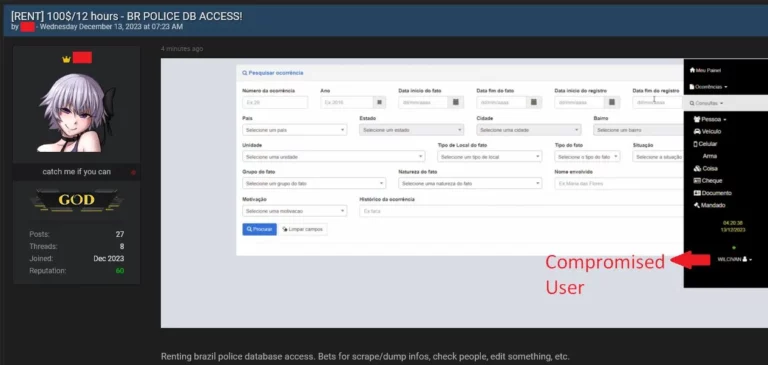
Hacker Uses Infostealer Data to Gain Access to Brazil’s Police Portal.
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…

It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…
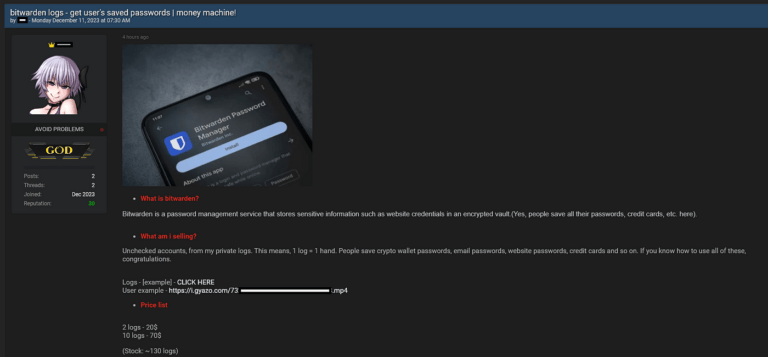
In today’s digital landscape, the reliance on password managers has become commonplace, providing users with a sense of security…

Session cookies are specific web cookies used to allow a browsing session to log in to a website’s services automatically…

The Lumma information-stealing malware is now using an interesting tactic to evade detection by security software…
In a significant development, the creators of the well-known Infostealer group, Lumma, have reportedly made a groundbreaking discovery…

Recent weeks have seen a number of macOS-specific infostealers appear for sale in crimeware forums…

What causes a man to wake up one day and say, “I’m going to build my own malware and go sell it to cybercriminals on the dark web”?
Rapid7 routinely conducts research into the wide range of techniques that threat actors use to conduct malicious activity…
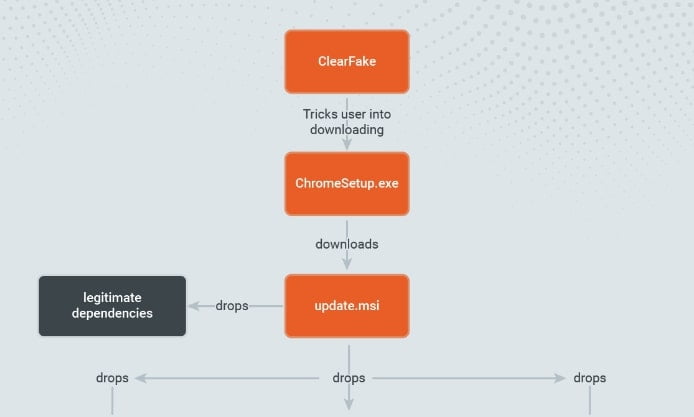
Recently, Rapid7 observed the Fake Browser Update lure tricking users into executing malicious binaries…
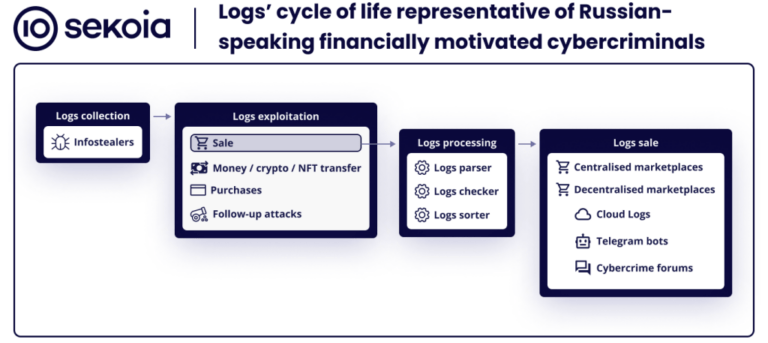
This blog post aims at presenting the life cycle of logs, the cybercrime marketplaces dedicated to logs and the noticeable schemes…

This year has seen an explosion of infostealers targeting the macOS platform. Throughout 2023…

A relatively unknown threat actor who goes by the alias “USDoD” posted a thread in which they offered the database of the FBI’s…

Using Hudson Rock’s cybercrime intelligence database, which consists of over 14,500,000 computers infected by info-stealing malware…

Threat actor “La_Citrix” is known for hacking companies and selling access to their citrix/vpn/RDP servers or otherwise for selling info-stealer logs from computer infections…

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
