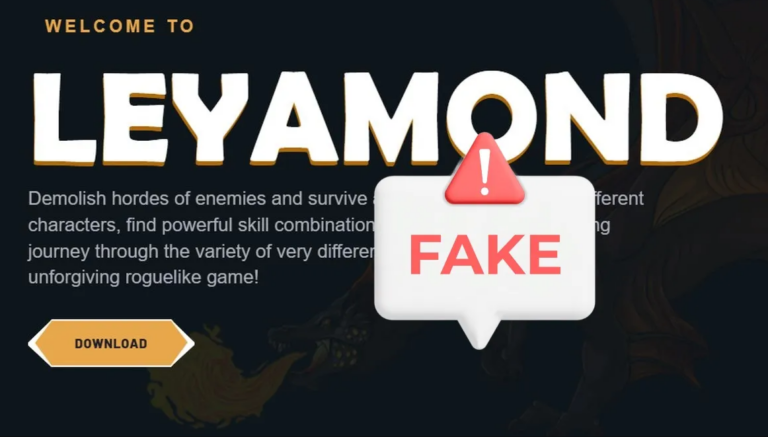
“Can you try a game I made?” Fake Game Sites Lead to Information Stealers
The background and the IOCs for this blog were gathered by an Expert helper on our forums and Malwarebytes researchers. Our thanks go out to

The background and the IOCs for this blog were gathered by an Expert helper on our forums and Malwarebytes researchers. Our thanks go out to

The cybersecurity landscape is rife with challenges, but some threats are quieter, subtler — and deadlier. Info stealers, the silent operators of the malware world,
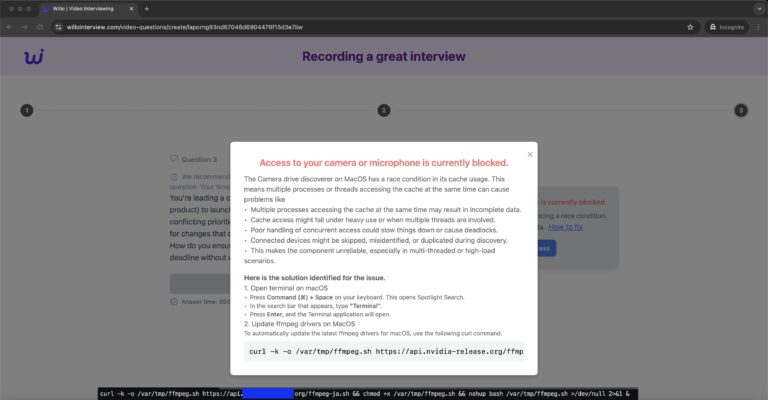
In a recent campaign, North Korean threat actors have demonstrated a sophisticated approach by copying novel malware distribution techniques, notably those employed in the Clickfix
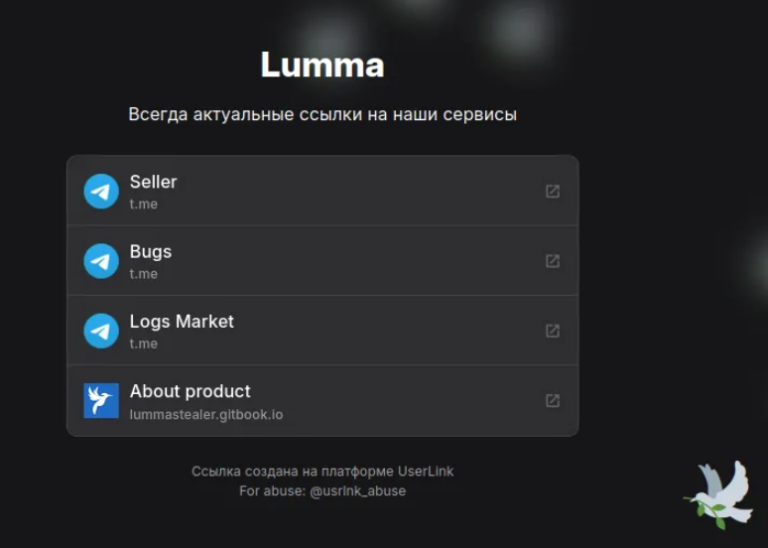
In this blog, we analyze the evolution of Lumma in 2024, based on the Diamond Model vertices. Disclaimer: Everything stated in this blog is for

In our previous interview with Pryx, the threat actor briefly touched upon the concept of server-side stealers claiming it to be completely different from how traditional

Another finding by Fox, related to LummaC2 infostealer sparked an infra hunt that led to many findings. C2 Host Pivot & Windows Server Pattern Following the

