By [Alon Gal] | March 2025
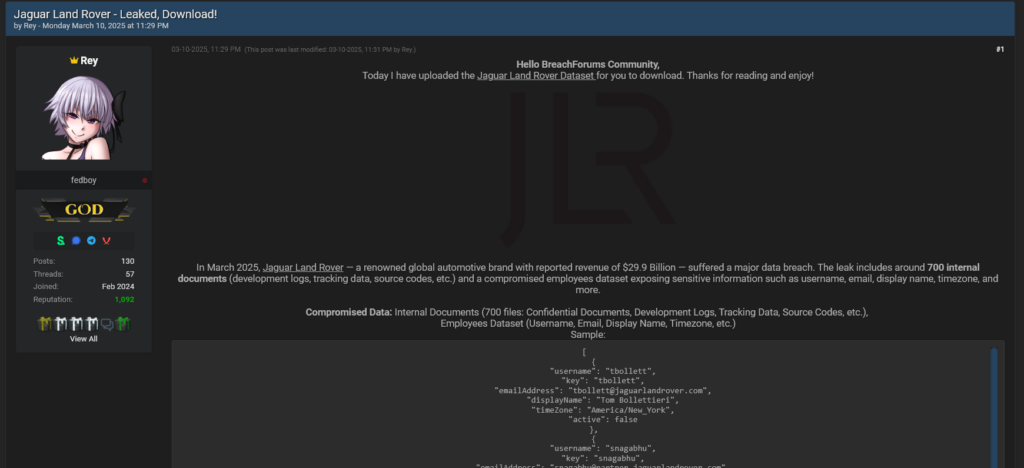
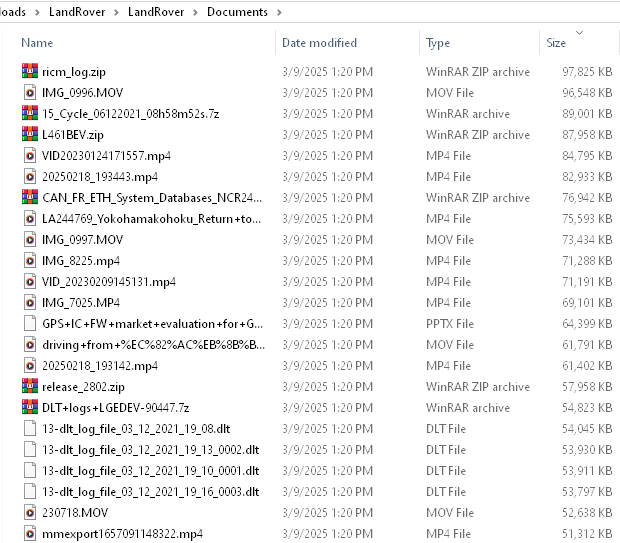
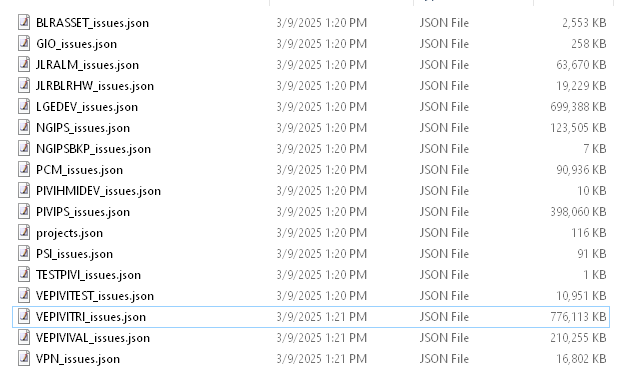
In a repeat of a now-familiar playbook, the HELLCAT ransomware group has claimed responsibility for a massive data breach targeting Jaguar Land Rover (JLR), leaking gigabytes of sensitive information including proprietary documents, source codes, and employee and partner data.
The breach, executed by a threat actor known as “Rey,” mirrors a pattern of attacks Hudson Rock researchers have previously detected against high-profile victims like Telefónica, Schneider Electric, and Orange.
At the heart of this latest incident lies a technique that has become HELLCAT’s signature: exploiting Jira credentials harvested from compromised employees that were infected by Infostealers.
The Breach: It’s a Playbook
What makes this breach particularly alarming is its reliance on a technique that has proven devastatingly effective: the use of infostealer malware to harvest credentials, which are then weaponized to infiltrate critical systems like Atlassian JIRA.
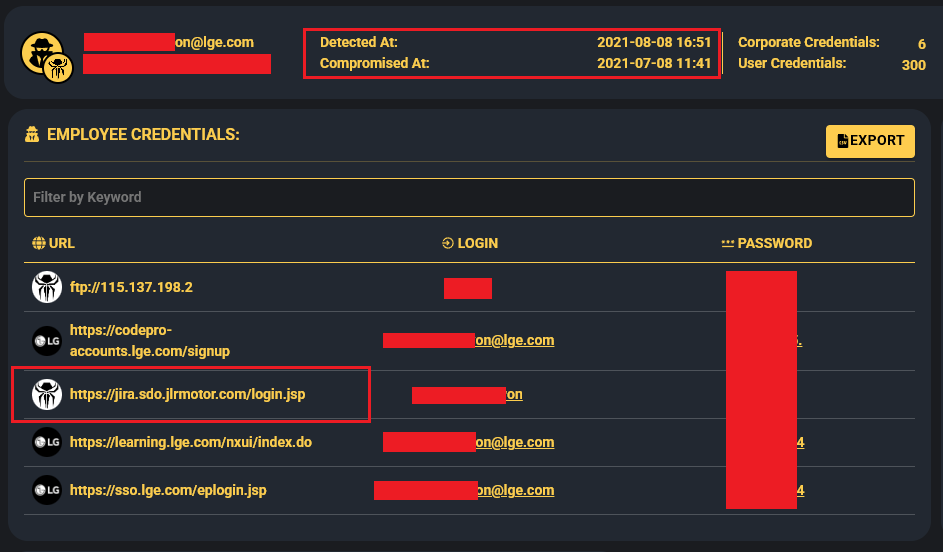
In this case, the compromised credentials belonged to an LG Electronics employee infected by an infostealer who had third party credentials to JLR’s Jira server.
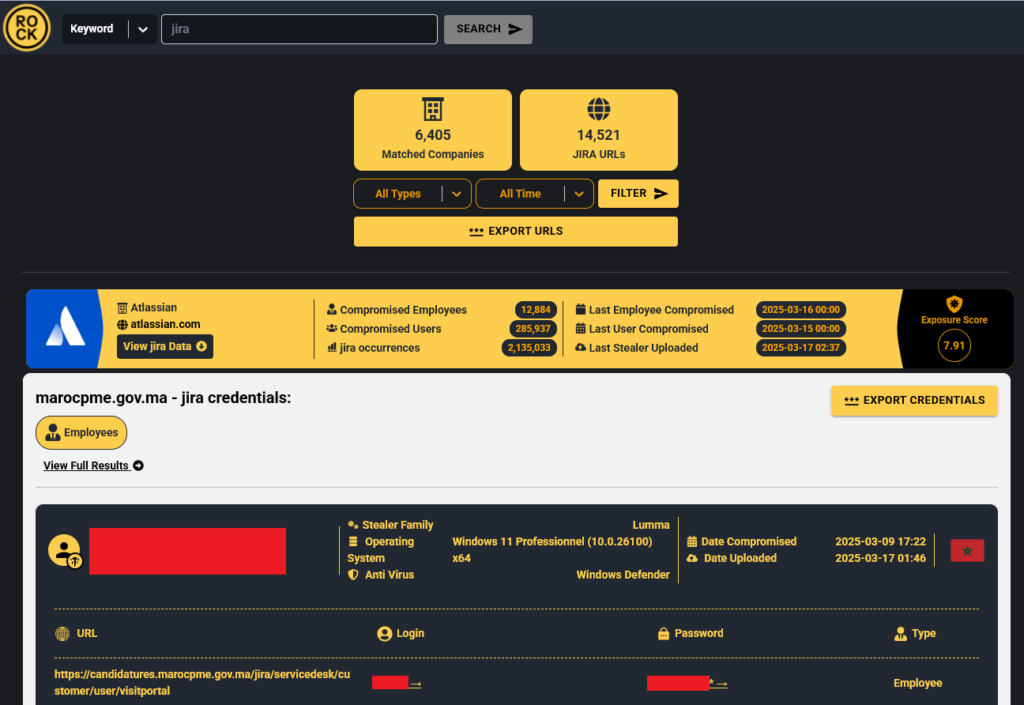
Escalation: A Second Threat Actor Uses the Playbook
Just days after Rey’s initial announcement, the Jaguar Land Rover breach took an even darker turn. A second threat actor, operating under the alias “APTS,” emerged with his own thread on the forum, claiming to have exploited infostealer credentials that date all the way back to 2021, also belonging to an LG Electronic employee, to access JLR’s systems and exfiltrate an even larger amount of data from the company.
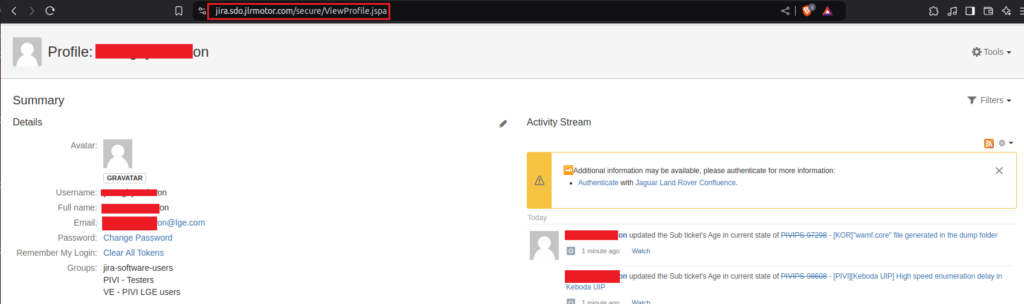
APTS shared a screenshot of a Jira dashboard and displayed additional sensitive data, they also confirmed that the credentials that were used matched the ones we have in Hudson Rock’s database:
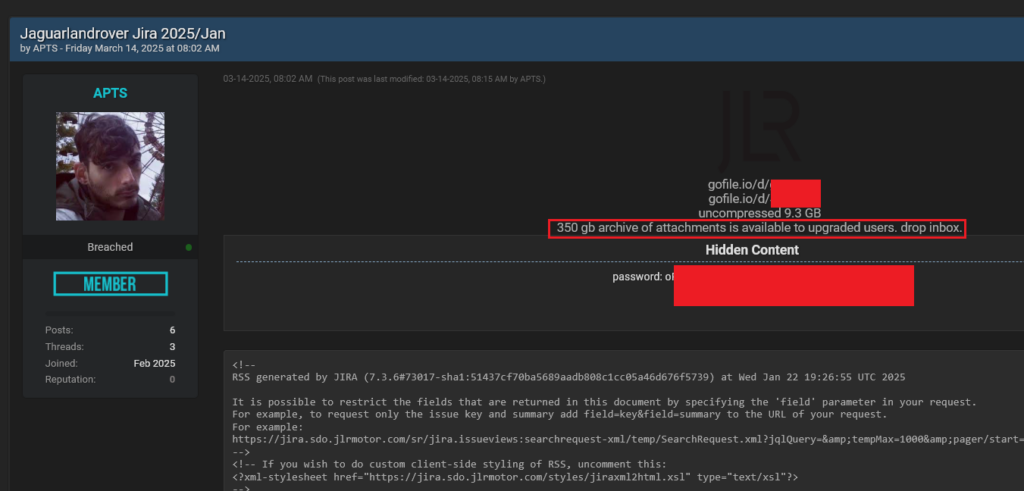
“APTS” leaked a further tranche of data—estimated at an even more worrying scale of 350 gigabytes—containing data that did not exist in Rey’s data dump.

The Attack Method: Infostealers and Jira as the Perfect Storm
HELLCAT’s modus operandi is very efficient. Infostealer malware—such as Lumma, which was implicated in the Schneider Electric breach—silently infects employees’ devices, often through phishing emails, malicious downloads, or compromised websites. Once embedded, the malware exfiltrates sensitive data, including login credentials for corporate systems. These stolen credentials are then sold or hoarded on the dark web, waiting for threat actors like Rey and “APTS” to exploit them.
