By [Alon Gal] | March 2025
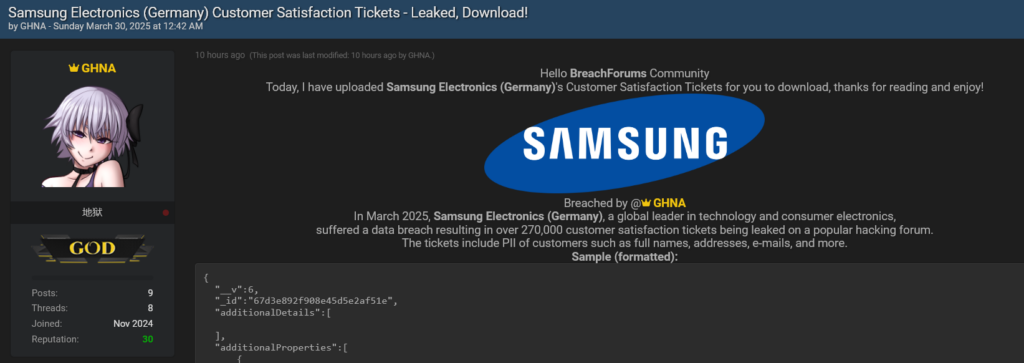
Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs.
A hacker going by the alias “GHNA” has dumped a staggering 270,000 customer tickets from Samsung Germany online, completely free of charge. The data, which appears to be sourced from samsung-shop.spectos.com, didn’t come from some sophisticated zero-day exploit or insider betrayal. No, this breach traces back to credentials stolen by infostealers way back in 2021. Credentials that cybercrime intelligence firm, Hudson Rock, has had in its database for years.
This could’ve been prevented, but instead, it’s now a treasure trove for cybercriminals worldwide. Let’s break it down.
How It Happened: Infostealers Strike Again
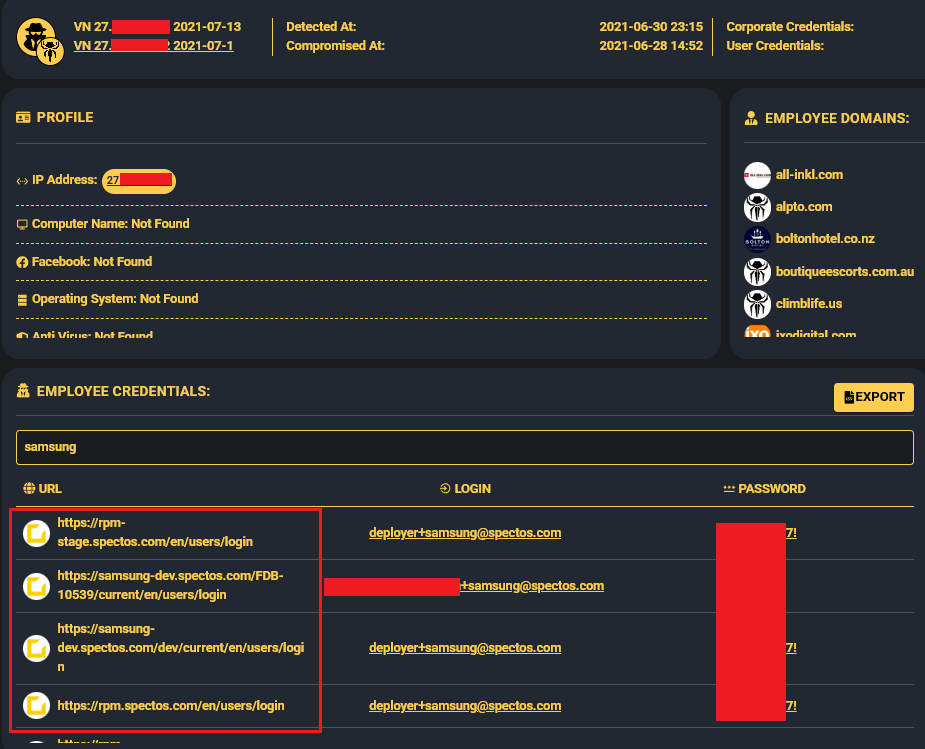
The story starts in 2021, when a Raccoon Infostealer malware silently harvested login credentials from an employee of Spectos GmbH which is used for monitoring and improving service quality and is tied to Samsung’s German ticketing system at samsung-shop.spectos.com as evident in the leak:
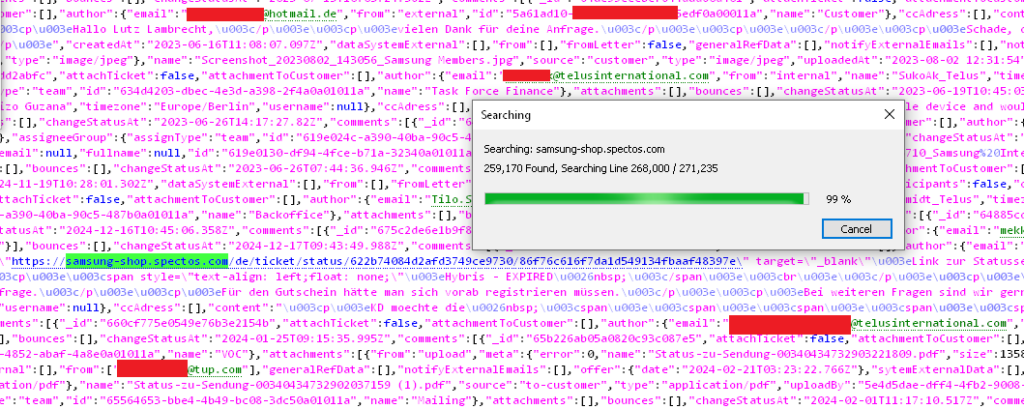
These credentials sat dormant, until “GHNA” got their hands on them. Fast forward to 2025, and boom: 270,000 customer tickets hit the open internet, most of them from 2025, courtesy of a simple login that never got rotated.
At Hudson Rock, we flagged these compromised credentials years ago in our Cavalier database, which tracks over 30 million infected machines. Samsung could’ve acted, but they didn’t, and now the damage is done.
This isn’t a one-off fluke. We’ve seen this playbook before—Telefonica’s ticketing system breach in January 2025, Jaguar Land Rover’s Jira fiasco earlier this month, even Snowflake’s customers such as AT&T suffered massive leaks last year.
Infostealers don’t need to brute-force their way in; they just wait for human error to hand them the keys. And when companies fail to monitor or rotate credentials, it’s game over.
What’s in the Leak? A Goldmine of Sensitive Data
The 270,000 tickets aren’t just random support logs—they’re a detailed snapshot of Samsung Germany’s customer base. Based on a sample we analyzed, here’s the sensitive data “GHNA” was able to leak:
- Personal Identifiable Information (PII):
- Full names (e.g., “John Förster”)
- Email addresses (e.g., “josi_92@gmx.de)
- Home addresses (e.g., “Trautenauer Str. 26, 85121 Dachau”)
- Transactional Details:
- Order numbers (e.g., “DE2213214-32511544”)
- Model numbers (e.g., “GU52AU7299UXZG” for a Crystal UHD TV)
- Payment methods (e.g., “de-adyenPaypal”)
- Prices and discounts (e.g., “469.00, 1029.00”)
- Tracking URLs (e.g., “https://myhes.de/de/tracking/xx7932321243293000“)
- Support Interactions:
- Ticket IDs (e.g., “230406.0095829”)
- Agent emails (e.g., “Tilo.Schmidt@telusinternational.com”)
- Customer emails notified (e.g., “josi_92@gmx.de)
- Communication:
- Issue descriptions (e.g., “DHL Lieferverfolgung sagt zugestellt, KD hat allerdings nichts erhalten. Bitte um Überprüfung” – “DHL tracking says delivered, but the customer received nothing. Please check.”)
- Vendor responses (e.g., “Hallo Jan H, … Wenn du deine Bestellung oder Teile davon nicht erhalten hast, sende uns bitte die ausgefüllte und unterschriebene Empfängererklärung zu” – “Hello Jan H, … If you haven’t received your order or parts of it, please send us the completed and signed recipient declaration.”)
