Hudson Rock’s continued research explores how Infostealer infections can provide insights into sanctioned entities and identify new opportunities for sanctions.
TL;DR (read the research — don’t be lazy)— Sanctioned companies have infected employees that can provide unrivaled insights to law enforcement, and Hudson Rock researchers were able to discover a company that should be sanctioned based on login data from an infected employee at a sanctioned company.
As of August 2024, Infostealing malware has compromised tens of millions of computers, stealing credentials, cookies, documents, browsing history, and other sensitive data.
While this data is commoditized by threat actors for initial access into companies to perform data breaches and ransomware attacks, it also serves security researchers in protecting organizations, de-anonymizing hackers, and uncovering illegal activities such as pedophilia.
Hudson Rock researchers have previously demonstrated that Infostealer infections don’t spare anyone, including hackers that have their own computers infected.
In this research, we will dive into the world of Infostealer infections at sanctioned entities, and explore an interesting never seen before use-case of gathering insights about sanctioned entities from infection of their employees, and also the discovery of new entities that warrant sanctions but are currently unknown to authorities.
To conduct this research, Hudson Rock researchers compiled a list of domains associated with sanctioned entities from the official “Office of Foreign Assets Control (OFAC)” website:
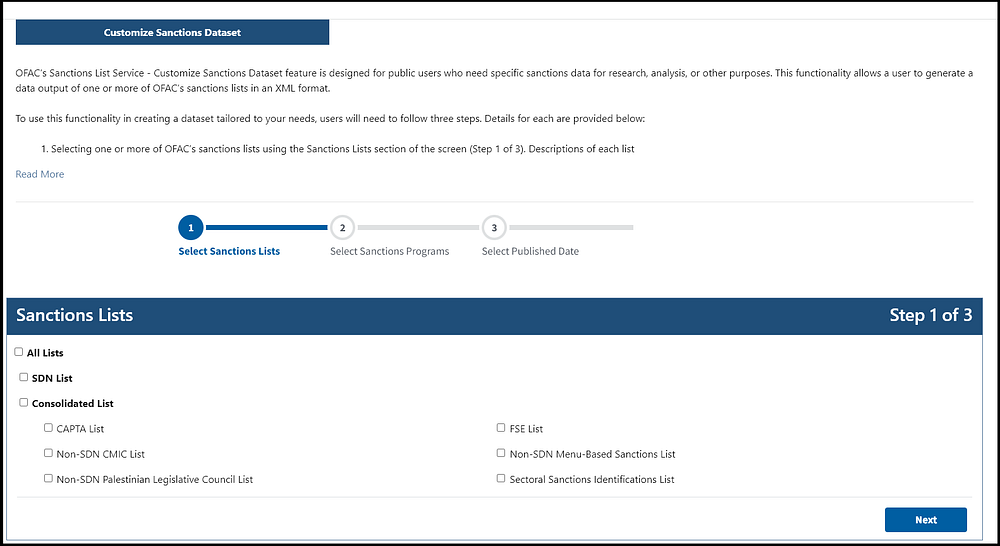
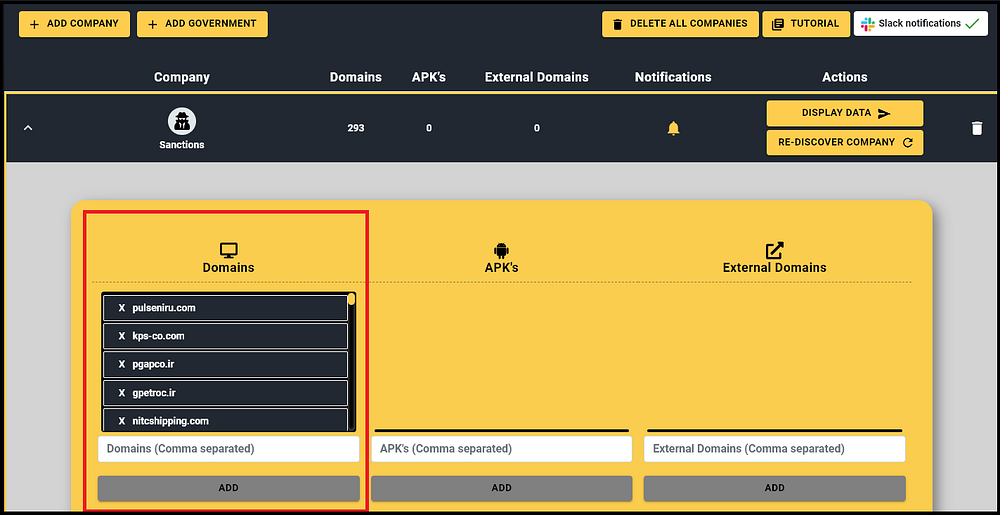
After exporting and cleaning the data, we created a list of approximately 300 websites of sanctioned entities, which was imported into Hudson Rock’s platform, Cavalier.
Cavalier’s “Companies” feature enables comprehensive asset monitoring:
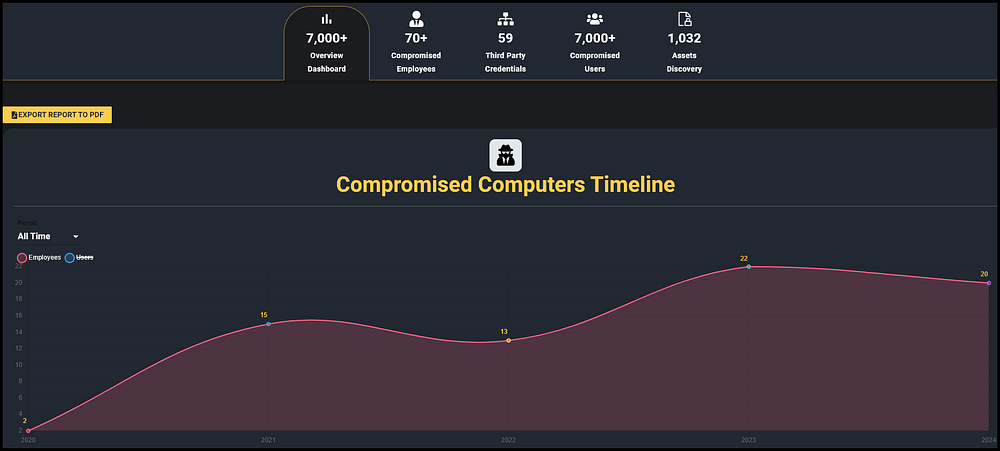
Our analysis revealed that over 70 computers infected by Infostealer malware were linked to employees at sanctioned websites, as determined by the corporate credentials found on these computers, which relate to sanctioned entities.
In addition, 59 of the computers contained corporate credentials of sanctioned entities (e.g corporate email address) to third party services which could implicate these services for servicing sanctioned entities.
The most common corporate credentials were found at the following URLs:
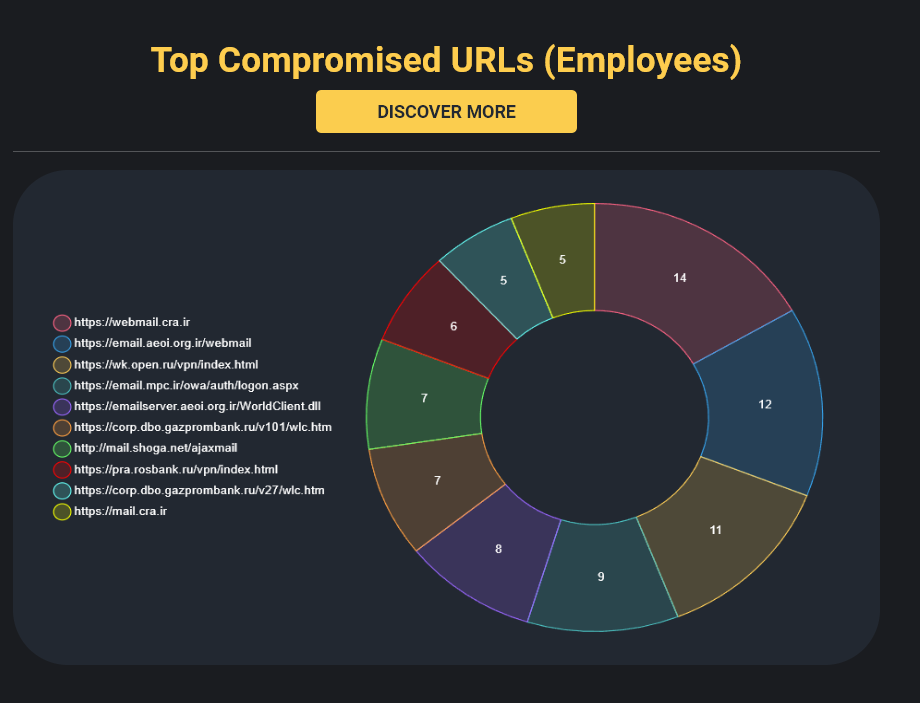
With the top three URLs with most associated credentials are:
- webmail.cra.ir — the mail server of the Communications Regulatory Authority of Iran (CRA), responsible for overseeing telecommunications and internet services in Iran.
- email.aeoi.org — the mail server of the Atomic Energy Organization of Iran (AEOI), main governmental body responsible for Iran’s nuclear energy program.
- wk.open.ru/vpn/index.html — the VPN network of Russia’s Open Joint-Stock Company Bank which was sanctioned as part of broader sanctions against Russian financial institutions in response to Russia’s actions against Ukraine.
When investigating the credentials associated with these entities, Hudson Rock researchers discovered interesting examples such as an infected employee at “KIMIYA PAKHSH SHARGH (KPS)”, an Iranian company involved in the production and distribution of pharmaceuticals and chemicals. It is often associated with the Iranian chemical industry, including substances that may have dual-use applications (i.e., they can be used for both civilian and military purposes).
The company was sanctioned by various international bodies, including the U.S. Department of the Treasury, for its involvement in the proliferation of weapons of mass destruction (WMD) and its support for the Iranian military-industrial complex. The sanctions typically target entities that are believed to be contributing to Iran’s ability to develop or acquire nuclear, chemical, or biological weapons, or to support missile programs.
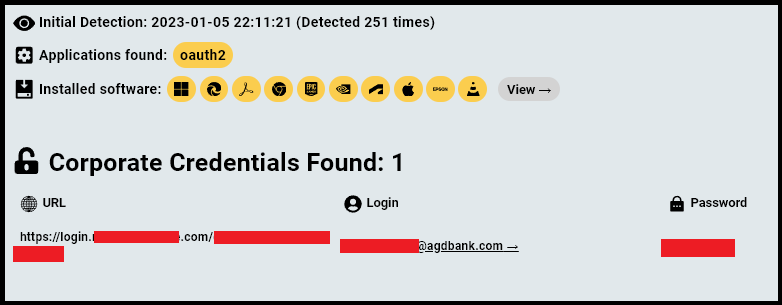
This KPS employee was infected by “Risepro” Infostealer in April 2024, and has sensitive corporate credentials associated with KPS-co.com:
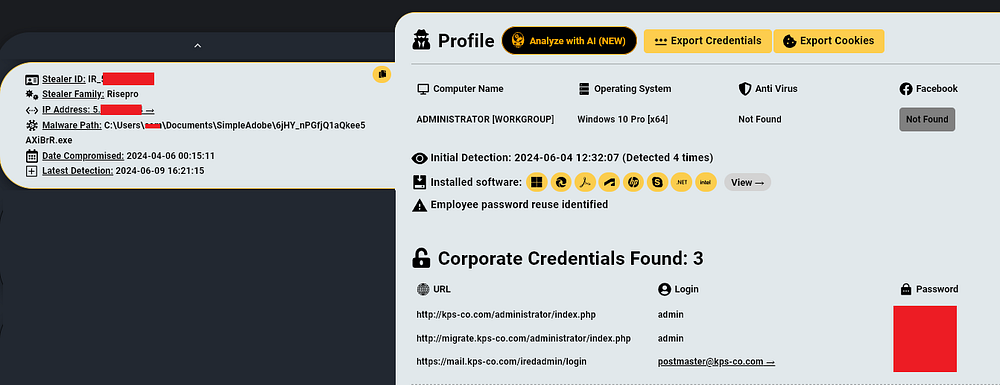
Generally, infostealers retrieve documents, credentials, browsing history, auto-fill data, and other textual data that could provide further insights into the entity’s inner workings.
This kind of data of infected employees at sanctioned entities offer law enforcement unrivaled insights into these entities’ operations.
For example, in this document that was retrieved from the computer of an employee at a highly sensitive sanctioned entity, the entire network architecture of the company is explained in great details —
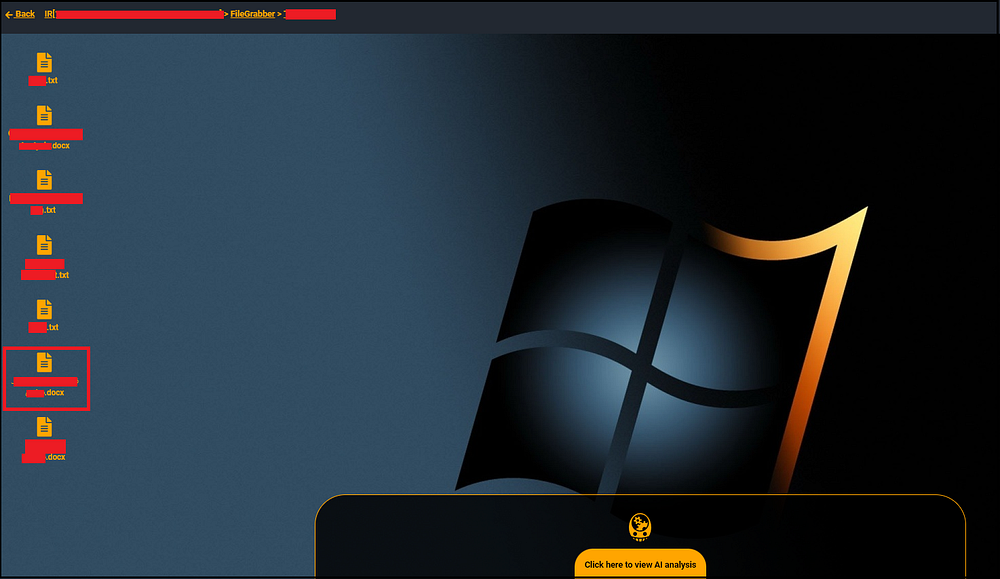
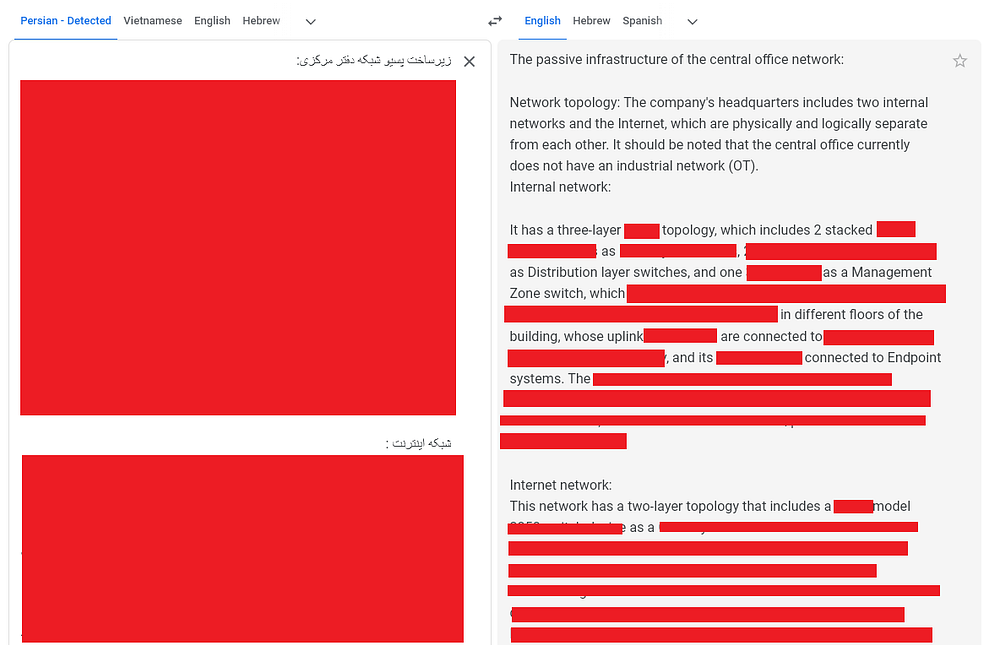
Discovering entities that OFAC overlooked:
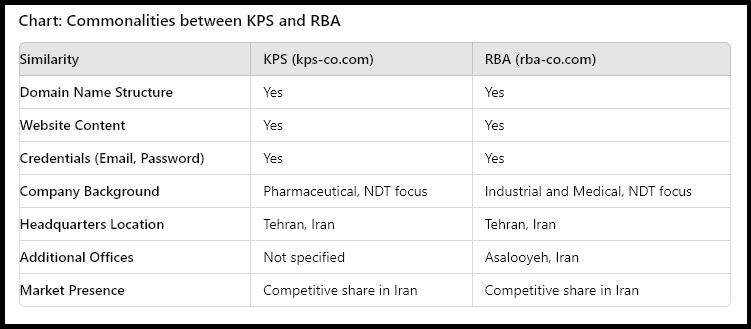
In this fascinating example, by going over the credentials associated with the abovementioned KPS employee, which arrived from an infection of their computer, Hudson Rock’s researchers discovered that the infected KPS employee has corporate credentials to another seemingly related entity that is not listed on OFAC’s website — Radman Barzin Aria (RBA) — rba-co.com
While RBA’s website doesn’t load as of August 2024, archive.org shows us a historical snapshot of the website (*remember the stock photo for later)—

