Falling victim to an infostealer, such as Redline, is arguably one of the biggest threats to consumers—individual users who might seem less lucrative targets compared to businesses. Traditional malware often targets enterprises, banking on their urgency to maintain operations and their capacity to pay hefty ransoms. Consumers, on the other hand, might find it more feasible to replace their PC than to negotiate with cybercriminals.
Why Redline Poses a Monumental Risk
Redline isn’t your average malware. It’s designed to slip past enterprise-level EDR systems, and its track record includes breaching government and military defences. This level of sophistication spells disaster for the average user, whose PC is a treasure trove of sensitive data: personal information, emails, family photos, financial details, and possibly even identification documents. Worse still, Redline can introduce additional malware, potentially enabling attackers to spy through webcams.
This scenario is alarming for any adult, but the risk to children online is even more concerning.
The Ethical Void in Malware Distribution
While some malware distributors might target large corporations out of a misguided sense of ethics, others exhibit no such restraint, targeting anyone within reach, including children. This is particularly alarming given recent findings by Kaspersky, which revealed that Redline stealer is being disguised as game cheats on YouTube—a platform and category with a significant child audience.
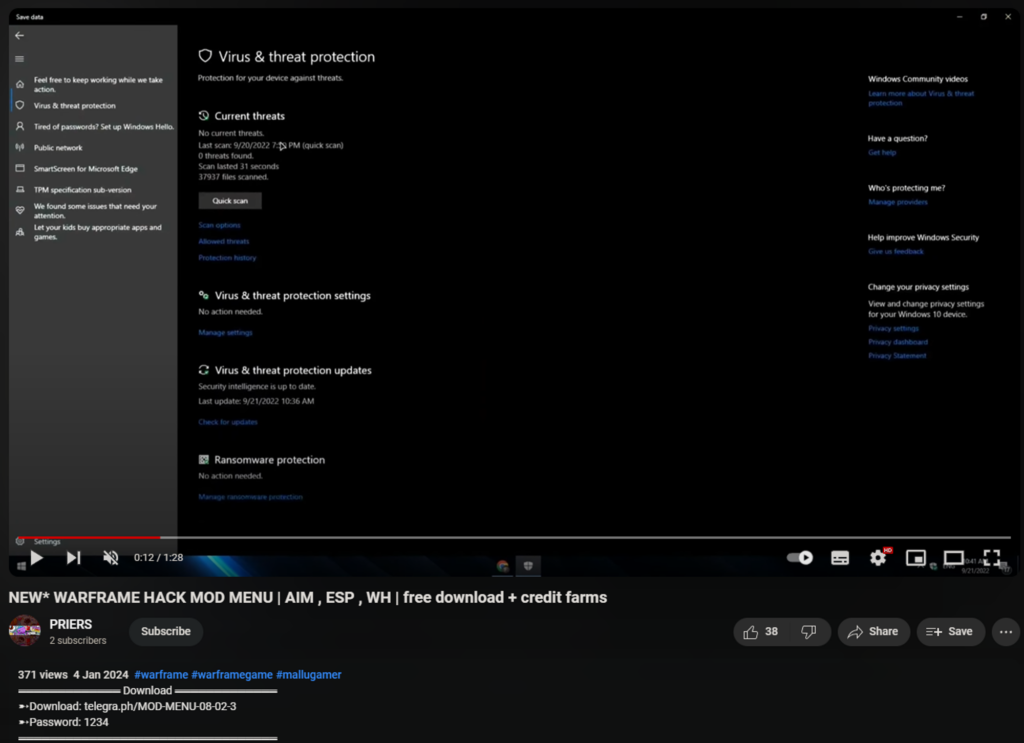
Case in Point: A YouTube Distribution Example
Consider the channel PRIERS, as seen above, which boasts a modest following of just 2 subscribers. Within the first 12 seconds of this video, it instructs viewers on disabling their device’s protection—ensuring the malware operates unimpeded.
This strategy of masquerading malicious software as harmless game cheats not only underscores the ease with which these threats are distributed but also highlights the vulnerability of a demographic often overlooked in discussions on cybersecurity: children.
The Usual Stealer Malware: Unveiling Redline
A very common stealer malware, like Redline, can be used beyond the conventional understanding of cyber threats. This scenario preys on the common misconception that antivirus software may incorrectly flag legitimate software—like game cheats—as malicious. This grey area provides fertile ground for malware distributors, allowing them to exploit the trust of unsuspecting users. The tactic is alarmingly simple: convince users to disable their antivirus under the guise of overcoming ‘false’ positives, thereby ensuring malware like Redline can operate unhindered.
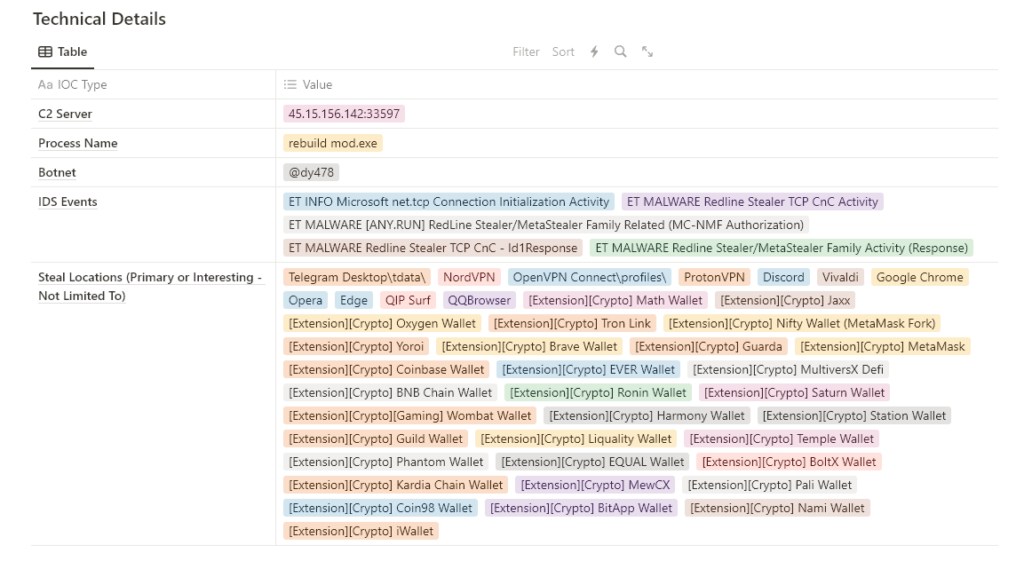
A Closer Look at the Adversary’s Tactics
A subtle hint to the operational deceit lies in the adversary’s choice of language settings—often displayed as EN on the desktop, possibly to align with the target audience or to obfuscate their true location. Delving into the Command and Control (C2) server’s location reveals a web of complexities further entangled by the staggering statistics provided by Hudson Rock: over 317,000 Warframe user accounts compromised, a significant fraction of the game’s 36 million registered users.
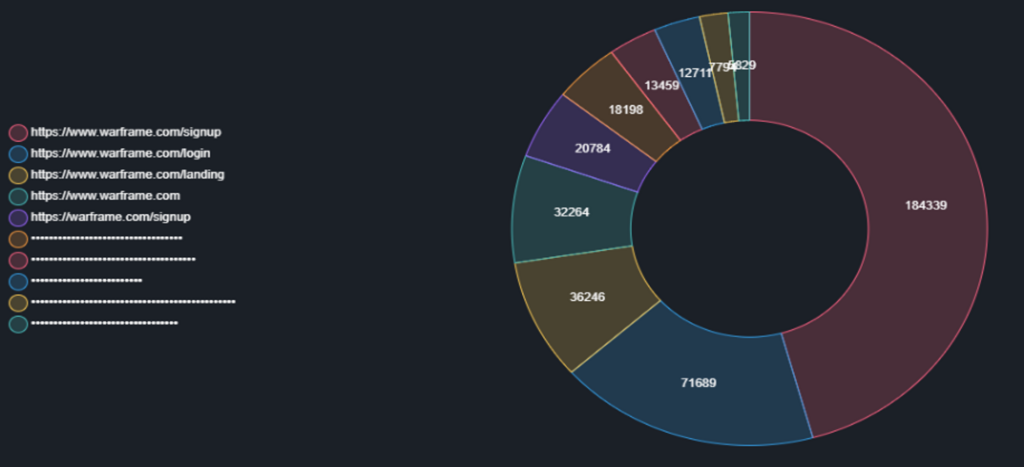
Feb 2023, Warframe Compromised Users, Credits: Hudson Rock
The data, revealing continuous breaches with the last compromised account detected merely hours before reporting, underscores the relentless nature of this threat.
