By [Alon Gal] | March 2025
At Infostealers.com, we’ve been sounding the alarm on the infostealer epidemic for years, uncovering how these malware families—like Vidar, Lumma, RedLine, and Raccoon—silently harvest credentials and pave the way for devastating breaches. Backed by Hudson Rock’s threat intelligence, we’ve tracked countless corporate compromises stemming from infected devices.
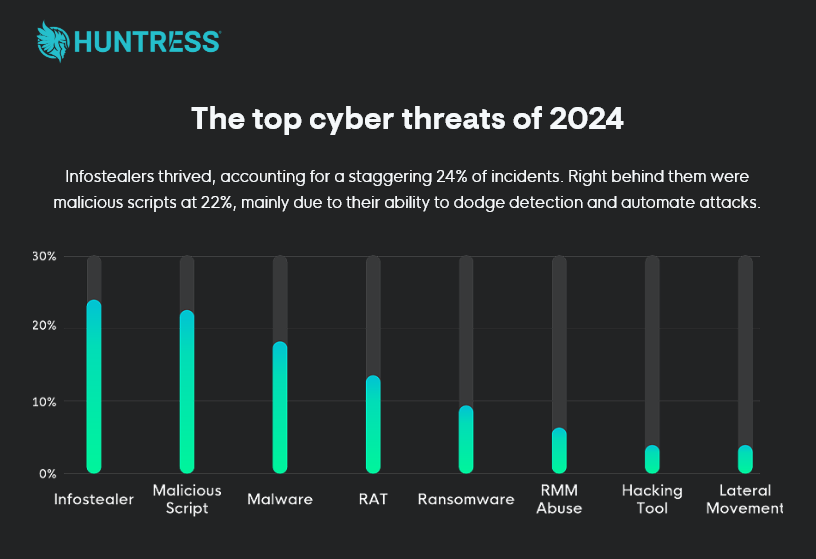
Now, the “2025 Cyber Threat Report” from Huntress, a cybersecurity powerhouse protecting over 3 million endpoints worldwide, confirms what we’ve long suspected: Infostealers aren’t just a passing trend—they’re a cornerstone of modern cyber threats, driving nearly a quarter (24%) of all cyber incidents in 2024.
Huntress’s Frontline View of the Infostealer Plague
Huntress, founded by ex-NSA cyber operators such as Kyle Hanslovan, isn’t your average security vendor. With a mission to empower under-resourced IT teams, they monitor millions of endpoints across industries like healthcare, education, and technology. This massive visibility makes them uniquely positioned to see the infostealer epidemic unfold in real time. Their 24/7 team of analysts and researchers doesn’t just detect threats; they dissect them, offering a granular look at how attackers operate.
In their latest report, Huntress reveals that infostealers topped the charts in 2024, accounting for 24% of observed incidents—outpacing malicious scripts (22%) and traditional malware (17%). That’s one in four cyberattacks tracing back to Infostealing malware.
Why does this matter? Because Huntress’s data isn’t from some ivory tower—it’s from the trenches, where small and medium-sized businesses (SMBs) battle the same sophisticated threats as big enterprises. Their findings echo what we’ve seen at Hudson Rock: Infostealers are the gateway drug of cybercrime, quietly collecting login credentials, financial data, and sensitive info before handing it off to ransomware gangs, extortionists, or initial access brokers.
Infostealers Across Industries: A Universal Threat
The Huntress report breaks down how infostealers hit different sectors, and the numbers are consistent. In healthcare, they made up 19% of threats, often tied to Gootloader and PowerShell-driven reconnaissance.
Education saw 16% of incidents linked to infostealers like Chromeloader, which dominated 70% of detections in that sector. Government entities faced a 21% infostealer hit rate, with families like SOCGholish and AsyncRAT leading the charge.
Technology companies weren’t spared either—14% of incidents involved infostealers like Meduza and Strela, targeting credential managers and RMM tools. Even manufacturing, with its legacy systems, clocked in at 15%, often seeing infostealers masquerading as Adobe components.
