Cryptocurrency on-chain sleuth, ZachXBT, alerted the cryptocurrency community today that several notable organizations such as CoinTelegraph and WalletConnect are being used to send phishing messages through their mailing lists.

It appears that the emails sent to victims are an attempt to convey them into signing a transaction that will drain their crypto wallets

So far over $500,000 were drained from victims and a money laundering attempt is undergoing.

“Scam Sniffer” detected that all of the impacted companies are using a mailing service named MailerLite and indicates that this is the reason for the hack
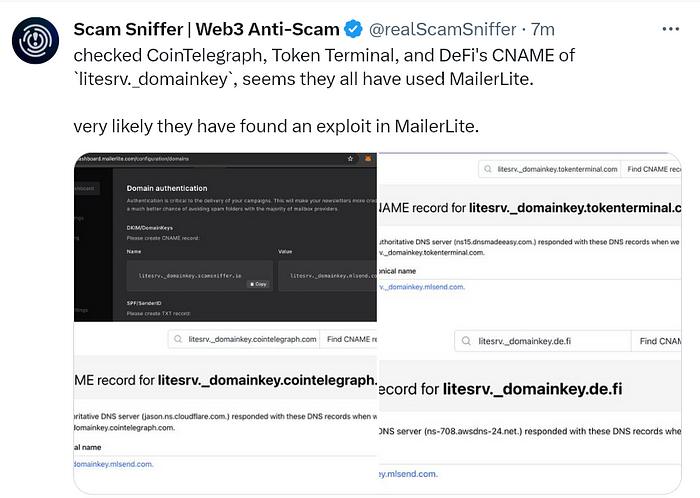
This was confirmed by one of the impacted companies as well.

While it is uncertain whether MailerLite suffered an exploit or not, Hudson Rock researchers identified a recently infected computer of a MailerLite employee with accesses to sensitive URLs within MailerLite & its third parties.

The computer was infected by CRYPTBOT Infostealer in August of 2023 and has sensitive credentials to Mailerlite such as https://admin.mailerlite.com/admin which could have been used by the threat actor to gain an initial access to the company’s servers.
In addition, the employee has valid cookies to sensitive services which were stolen by the infostealers and are often used by hackers to perform sessions hijacks.
Cookies for slack.com:

Cookies for microsoftonline.com (office365):

An image from the infected employee’s computer reveals that they were compromised when trying to execute an infected software.
The image also shows that they were using Slack at the time:

This attack again illustrates how a single infostealer infection could be detrimental to any company.
It is important to routinely check your organizational exposure to Infostealer infections which are the top initial attack vector for threat actors to access corporate and customer accounts.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





