By [Alon Gal] | February 2025
Introduction: When National Security Gets Compromised for $10
For years, the U.S. military and its defense contractors have been considered the gold standard of security — equipped with multi-billion-dollar budgets, classified intelligence networks, and the world’s most advanced cybersecurity measures.
Yet, Global Infostealing Malware Data from Hudson Rock reveals an unsettling reality:
- Employees at major defense contractors — including Lockheed Martin, Boeing, and Honeywell — have been infected by Infostealer malware.
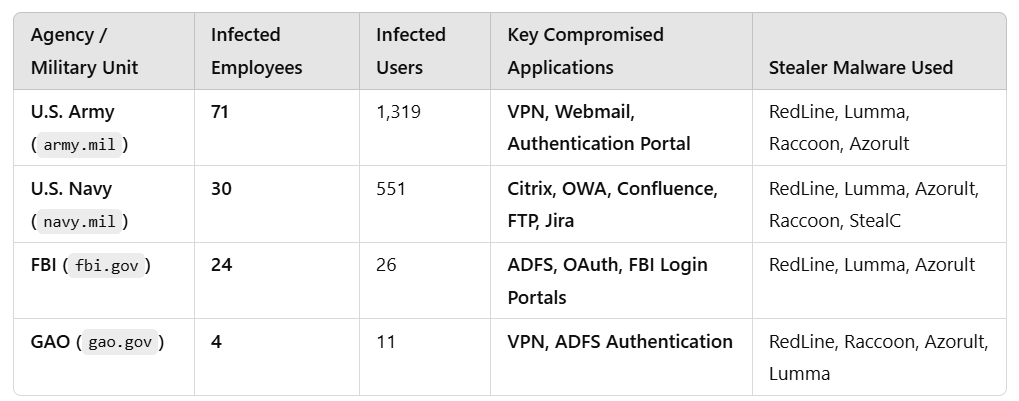
- U.S. Army and Navy personnel had their login details stolen — exposing VPN access, email systems, and classified procurement portals.
- Even the FBI and Government Accountability Office (GAO) have active infections, exposing investigative and cybersecurity personnel.
Each one of these infected employees is a real person — it could be an engineer working on military AI systems, a procurement officer managing classified contracts, a defense analyst with access to mission-critical intelligence.
At some point, these employees downloaded malware on a device they used for work, exposing not just their credentials, but potentially their entire digital footprint: browsing history, autofill data, internal documents, and session cookies for sensitive applications.
And if these organizations — the backbone of U.S. national security — are infected, what does that say about their ability to defend against more sophisticated attacks?

Infostealers: The Malware That Turns Employees Into Insider Threats
In the past few years, Hudson Rock has identified over 30,000,000 computers infected by Infostealers, with 1 in 5 infected individuals having corporate credentials stored on their computers.
For as little as $10 per log (computer), cybercriminals can purchase stolen data from employees working in classified defense and military sectors.
Unlike traditional hacking, Infostealers don’t brute-force their way into networks. Instead, they wait for an employee to slip up — download a game mod, a pirated software crack, or an infected PDF — and then exfiltrate everything:
✅ VPN credentials to military and contractor networks
✅ Multi-factor authentication session cookies
✅ Email logins to government and defense agencies
✅ Internal development tools (GitHub, Jira, Confluence)
✅ Stored documents, browser autofill data, and history
Below is an example of a real cybercrime marketplace where the data of millions of computers infected by Infostealers is sold for just a few bucks.
The marketplace makes it easy for cybercriminals to search for specific credentials found on infected computers, such as army.mil:
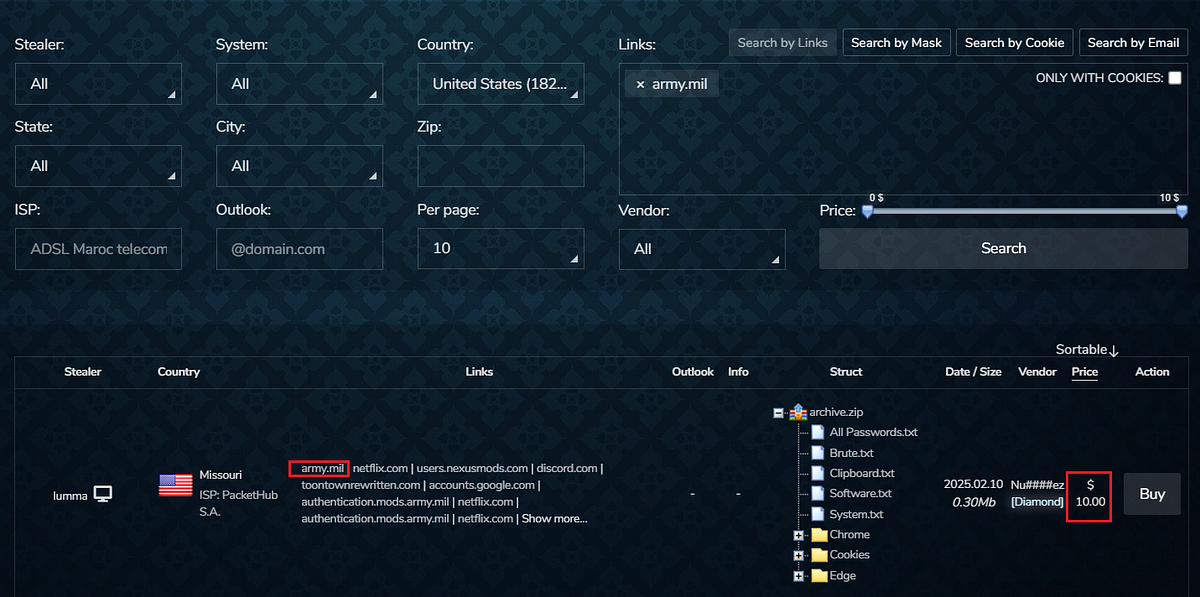
Beside credentials, Infostealer logs often come with a list of active session cookies that allow hackers to hijack live sessions and bypass 2FA/MFA
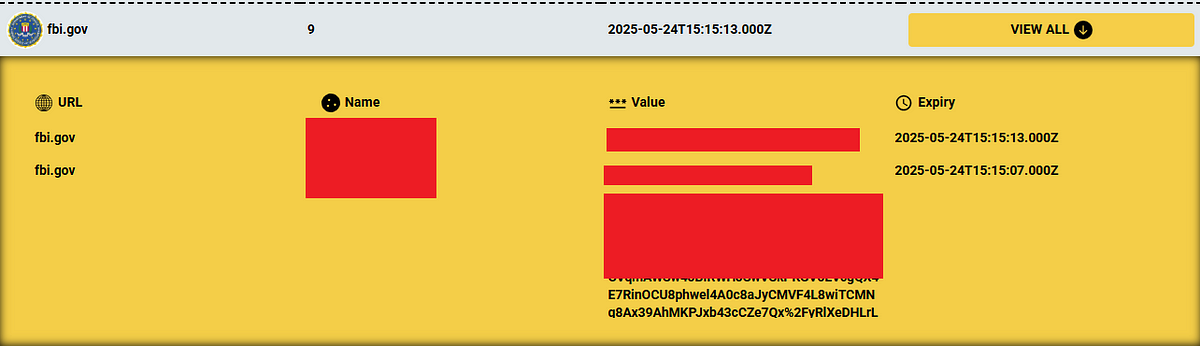
Infostealer Infections Across Major U.S. Defense Contractors
Now, let’s take a look at real-world cases where Infostealers have already infiltrated America’s most sensitive organizations.
These companies engineer the most advanced military technologies on Earth — from F-35 fighter jets to nuclear submarines.
Yet, Hudson Rock data reveals that high-level employees within these organizations have been infected by Infostealer malware — potentially exposing classified projects, internal communications, and sensitive blueprints.
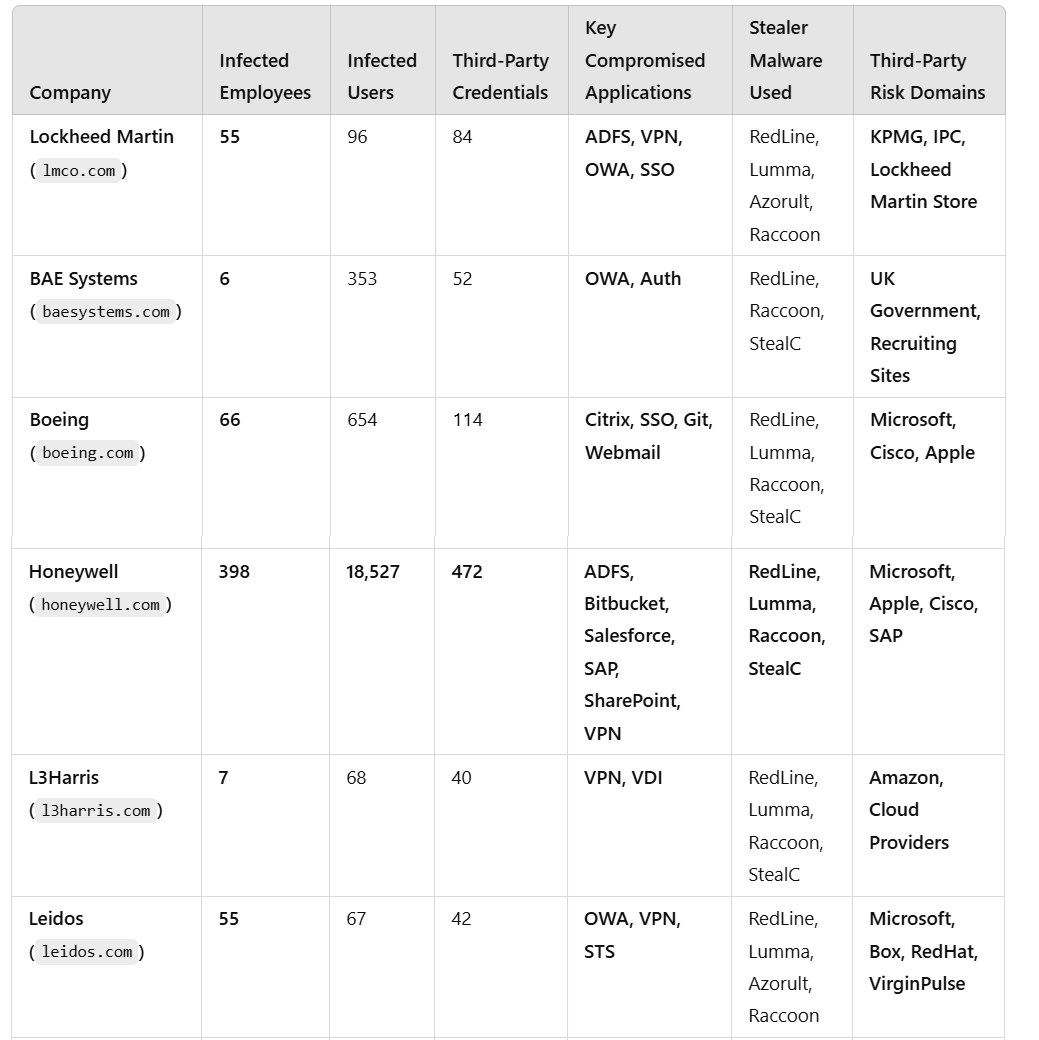
Case Study: The Honeywell Compromise — A Supply Chain Nightmare
- 398 Honeywell employees were infected by Infostealers over the years, leaking access to authentication portals and development tools (Bitbucket, SharePoint, SAP).
- 472 third-party corporate credentials were exposed, including Microsoft, Cisco, and SAP integrations.
- If an adversary wanted to infiltrate a defense contractor’s supply chain, this would be their golden ticket, and for those to people who don’t regularly read our researches, we broke the news and specific attack vectors in many sensitive breaches, all of which started with Infostealer credentials — Airbus, AT&T, Change Healthcare, Schneider Electric, Hot Topic, and more.
Below is a real example of a Honeywell employee who was infected in September 2024. They have been employed at Honeywell as an engineer for 30 years, according to LinkedIn, accumulating tens of corporate credentials in the process:
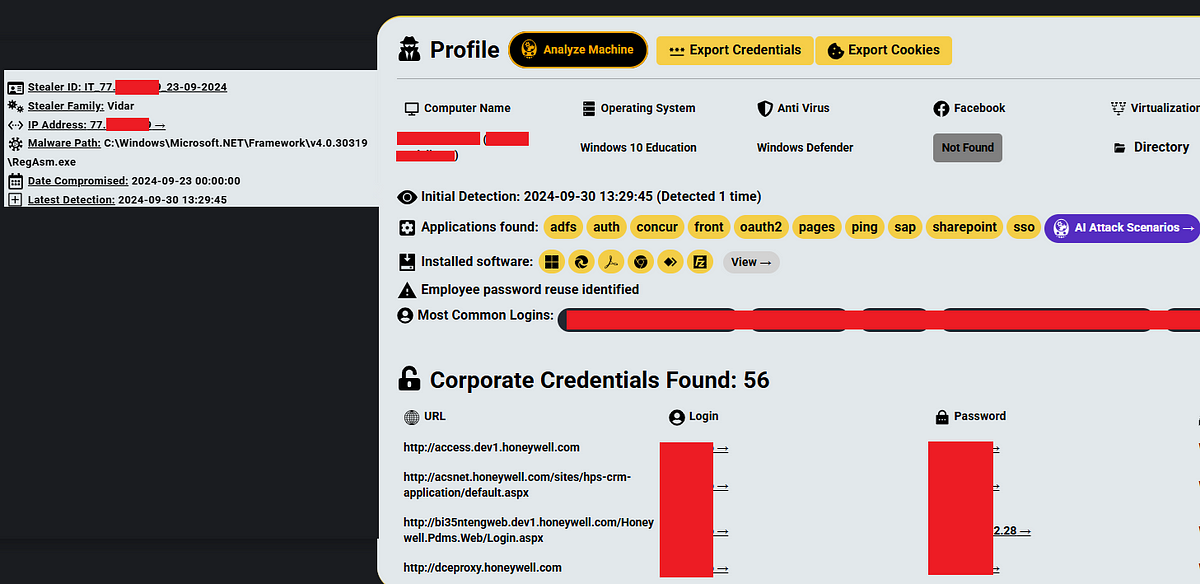
This infected employee, one of hundreds of Honeywell employees affected, has 56 corporate credentials for Honeywell’s infrastructure, along with 45 additional third-party credentials.
Below is a list of some of the URLs for which the infected employee had credentials (the full list is available here):
Credentials to Honeywell’s Infrastructure in the Following Sensitive URLs –
“http://intranet.honeywell.com” – The internal intranet for Honeywell, typically used for internal communications, company resources, and employee services.
“http://access.dev1.honeywell.com” – Likely an internal access or login portal for Honeywell employees, possibly used for testing or development (indicated by “dev1”).
“http://globalapps.honeywell.com” – This might be a global applications portal, providing access to various internal applications across Honeywell’s global operations.
“https://adfs1.honeywell.com/adfs/ls” – Active Directory Federation Services (ADFS) login system. This is crucial for Honeywell’s SSO infrastructure and could provide access to multiple internal services if compromised.
“https://itim.honeywell.com/idm/controller” – Identity and Access Management (IAM) system for managing user roles, permissions, and accounts.
When examining this computer, Hudson Rock’s AI analyzed the download and browser history which came directly from the computer in order to determine which file they downloaded in order to get infected:
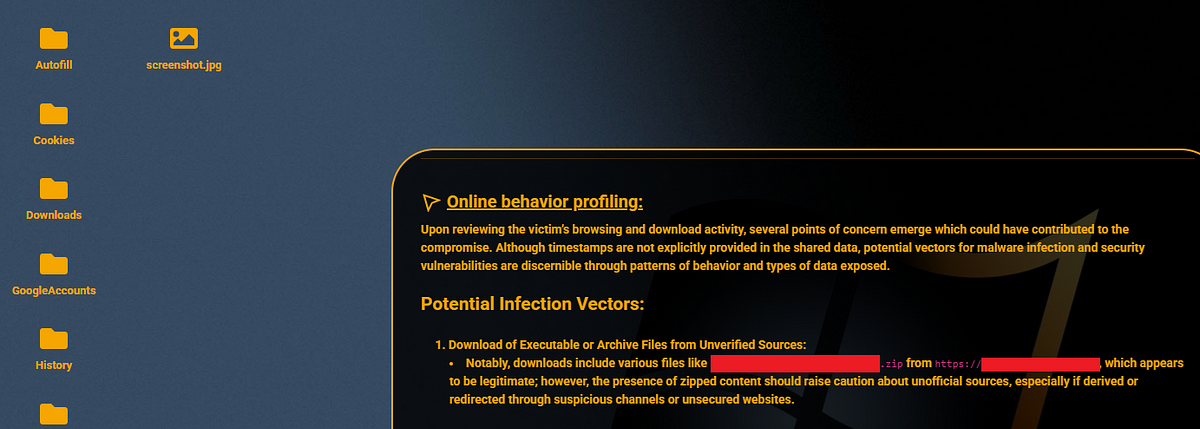
But to make it clear, this isn’t just a Honeywell problem — it’s a systemic issue that affects every company connected to them, including firms like Anduril, SpaceX, and Palantir.
Even companies that have no infected employees can still be compromised — because their partners, suppliers, and vendors are leaking data.
