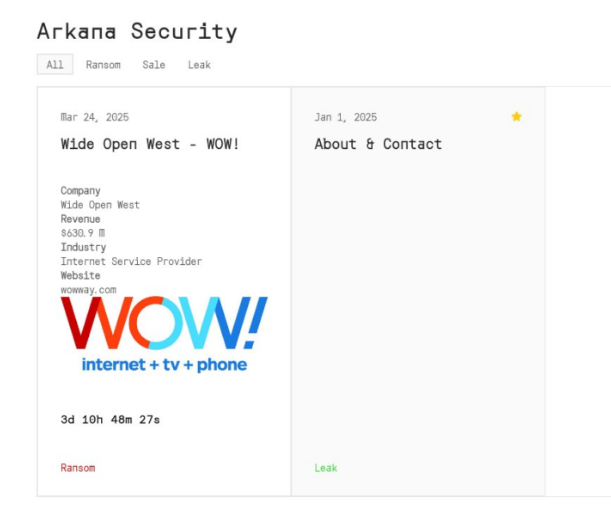
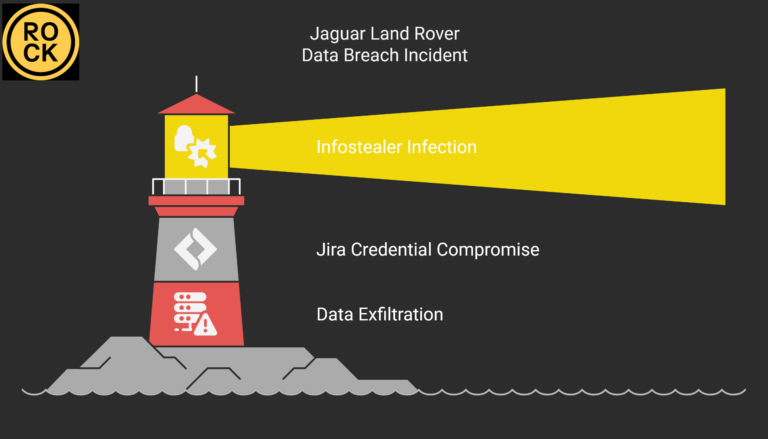
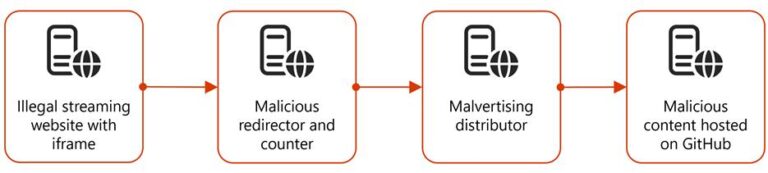
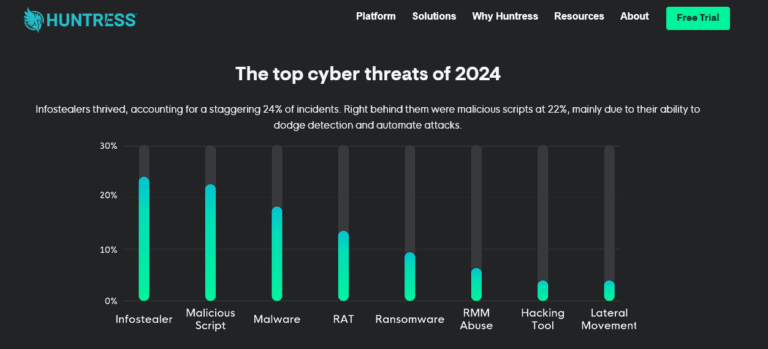
HELLCAT Ransomware Group Strikes Again: Four New Victims Breached via Jira Credentials from Infostealer Logs
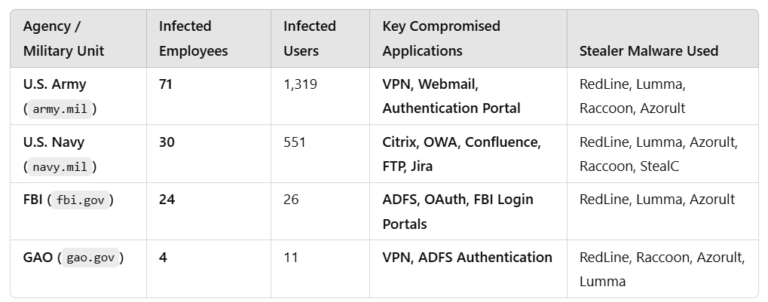
By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting