Principle of Least Privilege by granting only the minimal level of access necessary.
- Rotate Keys Frequently and regularly review IAM policies.
3. Behavioral Analysis & Continuous Monitoring
- Track Anomalous API Calls: Set up CloudTrail and GuardDuty to watch for suspicious activities, like mass encryption or unrecognized IAM entities.
- Use Real-Time Dashboards: Integrate logs into SIEM/SOAR solutions to detect potential attacks as they happen.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock