By [Alon Gal] | April 2025
Infostealers have become a cornerstone of cybercrime in 2025, infiltrating systems to steal credentials and sensitive data, enabling devastating follow-on attacks. This article for Infostealers.com synthesizes insights from Verizon’s 2025 Data Breach Investigations Report (DBIR), IBM’s X-Force Threat Intelligence Index 2025, and perspectives from cybersecurity leaders like Check Point, Hudson Rock, Huntress, Recorded Future, CrowdStrike, SpyCloud, Sophos, and Mandiant.
It explores the surge in infostealer activity, their real-world impact through 2025 breaches, and how Hudson Rock’s threat intelligence can help organizations stay ahead.
With high-profile incidents underscoring their threat, infostealers are a critical concern for modern cybersecurity.
Infostealers: The Silent Powerhouse of Cybercrime
Infostealers are malicious programs designed to covertly harvest sensitive information, including login credentials, financial details, personal data, and cryptocurrency wallet information, often without detection.
Unlike ransomware’s overt disruption, infostealers thrive in obscurity, making them a preferred tool for cybercriminals. The IBM X-Force Threat Intelligence Index 2025 highlights their versatility, stating, “Infostealers are distributed through techniques such as SEO poisoning, Google Ads, drive-by attacks, and software supply chain compromises.”
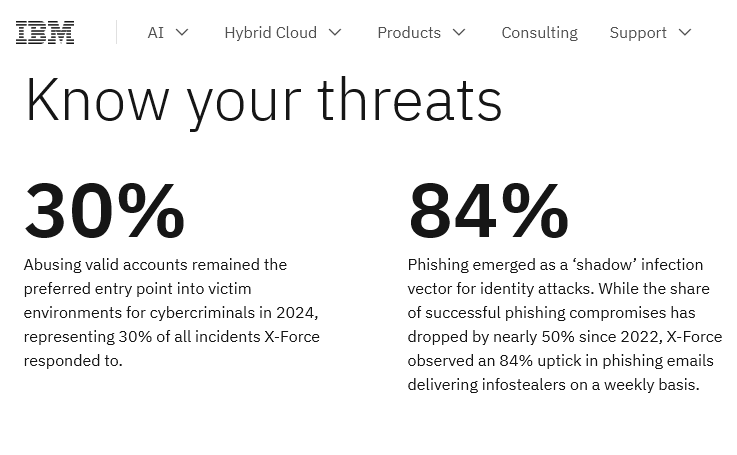
The Verizon 2025 DBIR reveals their enterprise impact: “Analysis performed on information stealer malware (infostealer) credential logs revealed that 30% of the compromised systems can be identified as enterprise-sponsored devices.” Notably, 46% of these were non-managed devices hosting both personal and business credentials, often linked to Bring Your Own Device (BYOD) policies. Check Point Software reinforces this, noting, “Infostealer attacks surged by 58%, revealing a maturing cyber ecosystem. Over 70% of infected devices were personal, as threat actors targeted bring-your-own device (BYOD) environments to breach corporate resources.”

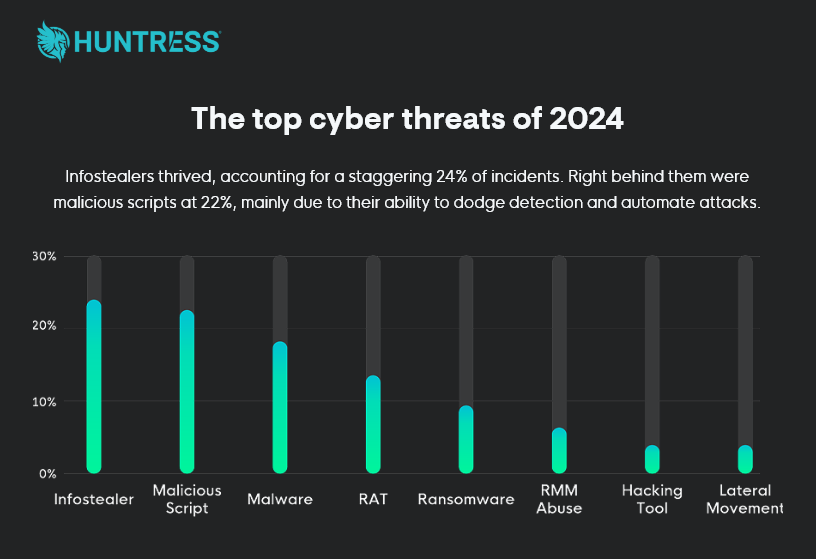
Huntress’s 2025 Cyber Threat Report underscores their dominance, stating, “Infostealers aren’t just a passing trend; they’re a cornerstone of modern cyber threats, driving nearly a quarter (24%) of all cyber incidents in 2024.” Their analysis of over 2 million endpoints showed a 104% year-over-year increase in infostealer detections, with small and medium-sized businesses (SMBs) hit hardest due to limited resources.