If there is one type of content strictly banned and monitored across every platform on the internet, it is the CSAM (Child Sexual Abuse Material).
In a recent interview given to Osint10x , “Pryx”, the admin of the Hellcat Ransomware Group, shared insights into their methods, their vision for the future
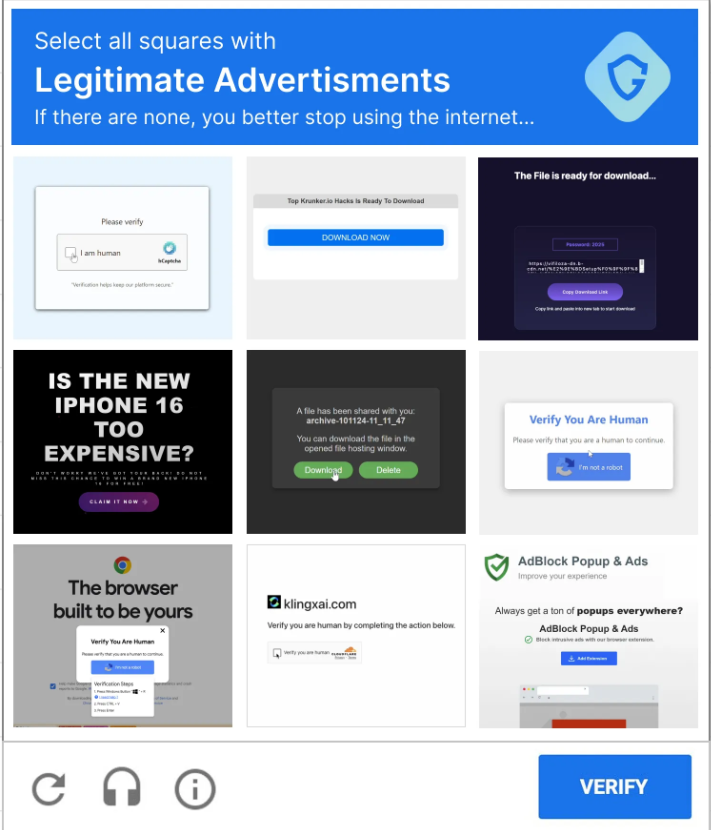
Guardio Labs tracked and analyzed a large-scale fake captcha campaign distributing a disastrous Lumma info-stealer malware that circumvents general security measures like Safe Browsing. Entirely
A coalition of international law enforcement agencies has been investigating the creator and distributor of the notorious infostealer variant RedLine in an operation codenamed “Operation

Executive Summary ReversingLabs’ machine learning-based threat hunting system detected malicious code in a legitimate looking package, aiocpa, last week that was engineered to compromise crypto currency wallets. RL
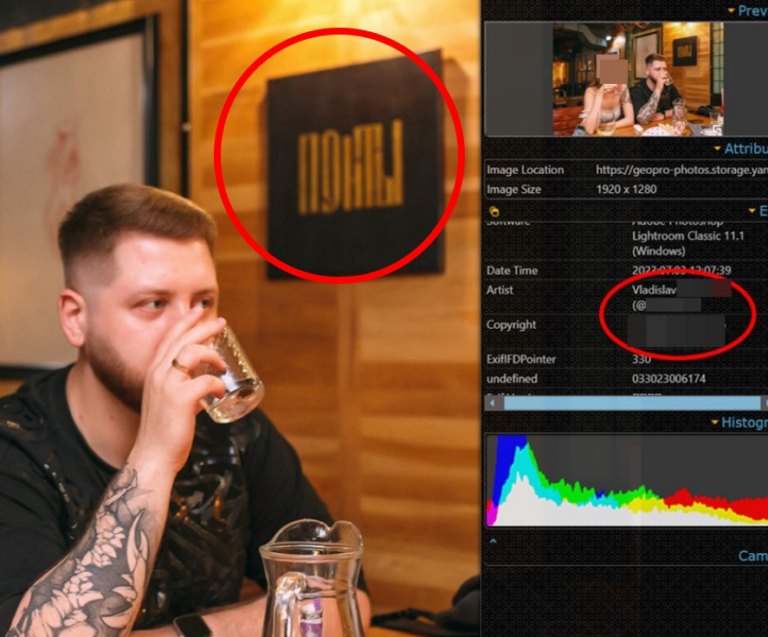
Cado Security Labs have identified a new sophisticated scam targeting people who work in Web3. The campaign includes crypto stealer Realst that has both macOS

December 10, 2024 – Hudson Rock, a leader in cybercrime intelligence, is proud to announce the official launch of CavalierGPT, the industry’s first AI-powered bot

Hudson Rock is thrilled to announce the launch of CavalierGPT, the first-ever Infostealer Intelligence AI Bot designed to empower researchers with free access to data
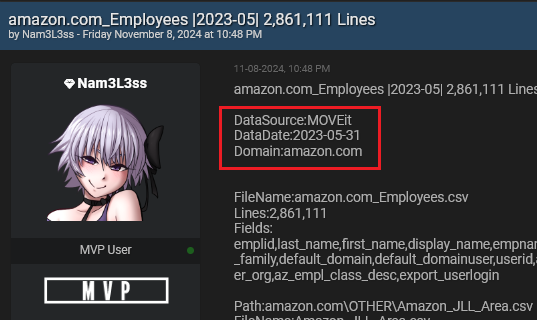
Written by Alon Gal A person operating under the username Nam3L3ss has exploited a critical vulnerability in MOVEit, a file transfer software, exposing extensive employee

Phishing email campaign targets Taiwan Talos observed an unknown threat actor conducting a malicious phishing campaign targeting victims in Taiwan since at least July 2024.

In this new episode of the mnemonic security podcast, Robby Peralta is joined by Leonid Rozenberg, a cybersecurity expert and dark web researcher at Hudson

Free Infostealer Intelligence Tools by Hudson Rock – www.hudsonrock.com/free-tools On November 4th, Schneider Electric acknowledged a data breach in which hackers stole 40GB of data

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