This isn’t just a list of names—it’s a roadmap to people’s lives. From exact addresses to what TV they bought three years ago, it’s all there, dumped for anyone to grab. And since it’s free, the barrier to entry for exploitation is zero.
What Can Hackers Do With This? The Fun Stuff
When I say “interesting use cases,” I mean the creative ways cybercriminals can turn this data into chaos. Here are some of the standout possibilities:
- Physical World Attacks: “Porch Pirate 2.0”
- With full addresses, order numbers, and tracking URLs, hackers could monitor delivery schedules and swoop in to steal packages. Imagine a script scraping the leak for high-value items (like that “PREMIUM UHD TV”), cross-referencing active tracking links, and dispatching local thieves. It’s not just digital—these guys could show up at your doorstep.
- Hyper-Targeted Phishing: “Samsung Calling”
- Armed with names, emails, and exact purchase details, a hacker could craft phishing emails that look scarily legit. Picture this: “Dear Joseph Förster, we’re processing your return for order DE321116-32511544 (GU50AV7199UXZG). Click here to confirm your refund.” Few clicks later and your own computer is infected by an Infostealer or your credit card number is stolen.
- Fake Warranty Claims
- Hackers could use order numbers (e.g., “DE230616-51431354”), model numbers (e.g., “MZ-V8P2T0BW”), and purchase dates (e.g., “2025-06-16 06:11:00”) to submit fraudulent warranty claims to Samsung or third-party retailers. They could claim the product was defective, leveraging tracking URLs (e.g., DHL’s “8376959286”) to “prove” delivery, and request replacements or refunds sent to a new address or account.
- Account Takeover via Customer Support Impersonation:
- Using ticket IDs (e.g., “230621.0105676”), customer emails (e.g., “b.andrea@hotmail.de”), and support agent details (e.g., “Brian.Wagner@telusinternational.com”), hackers could impersonate Samsung support via email or phone. They could trick customers into “verifying” their account by providing passwords or 2FA codes, claiming it’s needed to resolve an ongoing ticket issue like “Lieferung unvollständig” (incomplete delivery).
AI Turns Messy Leaks Into Gold
Here’s where it gets scary: even a messy dump like this—270,000 tickets with inconsistent fields, attachments, and half-filled data can be weaponized at scale with AI.
Back in January, we dug into this exact scenario with the Orange breach (AI’s Role in Turning Massive Data Leaks Into Hacker Paydays). That leak was a chaotic pile of customer records, but AI tools like LLMs parsed it in hours, extracting emails, phone numbers, and billing details for automated phishing campaigns. Samsung’s leak is no different.
Picture this: an AI model ingests these tickets, sifts through the JSON mess—names, addresses, order numbers, even PDFs like “Empfaengererklaerung.pdf” and spits out clean datasets.
It could flag high-value targets (e.g., “high” priority tickets or pricey items like “1029.00” TVs), generate tailored phishing emails, or even script fake support calls using voice synthesis, all in real time. Our Orange research predicts a spike in exploit efficiency when AI was involved. Hackers will go from manual cherry-picking to hitting thousands of victims daily. With “GHNA” handing this out for free, any script kiddie with a GPT knockoff could turn it into a payday. That’s the future we’re staring at.
This breach is a wake-up call. Infostealers aren’t a trending threat—they’re a slow burn that explodes when you least expect it. Companies can’t just patch and pray; they need to hunt down stolen creds proactively. Our Cavalier tool flagged this, just like it did for Telefonica and JLR. The pattern’s clear: ignore infostealers, and you’re next.
Closing Thoughts
“GHNA” didn’t sell this data for millions—they gave it away, which makes it even more dangerous. Free dumps democratize crime, letting script kiddies and pros alike run wild.
For Samsung, it’s a PR nightmare and a legal headache (GDPR fines?). For the 270,000 customers, it’s a race against exploitation. And for us at Infostealers.com, it’s another case study in why Infostealers, and now AI, remain the king of attack vectors in 2025.
Stay vigilant. Check your email against Infostealer logs for free, rotate your passwords, and if you’re a company, talk to us at Hudson Rock before your old creds come back to haunt you. “GHNA” won’t be the last to pull this stunt.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