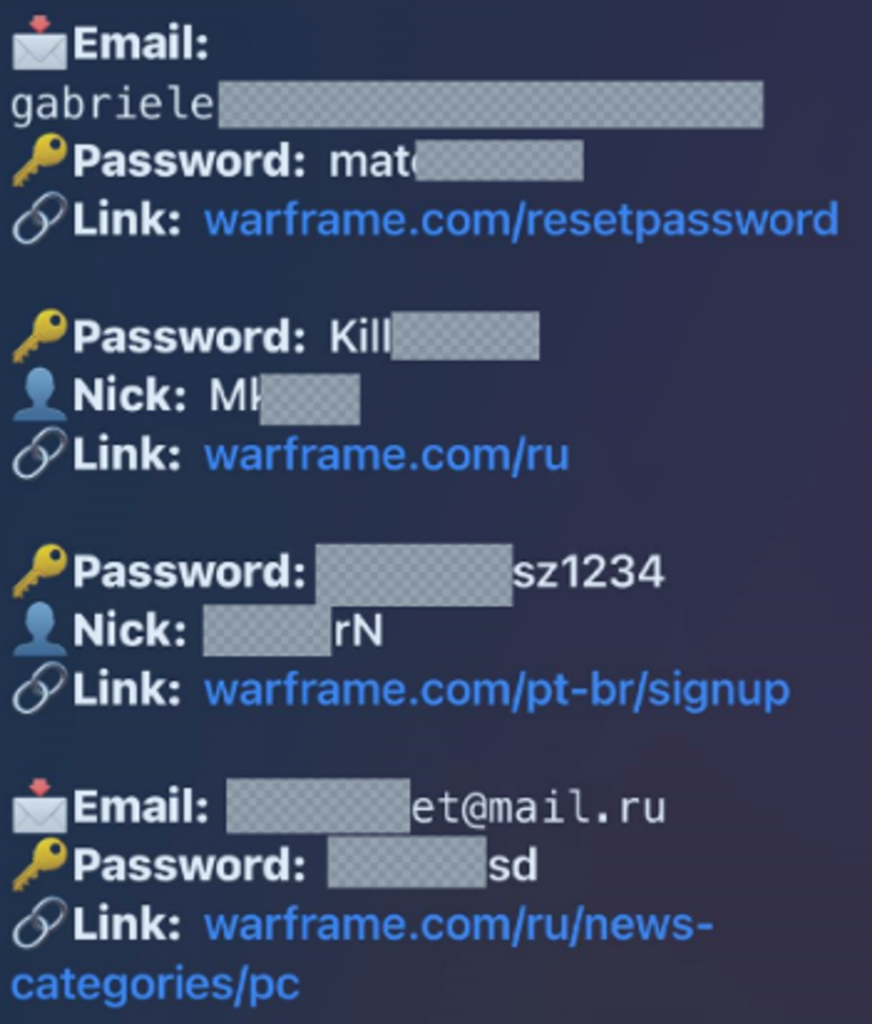
Data Pulled from Naz.API
The depth of the issue is further illuminated by the Naz.Api’s aggregation of stolen credentials, highlighting the extensive reach of such stealers.
Unmasking the (somehow) Undetected C2
Despite the apparent visibility of this C2 server on platforms like Abuse.ch, where it’s unequivocally linked to Redline, there’s a puzzling lack of widespread flagging across the cyber security community.
This discrepancy raises critical questions about the effectiveness of current detection and response strategies against such malware campaigns impacting everyday users.
Preventing Compromise
In the face of these prominent threats, the best defence is a combination of caution and adherence to general best practice:
- Always download software from reputable sources.
- Don’t deactivate your anti-virus; it’s your main defence.
- Steer clear of cracked software and piracy websites.
- Above all, question the credibility of online advice, especially when it could compromise your security and privacy
Today when adversaries are consistently evolving their strategies, staying informed and vigilant is paramount. The battle against malware like Redline is not just about technological defences but also about understanding and anticipating the tactics employed by cyber adversaries.
Elevated Risk to Crypto Wallets
The threat from stealer malware like Redline extends significantly into the cryptocurrency domain. Given the decentralized nature of crypto assets and the autonomy users have over their wallets, these digital assets are particularly exposed.
Redline has shown capability to access and empty crypto wallets, leveraging the anonymity and irreversible nature of crypto transactions to its advantage. This situation highlights a stark reality: the security of digital assets is paramount, yet often overlooked.

The Broader Financial Motivation
Redline’s primary focus is financial gain, targeting major browsers: Edge, Firefox, and Chrome – to access financial and crypto wallet information. This approach is not random but a calculated effort to extract valuable assets directly. Where direct financial gain is not immediately achievable, the strategy shifts towards monetizing the stolen data through sales to the highest bidder, irrespective of the buyer’s identity or intentions.
In Summary: The risk is universal
The belief of “I have nothing to hide” is a misconception in today’s digital landscape. Stealer malware like Redline shows that everyone has data of value, from financial details to children’s personal information. This universal risk demands a vigilant approach to digital security.





