Sextortion schemes are about to take a much darker turn. With the rise of Infostealer malware, the game is changing. Hackers will no longer rely on fake threats or generic scare tactics like Google Street View images. Instead, they now have access to real victim data pulled straight from infected computers—data that includes sensitive browsing history, personal photos, and even login credentials to adult websites.
One alarming statistic: over 500,000 unique infected computers contain credentials for pornhub(.)com. And that’s just for users who logged in—many more likely have their sensitive browsing history recorded. It’s only a matter of time before hackers use this data to launch targeted, highly convincing sextortion efforts.
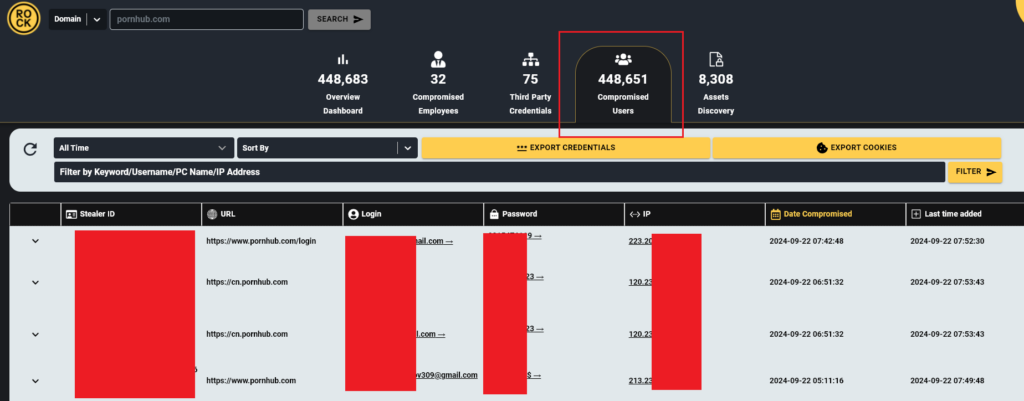
The Next Step for Sextortion: Real Victim Data
Imagine this: You download what seems to be a harmless file, maybe a cracked software, or you open an email attachment that slipped past your spam filter. The next day, you receive an email claiming to have access to your computer, but this time it’s different. The email includes not just vague threats, but details about the websites you visited, the videos you watched, and even a picture from your computer’s camera.
What makes this terrifying is the credibility. It’s not a fabricated story or a random scare tactic anymore. Hackers have your real data—browsing history, login details, maybe even personal photos that were on your device. Suddenly, the threat feels very real. For the victim, it’s a nightmare scenario. You’re left questioning how much they actually know and whether or not they have the power to carry out a sextortion scheme.
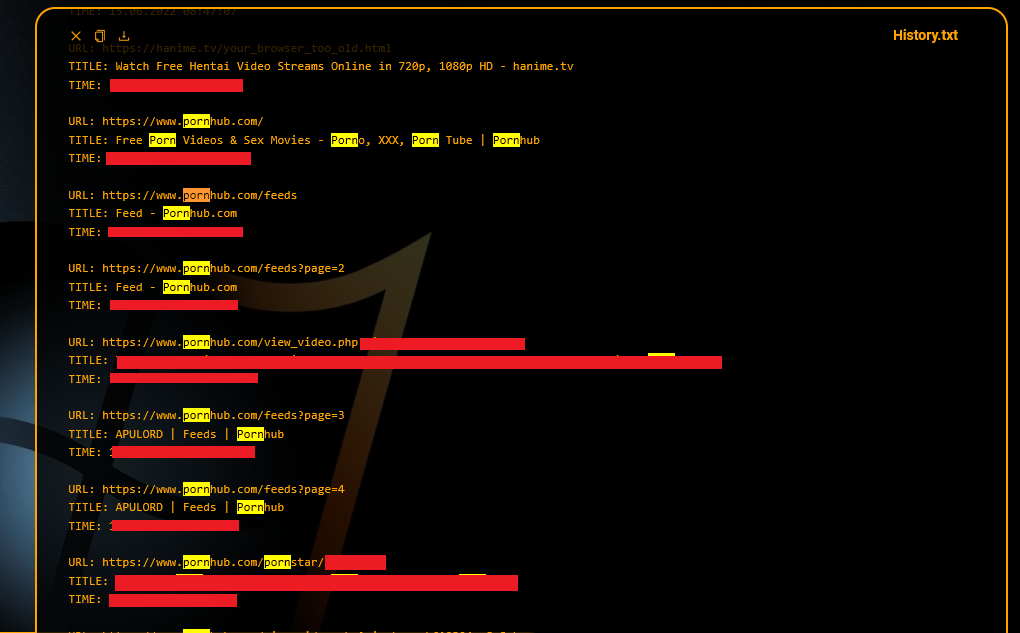
A Growing Problem: Infostealer Malware and Its Impact
Infostealers are becoming a common tool for cybercriminals, silently gathering massive amounts of data from compromised devices. And this isn’t just about stolen passwords anymore. Most modern Infostealer families now have the ability to collect browsing history, cookies, autofill data, and even sensitive files from victim computers.
It would come at no surprise if Infostealer developers support this kind of use case when building new features into different Infostealers families, such as grabbing victim photos from their computers and even filming victims who experience sextortion that involves computer cameras.
A Dangerous Evolution in Cybercrime
Sextortion schemes built on stolen Infostealer data are poised to be far more successful than the fake threats we’ve seen in the past. The use of real data significantly increases the psychological pressure on victims, making them more likely to comply with demands out of fear and embarrassment.
While most current sextortion schemes are easily identified as hoaxes, these new attacks could be indistinguishable from real breaches. It’s a frightening thought, but one we need to prepare for.
What Comes Next?
The reality is, it’s hard to say exactly how we can protect against these new types of sextortion threats. But one thing is clear: awareness is key. We need to start thinking about this now before it becomes widespread. More research and prevention measures are necessary to counteract the growing capabilities of Infostealer malware and the criminals who use it.
While we don’t have all the answers yet, we do know that it’s only a matter of time before sextortion becomes the next big cybercrime wave. Hackers are getting smarter, and the tools they use are becoming more sophisticated. It’s time to start having serious conversations about how to shield ourselves from this looming threat.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock