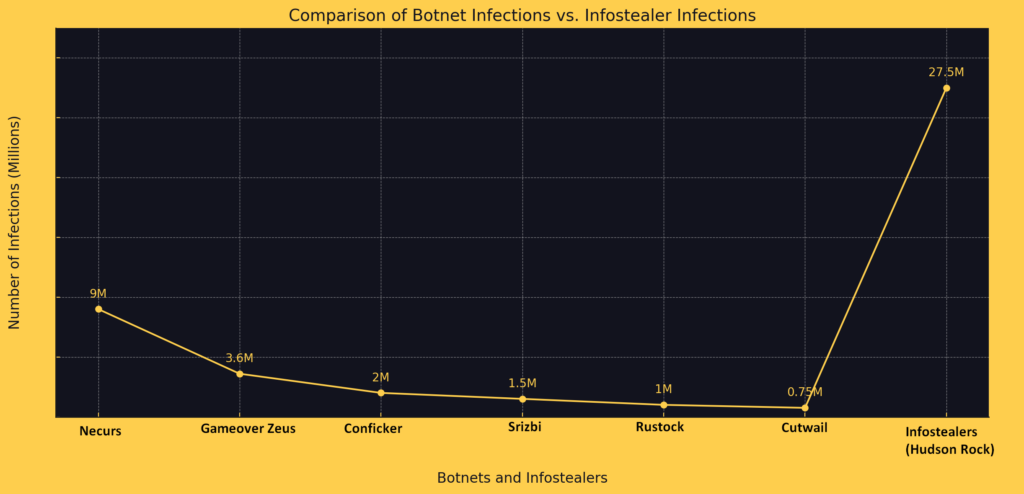
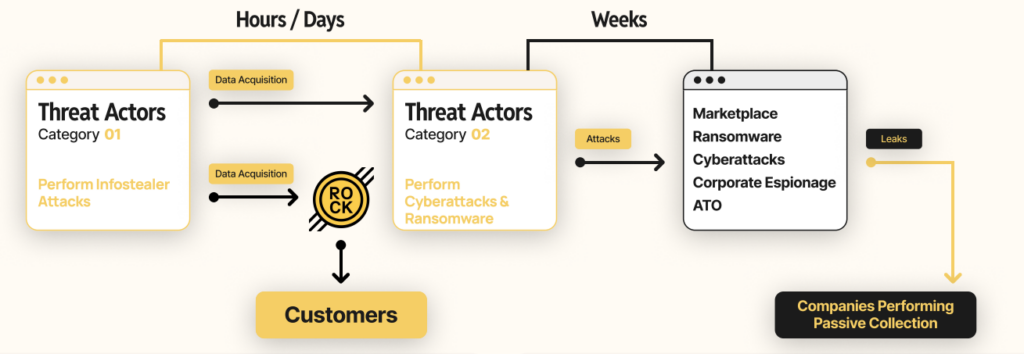
Hudson Rock provides context, noting, “The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of malware: Infostealers. Cybercriminals now favor Infostealers for their efficiency and profitability.”
How Infostealers Infiltrate Systems
Phishing remains the primary delivery mechanism for infostealers, with attackers employing sophisticated tactics. The IBM X-Force report highlights an “84% increase in infostealers delivered via phishing emails per week in 2024 versus 2023,” with early 2025 data showing a 180% surge compared to 2023. Common infostealers like AgentTesla, FormBook, Strela Stealer, Lumma, RisePro, Vidar, and Stealc are often disguised as legitimate invoices or attachments.