It is specifically mentioned that RBA is a leader in the “NDT” industry (Non-Destructive Testing):

Similarly, an old version of KPS (the sanctioned entity) mentions that they also operate in the healthcare industry & specifically with applications in NDT —

Both domains are strikingly similar in structure (kps-co.com & rba-co.com) and in addition to that, the credentials found for both entities are identical in terms of email structure, password, and login infrastructure:
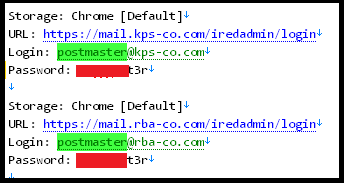
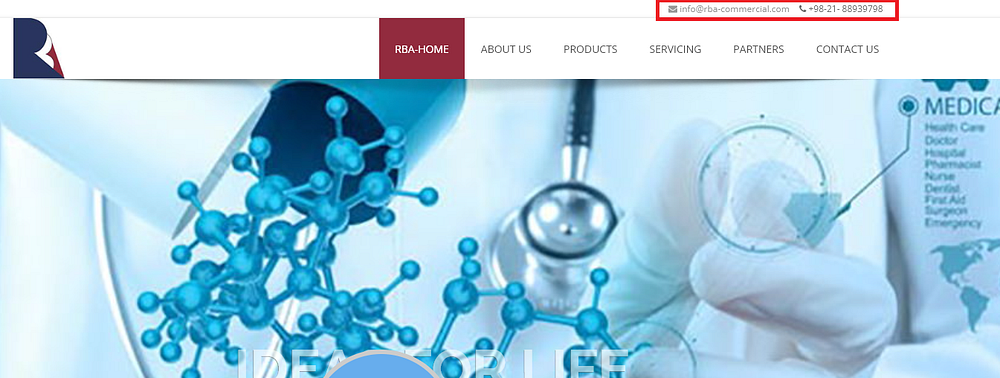
It is worth noting that RBA still operates using the website rba-commercial.com and there are no indications that this entity is sanctioned (*note the same stock image as the one that was used in rba-co.com is also found in rba-commercial.com, indicating that they are the same company) —
This discovery underscores the potential of Infostealer data to uncover entities that should be sanctioned, helping law enforcement enhance investigations into fraudulent companies.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock