
The Lumma information-stealing malware is now using an interesting tactic to evade detection by security software – the measuring of mouse movements using trigonometry to determine if the malware is running on a real machine or an antivirus sandbox.
Lumma (or LummaC2) is a malware-as-a-service information stealer rented to cybercriminals for a subscription between $250 and $1,000. The malware allows the attacks to steal data from web browsers and applications running on Windows 7-11, including passwords, cookies, credit cards, and information from cryptocurrency wallets.
The malware family became available for purchase on cybercrime forums for the first time in December 2022, and a few months later, KELA reported that it had already started to become popular in the underground hacking community.
Malware devs turn to trigonometry
A new Outpost24 report looking at the new Lumma Stealer version 4.0 found several significant updates on how the malware evades detection and thwarts automated analysis of its samples.
These evasion techniques include control flow flattening obfuscation, human-mouse activity detection, XOR encrypted strings, support for dynamic configuration files, and enforcement of crypto use on all builds.
The most interesting of the above mechanisms is the use of trigonometry to detect human behavior, indicating that the infected system isn’t being simulated in a virtual environment.
The malware tracks the mouse cursor’s position on the host using the ‘GetCursor()’ function and records a series of five distinct positions in 50-millisecond intervals.
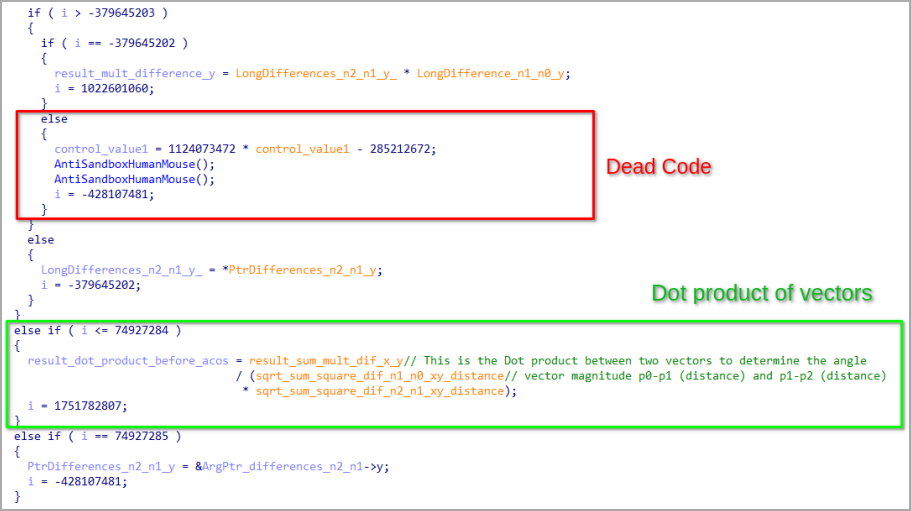
It then applies trigonometry to analyze these positions as Euclidean vectors, calculating the angles and vector magnitudes that form from the detected movement.
If the calculated vector angles are below 45 degrees, Lumma assumes that the malware movements aren’t emulated by software, allowing the execution to continue.
If the angles are 45 degrees and higher, the malware halts all malicious behavior but continues to monitor mouse movement until human-like behavior is detected.
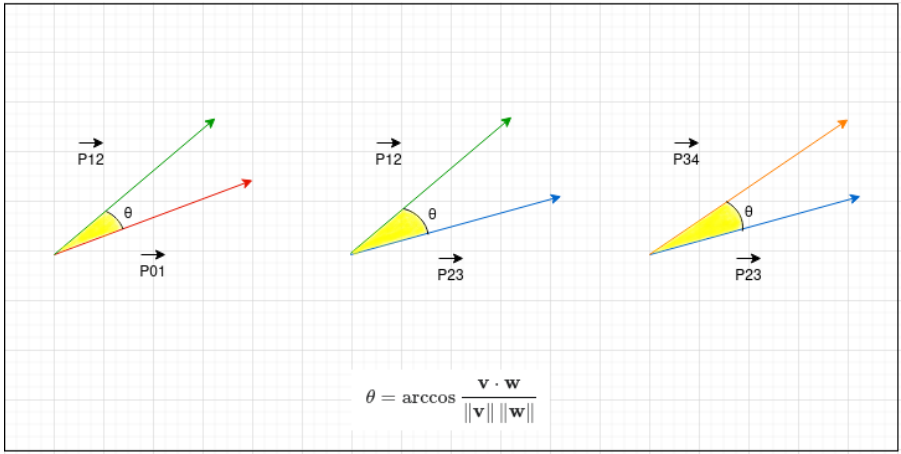
The choice of a 45-degree threshold in Lumma’s anti-sandbox mechanism is an arbitrary value set by the malware’s developer and is likely based on empirical data or research on the operation of automated analysis tools.
Another interesting development concerning the Lumma operation is the requirement to use a crypter to protect the malware executable from leaking to non-paying hackers and threat analysts.
Lumma now automatically checks for a specific value at a certain offset in the executable file to determine if it is crypted and serves a warning if it isn’t.
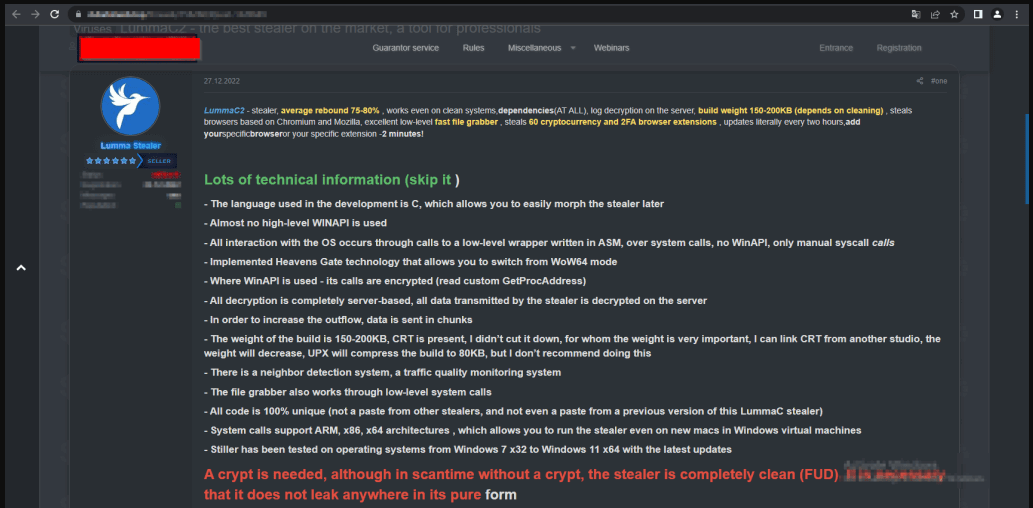
As a last line of defense against scrutiny, Lumma 4.0 incorporates obstacles within its code, like opaque predicates that unnecessarily complicate the program’s logic, and blocks of dead code injected within functional code segments to create confusion and analysis errors.
The latest version of the Lumma stealer demonstrates a heightened emphasis on evading analysis, introducing multiple layers of protective measures designed to thwart and complicate any attempts at dissecting and understanding its mechanisms.