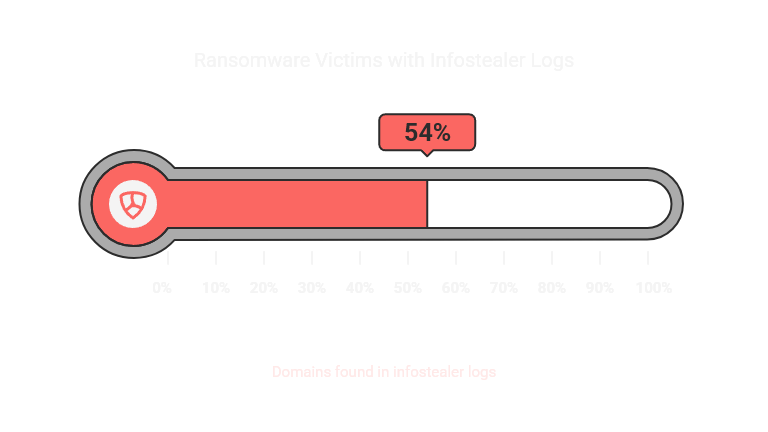
Cloud-hosted phishing campaigns have complicated defenses. IBM notes, “Threat actors have shifted to using cloud hosting services to facilitate mass phishing campaigns,” exploiting trusted platforms like Microsoft Azure Blob Storage to evade detection. Latin America, particularly Brazil, has seen a spike in such campaigns. The Verizon DBIR adds, “By examining some of the victims posted to the ransomware extortion sites, we found that 54% of the victims had their domains show up in at least one infostealer log,” suggesting infostealers often precede ransomware.
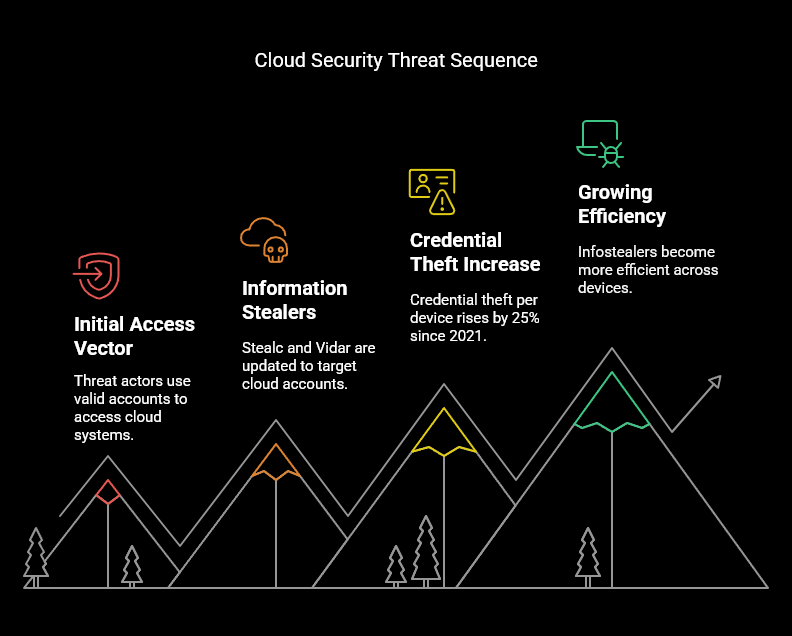
CrowdStrike’s 2025 Global Threat Report highlights the cloud angle, stating, “Abusing valid accounts has become the primary initial access vector to the cloud, accounting for 35% of cloud incidents in the first half of 2024, one likely initial access mechanism is leveraging information stealers; during 2024, threat actors updated Stealc and Vidar to target cloud accounts.” Recorded Future adds, “Credential theft per device has risen 25% since 2021,” underscoring infostealers’ growing efficiency across devices.
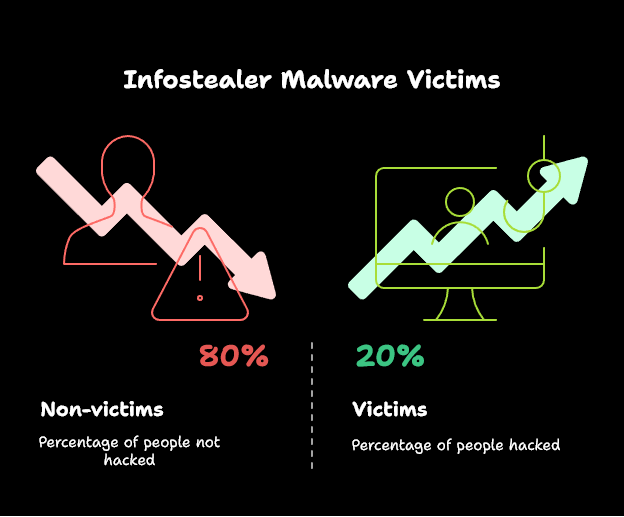
SpyCloud’s 2024 Annual Identity Exposure Report reveals the scale: “In 2023 alone, infostealer malware use tripled. We saw stealers skyrocket in our recaptured data, with as many as 1 in 5 people already the victims of an infostealer infection.” Sophos’s 2024 Threat Report focuses on SMBs, noting, “Data theft is the focus of most malware targeting small and medium businesses; password stealers, keyboard loggers, and other spyware made up nearly half of malware detections.”
The Risks: Fueling Ransomware and Beyond
Infostealers pose significant risks by enabling a range of cyberattacks, with credential harvesting being the most prevalent impact. The IBM X-Force Threat Intelligence Index 2025 states, “Credential harvesting, occurring in 29% of incidents, was the top impact experienced by victim organizations in 2024.” Stolen credentials allow attackers to bypass security measures, including multifactor authentication (MFA), using adversary-in-the-middle (AITM) phishing kits. The Verizon 2025 DBIR notes, “Analysis performed on information stealer malware (infostealer) credential logs revealed that 54% of those victims had their domains show up in the credential dumps,” with 40% involving corporate email addresses, indicating a strong link to subsequent attacks like ransomware.
Mandiant’s Cybersecurity Forecast warns, “We anticipate the use of stolen credentials to persist into 2025, with infostealers continuing to serve as a primary vector to obtain them.”
Real-World Breaches: 2025 Case Studies
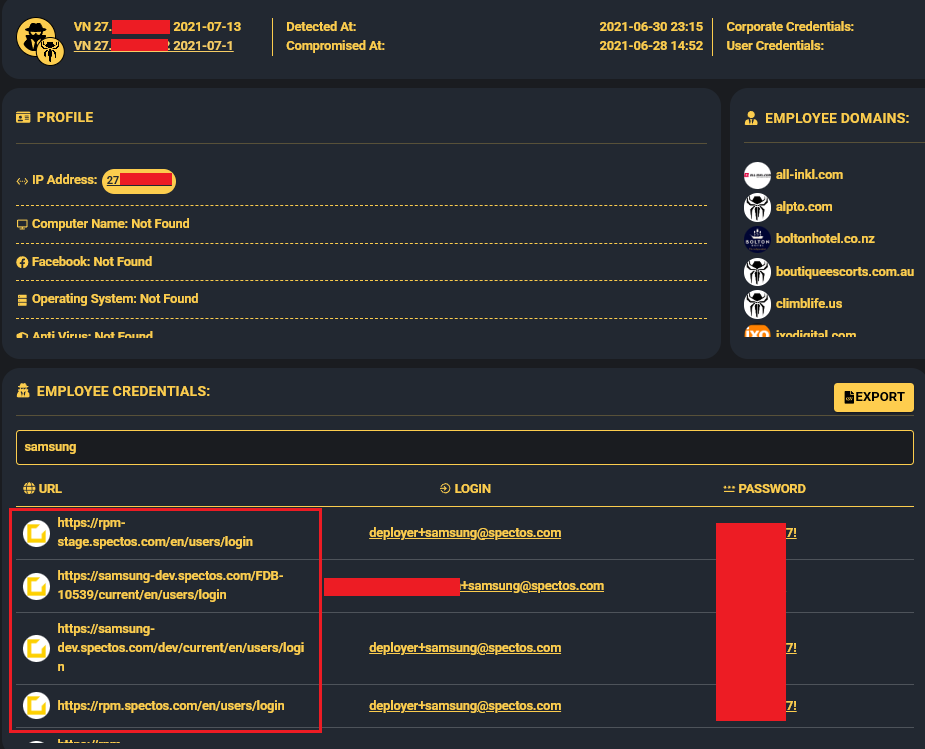
Samsung Tickets Data Leak (March 2025): A hacker, “GHNA,” leaked 270,000 customer tickets from Samsung Germany, sourced from a third-party provider, Spectos, via a 2021 infostealer infection. The free data dump exposed sensitive customer information, highlighting the longevity of stolen credentials (Samsung Tickets Data Leak: Infostealers Strike Again in Massive Free Dump).