Infostealer Infections Across U.S. Military & Government Agencies
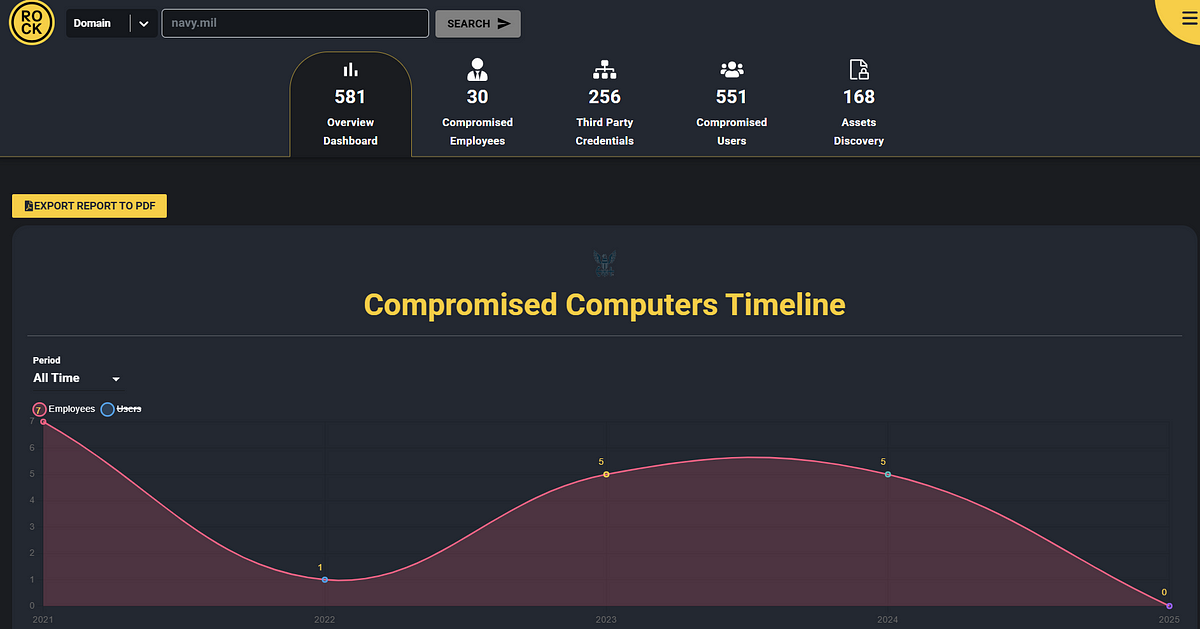
Case Study: The U.S. Navy Compromise — An Open Door to Cyberwarfare
- 30 Navy personnel had their credentials, browsing history, and cookies stolen.
- Leaked authentication data for OWA, Confluence, Citrix, and FTP suggests an adversary could move laterally inside military systems.
- 256 third-party credentials were also leaked, including military training platforms like USALearning.gov and McAfee security integrations.
If a hostile nation-state acquired these credentials, how long would it take them to breach deeper into classified Navy infrastructure?
The Hard Truth: This Is Just the Beginning
The reality is simple:
- If Infostealers can breach Lockheed, Boeing, the U.S. Army, and the FBI, they can breach anyone.
- Leaked credentials = supply chain attacks, insider threats, and national security vulnerabilities.
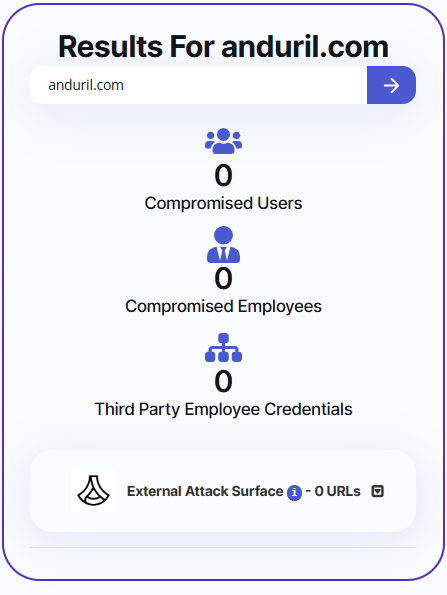
- Even companies that maintain fantastic cyber hygiene and don’t have compromised credentials — like Anduril — are still at risk because their partners and vendors have been compromised.
Solutions for monitoring Infostealer infections after they take place exist, but to prevent infections in the first place, organizations must uphold strong cybersecurity measures:
Conclusion
Infostealer intelligence isn’t just about detecting who’s infected — it’s about understanding the full network of compromised credentials and third-party risks.
If Infostealers can infiltrate the military-industrial complex, what else is already inside?
To learn more about how Hudson Rock protects companies from imminent intrusions caused by Infostealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading — Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





