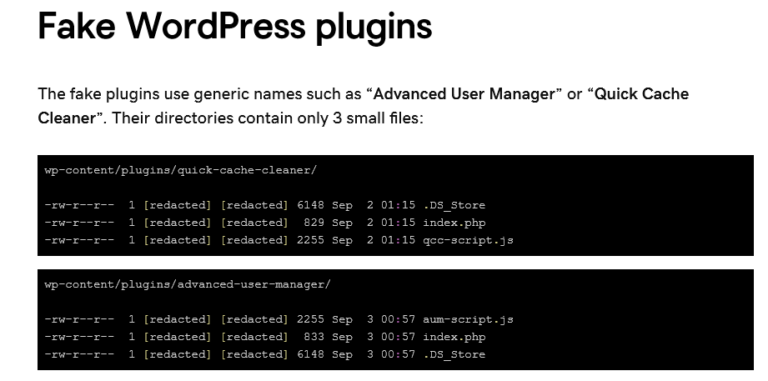
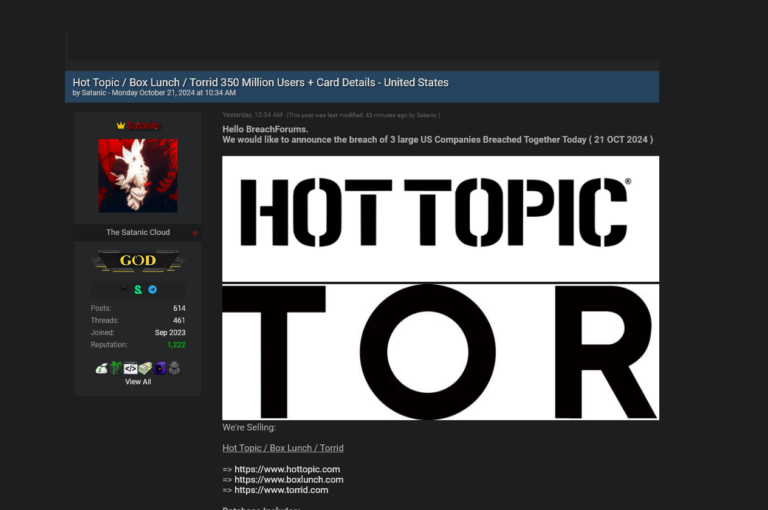
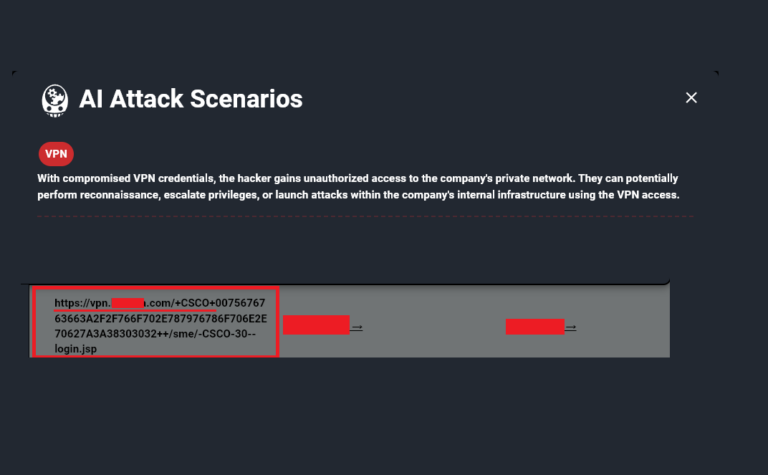
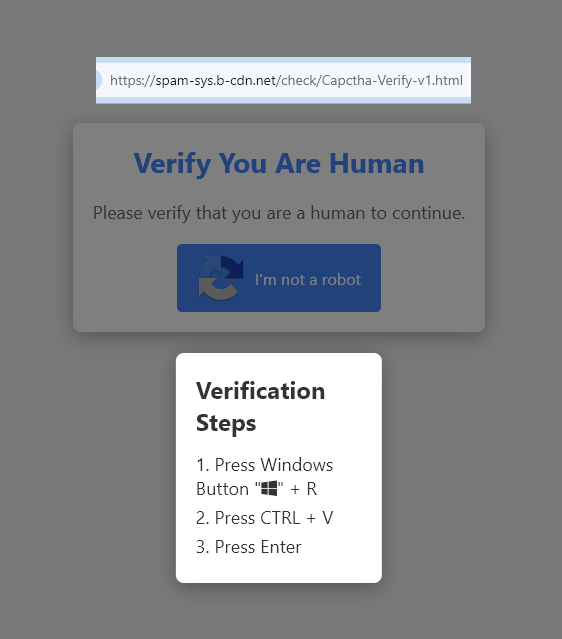
Schneider Electric Hacked and Blackmailed Following Lumma Infostealer Infection
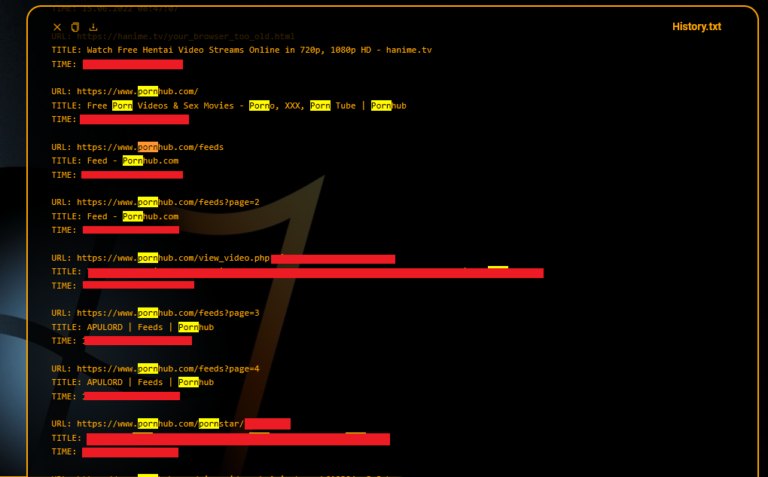
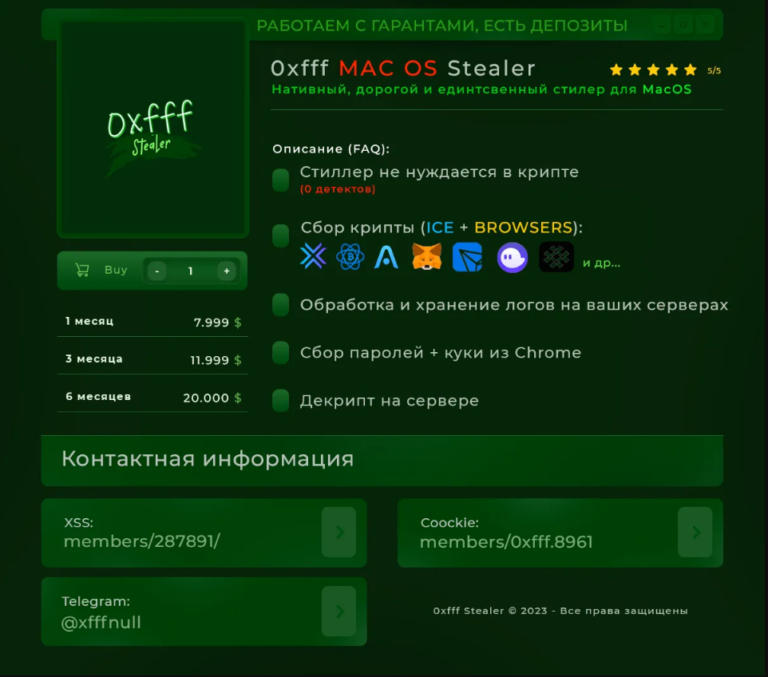
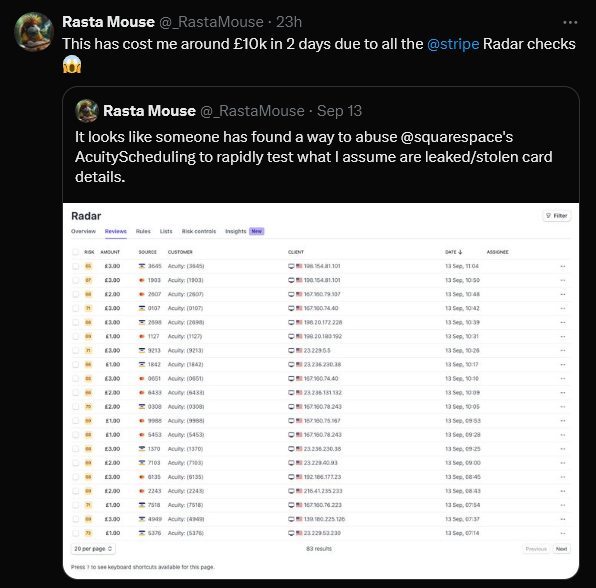
Free Infostealer Intelligence Tools by Hudson Rock – www.hudsonrock.com/free-tools On November 4th, Schneider Electric acknowledged a data breach in which hackers stole 40GB of data