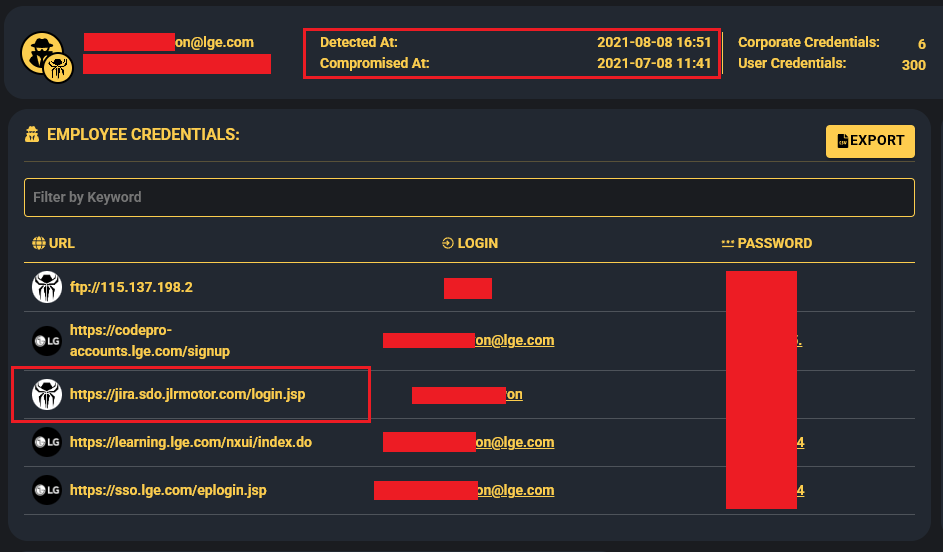
Jaguar Land Rover (March 2025): The HellCat ransomware group, using stolen Jira credentials from infostealers, breached Jaguar Land Rover, leaking proprietary documents and employee data. A second hacker, “APTS,” exploited 2021 infostealer credentials to exfiltrate 350GB more, showing the cascading risks of unmonitored credentials (Jaguar Land Rover Breached by HELLCAT Ransomware Using Its Infostealer Playbook—Then a Second Hacker Strikes).
Telefónica (March 2025): An infostealer infection compromised Telefónica’s internal ticketing system, enabling social engineering and extortion by the HellCat ransomware group. The breach exposed internal communications, emphasizing the need for robust credential security (Telefónica Breach: Infostealer Malware Opens Door for Social Engineering Tactics).
Royal Mail Group (April 2025): Threat actor “GHNA” leaked 144GB of Royal Mail data, including customer PII and Mailchimp mailing lists, via a 2021 infostealer infection at Spectos. AI-driven analysis of the 16,549 files amplified the threat, enabling targeted phishing (Royal Mail Group Loses 144GB to Infostealers: Same Samsung Hacker, Same 2021 Infostealer Log).
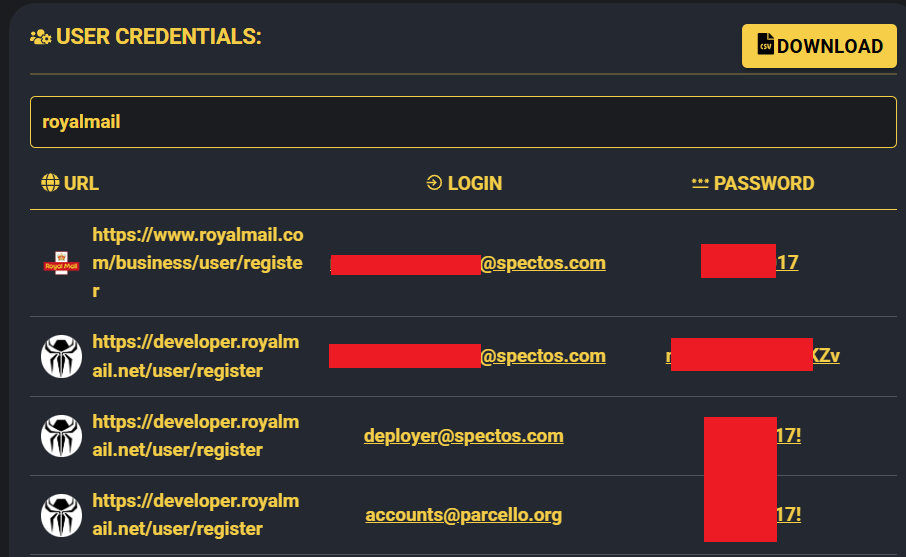
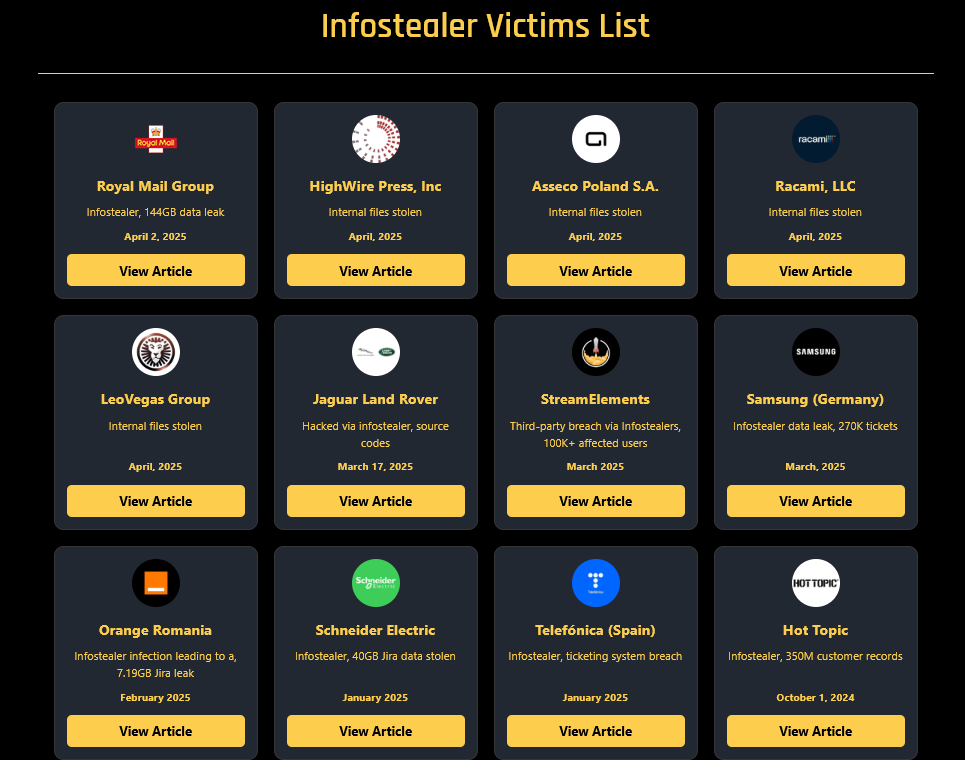
HellCat Ransomware Targets (April 2025): HellCat breached four organizations—HighWire Press, Asseco, Racami, and LeoVegas Group—using stolen Jira credentials from infostealer logs. The attacks extracted internal files and financial records, threatening leaks unless ransoms were paid, showcasing HellCat’s reliance on infostealers (HELLCAT Ransomware Group Strikes Again: Four New Victims Breached via Jira Credentials from Infostealer Logs).
The AI Factor: Amplifying Infostealer Threats
Generative AI (GenAI) is transforming the infostealer landscape by enabling attackers to scale and refine their operations. The IBM X-Force Threat Intelligence Index 2025 observes, “Threat actors are using AI to build websites and incorporate deepfakes in phishing attacks,” as well as to craft phishing emails and malicious code, making campaigns more efficient and harder to detect. The Verizon 2025 DBIR highlights risks from GenAI platforms, noting, “15% of employees were routinely accessing GenAI systems on their corporate devices,” often using non-corporate emails or bypassing authentication, creating new vulnerabilities.
