By [Alon Gal] | March 2025
StreamElements, a popular cloud-based streaming platform, has confirmed a significant data breach involving a third-party service provider, following reports of stolen data being offered for sale on a hacking forum.
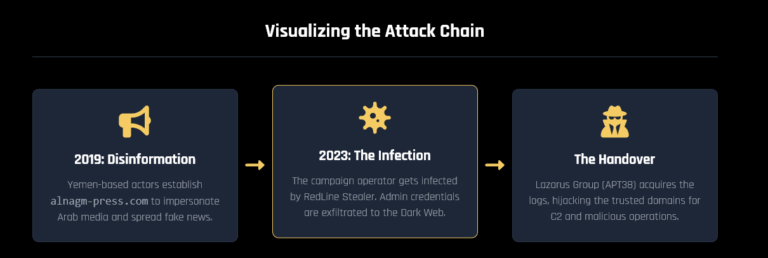
The breach, which potentially impacts over 100,000 individuals, exposed sensitive information including names, addresses, phone numbers, and emails. New details from Hudson Rock confirm that the breach was facilitated by a Redline Infostealer infection that compromised an employee’s corporate credentials, granting attackers access to a third-party service, Gooten.com, used by StreamElements for its merchandise operations.
The Breach: A Timeline of Events
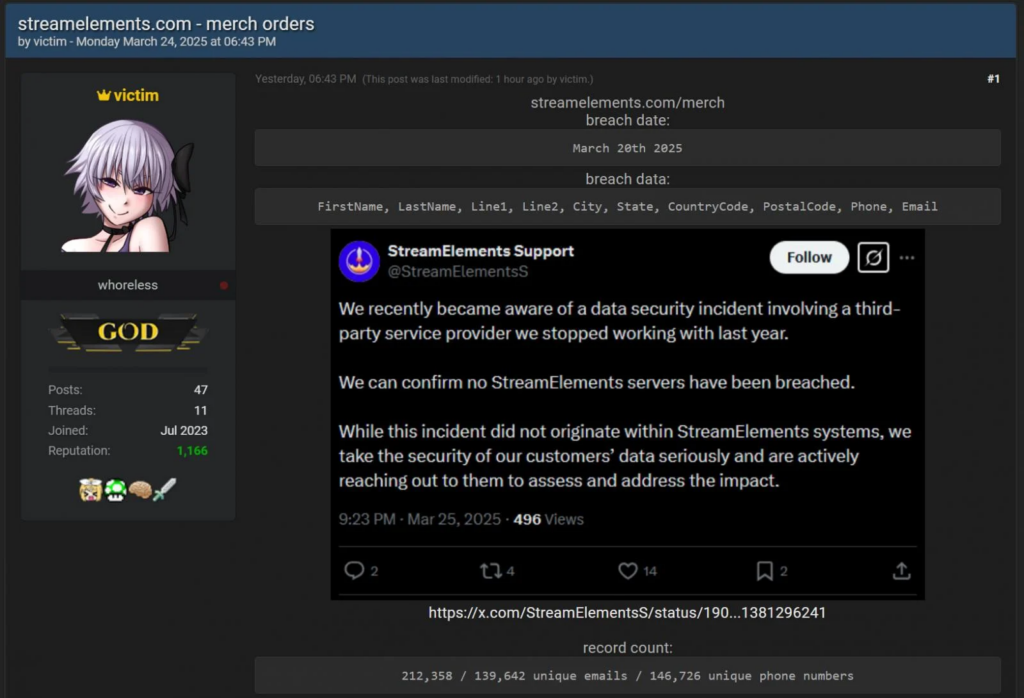
The incident came to light on March 24, 2025, when VX-Underground reported on X that an alleged data breach of StreamElements was up for sale, with a sample of 212,358 lines of data containing personal information such as names, addresses, phone numbers, and emails.
StreamElements web store was compromised. Over 100,000 people impacted.
— vx-underground (@vxunderground) March 25, 2025
The Threat Actor responsible was kind enough to notify the impacted customers by sending all of them an email from "Diddy Squad".