And then there’s the military and defense sector, where the stakes couldn’t be higher. Our own research at Infostealers.com, uncovered a cybersecurity disaster in the making: employees at U.S. defense giants like Lockheed Martin (55 infected), Boeing (66 infected), and Honeywell (398 infected) have fallen victim to infostealers.
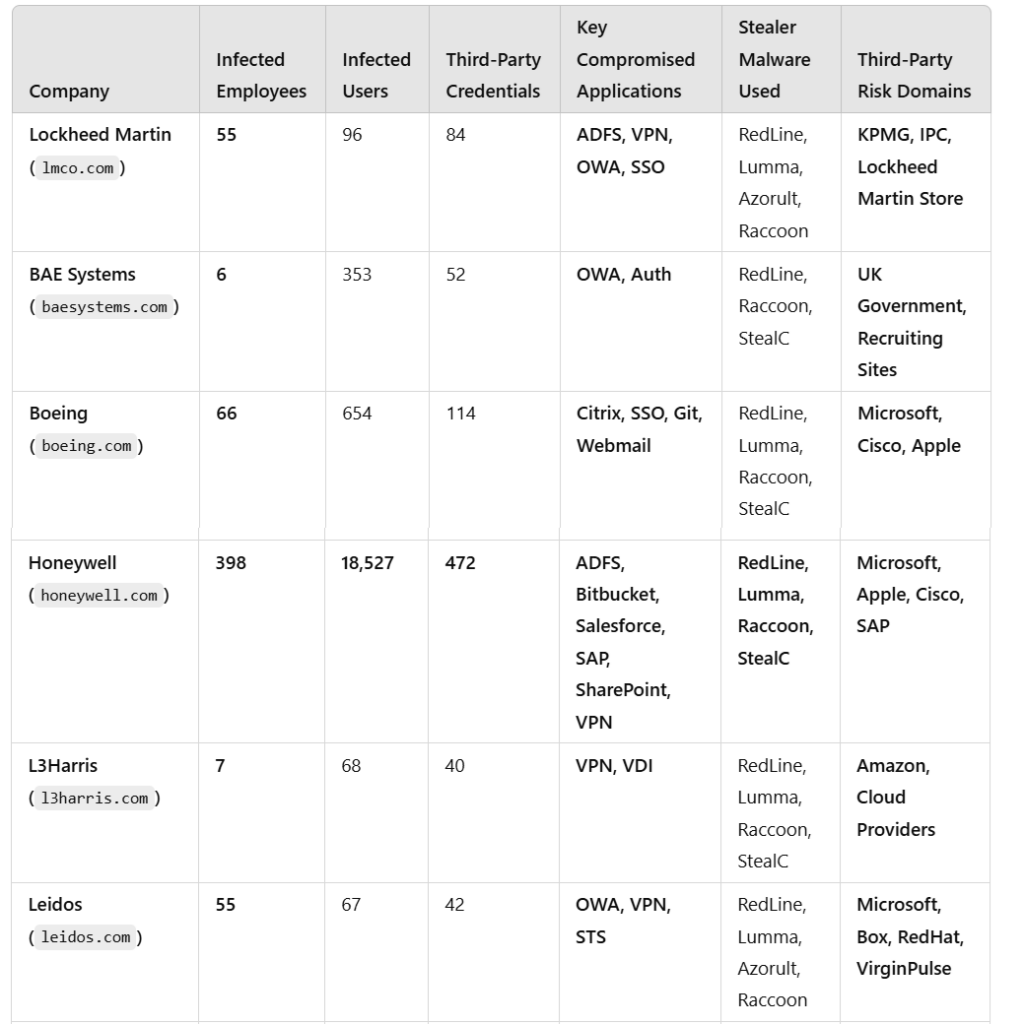
These aren’t random laptops—these are machines tied to classified projects. Honeywell alone saw 472 third-party credentials exposed, including Microsoft and SAP logins, offering adversaries a golden ticket to infiltrate supply chains. Huntress’s 21% infostealer rate in government aligns with this, showing how these threats don’t discriminate—they hit critical infrastructure just as hard, turning a single infection into a national security nightmare.
The Breach Connection: Infostealers.com’s Real-World Evidence
At Infostealers.com, we’ve cataloged breaches that trace back to Infostealer infections. Take the 2024 breach of a major healthcare provider we reported: an employee’s device, infected with an Infostealer, leaked credentials that let attackers access the healthcare’s network, ultimately triggering a ransomware hit.
Or the recent breaches of Telefonica and Schneider Electric, where JIRA creds from a developer’s machine were obtained by HELLCAT Ransomware group following Infostealer infections, leading to massive leaks from the servers of the companies.
These aren’t hypotheticals—they’re real incidents, validated by our intelligence and now corroborated by Huntress’s data.
Why Infostealers Are Winning—and What’s Next
So why are infostealers behind 24% of incidents? Huntress points to their adaptability. Malware like Jupyter evolves from infostealers to multi-stage backdoors, adding features as the market demands. Scripting abuse—PowerShell, VBScript, JavaScript—keeps them under the radar, while their low cost and high ROI make them a favorite among attackers. The report warns that this isn’t slowing down; as endpoint detection improves, attackers will lean harder on data theft, a tactic infostealers excel at.
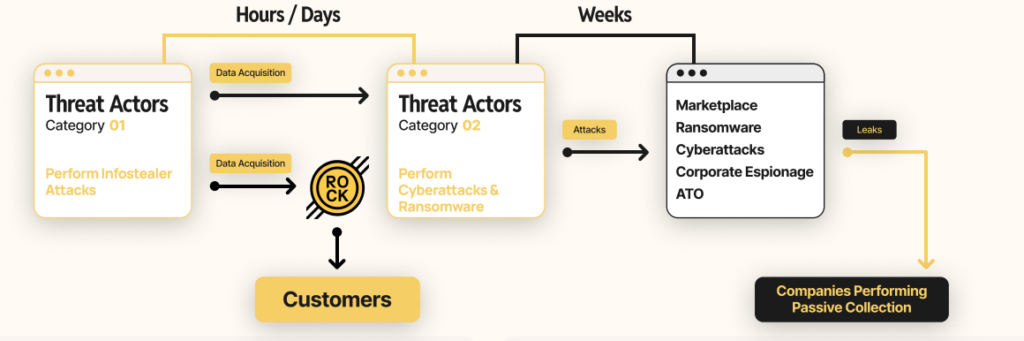
The report adds that the window from initial infostealer compromise to data theft or ransomware is shrinking fast.
Huntress’s data shows groups like Akira deploying ransomware in as little as six hours after access, with an average time-to-ransom of 17 hours across incidents. At Infostealers.com, we’ve seen this too—credentials hit dark web markets within days, sometimes hours, of infection. Companies often think they can just passively collect infostealer logs, sit back, and assume they’ll dodge a breach. That’s a fantasy. Attackers move quicker than ever leaving no time for complacency.
For us at Infostealers.com, this is personal. We’ve seen the fallout—businesses blindsided by breaches they never saw coming, all because an employee clicked the wrong link. Huntress’s 3 million endpoints give them a bird’s-eye view, but our ground-level intel from Hudson Rock shows the human cost. Together, the message is clear: Infostealers aren’t just a statistic—they’re an epidemic, and one in four incidents proves it.
The Takeaway: Act Now or Pay Later
Huntress’s advice—layered defenses, proactive monitoring, and patching, matches what we preach at Hudson Rock: know your exposure, lock down credentials, and train your people. Their 2025 outlook predicts more extortion, more LOLBin abuse, and more cloud attacks—all fueled by infostealers.
Check your status using Hudson Rocks free tools today – www.hudsonrock.com/freetools; if your creds are floating in a stealer log, ask us for an ethical disclosure.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