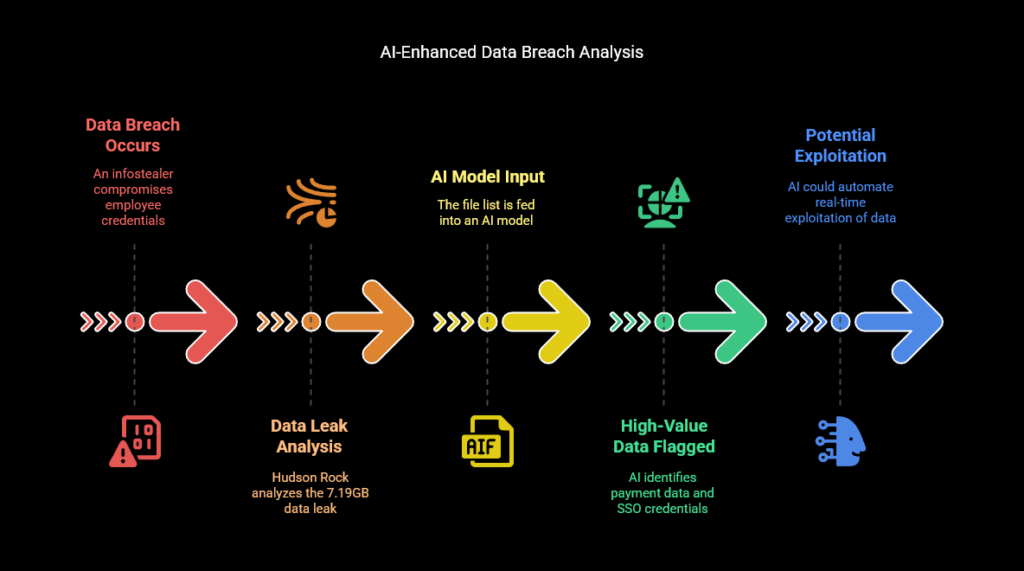
The potential of AI to amplify infostealer threats is evident in the 2025 Orange breach, where an infostealer compromised an employee’s JIRA account credentials. Hudson Rock’s analysis in “AI’s Role in Turning Massive Data Leaks into Hacker Paydays: A Look at the Orange Breach” illustrates how attackers could use AI to analyze the resulting 7.19GB data leak, containing 8,601 files.
Hudson Rock fed the file list into an AI model, which flagged high-value items like payment data and SSO credentials, demonstrating how AI can rapidly sift through massive leaks to identify exploitable data for phishing or extortion, though attackers in this case did not deploy AI. This foreshadows a future where AI could automate real-time exploitation of infostealer data.
Fighting Back: Strategies and Hudson Rock’s Role
To combat infostealers, organizations must adopt a multi-layered approach. Here are key strategies, with Hudson Rock’s threat intelligence as a critical tool:
- Strengthen Phishing Defenses: IBM recommends “time-sensitive threat intelligence tools to block URLs flagged as malicious” and deploying endpoint detection and response (EDR) systems. Huntress emphasizes phishing awareness training to address human error (2025 Cyber Threat Report).
- Enhance Credential Security: Verizon and IBM advocate for widespread MFA and passkeys. IBM’s action guide states, “Significantly expand MFA use” and modernize identity strategies. CrowdStrike’s focus on cloud account protection underscores robust identity management (2025 Global Threat Report).
- Monitor the Dark Web with Hudson Rock: Hudson Rock’s threat intelligence platform is vital for detecting infostealer threats. By sourcing Infostealers data, Hudson Rock identifies stolen credentials before they’re weaponized, offering real-time insights. IBM’s recommendation to “monitor the dark web to gather real-world threat intelligence” aligns with Hudson Rock’s capabilities. Check exposure using Hudson Rock’s free tools at Hudson Rock Free Tools or schedule a demo for Infostealer Intelligence solutions – Hudson Rock Demo.
- Secure AI and Cloud Environments: With attackers exploiting cloud services and AI, Verizon and IBM advocate securing AI pipelines and cloud infrastructure. IBM emphasizes, “Secure each stage of the AI pipeline including the data used to train, test, and tune models.”
- Patch and Update Systems: Huntress, Sophos, and IBM highlight timely patching, especially for SMBs. Sophos notes the need for regular updates to close vulnerabilities exploited by infostealers (2024 Sophos Threat Report).
The Bottom Line
Infostealers are a silent epidemic, driving credential theft, ransomware, and supply chain attacks across industries. The Verizon 2025 DBIR, IBM X-Force Threat Intelligence Index 2025, and insights from Check Point, Huntress, Recorded Future, CrowdStrike, SpyCloud, Sophos, and Mandiant reveal their surging volume and sophistication, targeting SMBs, healthcare, and technology sectors. The 2025 breaches at Orange, Samsung, Telefonica, and Royal Mail underscore their real-world impact.
Hudson Rock’s dark web monitoring is a critical weapon, empowering organizations to detect and neutralize infostealer threats before they escalate. At Infostealers.com, we urge you to stay vigilant, secure your credentials, patch your systems, and leverage solutions like Hudson Rock to keep cybercriminals at bay. The infostealer threat is real, but with the right tools and strategies, we can fight back.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