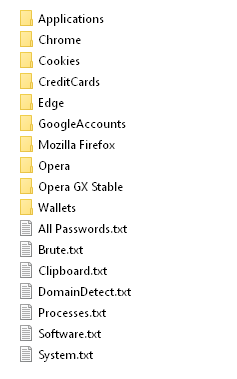
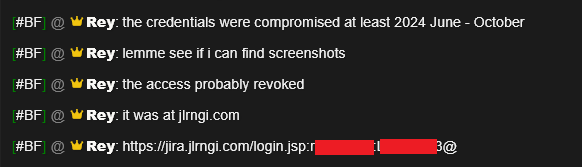
In the Jaguar Land Rover breach, following the thread posted by “APTS” and a short confrontation between the threat actors, Rey himself confirmed publicly that the entry point was an Atlassian Jira instance while referencing Hudson Rock’s research on his Telefonica hack –
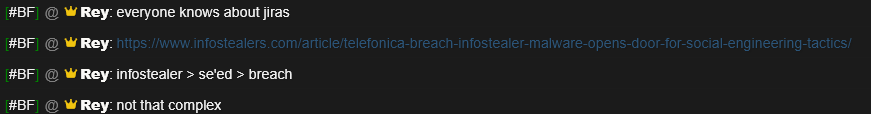
A Credential Time Bomb
What sets the JLR breach apart is the age of the compromised credentials. Hudson Rock, which has tracked infostealer infections since at least 2018, had previously identified the employee’s stolen login details as part of its vast database of exposed credentials. Despite their age, the credentials remained valid and unchanged within JLR’s systems—a lapse that hackers exploited years later. This delay between infection and exploitation is a reminder of the long tail of infostealer campaigns, where stolen data can linger as a latent threat until the right buyer comes along.
The Broader Implications
The Jaguar Land Rover breach is the latest in a string of high-profile attacks that expose the devastating potential of infostealer malware. Telefónica’s breach demonstrated how such infections could enable social engineering, while Schneider Electric’s ordeal revealed the blackmail potential of stolen data. Orange’s case illustrated how AI could amplify these leaks into hacker paydays. Now, JLR’s breach adds a new layer: the enduring danger of legacy credentials left unaddressed.
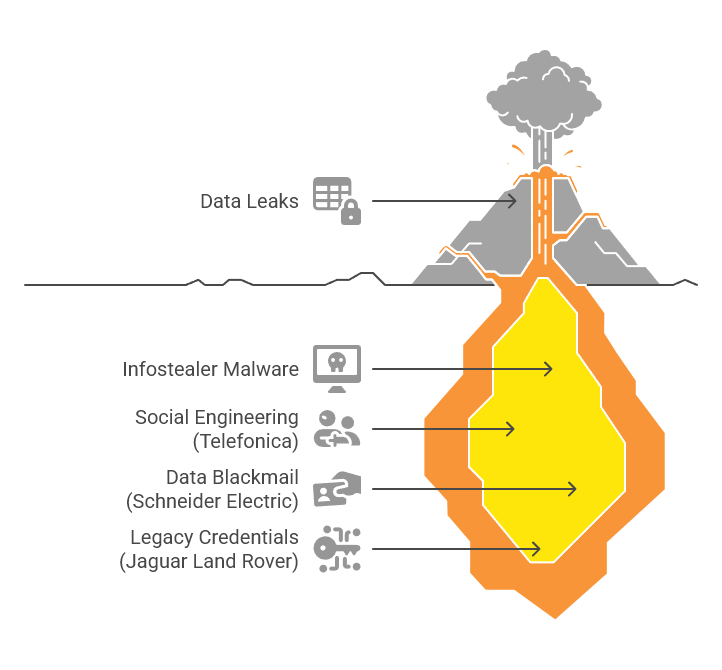
For organizations, the lesson is clear—infostealer infections are not one-off incidents but ticking time bombs. The credentials they harvest can remain viable for years, especially if companies fail to implement robust monitoring, multi-factor authentication (MFA), or timely credential rotation.
Atlassian Jira, while a powerful tool, has become a prime target for attackers due to its centrality in enterprise workflows and the wealth of data it houses. Once inside, threat actors like HELLCAT can move laterally, escalate privileges, and extract sensitive information with alarming ease.
What’s Next?
As Jaguar Land Rover scrambles to assess the damage and secure its systems, the cybersecurity community braces for the fallout. The leaked data—source code, employee details, and partner information—could fuel further attacks, from targeted phishing campaigns to intellectual property theft. This is especially true as threat actors begin utilizing AI to take advantage of large unorganized data breaches to create a bigger impact.
Meanwhile, HELLCAT’s success is likely to inspire copycat operations, with infostealer credentials remaining a hot commodity on the dark web.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





