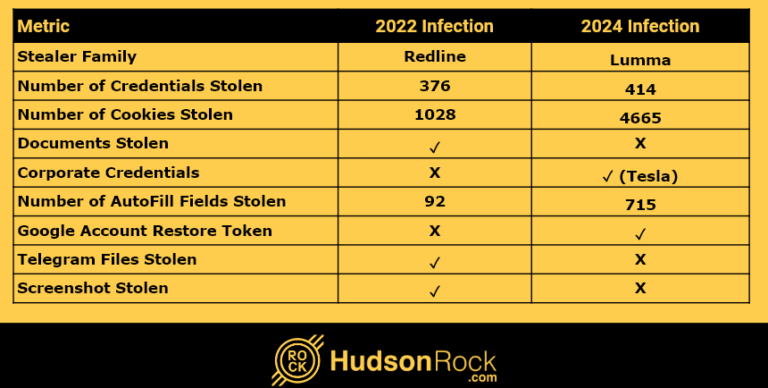
Lumma Stealer Packed with CypherIt Distributed Using Falcon Sensor Update Phishing Lure
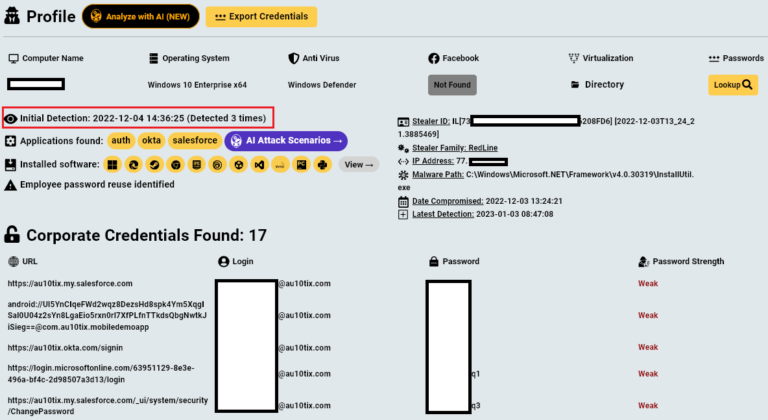
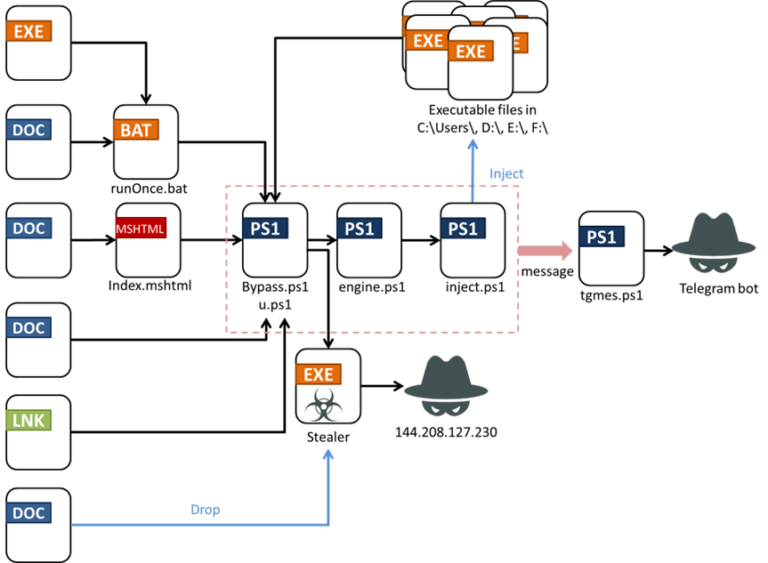
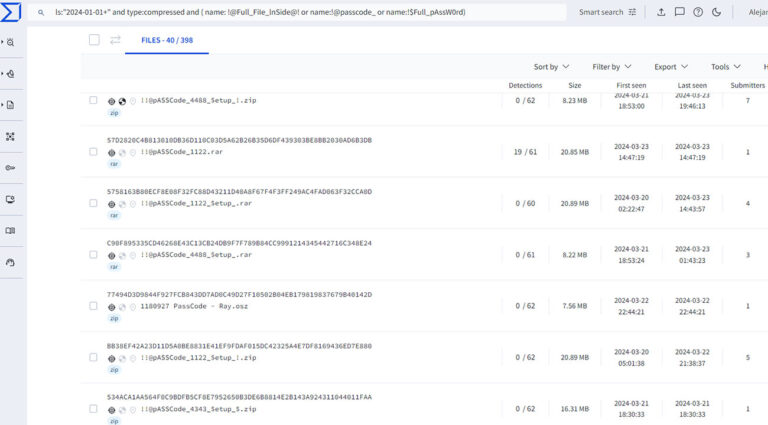
Summary On July 23, 2024, CrowdStrike Intelligence identified the phishing domain crowdstrike-office365[.]com, which impersonates CrowdStrike and delivers malicious ZIP and RAR files containing a Microsoft Installer