
Iluria Stealer; a Variant of Another Discord Stealer
EXECUTIVE SUMMARY At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors who target organizations and individuals.

EXECUTIVE SUMMARY At CYFIRMA, we are committed to offering up-to-date insights into prevalent threats and tactics employed by malicious actors who target organizations and individuals.

The adversaries use the open-source SapphireStealer to create their own Infostealer malware for collecting employee authentication data from Russian companies. Since March 2024, the BI.ZONE Threat
Executive summary In mid-April 2024, Trellix Advanced Research Center team members observed multiple fake AV sites hosting highly sophisticated malicious files such as APK, EXE
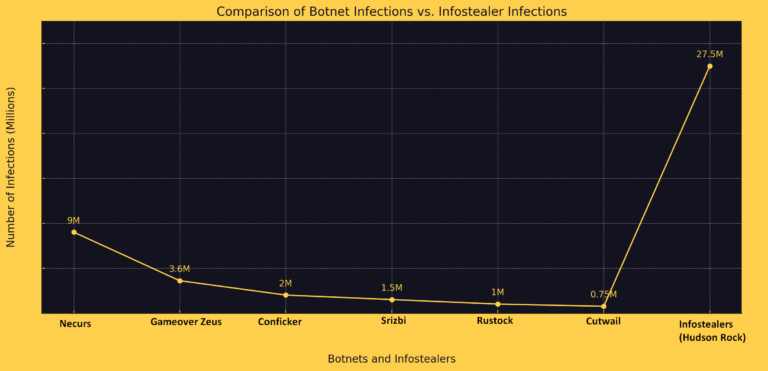
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of
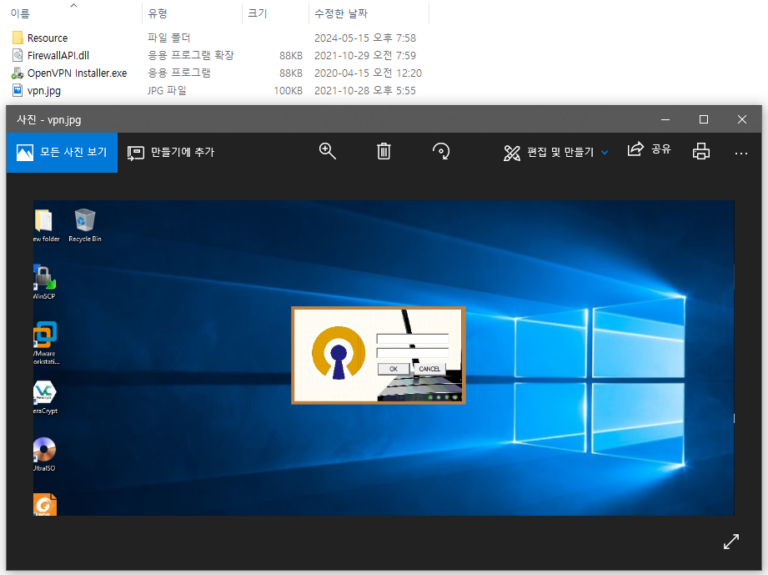
AhnLab SEcurity intelligence Center (ASEC) recently confirmed cases of APT attacks by the Andariel group targeting domestic companies and institutions. The organizations identified as targets

Summary So far, 2024 really has been the year of the infostealer when it comes to macOS malware. Families like AtomicStealer, Cuckoo, and CloudJump are

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
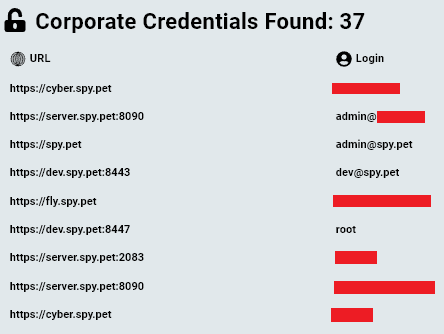
This article aims to shed light on the identity behind a massive Discord spying tool and raise concerns about the possibility of private Discord data
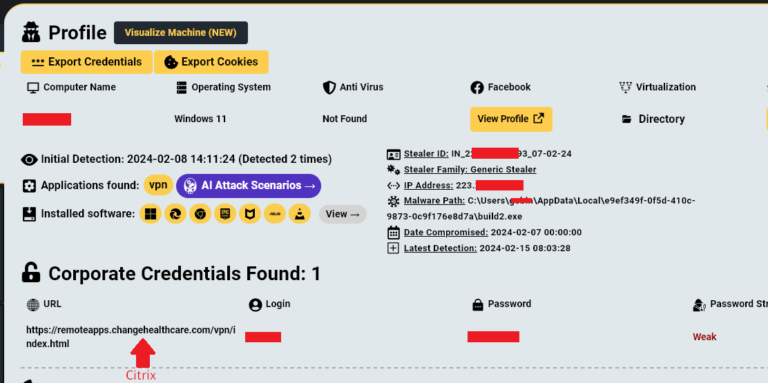
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000
AhnLab SEcurity intelligence Center (ASEC) has discovered an Infostealer strain made with Electron. Electron is a framework that allows one to develop apps using JavaScript,
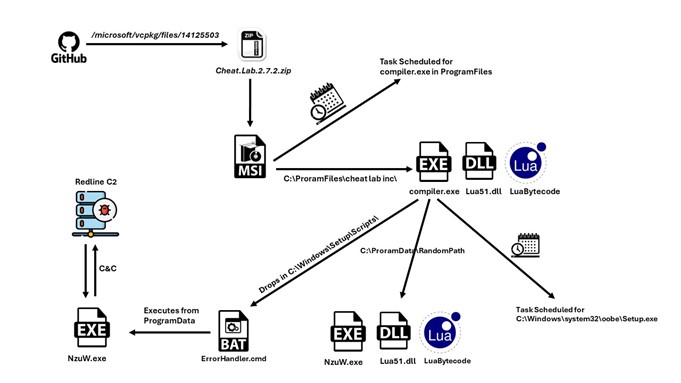
A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this

CoralRaider operators likely based in Vietnam Talos assesses with high confidence that the CoralRaider operators are based in Vietnam, based on the actor messages in

An infostealer malware campaign has collected millions of logins from users of various gaming websites, including players that use cheats, pay-to-cheat services. The details emerged

A few hours ago, The Python Package Index (PyPi) suspended new project creation and new user registration to mitigate an ongoing malware upload campaign. The

Group-IB discovers new information stealer targeting Vietnam with rare functionality to filter out Facebook accounts with advertising credits…
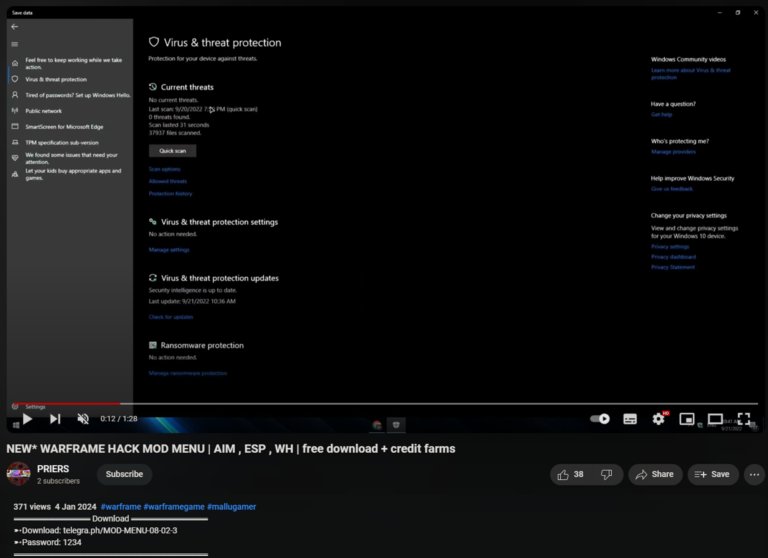
Falling victim to an infostealer, such as Redline, is arguably one of the biggest threats to consumers—individual users who might seem less lucrative targets compared

What do Andrew Tate, a Pro-Palestine hacking group, and AnyDesk all have in common? For a while now, Infostealer credentials data has been used as

Executive Summary Unit 42 researchers recently discovered activity attributed to Mispadu Stealer, a stealthy infostealer first reported in 2019. We found this activity as part

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