The following day, Zach Bussey (@zachbussey) amplified the report, noting that the breach could affect over 100,000 people, with the stolen data allegedly extracted from StreamElements’ Order Management System between 2020 and 2024—covering the period when StreamElements was active in the merchandise business.
StreamElements issued a statement on March 25, 2025, confirming that the breach originated from a third-party service provider they had ceased working with in the previous year. The company emphasized that no StreamElements servers were directly compromised, stating, “While the incident did not originate within StreamElements systems, we take the security of our customers’ data seriously and are actively reaching out to them to assess and address the impact.”
How the Breach Happened: Redline Infostealer Grabbing Third Party Credentials
Further investigation by Hudson Rock, a cybercrime intelligence firm, revealed the root cause of the breach.
The firm confirmed with the StreamElements team that the attack began with a Redline Infostealer infection targeting an employee in July 2023. The malware successfully extracted corporate credentials linked to Gooten.com, a third-party print-on-demand service StreamElements used for its merchandise operations.
Armed with these credentials, and only years later, threat actors gained unauthorized access to StreamElements’ Order Management System, allowing them to export order data spanning from 2020 to 2024.
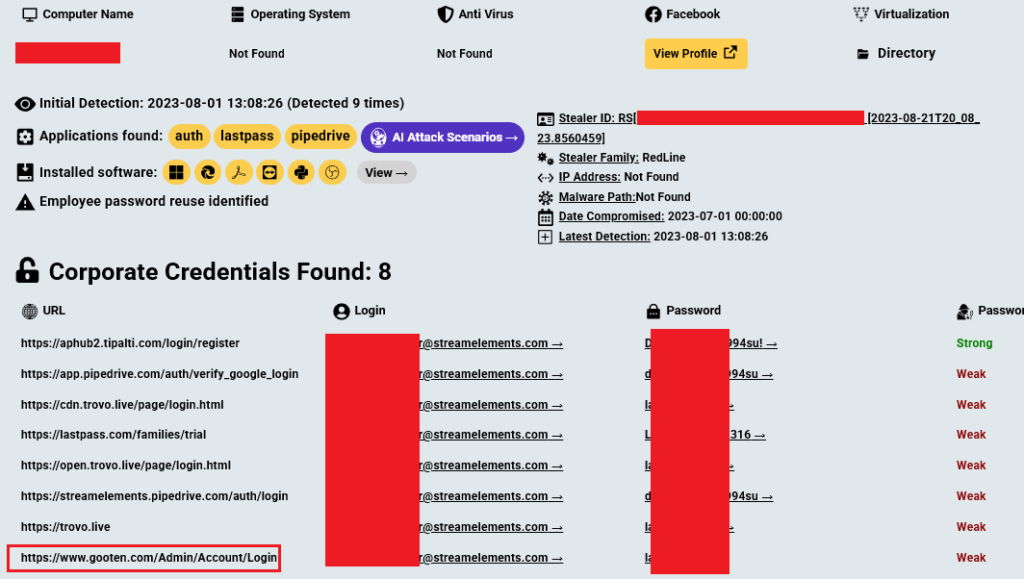
It is important to note that Hudson Rock had these credentials years prior to the attack, making the breach highly preventable.
Lessons from the StreamElements Breach
The StreamElements breach serves as a stark reminder of the persistent threat posed by infostealer malware like Redline. As seen in other high-profile incidents, such as the Jaguar Land Rover breach & WideOpenWest data breach, both occurring in March 2025.
These malware variants exploit human vulnerabilities to gain access to corporate systems. Hudson Rock’s findings in the Telefonica case also highlighted the importance of enforcing strong password policies—a lesson StreamElements may need to heed moving forward.
For organizations, this incident underscores the importance of robust cybersecurity practices, including:
- Employee Training: Regular training on phishing awareness and safe online practices can reduce the risk of infostealer infections.
- Third-Party Risk Management: Companies must thoroughly vet and monitor third-party service providers to ensure they meet stringent security standards.
- Credential Security: Enforcing strong password policies and implementing multi-factor authentication (MFA) can mitigate the impact of stolen credentials.
- Proactive Monitoring: Leveraging cybercrime intelligence tools, like those provided by Hudson Rock, can help organizations detect and respond to infostealer infections before they lead to a breach.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by infostealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock